Lesson Contents
Normally when your router receives unicast IP packets, it only cares about one thing:
- What is the destination IP address of this IP packet so I can forward it?
If the IP packet has to be routed it will check the routing table for the destination IP address, select the correct interface and it will be forwarded. Your router really doesn’t care about source IP addresses as it’s not important for forwarding decisions.
Because the router doesn’t check the source IP address it is possible for attackers to spoof the source IP address and send packets that normally might have been dropped by the firewall or an access-list.
uRPF is a security feature that prevents these spoofing attacks. Whenever your router receives an IP packet it will check if it has a matching entry in the routing table for the source IP address. If it doesn’t match, the packet will be discarded. uRPF has two modes:
- Strict mode
- Loose mode
Let’s examine the difference between both modes and how to configure them.
Strict Mode
Strict mode means that that router will perform two checks for all incoming packets on a certain interface:
- Do I have a matching entry for the source in the routing table?
- Do I use the same interface to reach this source as where I received this packet?
When the incoming IP packets pass both checks, it will be permitted. Otherwise, it will be dropped. This is perfectly fine for IGP routing protocols since they use the shortest path to the source of IP packets. The interface that you use to reach the source will be the same as the interface where you will receive the packets on. Here’s an illustration to demonstrate this:
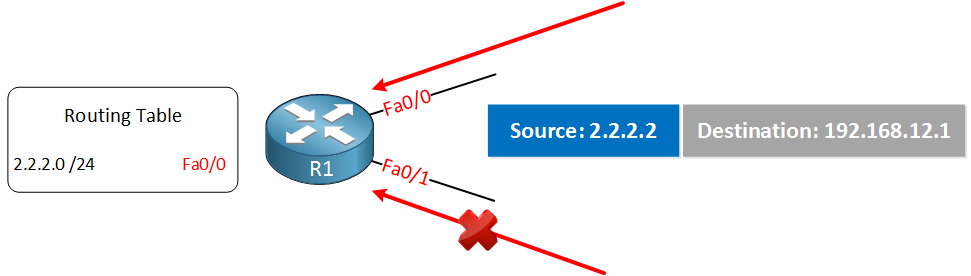
R1 has installed network 2.2.2.0 /24 in its routing table and in order to reach this network it will use the FastEthernet 0/0 interface. Suddenly this router receives an IP packet with source IP address 2.2.2.2 on both of its interfaces. The one it receives on the FastEthernet 0/0 will be accepted, but the packet on the FastEthernet 0/1 interface will be dropped because this is not the interface we use to reach this source.
Let’s configure the example above to see how it works. I’ll use the following topology:
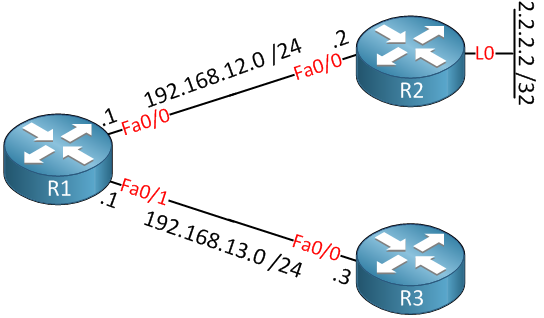
We will configure R1 with a static route so it can reach the loopback0 interface of R2:
R1(config)#ip route 2.2.2.2 255.255.255.255 192.168.12.2This is what the routing table looks like now:
R1#show ip route
C 192.168.12.0/24 is directly connected, FastEthernet0/0
C 192.168.13.0/24 is directly connected, FastEthernet0/1
2.0.0.0/32 is subnetted, 1 subnets
S 2.2.2.2 [1/0] via 192.168.12.2Now we’ll configure uRPF strict mode on both interfaces:
R1(config)#interface fastEthernet 0/0
R1(config-if)#ip verify unicast source reachable-via rx
R1(config)#interface fastEthernet 0/1
R1(config-if)#ip verify unicast source reachable-via rxYou can verify that it has been enabled on the interface like this:
R1#show ip interface fastEthernet 0/0 | include verify
IP verify source reachable-via RX
R1#show ip interface fastEthernet 0/1 | include verify
IP verify source reachable-via RXTo test uRPF we’ll send some pings from R2 first. These should be accepted:
R2#ping 192.168.12.1 source loopback 0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.12.1, timeout is 2 seconds:
Packet sent with a source address of 2.2.2.2
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 4/4/8 msAs expected, this ping works. Now I’ll create a new loopback interface on R3 with the 2.2.2.2 IP address on it so that we can spoof this IP address:
R3(config)#interface loopback 0
R3(config-if)#ip address 2.2.2.2 255.255.255.255Now we’ll send some pings from this loopback:
R3#ping 192.168.13.1 source loopback 0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.13.1, timeout is 2 seconds:
Packet sent with a source address of 2.2.2.2
.....
Success rate is 0 percent (0/5)The packets will make it to R1, but they will be dropped there, we can verify this as follows:
R1#show ip interface fastEthernet 0/0 | include drops
0 verification drops
0 suppressed verification dropsR1#show ip interface fastEthernet 0/1 | include drops
5 verification drops
0 suppressed verification dropsAbove, you see that the spoofed packets on the FastEthernet 0/1 interface have been dropped.
Configurations
Want to take a look for yourself? Here you will find the final configuration of each device.
R1
hostname R1
!
ip cef
!
interface FastEthernet0/0
ip address 192.168.12.1 255.255.255.0
ip verify unicast source reachable-via rx
!
interface FastEthernet0/1
ip address 192.168.13.1 255.255.255.0
ip verify unicast source reachable-via rx
!
ip route 2.2.2.2 255.255.255.255 192.168.12.2
!
endR2
hostname R2
!
ip cef
!
interface Loopback0
ip address 2.2.2.2 255.255.255.255
!
interface FastEthernet0/0
ip address 192.168.12.2 255.255.255.0
!
endR3
hostname R3
!
ip cef
!
interface Loopback0
ip address 2.2.2.2 255.255.255.255
!
interface FastEthernet0/0
ip address 192.168.13.3 255.255.255.0
!
endNow let’s take a look at loose mode…
Loose Mode
Loose mode means that the router will perform only a single check when it receives an IP packet on an interface:
- Do I have a matching entry for the source in the routing table?
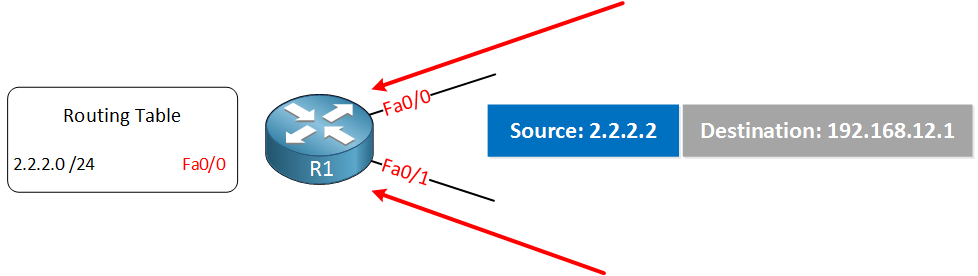
When it passed this check, the packet is permitted. Whether we use this interface to reach the source or not doesn’t matter. Loose mode is useful when you are connected to more than one ISP, and you use asymmetric routing. The only exception is the null0 interface, if you have any sources with the null0 interface as the outgoing interface, then the packets will be dropped. Take a look at this illustration:



First step to protect against DoS and DDoS attacks.
Further ones may include RTBH, prefix-lists denying the bogon and spoofed prefixes, CoPP on the backplane and rate-limiters.
Due to architectural differences, Nexus 7k uses the “allow default” option implicitly, while the 5k doesn’t.
the ONLY uRPF tutorial on internet that actually makes sense, thanks very much Rene.
Thanks a million Rene. Well done, well written, it simply goes straight to the point. Perfect!
hiii Rene,
Can you please explain the diff between verification drops and suppressed verification drops.