Lesson Contents
ISATAP (Intra Site Automatic Tunnel Addressing Protocol) is an IPv6 tunneling technique that allows you to connect IPv6 over an IPv4 network, similar to the automatic 6to4 tunnel.
On your IPv4 network, you can configure one of your routers as an IPv6 “headend” ISATAP router that your IPv6 hosts can connect to. The IPv4 source address of the ISATAP clients and router is embedded in the IPv6 address so that each device knows how to get to the other side of the IPv4 network.
Here’s what the IPv6 address looks like:
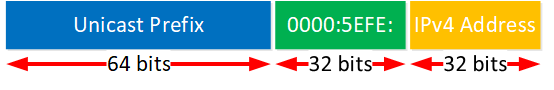
The first 64 bits are for the prefix, and you can pick anything you like. Global unicast, link-local addresses, both are possible. The next 64 bits are divided into two parts:
- 0000:5EFe: this is a reserved UOI value which indicates that this is an ISATAP address.
- the remaining 32 bits embed the IPv4 address, in hexadecimal.
ISATAP was designed for intra site, in other words…within your site, not between sites. However, nothing is stopping you from running this between sites.
It is easy to configure, and many clients support ISATAP, including any recent Windows or Linux OS. You can configure the tunnel destination address manually or add it to a DNS server so that it’s easy to find.
Configuration
Cisco IOS supports both the ISATAP client and headend router. In this lesson, I use the following topology:

R1 is the ISATAP client, R3 is the headend router. We will use 2001:DB8:13:13::/64 as the prefix on the tunnel interface. I use OSPFv2 so that R1 and R3 are able to reach each other through IPv4. R3 also has a loopback interface with an IPv6 address, something we can try to ping from R1.
Set-NetIsatapConfiguration -State Enabled -Router 192.168.23.3 -PassThru and it will connect to your headend router. You can check the IPv6 address with ipconfig.Configurations
Want to take a look for yourself? Here you will find the startup configuration of each device.
R1
hostname R1
!
ip cef
!
interface FastEthernet0/0
ip address 192.168.12.1 255.255.255.0
!
router ospf 1
router-id 1.1.1.1
log-adjacency-changes
network 192.168.12.0 0.0.0.255 area 0
!
endR2
hostname R2
!
ip cef
!
interface FastEthernet0/0
ip address 192.168.12.2 255.255.255.0
!
interface FastEthernet1/0
ip address 192.168.23.2 255.255.255.0
!
router ospf 1
router-id 2.2.2.2
network 192.168.12.0 0.0.0.255 area 0
network 192.168.23.0 0.0.0.255 area 0
!
endR3
hostname R3
!
ip cef
!
interface Loopback0
ipv6 address 2001:DB8:3:3::3/128
!
interface FastEthernet0/0
ip address 192.168.23.3 255.255.255.0
!
router ospf 1
router-id 3.3.3.3
log-adjacency-changes
network 192.168.23.0 0.0.0.255 area 0
!
endHeadend
Let’s start with the headend router. First, we need to enable IPv6 unicast routing:
R3(config)#ipv6 unicast-routingNow we can focus on the tunnel interface:
R3(config)#interface Tunnel 0
R3(config-if)#ipv6 address 2001:db8:13:13::/64 eui-64
R3(config-if)#no ipv6 nd suppress-ra
R3(config-if)#tunnel source FastEthernet0/0
R3(config-if)#tunnel mode ipv6ip isatapI configure the 2001:DB8:13:13::/64 prefix and let the router configure the last 64 bits using EUI-64. You’ll see in a bit what address we end up with. By default, the router will not send router advertisements on the tunnel interface which is why we need to add the no ipv6 and suppress-ra command,
Client
Let’s configure our client:
R1(config)#interface Tunnel 0
R1(config-if)#ipv6 address autoconfig
R1(config-if)#tunnel source FastEthernet 0/0
R1(config-if)#tunnel destination 192.168.23.3
R1(config-if)#tunnel mode ipv6ipThe tunnel interface is configured to configure its IPv6 address automatically. The tunnel source is our FastEthernet 0/0 interface and the destination is the IPv4 address of R3.
Verification
Let’s see if our configuration works. I’ll start with the headend router…
Headend
Let’s take a look at our tunnel interface:
R3#show ipv6 interface Tunnel 0
Tunnel0 is up, line protocol is up
IPv6 is enabled, link-local address is FE80::5EFE:C0A8:1703
Global unicast address(es):
2001:DB8:13:13:0:5EFE:C0A8:1703, subnet is 2001:DB8:13:13::/64 [EUI]
Joined group address(es):
FF02::1
FF02::2
FF02::1:FFA8:1703
MTU is 1480 bytes
ICMP error messages limited to one every 100 milliseconds
ICMP redirects are enabled
ND DAD is not supported
ND reachable time is 30000 milliseconds
ND advertised reachable time is 0 milliseconds
ND advertised retransmit interval is 0 milliseconds
ND router advertisements live for 1800 seconds
Hosts use stateless autoconfig for addresses.Above, we see a couple of interesting things:
- Both the link-local and global unicast prefix have the 0000:5EFE: bits that indicate that this is an ISATAP address.
- Our IPv6 addresses end with C0A8:1703.
- We can verify that this router is sending router advertisements.
Below you can see the decimal IPv4 address that is embedded in the IPv6 address:
| Decimal | 192 | 168 | 23 | 3 |
| Binary | 11000000 | 10101000 | 00010111 | 00000011 |
| Hexadecimal | C0 | A8 | 17 | 03 |
Client
Let’s take a look at our client:
R1#show ipv6 interface Tunnel 0
Tunnel0 is up, line protocol is up
IPv6 is enabled, link-local address is FE80::C0A8:C01
Global unicast address(es):
2001:DB8:13:13::C0A8:C01, subnet is 2001:DB8:13:13::/64 [PRE]
valid lifetime 2591842 preferred lifetime 604642
Joined group address(es):
FF02::1
FF02::2
FF02::1:FFA8:C01
MTU is 1480 bytes
ICMP error messages limited to one every 100 milliseconds
ICMP redirects are enabled
ND DAD is enabled, number of DAD attempts: 1
ND reachable time is 30000 milliseconds
Default router is FE80::5EFE:C0A8:1703 on Tunnel0Above, we see two interesting items:



HI Rene’
I not understand very well why the eui-64 i s needed, and also why on R1 the command
tunnel mode ipv6ip isatapis not needed.
Also I’m testing this configuration on gns3 and router r1 not install a static route.
Hello Giovanni
According to Cisco documentation, when configuring ISATAP:
If you were to specify the address fully, the ISATAP operation would not function.
Also, when you configure
... Continue reading in our forumtunnel mode ipv6ip isatapon the headend, there is no need to specify the mode in which the tunnel will be functioning on the client. On the client, you also setipv6 address autoconfig, which meansHi Rene and Laz,
Would you say that the ISATAP operation is very similar to the DMVPN Phase 1 where all of the tunnel traffic has to traverse the “Headend” router just like with DMVPN phase 1 and its “HUB”?
Hello Nitay
It is similar only so far as the traffic actually traverses the router itself (either the head end or the HUB in each case) to get to its destination. However, beyond that, the purpose and the mechanisms of the two features you mention are completely different.
I hope this has been helpful!
Laz
In the ISATAP lesson, client config section, the tunnel mode command says:
tunnel mode ipv6ipand there is noisatapin the end. Was that left out on purpose -because it’s a client- or is that a typo?