When it comes to securing the network, AAA and 802.1X authentication are two powerful tools we can use. Let me show you an example of why you might want this for your switches:
Network users might bring their own wireless router from home and connect it to the switch so they can share wireless internet with all their colleagues. An access point like this is called a rogue access point, which you DON’T want to see on your network. It’s hard to detect because on the switch you’ll only see one MAC address. The router is doing NAT so you will only see one IP address, this is something you can’t prevent with port security.
One way of dealing with issues like this is to use AAA.
AAA stands for Authentication, Authorization, and Accounting:
- Authentication: Verify the identity of the user. Who are you?
- Authorization: What is the user allowed to do? what resources can he/she access?
- Accounting: Used for billing and auditing.
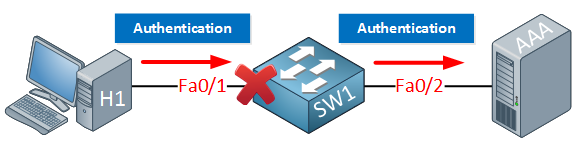
The idea behind AAA is that a user has to authenticate before getting access to the network. The fa0/1 interface on SW1 will be blocked, and you will not even get an IP address. The only thing the user is allowed to do is send his/her credentials, which will be forwarded to the AAA server. If your credentials are OK, the port will be unblocked, and you will be granted access to the network.
802.1X is the mechanism that will block or unblock the interface. It’s called port-based control. In the picture above, an unknown user plugged in a cable to the switch.


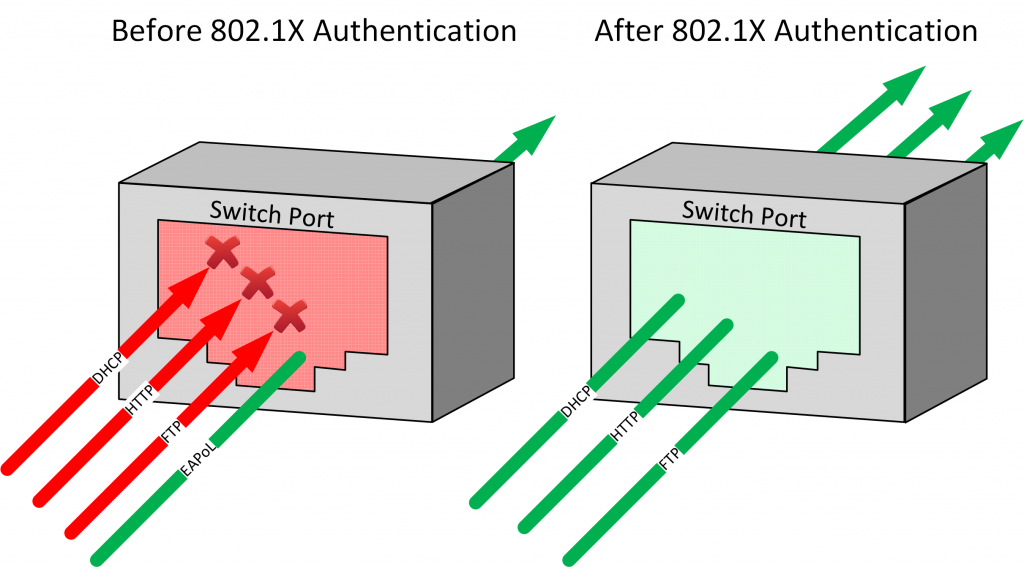

What’s the name of the follow-up lesson? “In another lesson I will give you a configuration example how to implement this on a Cisco Catalyst Switch.”
Or does it not yet exist?
Hi Tim,
I just added a link in the lesson, or you can use this one:
AAA Configuration on Cisco Catalyst Switch
Rene
Radius and tacacs are used to authenticate user for only management of intermediary device ,or to access at intranet domain and my be go out to internet??
Hi Francesco,
We use RADIUS and TACACS+ for both user authentication and management. For example, with wireless networks we use RADIUS for user authentication (WPA2-enterprise). This allows us to use client and server certificates and it’s a far more secure solution than using pre-shared keys only.
For network management, it’s useful since you can centralize all your authentication instead of creating usernames/passwords on each and every router, switch, firewall, etc on your network.
It’s used on local networks, the only time you might use it on the Internet i
... Continue reading in our forumHi Rene,
Which’s standard of RFC that I can follow when learning the TACACS+?
Many thanks!