Lesson Contents
In this lesson, we will take a look at how to configure a Cisco Catalyst Switch to use AAA and 802.1X for port-based authentication. If you have no idea what AAA (Authentication, Authorization, and Accounting) or 802.1X are about then you should look at my AAA and 802.1X Introduction first. Having said that, let’s look at the configuration. I will use the following topology:
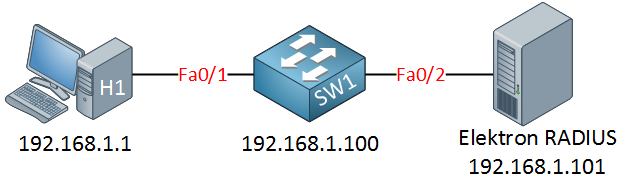
I will show you an example of 802.1X with a RADIUS server. I am going to use the Elektron RADIUS server as the authentication server because it’s easy to install and has a nice GUI.
RADIUS Server Configuration
Using a RADIUS server like Elektron will save you the time of hassling with installing Windows Server, configuring Active Directory, and checking many checkboxes or messing around with Freeradius on Linux. When you configure a RADIUS server, you will need to create a shared password:
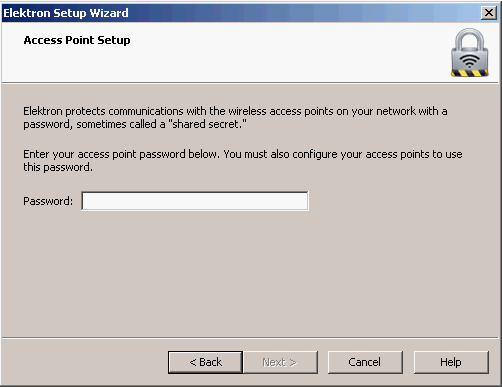
I’m going to use “radiuspass” to keep things simple. Hit Next, and you will see this:
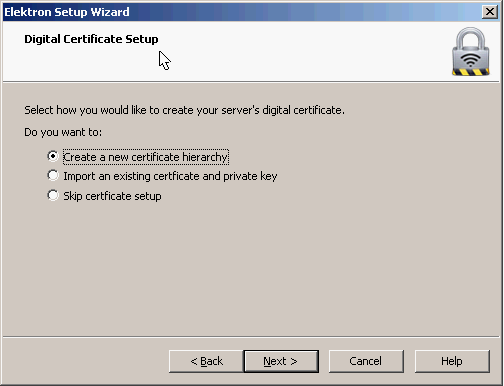
There are different authentication methods, for example:
- Only username and password.
- Username, password, and a digital certificate on the server.
- Username, password, and digital certificate on the server AND the clients.
In a production network, you might already have a certificate authority within your network. I don’t care about certificates for this demonstration, but we’ll generate them anyway in case you want to play with them sometime in the future. The next steps will let you configure a name for your RADIUS server, and if you want the digital certificate, you will get some questions about it. Once you are done, you will be on the main screen of Elektron:
By default, everything should work out of the box so we don’t have to touch anything. Let’s start and add a user account:
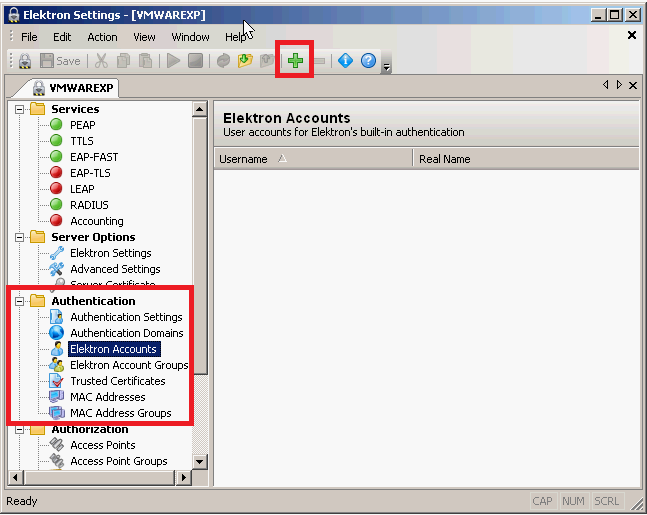
I want to create a new user account. Click on authentication, Elektron accounts, and then on the green plus symbol in the menu.
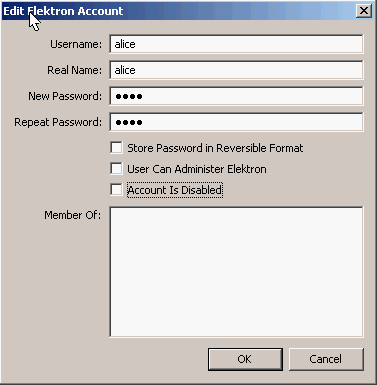
My new user account will be for Alice. My password will be “safe”, and I don’t need her to be a member of any groups. Click on OK.
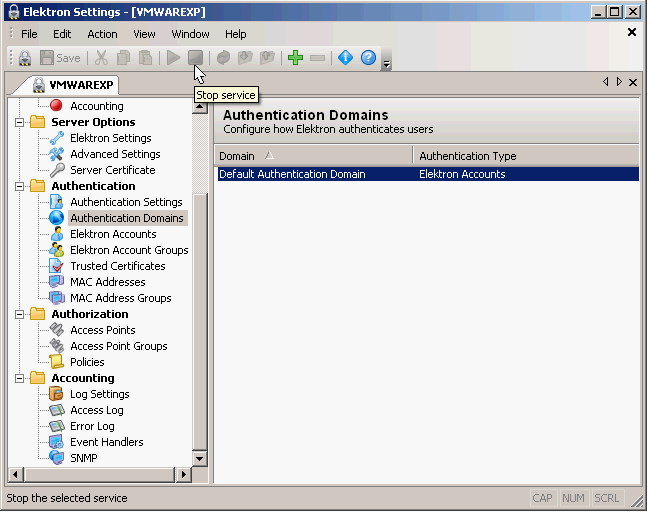
By default, Elektron will check Windows usernames instead of its database. We need to configure it so the local database is used. Click on “Authentication Domains” and then on “Default Authentication Domain”.
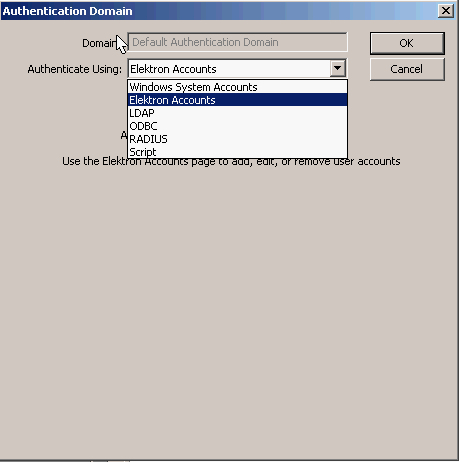
Change it to “Elektron Accounts” and click on OK. That’s all you have to do on the Elektron RADIUS server. We’ll look at the switch now!
Switch Configuration
First, I need to make sure SW1 and the Elektron RADIUS server can reach each other. We’ll use the management interface (VLAN 1) and configure an IP address on it:
SW1(config)#interface vlan 1
SW1(config-if)#ip address 192.168.1.100 255.255.255.0Now, we should enable AAA:
SW1(config)#aaa new-modelThis is an important command. Use aaa new-model to unlock all the different AAA commands that we need. Let’s configure the RADIUS server:



Nice read , thank you Rene
I was looking for something like this…
Thanks
If different users want to set different passwords , how can we configure that?
Hi Sakeb,
You can do this on the radius server. In my example I only created one user account (Alice) but you can create an account for each user here.
Rene
Hi Rene,
I’m playing with an IE3000 switch SW version 15, and the command dot1x port-control auto does not exist, I have the following options:
I tried default, but
... Continue reading in our forum