Lesson Contents
IP SLA (Service-Level Agreement) is a great feature on Cisco IOS devices that can be used to “measure” network performance.
This can be something simple like a ping where we check the round-trip time or something more advanced like a VoIP RTP packet where we check the delay, jitter and calculate a MOS score that gives you an indication what the voice quality will be like.
Measuring network performance is pretty cool but what makes IP SLA even more powerful is that you can combine it with static routes, policy based routing and routing protocols like OSPF or EIGRP.
Let me give you an example why this is a great feature to use. Take a look at the image below:
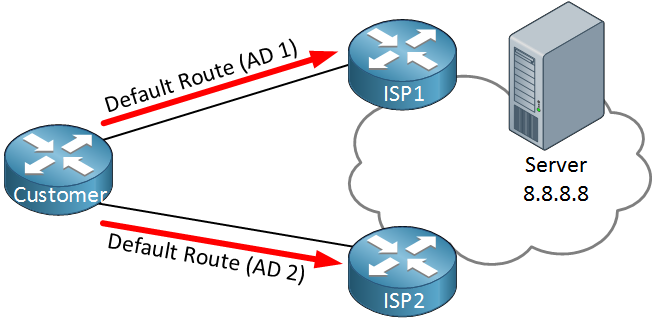
Above we have a customer router connected to two ISPs. Somewhere on the Internet there’s a server we’d like to reach. In a scenario like this, typically we use two default routes with different ADs. Whenever ISP1 fails, we switch over to ISP2.
The problem with this setup is that it’s not very reliable. The default route will be in the routing table as long as the interface is up and/or the next hop is reachable. It’s possible that ISP1 is having connectivity issues and unable to reach that remote server but we still use them for all our traffic.
To prevent this from happening we can combine default routes with IP SLA. Here’s an example:
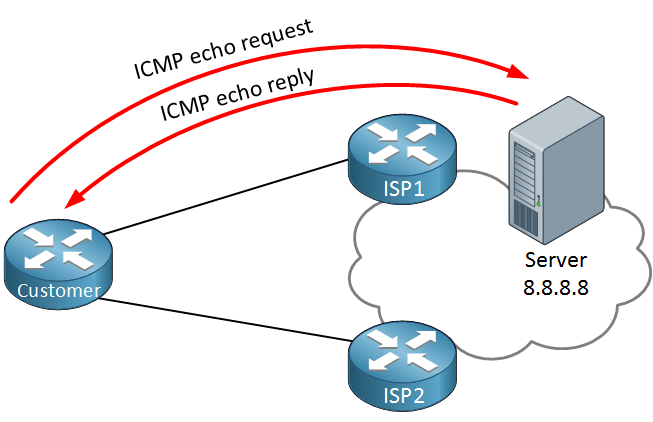
Our customer router is now using IP SLA to ping the remote server. As long as we get a reply, we will keep using ISP1 as our main route. When the ping fails, we switch over to ISP2. This method is far more reliable as we check end-to-end connectivity.
Here’s another example where IP SLA might be useful:
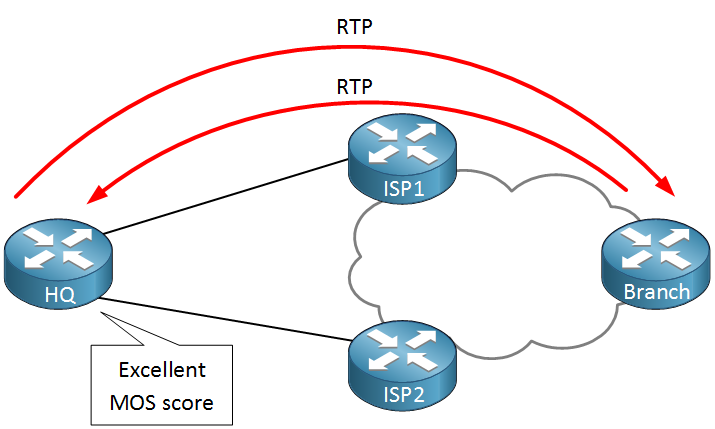
Above we have two ISPs that we can use to reach a remote branch router. Instead of a simple ping, we can send RTP packets and check these for a certain delay, jitter and calculate a MOS score. When we get below a certain threshold we will switch from ISP1 to ISP2.
Each measurement that we do with IP SLA is called an operation. For each operation we have to configure the type of traffic, source IP, destination IP, port numbers, etc. We can then configure when to run the operation…24/7, 9-to-5, etc.
When you use IP SLA for a simple ping then you only have to configure your local router. However when you want to use it for some more advanced things like sending RTP packets then you have to configure the remote router to respond to your IP SLA traffic.
Besides pings and RTP, there are a lot of different operations we can use:
- TCP Connections
- UDP
- DNS
- DHCP
- HTTP
- FTP
Now you have an idea what IP SLA is about, let’s take a look how we can configure an operation.
Configuration
I will show you two examples so you will learn how to configure IP SLA operations. We’ll try an example with pings and an example with UDP jitter.
ICMP echo Operation
We will use the following topology:
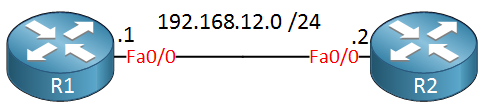
All I need is two routers, R1 will send ICMP echo requests and R2 will reply to them. Here’s how to configure IP SLA:
R1(config)#ip sla 1
R1(config-ip-sla)#?
IP SLAs entry configuration commands:
dhcp DHCP Operation
dns DNS Query Operation
ethernet Ethernet Operations
exit Exit Operation Configuration
ftp FTP Operation
http HTTP Operation
icmp-echo ICMP Echo Operation
icmp-jitter ICMP Jitter Operation
mpls MPLS Operation
path-echo Path Discovered ICMP Echo Operation
path-jitter Path Discovered ICMP Jitter Operation
tcp-connect TCP Connect Operation
udp-echo UDP Echo Operation
udp-jitter UDP Jitter Operation
voip Voice Over IP OperationFirst we have to choose an operation number, let’s pick number 1. You can see that there are a lot of different operations we can choose from. Let’s start with the icmp echo:
R1(config-ip-sla)#icmp-echo 192.168.12.2
R1(config-ip-sla-echo)#?
IP SLAs Icmp Echo Configuration Commands:
default Set a command to its defaults
exit Exit operation configuration
frequency Frequency of an operation
history History and Distribution Data
no Negate a command or set its defaults
owner Owner of Entry
request-data-size Request data size
tag User defined tag
threshold Operation threshold in milliseconds
timeout Timeout of an operation
tos Type Of Service
verify-data Verify data
vrf Configure IP SLAs for a VPN Routing/Forwarding instanceLet’s send ICMP echos to 192.168.12.2. There are a lot of optional parameters you can configure for an operation, for example let’s change the frequency:
R1(config-ip-sla-echo)#frequency 10We’ll send an ICMP echo every 10 seconds. The only thing left to do is to start our IP SLA operation. This is how you do it:
R1(config)#ip sla schedule 1 ?
ageout How long to keep this Entry when inactive
life Length of time to execute in seconds
recurring Probe to be scheduled automatically every day
start-time When to start this entry
<cr>You have to use the ip sla schedule command to start your operation. You can schedule it but we will start our operation right now and let it run forever:
R1(config)#ip sla schedule 1 start-time ?
after Start after a certain amount of time from now
hh:mm Start time (hh:mm)
hh:mm:ss Start time (hh:mm:ss)
now Start now
pending Start pendingR1(config)#ip sla schedule 1 start-time now ?
ageout How long to keep this Entry when inactive
life Length of time to execute in seconds
recurring Probe to be scheduled automatically every dayR1(config)#ip sla schedule 1 start-time now life ?
<0-2147483647> Life seconds (default 3600)
forever continue running foreverR1(config)#ip sla schedule 1 start-time now life foreverIt should now be up and running. You can check your IP SLA configuration like this:



Hi Rene,
How would you go about redirecting traffic if a MOS falls below a certain score?
Thanks
Rob
Hi Rob,
I’m not sure if MOS can be used directly as a operation “failure” for IP SLA, that’s something I’d have to check.
One method that works for sure is to use an IP SLA reaction. You can configure it to produce a syslog message when the MOS score gets below a certain value.
You can then use EEM to act upon this syslog message:
https://networklessons.com/system-management/cisco-ios-embedded-event-manager
Rene
Hi Rene,
Would you please let me know why this post is not shown in your official book HOW TO MASTER CCNP .
This is not the only article which is not shown in the book ? why the book is not updated in the same manner of the website ?
I evaluated the website 100% , but the book has some missing information if we compared to the website.
Can you please let me know . The version of the book has been buy from amazon.com and it is printed on 2015 .
Hi Sinan,
The books are updated a few times per year, it’s possible that there is newer material here (one of the advantages of online publishing). The next time I do an update on the books, I might add some of the articles here in it.
Rene
For whomever do not know what MOS means, I just wanted to share some basic info:
Mean opinion score (MOS)
VoIP measurements are collected for after testing the one-way delay or the latency of the connection, packet loss with a metric to include the number of consecutive packets lost, and the amount jitter (difference in time it takes packets to arrive). Calculations then factor an R Factor that can be used to estimate a MOS score.
MOS has a subjective measurement where listeners would sit in a “quiet room” and score call quality as they perceived it
Mean opini
... Continue reading in our forum