Lesson Contents
Configuring IPSec tunnels can be an administrative nightmare if you have a lot of remote peers. In hub and spoke topologies, we can use VTIs (Virtual Tunnel Interface) to simplify our configuration.
There are two VTI “types”:
- Dynamic VTI (DVTI)
- Static VTI (VTI)
With DVTI, we use a single virtual template on our hub router. Whenever a new IPSec session is needed, the router automatically creates a virtual access interface that is cloned from the virtual template. The virtual template can include pretty much everything you would use on a regular interface. You can add access-lists, policy-maps for QoS, etc. These are all copied to the virtual access interfaces. This makes it really easy to create lots of IPSec sessions with remote peers.
On the spoke routers, we only have an IPSec session with the hub so we use static VTIs with a normal tunnel interface. In this lesson, I’ll show you how to configure DVTI on a hub and static VTIs on the spokes.
Configuration
Here is the topology we will use:
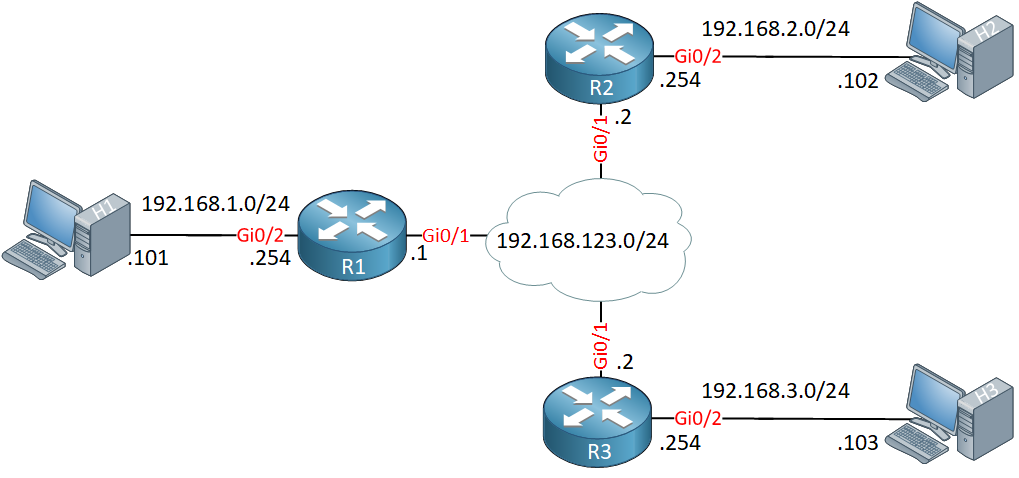
We have three routers. R1 is our hub, R2 and R3 are spoke routers. Behind each router, I have a host that we’ll use to test our VPN.
Configurations
Want to take a look for yourself? Here you will find the startup configuration of each device.
H1
hostname H1
!
no ip routing
!
no ip cef
!
interface GigabitEthernet0/1
ip address 192.168.1.101 255.255.255.0
!
endH2
hostname H2
!
no ip routing
!
no ip cef
!
interface GigabitEthernet0/1
ip address 192.168.2.102 255.255.255.0
!
ip default-gateway 192.168.2.254
!
endH3
hostname H3
!
no ip routing
!
no ip cef
!
interface GigabitEthernet0/1
ip address 192.168.3.103 255.255.255.0
!
ip default-gateway 192.168.3.254
!
endR1
hostname R1
!
ip cef
!
interface GigabitEthernet0/1
ip address 192.168.123.1 255.255.255.0
!
interface GigabitEthernet0/2
ip address 192.168.1.254 255.255.255.0
!
interface Loopback0
ip address 1.1.1.1 255.255.255.255
!
endR2
hostname R2
!
ip cef
!
interface GigabitEthernet0/1
ip address 192.168.123.2 255.255.255.0
!
interface GigabitEthernet0/2
ip address 192.168.2.254 255.255.255.0
!
interface Loopback0
ip address 2.2.2.2 255.255.255.255
!
endR3
hostname R3
!
ip cef
!
interface GigabitEthernet0/1
ip address 192.168.123.3 255.255.255.0
!
interface GigabitEthernet0/2
ip address 192.168.3.254 255.255.255.0
!
interface Loopback0
ip address 3.3.3.3 255.255.255.255
!
endLet’s get started…
Hub Router
The hub router will have a dynamic VTI. Let’s start with a key ring where I configure the pre-shared keys for our two routers:
R1(config)#crypto keyring KEY_RING
R1(conf-keyring)#pre-shared-key address 192.168.123.2 key R1_R2
R1(conf-keyring)#pre-shared-key address 192.168.123.3 key R1_R3pre-shared-key address 0.0.0.0 key R1_R2_R3 instead.Let’s create an IKE phase 1 policy:
R1(config)#crypto isakmp policy 1
R1(config-isakmp)#encryption aes
R1(config-isakmp)#hash sha
R1(config-isakmp)#group 5
R1(config-isakmp)#authentication pre-shareAnd a phase 2 policy:
R1(config)#crypto ipsec transform-set TRANSFORM_SET esp-aes esp-sha-hmac
R1(cfg-crypto-trans)#mode tunnelOur next step is to create an IPSec profile, this is a replacement for the crypto map and used for tunnel interfaces.
The IPSec profile is where we configure parameters that we want to use for IPSec encryption. We only need to refer to the transform-set we created:
R1(config)#crypto ipsec profile IPSEC_PROFILE
R1(ipsec-profile)#set transform-set TRANSFORM_SETNow, we can create the virtual template:
R1(config)#interface Virtual-Template 1 type tunnel
R1(config-if)#tunnel mode ipsec ipv4
R1(config-if)#ip unnumbered loopback 0
R1(config-if)#tunnel protection ipsec profile IPSEC_PROFILEThe tunnel mode is IPSec for IPv4 and I will use the IP address of my loopback interface with the ip unnumbered command. We also link the IPSec profile to the virtual template.
The last thing we need to do to finish our VPN configuration is to create an ISAKMP profile. The ISAKMP profile is where we can configure phase 1 and phase 1.5 commands for a set of peers. This includes things like the keepalive, identities, authentication (xauth) etc.
We only need to define our key ring, the remote peers and the virtual template in our ISAKMP profile:
R1(config)#crypto isakmp profile ISAKMP_PROFILE
R1(conf-isa-prof)#keyring KEY_RING
R1(conf-isa-prof)#match identity address 192.168.123.2 255.255.255.255
R1(conf-isa-prof)#match identity address 192.168.123.3 255.255.255.255
R1(conf-isa-prof)#virtual-template 1match identity address 0.0.0.0here instead.The VPN configuration is complete but there is one thing left to do. Let’s configure EIGRP so that our routers can reach the networks where the hosts are:
R1(config)#router eigrp 1
R1(config-router)#no auto-summary
R1(config-router)#network 1.1.1.1 0.0.0.0
R1(config-router)#network 192.168.1.0 0.0.0.255The first network command activates EIGRP on the virtual access interface. We use IP unnumbered which takes the IP address from the loopback interface (1.1.1.1).
Spoke routers
The spoke routers will have a slightly different configuration.
R2
We only need to specify the pre-shared key for the hub. Let’s use the crypto isakmp key command for this:
R2(config)#crypto isakmp key R1_R2 address 192.168.123.1Let’s create a phase 1 policy:
R2(config)#crypto isakmp policy 1
R2(config-isakmp)#encryption aes
R2(config-isakmp)#hash sha
R2(config-isakmp)#group 5
R2(config-isakmp)#authentication pre-share And the phase 2 policy:
R2(config)#crypto ipsec transform-set TRANSFORM_SET esp-aes esp-sha-hmac
R2(cfg-crypto-trans)#mode tunnelWe create an IPSec profile and link the transform set to the profile:



Hi Rene,
Hopefully, you are fine…Beside study everyday I am checking your new lesson and forum as well, After taken membership i am able to see you are continually adding new lessons in CCIE Routing & Switching Written like:
- IPSec VTI Virtual Tunnel Interface April 2018
- BGP PIC (Prefix Independent Convergence) Core & Edge March 2018
- BGP Multipath load sharing iBGP and eBGP March 2018
- BGP Aggregate AS-SET March 2018
- IPv6 RA Guard March 2018
- IPv6 over MPLS 6PE/6VPE March 2018
- IPv6 DHCPv6 Prefix Delegation February 2018
- Multicast Tunnel RPF Failure February 2018
... Continue reading in our forumHi Arindom,
There was a small list of CCIE R&S written topics that I still didn’t have so right now, I’m working on completing those Just a few more and then the written course is 100% according to the blueprint.
Just a few more and then the written course is 100% according to the blueprint.
Rene
Hi Rene,
Thanks for replying..
Yes yes sure All the best Rene:+1: we believe your lesson will be best for CCIE technology learning,I will take your CCIE lession as well.but due to some financial problem its not effortable for me to take annual membership but i will continue with monthly membership.
Thanks & Regards,
Arindom
Isn’t IPSec tunnel mode not supporting multicast?
How does EIGRP establishes neighborship within these routers?
Hello Ray
It is true that IPsec alone does not support multicast. However, if you want to create an EIGRP neighbourship over IPsec, you must run a GRE tunnel in conjunction with IPsec. GRE supports multicast so this would solve the problem.
Another option is to use an EIGRP static neighbour. This automatically makes EIGRP use only unicast for communication between neighbours.
I hope this has been helpful!
Laz