IS-IS routers in a level 1 area only know the prefixes in their own area. If they want to reach something in another area, they have to use a default route to a level 1-2 router. If there are multiple level 1-2 routers, then IS-IS picks the closest level 1-2 router to exit the area. This sometimes causes sub-optimal routing.
We can deal with this by leaking prefixes from level 2 into level 1.
A level 1-2 router has access to the local area and also knows all prefixes because of its level 2 database. We can redistribute one or more prefixes from level 2 into the local area so that level 1 routers can select the most optimal path in the network.
This is best explained with an example, so in this lesson, I’ll show you what route leaking is and how it solves sub-optimal routing. This is the topology we will use:
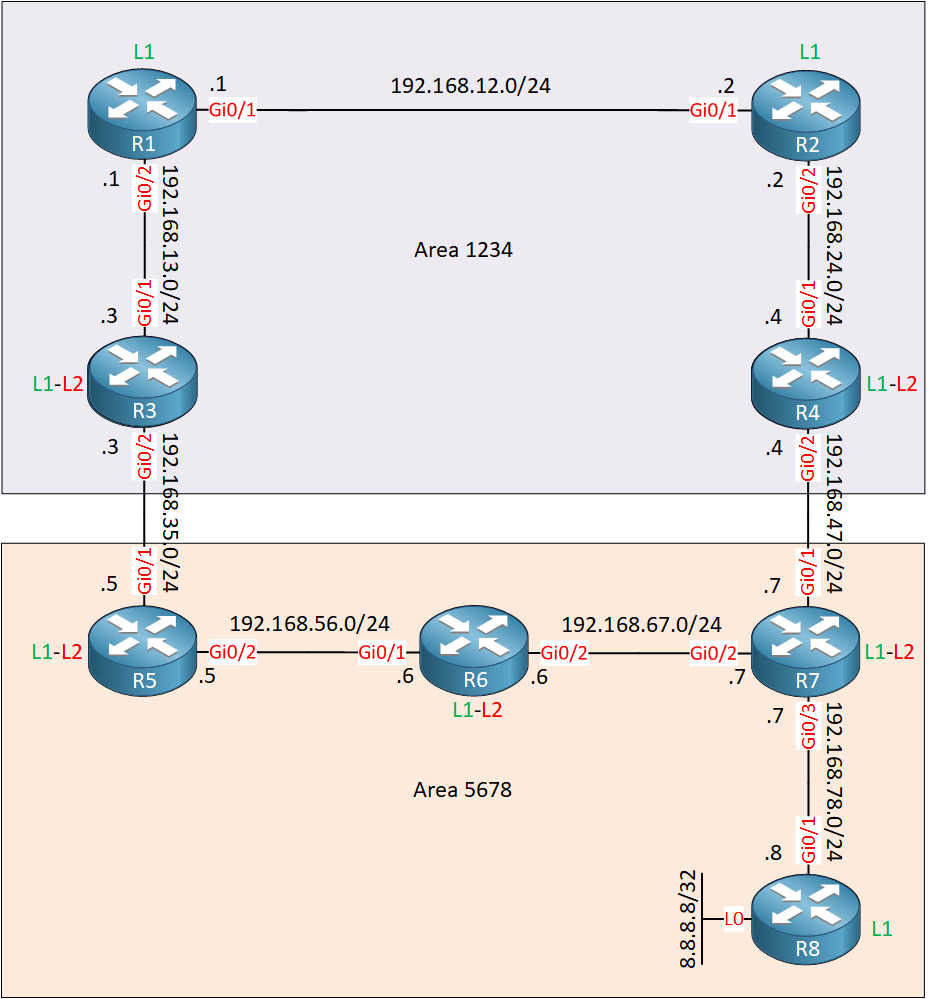
We have a bunch of IS-IS routers. R8 has a loopback interface that we will try to reach from R1. All interfaces are Gigabit Ethernet with the default metric of 10.
Configurations
Want to take a look for yourself? Here you will find the startup configuration of each device.
R1
hostname R1
!
ip cef
!
interface GigabitEthernet0/1
ip address 192.168.12.1 255.255.255.0
ip router isis
!
interface GigabitEthernet0/2
ip address 192.168.13.1 255.255.255.0
ip router isis
!
router isis
net 49.1234.0000.0000.0001.00
log-adjacency-changes
!
endR2
hostname R2
!
ip cef
!
interface GigabitEthernet0/1
ip address 192.168.12.2 255.255.255.0
ip router isis
!
interface GigabitEthernet0/2
ip address 192.168.24.2 255.255.255.0
ip router isis
!
router isis
net 49.1234.0000.0000.0002.00
is-type level-1
log-adjacency-changes
!
endR3
hostname R3
!
ip cef
!
interface GigabitEthernet0/1
ip address 192.168.13.3 255.255.255.0
ip router isis
!
interface GigabitEthernet0/2
ip address 192.168.35.3 255.255.255.0
ip router isis
!
router isis
net 49.1234.0000.0000.0003.00
log-adjacency-changes
!
endR4
hostname R4
!
ip cef
!
interface GigabitEthernet0/1
ip address 192.168.24.4 255.255.255.0
ip router isis
!
interface GigabitEthernet0/2
ip address 192.168.47.4 255.255.255.0
ip router isis
!
router isis
net 49.1234.0000.0000.0004.00
log-adjacency-changes
!
endR5
hostname R5
!
ip cef
!
interface GigabitEthernet0/1
ip address 192.168.35.5 255.255.255.0
ip router isis
!
interface GigabitEthernet0/2
ip address 192.168.56.5 255.255.255.0
ip router isis
!
router isis
net 49.5678.0000.0000.0005.00
log-adjacency-changes
!
endR6
hostname R6
!
ip cef
!
interface GigabitEthernet0/1
ip address 192.168.56.6 255.255.255.0
ip router isis
!
interface GigabitEthernet0/2
ip address 192.168.67.6 255.255.255.0
ip router isis
!
router isis
net 49.5678.0000.0000.0006.00
log-adjacency-changes
!
endR7
hostname R7
!
ip cef
!
interface GigabitEthernet0/1
ip address 192.168.47.7 255.255.255.0
ip router isis
!
interface GigabitEthernet0/2
ip address 192.168.67.7 255.255.255.0
ip router isis
!
interface GigabitEthernet0/3
ip address 192.168.78.7 255.255.255.0
ip router isis
!
router isis
net 49.5678.0000.0000.0007.00
log-adjacency-changes
!
endR8
hostname R8
!
ip cef
!
interface Loopback0
ip address 8.8.8.8 255.255.255.255
ip router isis
!
interface GigabitEthernet0/1
ip address 192.168.78.8 255.255.255.0
ip router isis
!
router isis
net 49.5678.0000.0000.0008.00
is-type level-1
log-adjacency-changes
!
endLet’s take a look at the routing table of R1:
R1#show ip route isis
i*L1 0.0.0.0/0 [115/10] via 192.168.13.3, 00:04:01, GigabitEthernet0/2
i L1 192.168.24.0/24 [115/20] via 192.168.12.2, 00:04:21, GigabitEthernet0/1
i L1 192.168.35.0/24 [115/20] via 192.168.13.3, 00:04:11, GigabitEthernet0/2
i L1 192.168.47.0/24 [115/30] via 192.168.12.2, 00:04:11, GigabitEthernet0/1R3 is the closest level 1-2 router for R1 so R1 generates a default route to R3. When we try to reach 8.8.8.8, this is the path we use:
R1#traceroute 8.8.8.8
Type escape sequence to abort.
Tracing the route to 8.8.8.8
VRF info: (vrf in name/id, vrf out name/id)
1 192.168.13.3 5 msec 10 msec 5 msec
2 192.168.35.5 7 msec 11 msec 7 msec
3 192.168.56.6 11 msec 13 msec 16 msec
4 192.168.67.7 11 msec 16 msec 11 msec
5 192.168.78.8 12 msec 10 msec *R1 uses R3 to get to 8.8.8.8. This makes sense since R3 is the closest level 1-2 router.To reach any networks outside of area 1234, R1 will use the default route from R3. It’s not the shortest path however since R6 is in between R5 and R7:
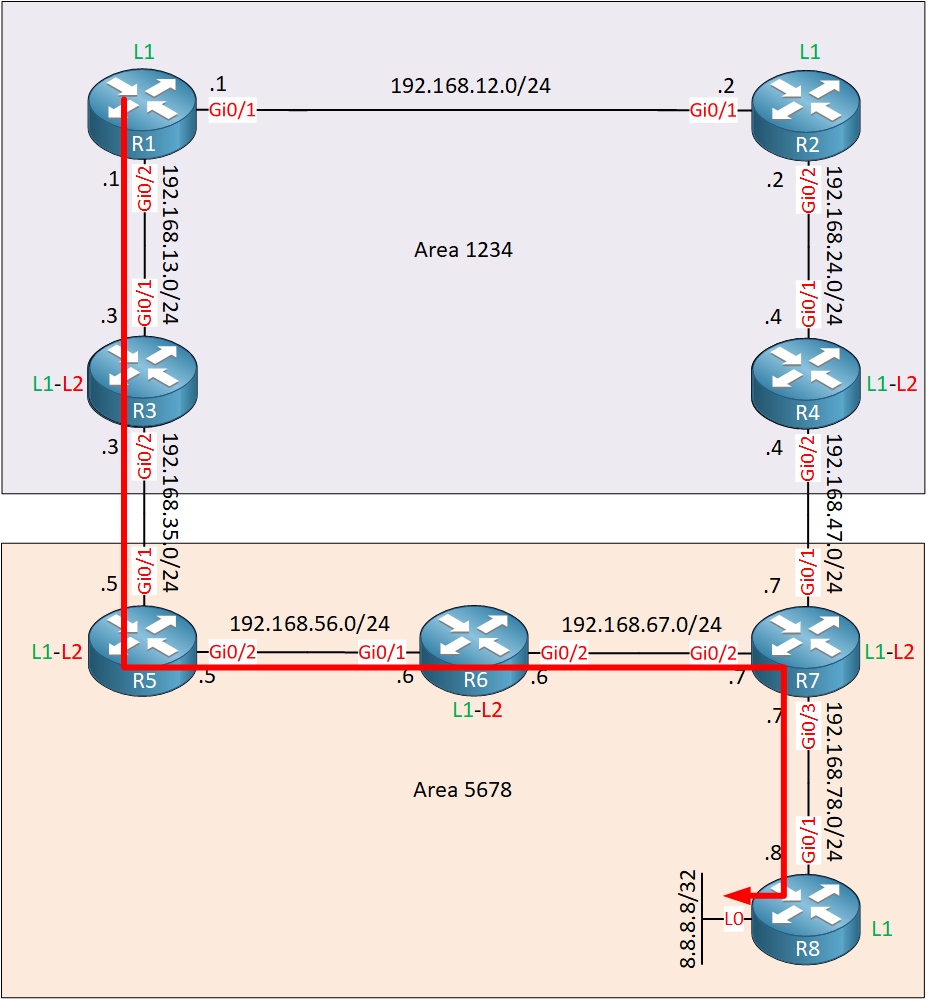
We can solve this by leaking information about 8.8.8.8/32 into area 1234. When R1 learns about 8.8.8.8/32, it will no longer use the default route to reach this network.
On R4, we’ll configure route leaking. You can use a distribute-list or a route-map to select the networks you want to leak. I’ll use a route-map since it allows you to use named access-lists. First, we create an access-list that matches 8.8.8.8/32:
R4(config)#ip access-list extended R8_L0
R4(config-ext-nacl)#permit ip host 8.8.8.8 anyAnd then we create a route-map that matches the access-list we just created:
R4(config)#route-map ROUTE_LEAKING permit 10
R4(config-route-map)#match ip address R8_L0Now we can configure route leaking with the redistribute command:
R4(config)#router isis
R4(config-router)#redistribute isis ip level-2 into level-1 route-map ROUTE_LEAKINGThe command above tells R4 to leak level 2 prefixes into level 1 but only those that are configured in the route-map. Let’s take a look at R1:
R1#show ip route isis
i*L1 0.0.0.0/0 [115/10] via 192.168.13.3, 00:16:05, GigabitEthernet0/2
8.0.0.0/32 is subnetted, 1 subnets
i ia 8.8.8.8 [115/50] via 192.168.12.2, 00:00:41, GigabitEthernet0/1
i L1 192.168.24.0/24 [115/20] via 192.168.12.2, 00:16:28, GigabitEthernet0/1
i L1 192.168.35.0/24 [115/20] via 192.168.13.3, 00:16:28, GigabitEthernet0/2
i L1 192.168.47.0/24 [115/30] via 192.168.12.2, 00:16:28, GigabitEthernet0/1Above we see an IS-IS “ia” (interarea) route for 8.8.8.8/32 via R2. This is the leaked route. We can also see it in the level 1 link-state database:
R1#show isis database level-1 verbose R4.00-00
IS-IS Level-1 LSP R4.00-00
LSPID LSP Seq Num LSP Checksum LSP Holdtime ATT/P/OL
R4.00-00 0x00000005 0xC9D0 1099 1/0/0
Area Address: 49.1234
NLPID: 0xCC
Hostname: R4
Metric: 10 IS R4.01
IP Address: 192.168.47.4
Metric: 10 IP 192.168.24.0 255.255.255.0
Metric: 10 IP 192.168.47.0 255.255.255.0
Metric: 30 IP-Interarea 8.8.8.8 255.255.255.255Above we see the interarea route that was leaked into level 1. With this specific entry, R1 will use the most optimal path to reach 8.8.8.8:
R1#traceroute 8.8.8.8
Type escape sequence to abort.
Tracing the route to 8.8.8.8
VRF info: (vrf in name/id, vrf out name/id)
1 192.168.12.2 10 msec 4 msec 6 msec
2 192.168.24.4 5 msec 7 msec 7 msec
3 192.168.47.7 9 msec 10 msec 10 msec
4 192.168.78.8 7 msec 19 msec *This is looking good. We now use R2 to get to our destination:
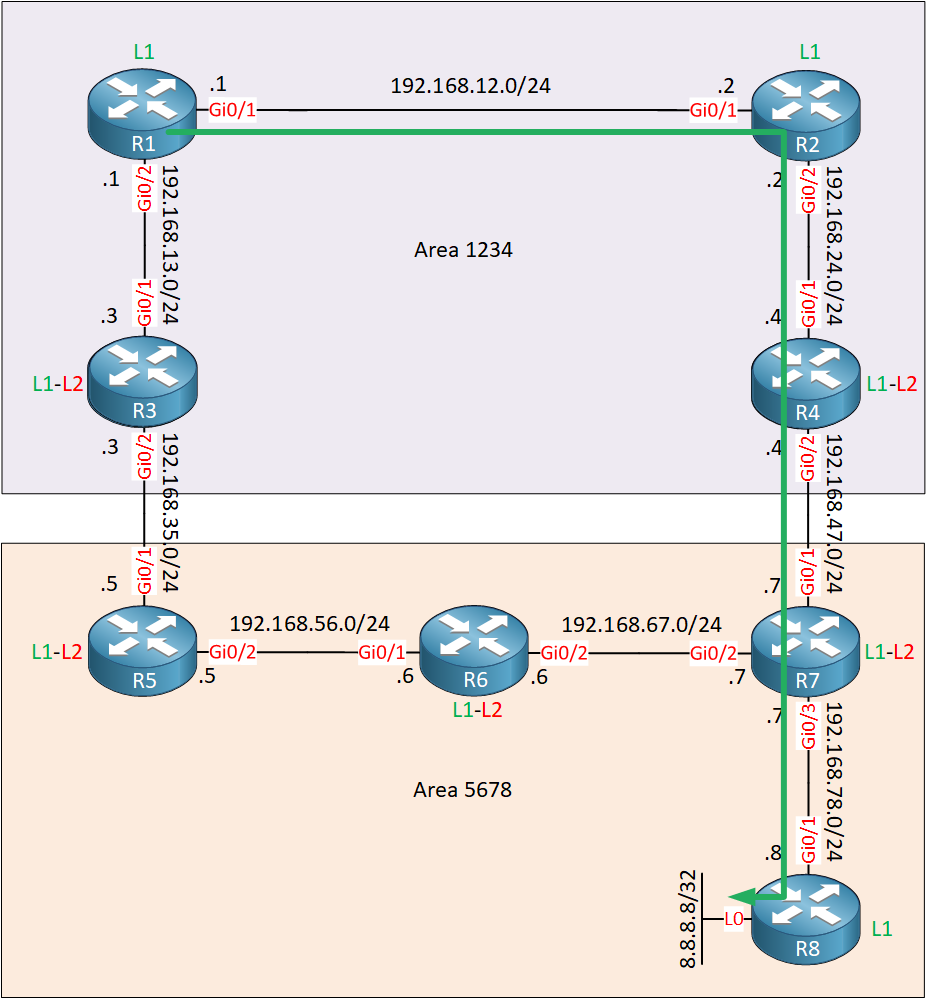
The last thing we need to discuss are routing loops. R4 redistributes 8.8.8.8/32 into area 1234 so R3 will also learn this prefix from R1.
What prevents R3 from redistributing 8.8.8.8/32 back into the level 2 database? When a prefix is redistributed like this, the router that does the redistribution will set the distribution up/down bit. For example, here’s the level 1 LSP from R4:
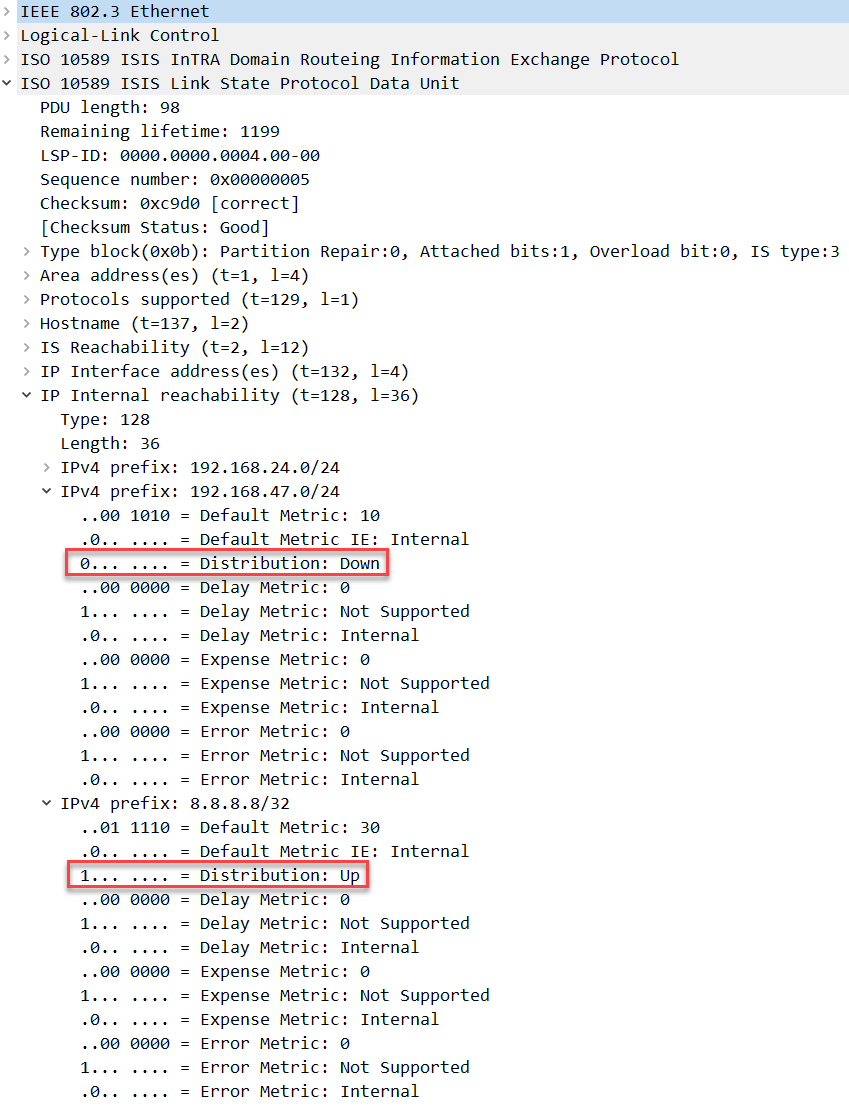
Packet Capture: IS-IS Route Leaking Down Bit
Above we see that R4 is advertising 192.168.24.0/24, 192.168.47.0/24 and 8.8.8.8/32 in its level 1 LSP. For 8.8.8.8/32 it has set the distribution bit to 1 (up). Another level 1-2 router like R3 will never redistribute this back into the level 2 database.
Configurations
Want to take a look for yourself? Here you will find the final configuration of each device.


Hi Rene,
thanks a lot for your helpful explanation, I simulated your lab and found something that I need your explanation for it.
when I leaked 8.8.8.8 at R4, R2 calculated the metric of 8.8.8.8 with 168 as below:
although R4 calculated it with 30 :
the metric calculated with 40 at R2 when I configured the
... Continue reading in our forumHi Walid,
That’s a good question. I just booted this topology again and I see a metric of 40 on R2:
... Continue reading in our forumHi Rene,
this command result:
R1 uses R3
Why do you write:
R1 uses R2
Hi Rene
why we will configure on R4 , not on R2 , is there a reason or first level-1-2 router
Hi Bahri,
Thanks, this is a typo yes. Just fixed it.
Rene