Spanning tree BPDU guard is one of the features that helps you protect your spanning tree topology. Let me give you an example:
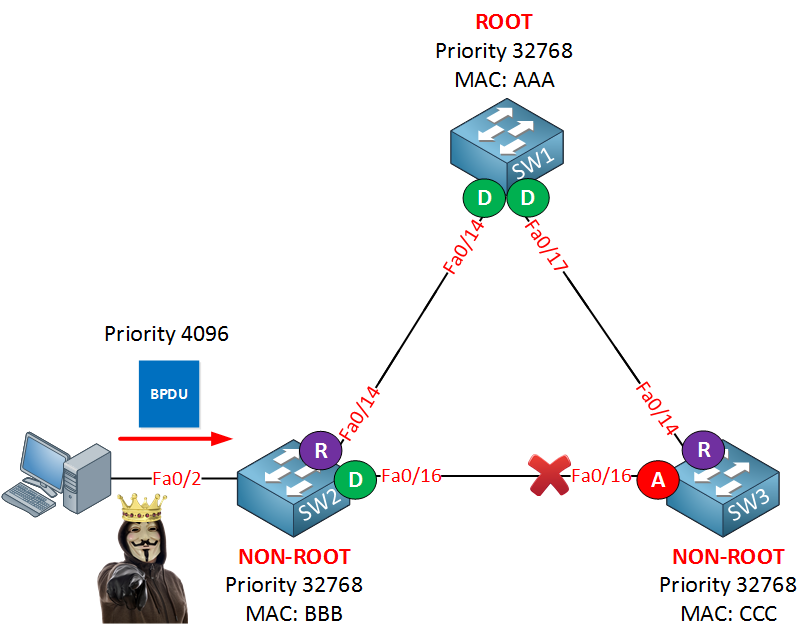
In my topology above, we have a perfectly working spanning tree topology. By default spanning tree will send and receive BPDUs on all interfaces. In our example, we have a computer on the fa0/2 interface of SW2. Someone with curious, hostile intentions could start a tool that generates BPDUs with a superior bridge ID. What’ll happen is that our switches will believe that the root bridge can now be reached through SW2, and we’ll have a spanning tree re-calculation. That doesn’t sound like a good idea, right? Here’s what could go wrong:
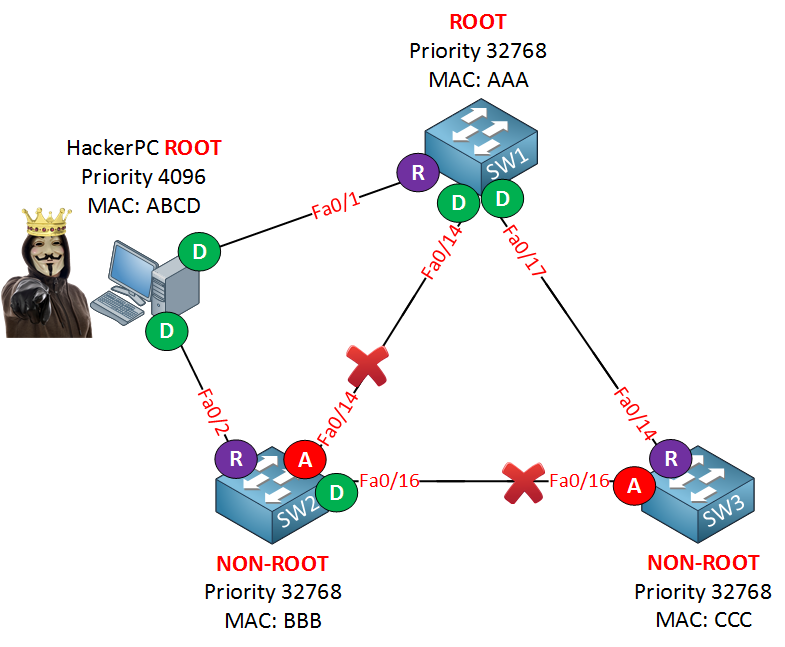
You could even do a man-in-the-middle attack without anyone knowing. Imagine I connect my computer to two switches. If I become the root bridge, all traffic from SW1 or SW3 towards SW2 will flow through me. I’ll run Wireshark and wait till the magic happens.
We can use BPDU Guard to prevent this from happening as it will block BPDUs:
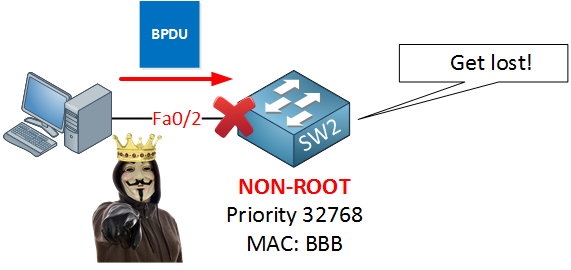
BPDU guard will ensure that when we receive a BPDU on an interface, the interface will go into err-disable mode.
Let’s take a look at how to configure this…



awesome explaination Renee .
I really enjoy reading your topics and make me feel more confortable and confident when I learn it
thanks
Good stuffs!
Hi Rene,
I am more curious if STP will send BPDUs on Access ports enabled with Portfast or this will be out of the STP topology, Let be more specific with my query
In case i have 2 SWs running RSTP a third SW is introduced which happens to be not supporting STP and is connected to my 2 Sws with portfast enabled
In case BPDUs is being sent on portfast then i assume BPDUGuard will save the day for me on the 2nd SW as it will shut down the port once it receives BPDU on its access port, Is this correct?
Hi Ahmed,
Enabling portfast doesn’t disable STP and the interface will still send BPDUs. Take a look at this post:
https://networklessons.com/spanning-tree/does-portfast-disable-spanning-tree
In your example, you shouldn’t enable portfast on interfaces that connect to other switches. Only use this for “end” devices like computers, laptops, servers, etc. In your case, BPDUguard will ensure that the interface will go down.
Mixing PVST and rapid PVST is no problem btw, they are compatible.
Rene
Thanks Rene, The point here is usually you don’t know the end host capability, I saw cases loop can happen from a server with NIC bridging without STP capability.
Just wanted to make sure Portfast + BPDUGuard can address this case