Lesson Contents
EIGRP OTP (Over the Top) allows you to run EIGRP between routers that are not directly connected. It is a great feature to use when you want to run EIGRP between routers that are connected to a service provider network and you don’t want the hassle of other solutions like MPLS VPN and you don’t want the service provider’s involvement with your routing. With EIGRP OTP, you can configure everything on your own routers as long as you are able to reach the remote router(s).
EIGRP OTP uses an overlay VPN and thus uses tunneling, it is a bit similar to other solutions like DMVPN / multipoint GRE but it uses LISP (Locator/Identifier Separation Protocol) instead.
LISP is a technology where each end device has a separate “identity” and “location”, unlike IP where the IP address is both the identity and location of the end device. LISP is useful in scenarios where an end device should be able to retain its original IP address, even if it moves to another subnet. It is useful for VM motion where virtual machines are moved from one hypervisor to another but also for mobile devices that end up in another subnet after roaming.
There is a control plane and data plane for LISP. Learning all the details about the LISP control plane is quite a story. On the data plane, LISP uses UDP to encapsulate data and tunnel traffic. EIGRP OTP only uses LISP for the data plane, EIGRP is used for the control plane. This is convenient as you don’t really have to understand LISP to be able to understand EIGRP OTP.
In this lesson, I’ll show you how to configure EIGRP OTP.
Configuration
To demonstrate EIGRP OTP, I use the following topology:
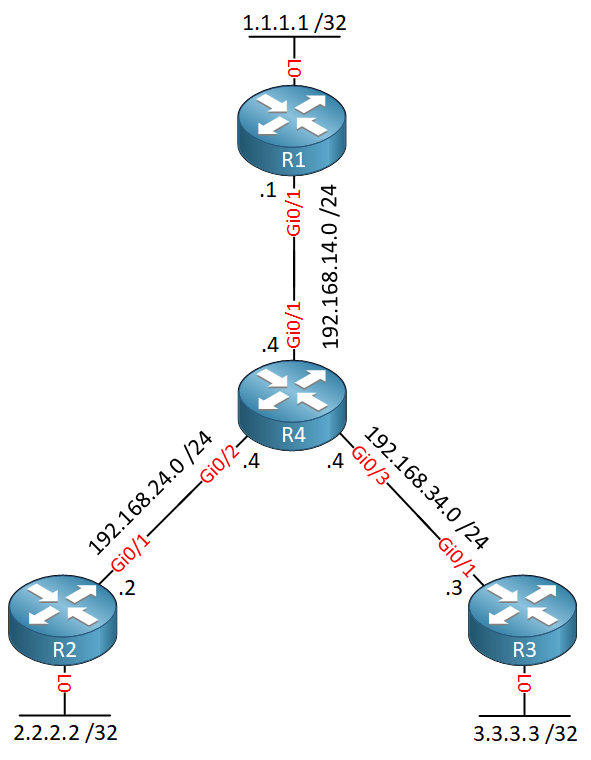
Above we have four routers:
- R1, R2 and R3 are customer routers that want to use EIGRP to exchange routing information. These routers each have a loopback interface with an IP address that we will advertise in EIGRP.
- R4 is the service provider network. In a production network, this could be a large network but for simplicity reasons, I’m only using one router here.
The only requirement to run EIGRP OTP is that the customer routers have to be able to reach each other. I will use a couple of static routes so that R1, R2 and R3 are able to reach the IP addresses on their GigabitEthernet 0/1 interfaces:
R1(config)#ip route 192.168.24.2 255.255.255.255 192.168.14.4
R1(config)#ip route 192.168.34.3 255.255.255.255 192.168.14.4R2(config)#ip route 192.168.14.1 255.255.255.255 192.168.24.4
R2(config)#ip route 192.168.34.3 255.255.255.255 192.168.24.4R3(config)#ip route 192.168.14.1 255.255.255.255 192.168.34.4
R3(config)#ip route 192.168.24.2 255.255.255.255 192.168.34.4Now we can configure EIGRP.
Route Reflector
EIGRP OTP is only supported in EIGRP named mode, you can’t configure it in classic mode. Neighbors have to be configured statically and we have two options here:
- We can configure a full-mesh of static EIGRP neighbors.
- We can configure one router as a route reflector which works similar to the BGP route reflector.
With three routers, a full mesh is no problem but if you have a lot of customer routers, a route reflector is an interesting option. I will configure R1 as the route reflector and R2/R3 will be its clients:
R1(config)#router eigrp OTP
R1(config-router)#address-family ipv4 autonomous-system 123
R1(config-router-af)#remote-neighbors source GigabitEthernet 0/1 unicast-listen lisp-encap 123The remote-neighbors command is all we need for EIGRP OTP. It tells R1 to use the GigabitEthernet 0/1 interface and listen for unicast packets. LISP uses different IDs, I’m going to use ID 123 on all routers. Optionally, this command allows you to set a maximum number of neighbors and/or use an access-list to permit only certain IP addresses to accept as EIGRP neighbors.
Let’s advertise the loopback interface and GigabitEthernet 0/1 on R1:
R1(config-router-af)#network 1.1.1.1 0.0.0.0
R1(config-router-af)#network 192.168.14.0 0.0.0.255Last but not least, there are two more things we have to configure:
- Disable next-hop-self: If you don’t do this, R1 will set its own IP address as the next hop for everything it advertises to R2 and R3. If you don’t disable this, then whenever R2 or R3 want to reach each other’s loopback interface, they will send their traffic to R1. It works but it’s sub-optimal routing. If you disable this then R1 will leave the next hop IP address alone and R2/R3 are able to reach each other directly.
- Disable split horizon: R1 is using a single interface so if you don’t disable split horizon, R2 and R3 are unable to learn each others loopback interfaces.
Let’s disable next-hop-self and split horizon:
R1(config-router-af)#af-interface GigabitEthernet 0/1
R1(config-router-af-interface)#no next-hop-self
R1(config-router-af-interface)#no split-horizon That’s all we have to do on the route reflector.
Spoke routers
Let’s configure R2 and R3. The only thing we have to do is configure R1 as a static remote neighbor and set the LISP encapsulation ID:



Hi Rene
The official documentation states the following:
https://www.cisco.com/c/en/us/products/ios-nx-os-software/locator-id-separation-protocol-lisp/index.html
However in your capture it shows 4343? Can you explain that one?
Hello Chris
Thanks for catching that, that’s great. Looking further into the issue, it is the case that UDP port 4342 is used by LISP, while 4343 is used by something called Unicall. I wasn’t able to find more information about Unitcall, however, there is extensive Cisco documentation that mentions that EIGRP OTP uses port 4343 and not 4342 for LISP. Extensive decodes and captures of exchange packets repeatedly indicate the use of 4343 in this related Cisco documentation concerning OTP architecture. (search for 4343). Additionally, unicall is mentioned as t
... Continue reading in our forumLike @lagapidis, I tried to figure this out but I can’t find anything why they used UDP 4343. The official LISP ports that were assigned by IANA are 4341 and 4342. I guess they wanted to stay away from those two for EIGRP OTP, which is why they used 4343 instead.
Unicall seems to be an old protocol:
https://www.soft-switch.org/unicall/mfcr2/ch01.html
So there’s probably no harm using UDP 4343 instead.
Hello Team,
I try EIGRP OTP + IPSEC on a customer Network and it work well
Can I use EIGRP OTP instead of DMVPN ?
Cordially
Hello Fabrice,
This mostly depends on your transport network. If you use the Internet, you need to use something like DMVPN since you need to encapsulate your private traffic.
If you have a private network and routing works between your endpoints, you can use EIGRP OTP or GETVPN.
Rene