Lesson Contents
Wireless networks are complex; there are many technologies and protocols required to offer a stable wireless network to end-users. It also sounds scary to transmit data through the air, where everyone can listen to it.
Wired networks feel secure; after all, you can’t easily listen to this traffic. You could connect to a switchport, but the only unicast traffic you’ll see is the traffic between your computer and the switch. You will see multicast and broadcast traffic from within the VLAN, though.
Anyone can see the data that travels through the air, which is why wireless security is so important. Someone can monitor wireless traffic, and you won’t even notice that it’s happening.
In the 802.11 service sets lesson, you learned how wireless clients associate with APs. All wireless traffic has to go through the AP, instead of directly between the sender and receiver. Anyone in range of the AP or other wireless clients can receive the signal.
This can be a problem. For example, imagine we have a user who sends a password to a remote server:
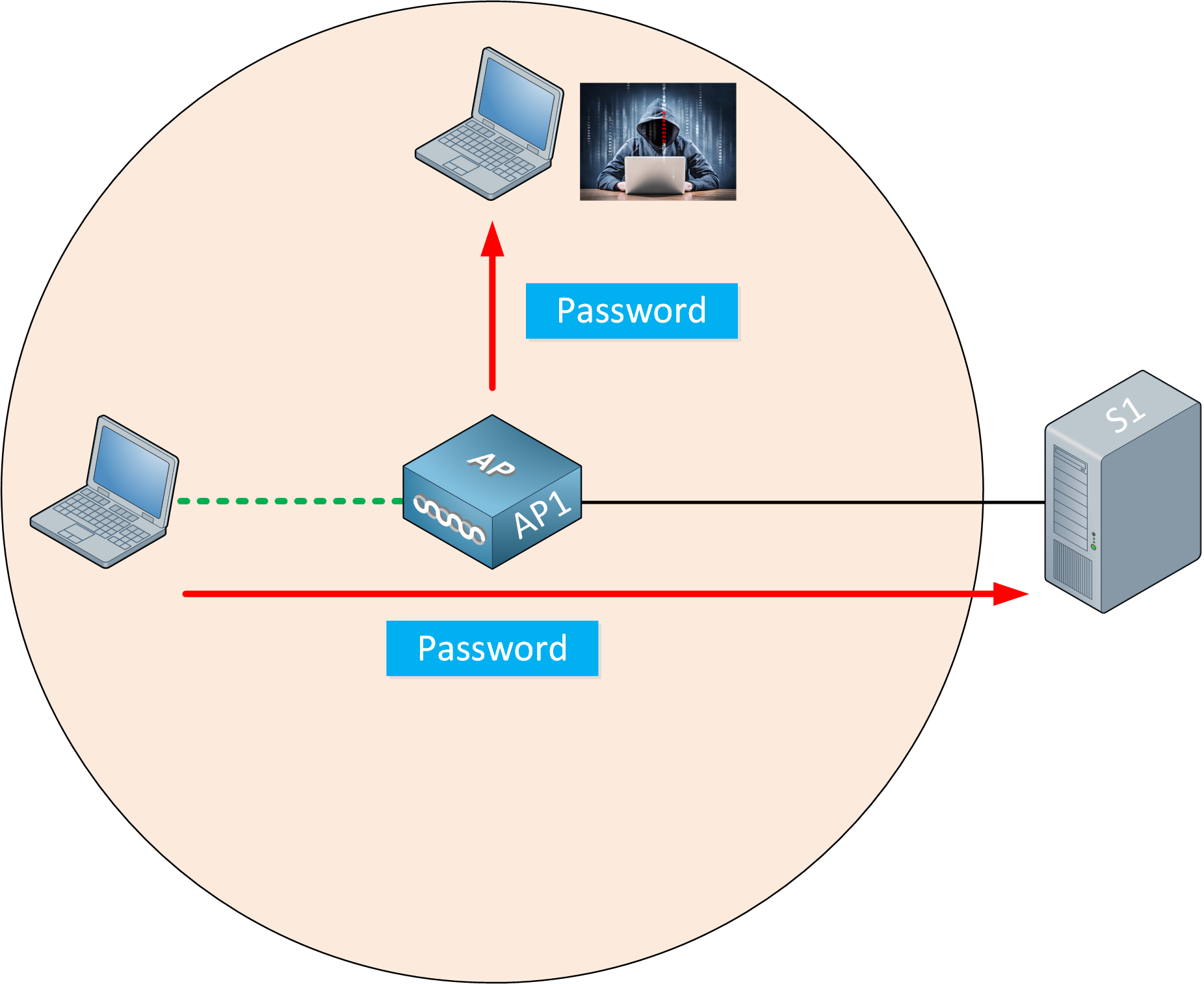
The wireless user transmits a password to the remote server. Because the attacker is in range of our wireless network, he can capture the password.
How can we securely transmit data through the air and ensure that it remains private and is not tampered with? The 802.11 standard offers security mechanisms that provide authentication, encryption, and integrity. In this lesson, I’ll give you an overview of these three items.
Authentication
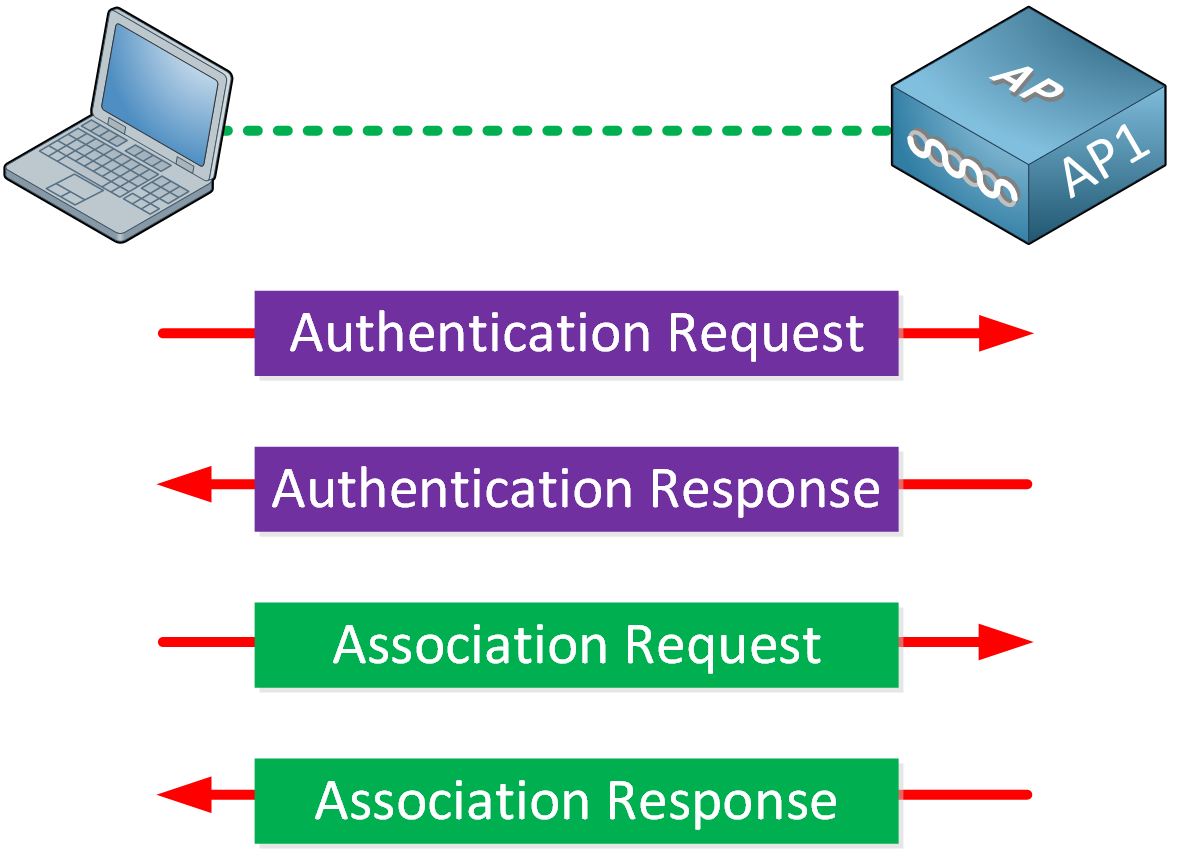
To use a wireless network, the wireless client has to discover a BSS. APs advertise beacons with their SSID, and the wireless client selects the wireless network she wants to connect to and associates with the AP. By default, authentication is open, which means everyone is welcome.
You probably want to authenticate your wireless clients, though. If you have a corporate network, you don’t want just anyone to join the network. Only legitimate users should be able to use your wireless network. After all, the wireless network might be connected to the wired network where you can access all corporate resources.
What if you have guest users? If you want to offer a guest wireless network, you should configure a second SSID, linked to a VLAN with restricted access.
APs can authenticate wireless clients before they associate with the AP. This keeps rogue clients away from our wireless network.
There are many options for wireless authentication. You are probably familiar with the most common choice, a pre-shared key. We configure the pre-shared key on the AP. Any wireless client that wants to join the wireless network has to enter the pre-shared key.
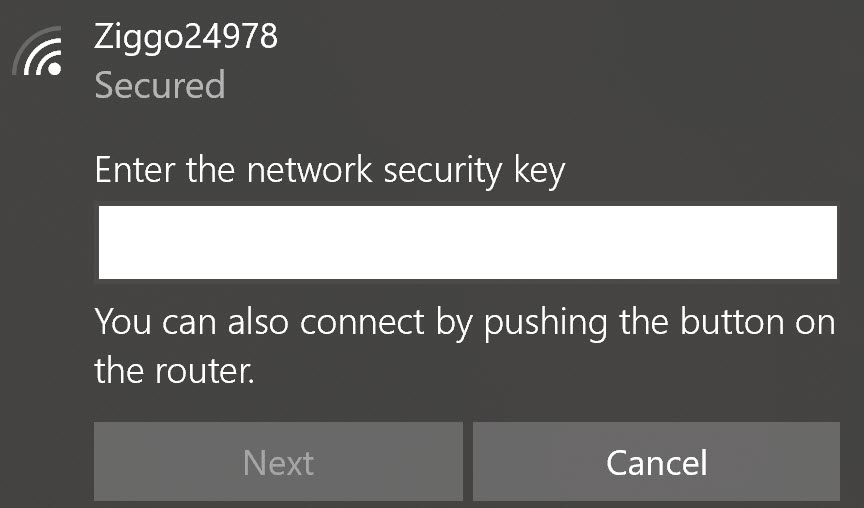
What happens when someone steals one of the wireless clients? That’s a problem because of two main reasons:
- The attacker has access to your pre-shared key:
- And can now connect to the wireless network from any device.
- And can decrypt traffic from other clients connected to the same wireless network.
- You need to configure a new pre-shared key on the AP and all wireless clients.
There are stronger authentication options where we ask users for a username and password instead. This helps. When a device is stolen, at least you can pinpoint which username was compromised and reset the password for that username. You don’t have to reset the pre-shared key and configure it on all wireless clients.



Hi, I really enjoy the lessons.
I have two related questions, please.
In the lesson, you said
So that’s mean the attacker can’t make a certificate for its rogue AP? or it’s possible but difficult to make?
Who originate these certificates? is it the 802.11 standard or the Manufacture of the AP? In other words, where do these certificates come from?
I appreciate your effort.
Hello Ameen
Certificates are a widely used method for authentication in a very broad area of application. Some examples include:
A certificate, or digital certificate, or more correctly referred to as a public key certificate, is a method used to prove the ownership of a public key. A digital certificate includes information about the key, information about the identity of its owner, as well as the digital signature of the entity that has verified the certificate’s
... Continue reading in our forumThanks a lot, Mr. Lazaros.
Guys, the lesson is great, but I would like to suggest two improvements:
1 - Add the “full wireless handshake”
In this image here, you share the phases “Authentication” and “Association”. But I think you should introduce the “Beacon” and “Probe” phases as well, and quickly introduce them, just like here. I’m following the CCNA 200-301 course and, at this point, beacon and probes were not introduced yet. Adding all the phases will make easier for the student to understand exactly where/when the authentication phase occurs.
2 - Improve wording
... Continue reading in our forumHello Rarylson
Thanks for your feedback! I’ll let @ReneMolenaar know to take a look and consider your suggestions.
Laz