In this lesson we’ll take a look at some of the basics of Cisco Campus network design.
What is a “campus” network anyway?
A campus network is an enterprise network (hundreds or thousands of users) where we have one or more LANs in one or multiple buildings. Everything is geographically close to each other so we typically use Ethernet (and Wireless) for connectivity. Typically the company owns everything on the campus…hardware, cabling, etc.
To support this many users we require a lot of switchports which means a lot of switches. We need a physical design to connect these switches to each other and also a good logical design to make it work.
Let’s take a look at some networks to see how they “grow” and some design issues that we will face. Let’s start with a simple example:
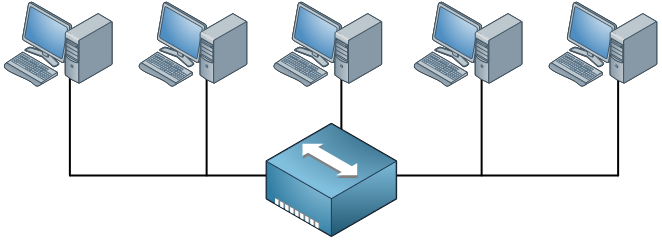 Back in the old days we used to have hubs so we had half-duplex networks. When one host would transmit something, the others had to wait. When two hosts would send at the same time we’d get a collision and we used the CSMA/CD algorithm to deal with these collisions. Everything that is connected to the hub is a single collision domain. Also, whenever a host sends a broadcast everyone will receive it. There’s only one broadcast domain.
Back in the old days we used to have hubs so we had half-duplex networks. When one host would transmit something, the others had to wait. When two hosts would send at the same time we’d get a collision and we used the CSMA/CD algorithm to deal with these collisions. Everything that is connected to the hub is a single collision domain. Also, whenever a host sends a broadcast everyone will receive it. There’s only one broadcast domain.
In this example there are only 5 hosts so it’s no problem but when you have hundreds of hosts the collisions and broadcasts will have a serious impact on the available bandwidth. To reduce the size of the collision domain we started using bridges and then switches. The broadcast domains can be reduced by using VLANs. Here’s an example:
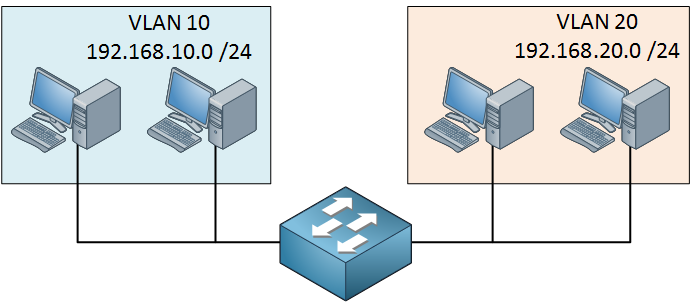
Now we have a single switch and some hosts that are in different VLANs. Each port on the switch is a collision domain and each VLAN is a separate broadcast domain. If we use a multilayer switch, the VLANs will be able to communicate with each other.
Once this network grows we might not have enough switchports anymore on a single switch. You could add a second switch and connect it to the first one but what if we add a third of fourth switch? How are we going to connect them to each other?
If you don’t think about your design beforehand, you might end up with something like this:
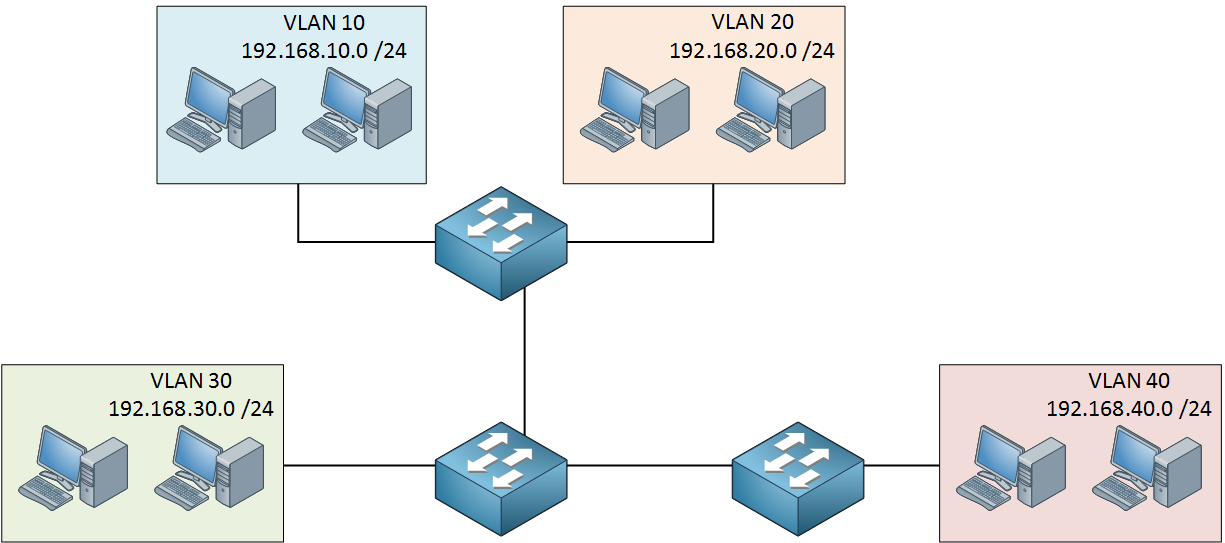
Switches, hosts, cables and VLANs everywhere. Before we know it, the network is one big spaghetti.
We need a network that is easy to maintain, offers high availability, scalability and is able to quickly respond to changes in the topology. To achieve all of this, Cisco has a hierarchical approach to network design where we have multiple layers in the network. Here’s an example:
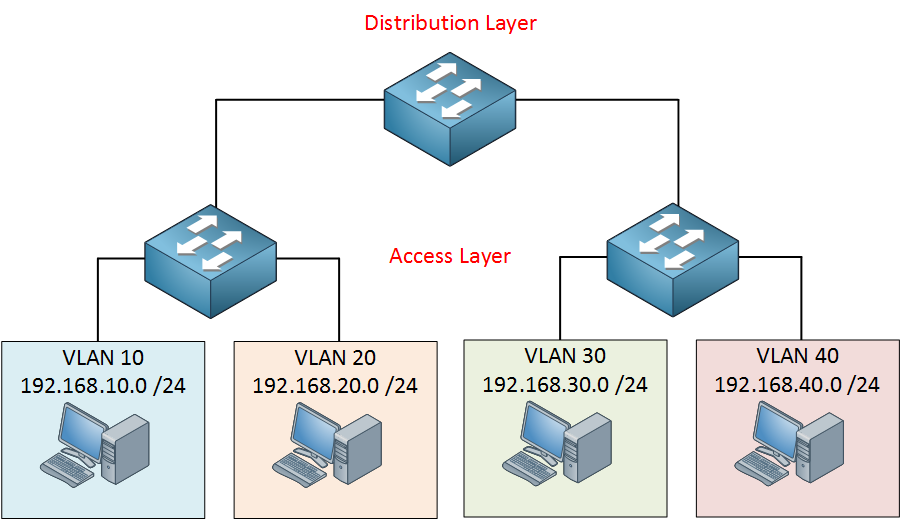
In this design we have an access layer and distribution layer. The access layer is close to the end users, these are switches that we use to connect computers, laptops, access points and more. The distribution layer is used to aggregate all the different access layer switches.
The advantage of this hierarchical network design is that it’s scalable. When the campus grows and we get more users, building and floors then we can add multiple distribution layers. When this happens, we’ll add another layer:
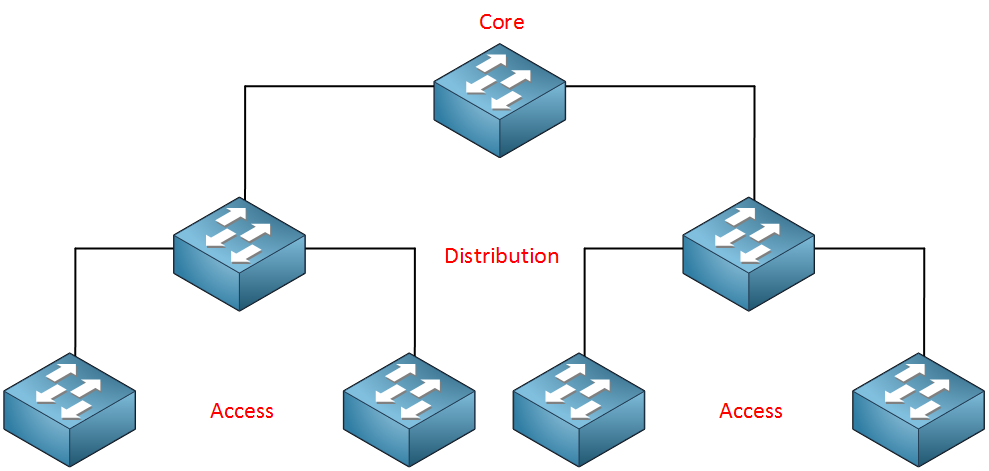
The core layer aggregates all the different distribution layer switches. This design also makes our traffic paths predictable and easy to visualize. Basically there are three different traffic flows:
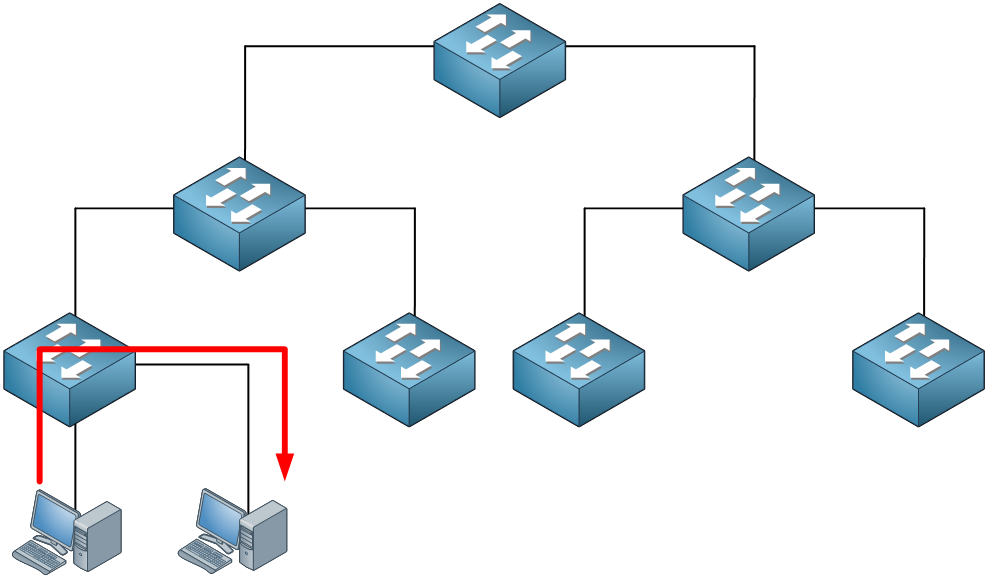
All traffic starts at the access layer and if needed it will move up the distribution and core layer. In this example the traffic is local; it doesn’t leave the access layer switch. This could be traffic between two hosts within the same VLAN. Here’s another example:
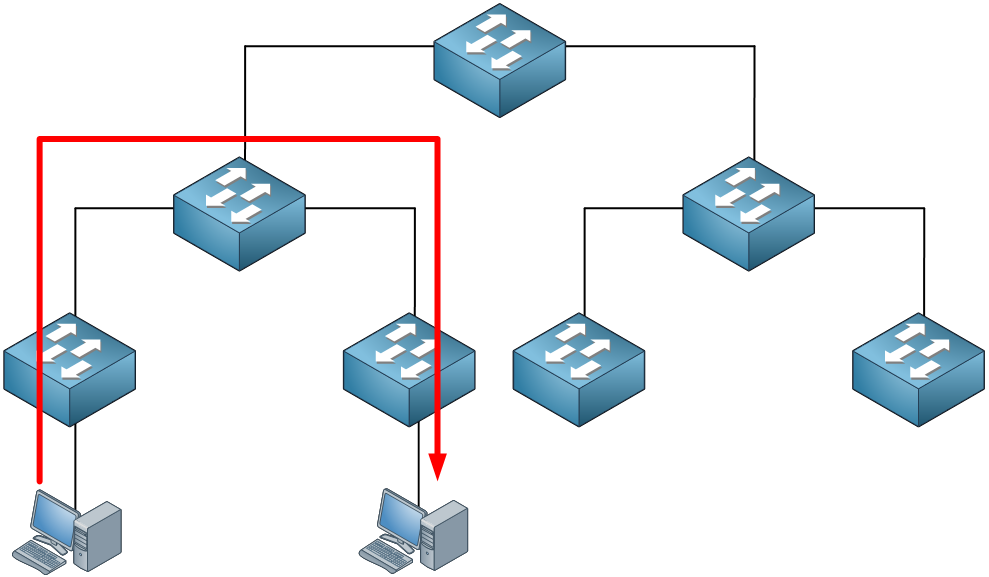
Traffic between hosts that are on different access layer switches has to cross the distribution layer switch. Finally, sometimes we have to cross the core layer:
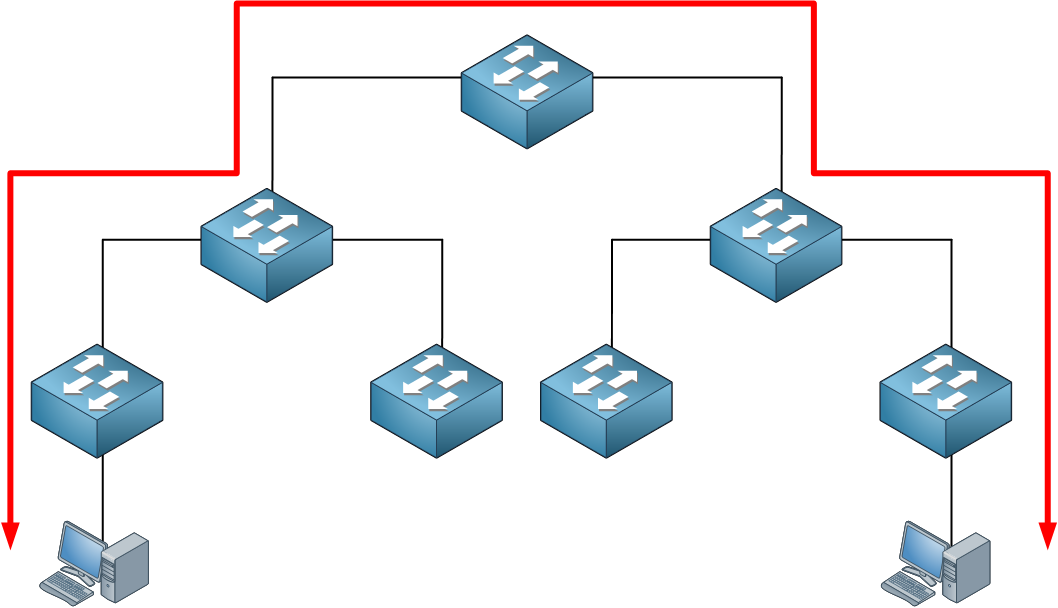
Each of the layers has a different function and requirements. Let’s discuss each layer:



Very Very good article Rene. Im so impressed and smiling right now.
I have seen designs where the firewalls are sitting on an access layer switch. Does it make sense to do that? Isnt there a “rule” that says that access layer switches should be used for your end stations or servers not for firewalls?
Hi Michael,
Glad to hear you like it Security will depend on which access layer we are dealing with. For example, we could have a “switch block” with a distribution + access layer that is only used for end devices like computers / laptops. You probably don’t want to use any firewalls there…not because there are no risks but it will be very expensive.
Security will depend on which access layer we are dealing with. For example, we could have a “switch block” with a distribution + access layer that is only used for end devices like computers / laptops. You probably don’t want to use any firewalls there…not because there are no risks but it will be very expensive.
You can configure your switches for some of the security risks on the access layer here:
- Port Security: against MAC spoofing / setting a limit to number of MAC addresses per port.
- DHCP Snooping: so nobody can spo
... Continue reading in our forumHi Rene,
A well written article on campus network design.
How can we have redundancy for each VLAN at the access layer?
Thanks,
RS
Hi RS,
Glad to hear you liked it.
There are a number of things you can do in the access layer. First of all, we use protocols like HSRP / VRRP / GLBP so that hosts in the access layer have a redundant gateway, redundant uplinks to the distribution layer is easy with Etherchannels.
An access layer switch that fails will still result in hosts without connectivity. You can get around this by using stacked switches and connecting your hosts to two different switches, this might be interesting for certain devices (servers) but a bit too expensive for regular hosts.
Rene
Hi Rene,
I am planning to change the design of my network and add more switches, but I am stuck. My end goal is to make everything virtual. Do you have any advice on how to do that?
Thanks
Aisha