Lesson Contents
Cloud security is about securing the cloud and securing access to the cloud. In this lesson, we’ll look at security, implications, and policies of cloud computing.
Shared Responsibility
We have different cloud service models (IaaS, Paas, and SaaS). In these different service models, there is a shared responsibility.
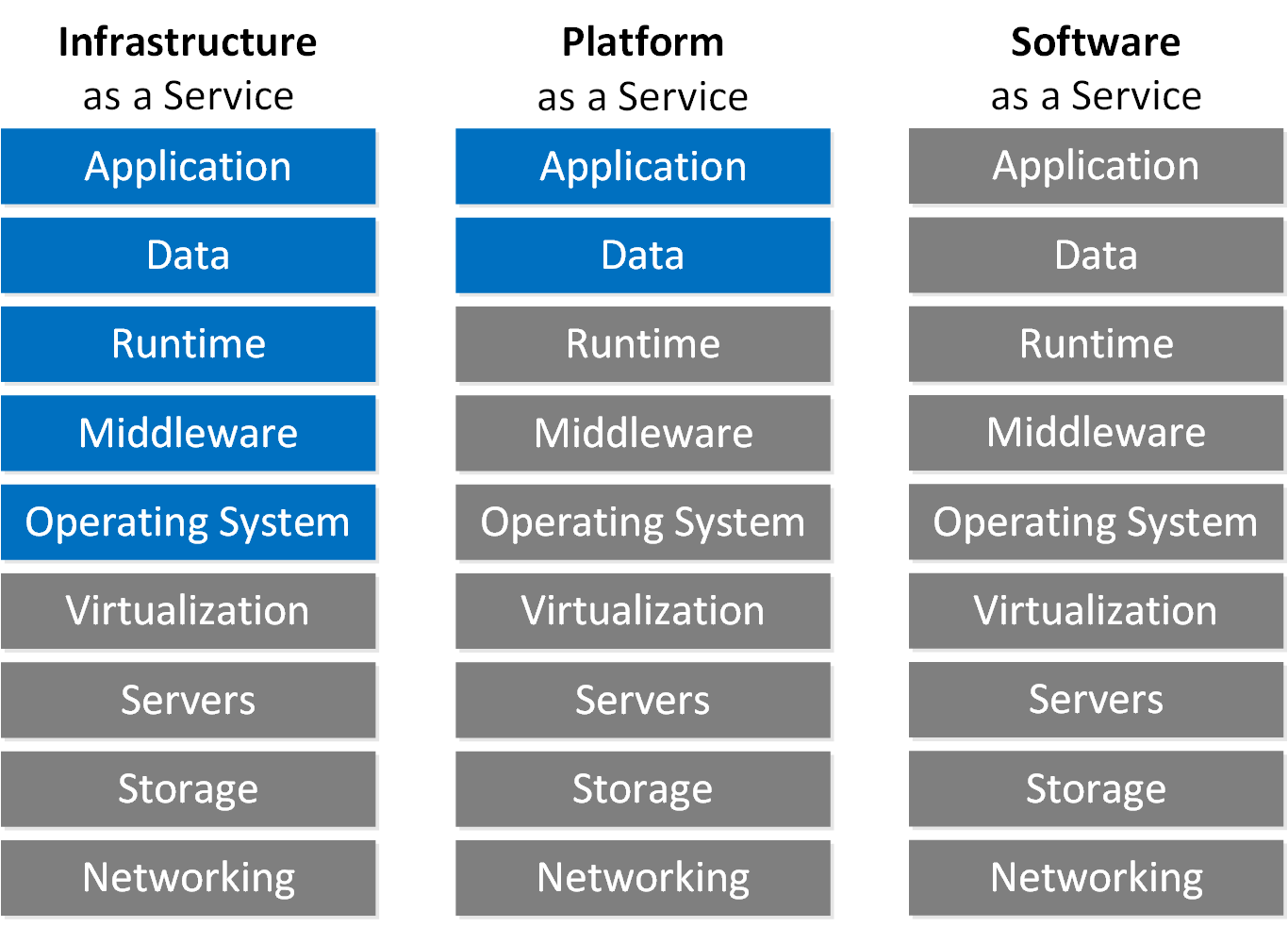
With the IaaS service model, the cloud provider is responsible for the security of the lower layers. The customer is responsible for the security of the operating system and everything that runs on top of it. With PaaS, the cloud provider is responsible for everything except the data and application.
With a SaaS solution, the cloud provider is responsible for everything. The higher the cloud provider’s control of the service model, the more security responsibilities the cloud provider has.

The Cloud Security Alliance (CSA) is an organization that promotes best practices for cloud security. They offer a security guidance document that covers best practices and recommendations for all domains in cloud computing.
They have two recommendations for the shared responsibility model:
Cloud providers should clearly document their internal security controls and customer security
features so the cloud user can make an informed decision. Providers should also properly
design and implement those controls.
Cloud users should, for any given cloud project, build a responsibilities matrix to document
who is implementing which controls and how. This should also align with any necessary
compliance standards.
The CSA provides two tools to help meet these requirements:
- Consensus Assessments Initiative Questionnaire (CAIQ): a template for cloud providers to document their security and compliance controls.
- Cloud Controls Matrix (CCM): lists cloud security controls and maps them to multiple security and compliance standards. You can also use the CCM to document security responsibilities.
Compliance
Regulatory compliance means that an organization has to conform to a specification, policy, standard, or law relevant to its business processes. Violations of regulatory compliance often result in legal punishment, including fines.
Here are examples of regulatory compliance laws and regulations:
- Payment Card Industry Data Security Standard (PCI DSS): an information security standard for organizations that handle credit cards.
- Health Insurance Portability and Accountability Act (HIPAA): US legislation that provides data security and privacy to protect medical information.
- General Data Protection Regulation (GDPR): EU legislation on data privacy and protection for individuals within the European Union.
There are also cloud-specific standards. Here are two ISO standards:
- ISO 27017: ISO standard that provides guidelines on the security aspects of cloud computing.
- ISO 27018: ISO standard that provides guidelines on protecting Personally Identifiable Information (PII) in cloud computing.
Threats and Risks
Cloud environments face the same threats as traditional (on-premises) IT infrastructures. The cloud runs on software. Software has vulnerabilities; attackers try to exploit these vulnerabilities.
The main difference between traditional IT infrastructures and cloud computing is that the cloud provider and customer share the responsibility for mitigating these threats. The customer has to understand who is responsible for what and trust the cloud provider meets their responsibilities.
Let’s discuss some threats unique to cloud computing.
Limited visibility and control
The responsibility of the customer and cloud provider depends on the cloud service model. With the PaaS and Saas service models, the cloud provider is responsible for most layers. This also means that the customer doesn’t have much visibility into what happens behind the scenes. The customer might want to monitor and analyze their applications outside of their control when the cloud provider manages the network layer.
Simplified unauthorized usage
Shadow IT is resources that users use without explicit approval from the organization. This is also a risk with traditional IT environments. For example, users that use Google Drive, Onedrive, or physical devices like USB sticks.
Cloud providers make it easy to provision new on-demand resources. It’s easy for staff to provision new cloud resources (especially PaaS and SaaS) without consent from the IT department. The IT department can’t protect something they don’t know about. Shadow IT reduces visibility and control.


