Lesson Contents
802.1x is a great way to protect your network by authenticating everything you connect to your switch ports, However, one disadvantage of 802.1X is that your end devices have to support it.
This is no problem with most modern devices but what if you have a network printer or camera that doesn’t support 802.1X?
If you can’t use 802.1X but still want to secure your switch ports somehow, you can use MAC Authentication Bypass (MAB).
When you enable MAB on a switchport, the switch drops all frames except for the first frame to learn the MAC address. Pretty much any frame can be used to learn the MAC address except for CDP, LLDP, STP, and DTP traffic. Once the switch has learned the MAC address, it contacts an authentication server (RADIUS) to check if it permits the MAC address.
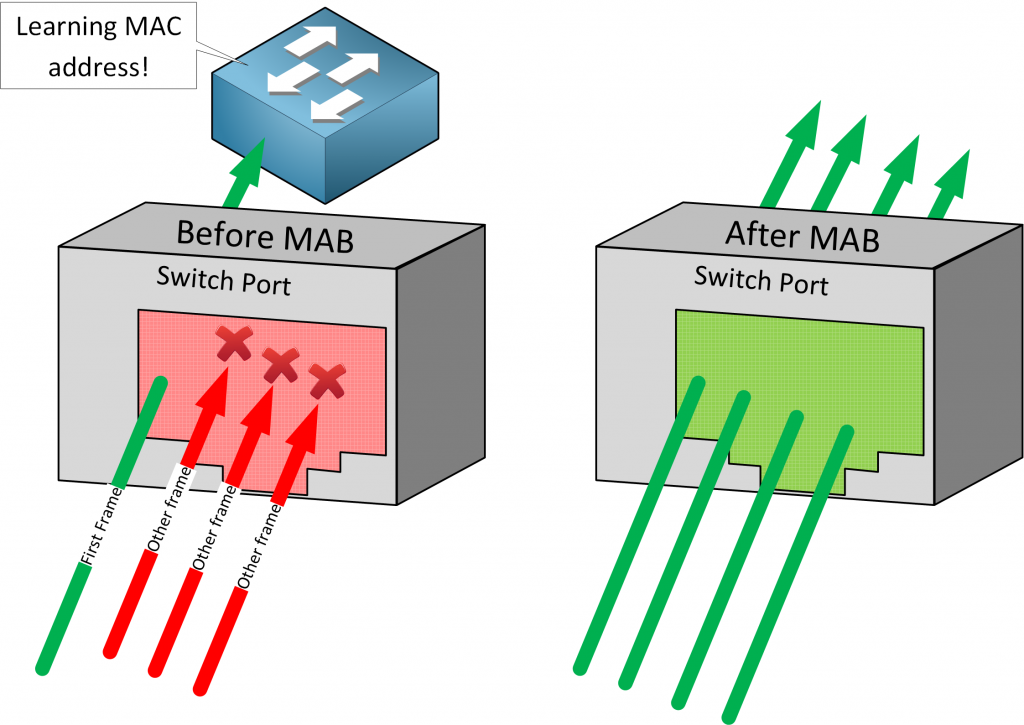
MAB also supports dynamic values from your RADIUS server. You can use dynamic access-list and VLAN assignment just like you can with 802.1X.
Besides MAC addresses, MAB can’t check anything else. This doesn’t make it a secure authentication option since it’s easy to spoof a MAC address.
There are two ways how you can configure MAB:
- Standalone: you only use MAB for authentication.
- Fallback: we use MAB as a fallback for 802.1X. The switch will first attempt 802.1X and when it fails, it uses MAB for authentication.
By default, MAB only supports a single endpoint (device) per switchport. When it sees more than one source MAC address, it causes a security violation. This can be an issue when for example, you use an IP phone with a PC behind it. It’s possible to change this behavior:
- Single-host mode: only a single source MAC address can be authenticated. When the switch detects another source MAC address after authentication, it triggers a security violation. This is the default setting.
- Multi-domain authentication host mode: you can authenticate two source MAC addresses, one in the voice VLAN and another one in the data VLAN. This is for the scenario where you have an IP phone and a PC on a single switchport. Any more source MAC addresses trigger a security violation.
- Multi-authentication host mode: you can authenticate multiple source MAC addresses. You can use this when your switchport is connected to another switch. Each source MAC address is separately authenticated.
- Multi-host mode: the switch allows multiple source MAC addresses. Only the first source MAC address is authenticated, all other source MAC addresses are automatically permitted.
Configuration
To demonstrate MAB, I’ll use the following topology:
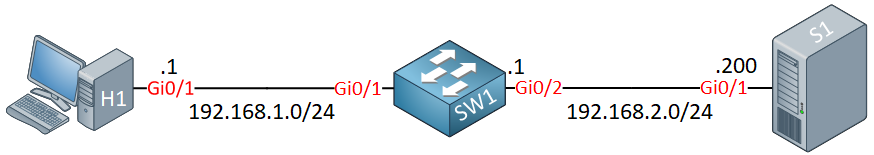
- H1 is our endpoint we want to authenticate.
- SW1 is where we configure MAB.
- S1 is my RADIUS server.
I’ll configure standalone and single-host mode.
Freeradius
To keep it simple, I use a basic RADIUS server (freeradius). If you want to follow this example, you don’t have to install it yourself. You can use my docker image.
The client configuration looks like this:
# cat clients.conf
client CISCO {
ipaddr = 0.0.0.0/0
secret = CISCO
}I use “CISCO” as the secret and we accept any client. Perfect for a lab.
Here is the users configuration:
# cat /etc/raddb/users
001da18b36d8 Cleartext-Password := "001da18b36d8"The username and password that you see here is the MAC address of H1.
Cisco IOS
Global Configuration
Let’s configure the switch. First, we need to enable AAA globally:
SW1(config)#aaa new-modelI’ll configure the default authentication list:
SW1(config)#aaa authentication dot1x default group radiusAnd we need to add our RADIUS server:



Hi,
Is it possible to dot1x authentication using freeradius ?
Thanks
Hello Sims
Dot1x port-based authentication by definition uses an authentication server such as RADIUS. FreeRADIUS is such a server as well, so yes, it can be used for authentication of dot1x. Take a look at the following link from FreeRADIUS. It refers to the use of 802.1x for WiFi but the concept is the same.
https://wiki.freeradius.org/guide/Enterprise-WiFi#ieee-802-1x-and-radius-authentication
I hope this has been helpful!
Laz
Hi,
I’m trying to dynamically assign vlan with freeradius and it’s not working. Do you guys have some tutorial to help with this?
Thanks
Hello Hilton
There’s currently no lab that includes the assignment of a VLAN using a RADIUS server. The closest thing is the following lab which uses a RADIUS server for 802.3X authentication.
https://networklessons.com/cisco/ccna-routing-switching-icnd2-200-105/aaa-authentication-on-cisco-ios
However, you can find information about such a configuration at the following Cisco documentation.
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_usr_8021x/configuration/xe-3se/3850/sec-user-8021x-xe-3se-3850-book/sec-ieee-8021x-vlan-assign.html
I hope this has been helpful!
Laz
Hello Burak
The following lesson describes how you can configure 802.1x for wired connections on a Cisco switch using a RADIUS server and certificates.
https://networklessons.com/cisco/ccie-routing-switching/aaa-configuration-cisco-switch
Take a look and if you have any further questions, let us know!
I hope this has been helpful!
Laz