Lesson Contents
IEEE 802.1X is an IEEE standard for port-based Network Access Control (PNAC). Devices wanting to access the network must authenticate themselves before accessing it. It’s commonly used in corporate networks where we require user or device authentication.
Here is the topology I’ll use:
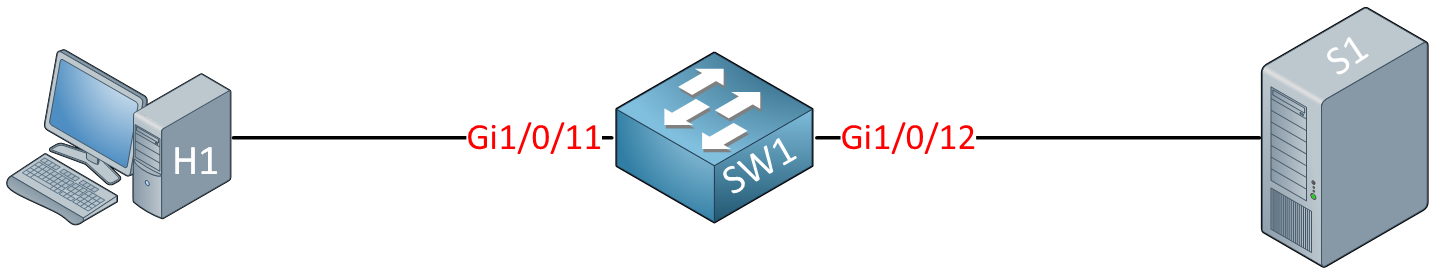
I’ll use the EAP-MD5 method because it’s one of the simplest EAP methods to set up. It’s insecure, so you shouldn’t use it in production anymore. EAP-MD only uses a challenge and response. Here are the devices I use:
- The host is a Ubuntu machine. I like to use Ubuntu because it has 802.1X support and still supports EAP-MD5.
- The switch is a Cisco catalyst 3850 running Cisco IOS Software, IOS-XE Software, Catalyst L3 Switch Software (CAT3K_CAA-UNIVERSALK9-M), Version 03.07.05.E RELEASE SOFTWARE (fc1).
- The RADIUS server is a freeradius server. You can use my Alpine freeradius image. It is simple to set up, and it supports many EAP methods.
Setting up 802.1X on Ubuntu is straightforward. Under network settings, you only have to enable 802.1X and specify the EAP method and credentials.Here it is:
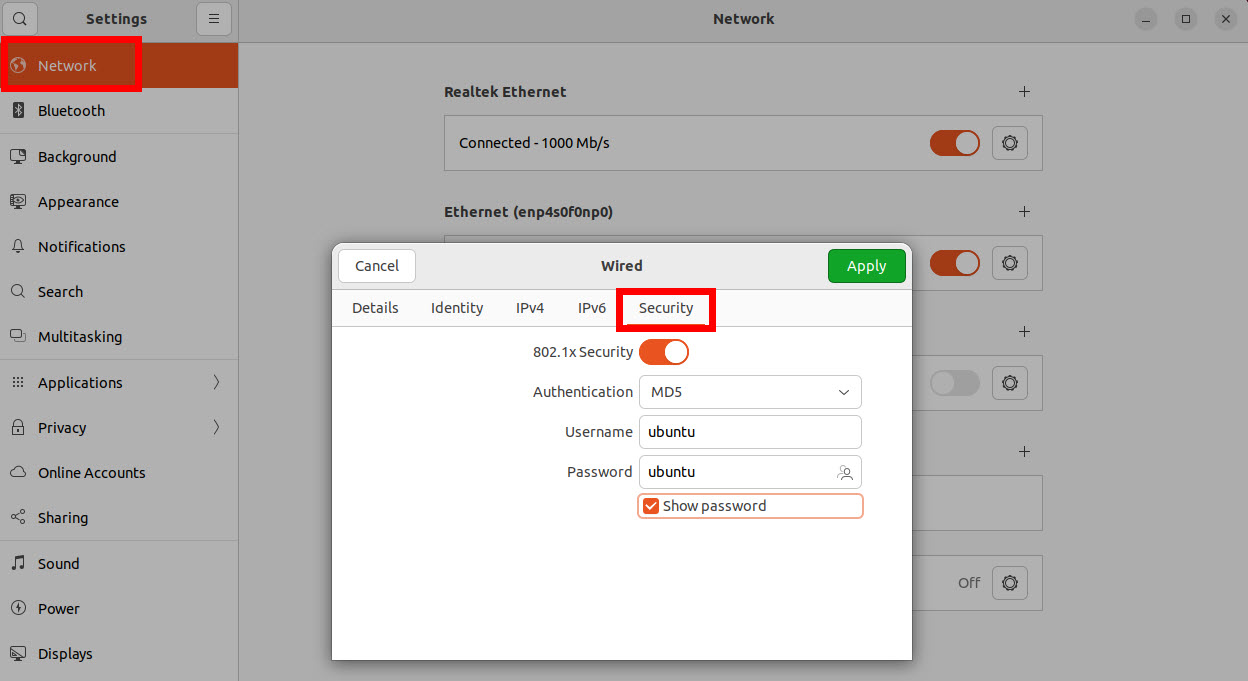
Configurations
Want to take a look for yourself? Here, you will find the startup configuration of the authenticator (SW1) and the configuration files for the freeradius server.
SW1
hostname SW1
!
username admin privilege 15 secret 5 $1$YVOP$xaZpE.nA.FwvKwXxtvzTw1
aaa new-model
!
aaa authentication dot1x default group radius
!
aaa session-id common
!
ip dhcp pool VLAN10
network 192.168.10.0 255.255.255.0
!
dot1x system-auth-control
!
interface GigabitEthernet1/0/11
switchport access vlan 10
switchport mode access
authentication host-mode multi-auth
authentication port-control auto
dot1x pae authenticator
spanning-tree portfast
!
interface GigabitEthernet1/0/12
switchport access vlan 10
switchport mode access
spanning-tree portfast
!
interface Vlan10
ip address 192.168.10.100 255.255.255.0
!
radius server FREERADIUS
address ipv4 192.168.10.200 auth-port 1812 acct-port 1813
key CISCOdocker-compose.yml
version: '2'
services:
freeradius:
image: networklessons/docker-alpine-freeradius:1
ports:
- 1812:1812/udp
- 1813:1813/udp
volumes:
- "./clients.conf:/etc/raddb/clients.conf"
- "./users:/etc/raddb/users"
- "./eap:/etc/raddb/mods-enabled/eap"clients.conf
client CISCO {
ipaddr = 0.0.0.0/0
secret = CISCO
}eap
eap {
default_eap_type = md5
timer_expire = 60
ignore_unknown_eap_types = no
cisco_accounting_username_bug = no
max_sessions = ${max_requests}
md5 {
}
}users
ubuntu Cleartext-Password := "ubuntu"I’ll show you all the packets from both sides: EAPOL and RADIUS.
EAPOL
Let’s start with the EAPOL packets. If you want to see them for yourself, you can download them here:
Packet Capture: 802.1X EAP MD5 EAPOL
EAPOL-Start
The EAPOL-Start packet is the first one and is sent from the supplicant to the authenticator:
Frame 1: 60 bytes on wire (480 bits), 60 bytes captured (480 bits) on interface -, id 0
Ethernet II, Src: Solarfla_25:11:f0 (00:0f:53:25:11:f0), Dst: Nearest-non-TPMR-bridge (01:80:c2:00:00:03)
Destination: Nearest-non-TPMR-bridge (01:80:c2:00:00:03)
Source: Solarfla_25:11:f0 (00:0f:53:25:11:f0)
Type: 802.1X Authentication (0x888e)
Padding: 000000000000000000000000000000000000000000000000000000000000000000000000…
802.1X Authentication
Version: 802.1X-2001 (1)
Type: Start (1)
Length: 0Here’s what we see:
- The packet is destined for the Ethernet multicast address 0180:c200:0003.
- The Ethertype is 0x888E.
- The version is set to 802.1X-2001.
- The type is “Start”.
EAP-Request/Identity
The authenticator sends the EAP-Request/Identity packet to the supplicant:
Frame 2: 60 bytes on wire (480 bits), 60 bytes captured (480 bits) on interface -, id 0
Ethernet II, Src: Cisco_6f:77:8b (bc:c4:93:6f:77:8b), Dst: Solarfla_25:11:f0 (00:0f:53:25:11:f0)
Destination: Solarfla_25:11:f0 (00:0f:53:25:11:f0)
Source: Cisco_6f:77:8b (bc:c4:93:6f:77:8b)
Type: 802.1X Authentication (0x888e)
Padding: 000000000000000000000000000000000000000000000000000000000000000000000000…
802.1X Authentication
Version: 802.1X-2010 (3)
Type: EAP Packet (0)
Length: 5
Extensible Authentication Protocol
Code: Request (1)
Id: 9
Length: 5
Type: Identity (1)The output above shows that the version is set to 802.1X-2010, and the type is an EAP packet. The EAP message shows that the code is set to request, and the type is identity.
EAP-Response/Identity
The supplicant replies with the EAP-Response/Identity packet:
Frame 3: 60 bytes on wire (480 bits), 60 bytes captured (480 bits) on interface -, id 0
Ethernet II, Src: Solarfla_25:11:f0 (00:0f:53:25:11:f0), Dst: Nearest-non-TPMR-bridge (01:80:c2:00:00:03)
Destination: Nearest-non-TPMR-bridge (01:80:c2:00:00:03)
Source: Solarfla_25:11:f0 (00:0f:53:25:11:f0)
Type: 802.1X Authentication (0x888e)
Padding: 00000000000000000000000000000000000000000000000000000000000000
802.1X Authentication
Version: 802.1X-2001 (1)
Type: EAP Packet (0)
Length: 11
Extensible Authentication Protocol
Code: Response (2)
Id: 9
Length: 11
Type: Identity (1)
Identity: ubuntuAbove, we see that the code is set to response, and the type is identity. The identity shows “ubuntu”, the username I configured on my desktop.
EAP-Request/Challenge
The authenticator will forward the challenge from the RADIUS server to the supplicant in the EAP-Request/Challenge packet:
Frame 4: 60 bytes on wire (480 bits), 60 bytes captured (480 bits) on interface -, id 0
Ethernet II, Src: Cisco_6f:77:8b (bc:c4:93:6f:77:8b), Dst: Solarfla_25:11:f0 (00:0f:53:25:11:f0)
Destination: Solarfla_25:11:f0 (00:0f:53:25:11:f0)
Source: Cisco_6f:77:8b (bc:c4:93:6f:77:8b)
Type: 802.1X Authentication (0x888e)
Padding: 0000000000000000000000000000000000000000
802.1X Authentication
Version: 802.1X-2010 (3)
Type: EAP Packet (0)
Length: 22
Extensible Authentication Protocol
Code: Request (1)
Id: 10
Length: 22
Type: MD5-Challenge EAP (EAP-MD5-CHALLENGE) (4)
[Expert Info (Warning/Security): Vulnerable to MITM attacks. If possible, change EAP type.]
[Vulnerable to MITM attacks. If possible, change EAP type.]
[Severity level: Warning]
[Group: Security]
EAP-MD5 Value-Size: 16
EAP-MD5 Value: 07132be14ba1bfea95cfe460094a23fbThis output shows that the code is set to request, and the type is MD5-Challenge EAP. The challenge is included under the EAP-MD5 Value.
EAP-Response/Challenge
The supplicant will reply with the EAP-Response/Challenge packet:
Frame 5: 60 bytes on wire (480 bits), 60 bytes captured (480 bits) on interface -, id 0
Ethernet II, Src: Solarfla_25:11:f0 (00:0f:53:25:11:f0), Dst: Nearest-non-TPMR-bridge (01:80:c2:00:00:03)
Destination: Nearest-non-TPMR-bridge (01:80:c2:00:00:03)
Source: Solarfla_25:11:f0 (00:0f:53:25:11:f0)
Type: 802.1X Authentication (0x888e)
Padding: 0000000000000000000000000000000000000000
802.1X Authentication
Version: 802.1X-2001 (1)
Type: EAP Packet (0)
Length: 22
Extensible Authentication Protocol
Code: Response (2)
Id: 10
Length: 22
Type: MD5-Challenge EAP (EAP-MD5-CHALLENGE) (4)
[Expert Info (Warning/Security): Vulnerable to MITM attacks. If possible, change EAP type.]
[Vulnerable to MITM attacks. If possible, change EAP type.]
[Severity level: Warning]
[Group: Security]
EAP-MD5 Value-Size: 16
EAP-MD5 Value: 6492f6ebd6ce9b437643ea37ac9b24c5The code is set to response. The type is MD5-Challenge EAP. It also includes the response under EAP-MD5 Value.
EAP-Success
Finally, the supplicant receives the EAP-Success packet from the authenticator:
Frame 6: 60 bytes on wire (480 bits), 60 bytes captured (480 bits) on interface -, id 0
Ethernet II, Src: Cisco_6f:77:8b (bc:c4:93:6f:77:8b), Dst: Solarfla_25:11:f0 (00:0f:53:25:11:f0)
Destination: Solarfla_25:11:f0 (00:0f:53:25:11:f0)
Source: Cisco_6f:77:8b (bc:c4:93:6f:77:8b)
Type: 802.1X Authentication (0x888e)
Padding: 000000000000000000000000000000000000000000000000000000000000000000000000…
802.1X Authentication
Version: 802.1X-2010 (3)
Type: EAP Packet (0)
Length: 4
Extensible Authentication Protocol
Code: Success (3)
Id: 10
Length: 4The code is set to Success.
RADIUS
While we are at it, let’s also look at the RADIUS packets. You can take a look for yourself here:



Doing some more research on this. Is this process described here for the wired EAPOL “handshake”. Is there different 4 way handshake used for wireless that uses PMK and GMK keys? Appreciate all the work you guys do!
-Chase
Hello Chase
EAPOL and the WPA 4-way handshake are both important components in network security, especially in authentication processes. In the lesson, EAPOL is described in the context of wired network security, and in particular, with 802.1X authentication. It’s a part of the IEEE 802.1X standard for port-based Network Access Control (NAC).
In this context, EAPOL and WPA 4-way handshake are quite different in their use and processes. Their key differences are listed below:
- Network Type: EAPOL is mainly used in wired networks, while the 4-way handshake is s
... Continue reading in our forum@ckress I’m writing an explanation of the WPA 4-way handshake today, which should be finished in a couple of days. I’ll add a link here once it’s finished.
Understanding the WPA keys is a prerequisite. I published this yesterday:
https://networklessons.com/cisco/ccnp-encor-350-401/introduction-to-wpa-key-hierarchy
Rene
Here is an explanation of the WPA 4-way handshake:
https://networklessons.com/cisco/ccnp-encor-350-401/wpa-and-wpa2-4-way-handshake
Hi, everyone.
After seeing this
https://cdn-forum.networklessons.com/uploads/default/original/2X/9/975664252c06f63e978e5eb9b0f62975b57846e1.png
https://cdn-forum.networklessons.com/uploads/default/original/2X/2/2ff74462066ec645d2dcaad904e3100d310a8171.png
Why are EAP messages such as request identity, etc encapsulated in an EAPOL header? Which is basically the part where it says 802.1X Authentication.
Wouldn’t it make more sense to just grab those fields in EAP and include them in EAPOL altogether?
Rene said that EAP messages are always carried by another proto
... Continue reading in our forum