Lesson Contents
Policy NAT (aka Conditional NAT) lets you combine NAT and route-maps so that you can create more specific NAT rules. In a route-map, one of the things you can use is access-lists so you can create NAT rules based on anything you can match in an access-list.
Configuration
To demonstrate this, I’ll use the following topology:
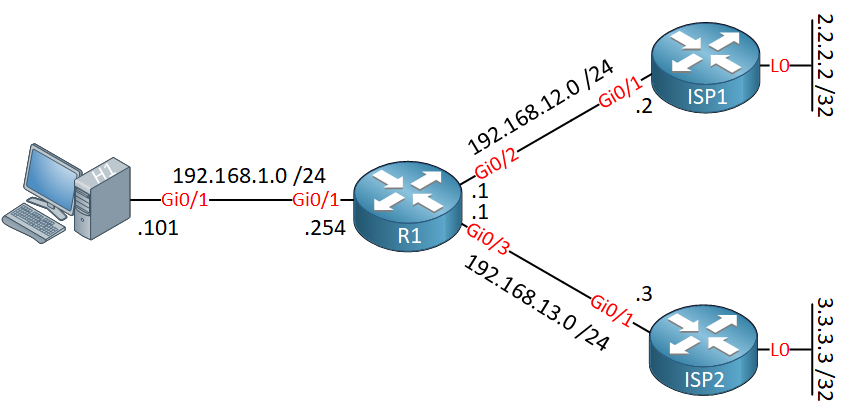
H1 is the host that we’ll source our traffic from. R1 is the NAT router that is connected to two ISPs. Each ISP has a loopback interface that represents a telnet server. We are going to create a NAT rule that translates:
- 192.168.1.101 to 192.168.12.1 when it connects to 2.2.2.2 port 23.
- 192.168.1.101 to 192.168.13.1 when it connects to 3.3.3.3 port 23.
Configurations
Want to take a look for yourself? Here you will find the startup configuration of each device.
H1
hostname H1
!
no ip routing
!
no ip cef
!
interface GigabitEthernet0/1
ip address 192.168.1.101 255.255.255.0
!
ip default-gateway 192.168.1.254
!
endISP1
hostname ISP1
!
ip cef
!
interface Loopback0
ip address 2.2.2.2 255.255.255.255
!
interface GigabitEthernet0/1
ip address 192.168.12.2 255.255.255.0
!
endISP2
hostname ISP2
!
ip cef
!
interface Loopback0
ip address 3.3.3.3 255.255.255.255
!
interface GigabitEthernet0/1
ip address 192.168.13.3 255.255.255.0
!
endR1
hostname R1
!
ip cef
!
interface GigabitEthernet0/1
ip address 192.168.1.254 255.255.255.0
!
interface GigabitEthernet0/2
ip address 192.168.12.1 255.255.255.0
!
interface GigabitEthernet0/3
ip address 192.168.13.1 255.255.255.0
!
ip route 2.2.2.2 255.255.255.255 192.168.12.2
ip route 3.3.3.3 255.255.255.255 192.168.13.3
!
end
Let’s get started. First, I need to configure the correct NAT inside and outside interfaces:
R1(config)#interface GigabitEthernet 0/1
R1(config)#ip nat inside
R1(config)#interface GigabitEthernet 0/2
R1(config-if)#ip nat outside
R1(config)#interface GigabitEthernet 0/3
R1(config-if)#ip nat outsideI’ll create two access-lists that match the traffic that I want to translate with NAT:
R1(config)#ip access-list extended ISP1_L0
R1(config-ext-nacl)#permit tcp host 192.168.1.101 host 2.2.2.2 eq 23
R1(config)#ip access-list extended ISP2_L0
R1(config-ext-nacl)#permit tcp host 192.168.1.101 host 3.3.3.3 eq 23Now I’ll create a route-map and attach the access-lists in two different permit statements:



Hi Rene,
Believe you have a typo:
Should be
Hello Chris
Yes you are correct! Thanks for catching that! I will let @ReneMolenaar know to have that changed.
Thanks again!
Laz
Hello Rene,
I haven’t yet tried out, but couldn’t we do something like this instead of using a route-map?
--
Respectfully
Hello Network E,
I hope you are doing well. I will admit that I have not read this lesson, but I have read the headline, and I might be able to answer your question. Policy based NAT is done with a route map, if you used some other method to NAT it would not be policy based NAT. So would your config work? Possibly, but if it did you are no longer using policy based NAT.
I hope this helps.
Scott
Hello Network E
@wellerk.scott is absolutely right. You could do it that way as well. However, the exercise was used to show how to use a route-map.
The advantage of using a route map instead is that you have more flexibility by creating more specific NAT rules.
I hope this has been helpful!
Laz