Lesson Contents
ICMP (Internet Control Message Protocol) is a network protocol used for diagnostics and network management. A good example is the “ping” utility which uses an ICMP request and ICMP reply message. When a certain host of port is unreachable, ICMP might send an error message to the source. Another example of an application that uses ICMP is traceroute.
ICMP messages are encapsulated in IP packets so most people would say that it’s a layer 4 protocol like UDP or TCP. However, since ICMP is a vital part of the IP protocol it is typically considered a layer 3 protocol.
The header that ICMP uses is really simple, here’s what it looks like:
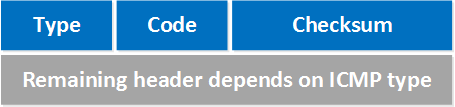
The first byte specifies the type of ICMP message. For example, type 8 is used for an ICMP request and type 0 is used for an ICMP reply. We use type 3 for destination unreachable messages.
The second byte called code specifies what kind of ICMP message it is. For example, the destination unreachable message has 16 different codes. When you see code 0 it means that the destination network was unreachable while code 1 means that the destination host was unreachable.
The third field are 2 bytes that are used for the checksum to see if the ICMP header is corrupt or not. What the remaining part of the header looks like depends on the ICMP message type that we are using.
If you are interested, here is a full list with all ICMP codes and types.
To show you some examples of ICMP in action, let’s look at some popular ICMP messages in Wireshark.
Wireshark Captures
ICMP Echo request and reply
Let’s start with a simple example, a ping. I will use two routers for this:
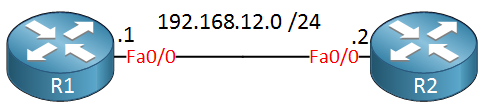
Let’s send a ping from R1:
R1#ping 192.168.12.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.12.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 4/21/64 msHere’s what it looks like:
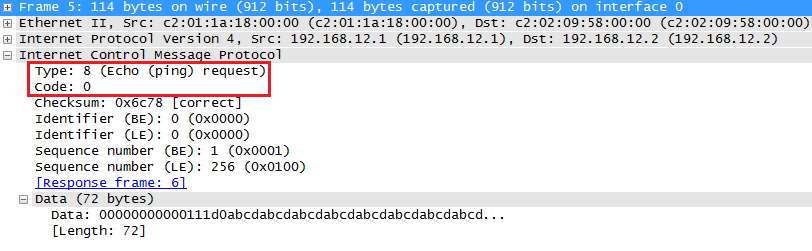
The message above is the ICMP request, you can see it uses type 8 and code 0 for this. When R2 receives it will reply:
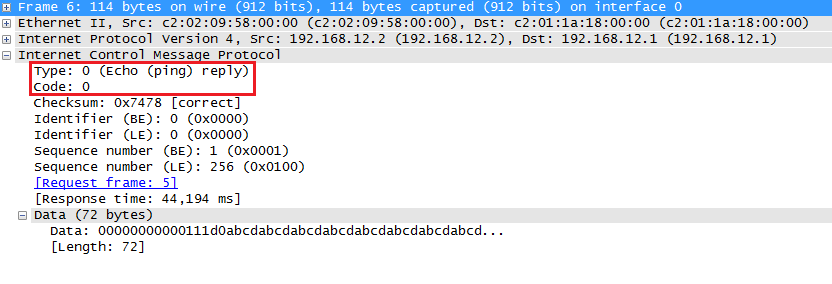
The ICMP echo reply is a type 0 and code 0 message.
Destination Unreachable
Another nice example to look at is the destination unreachable message. We can test this by adding an access-list on R2 that denies ICMP messages:
R2(config)#ip access-list extended NO_ICMP
R2(config-ext-nacl)#deny icmp any host 192.168.12.2
R2(config-ext-nacl)#permit ip any any
R2(config)#interface FastEthernet 0/0
R2(config-if)#ip access-group NO_ICMP inNow let’s try that ping from R1 again:
R1#ping 192.168.12.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.12.2, timeout is 2 seconds:
UUUUU
Success rate is 0 percent (0/5)The ping fails and you can see the U (unreachable) messages on R1. Here’s the ICMP message that R2 sends:
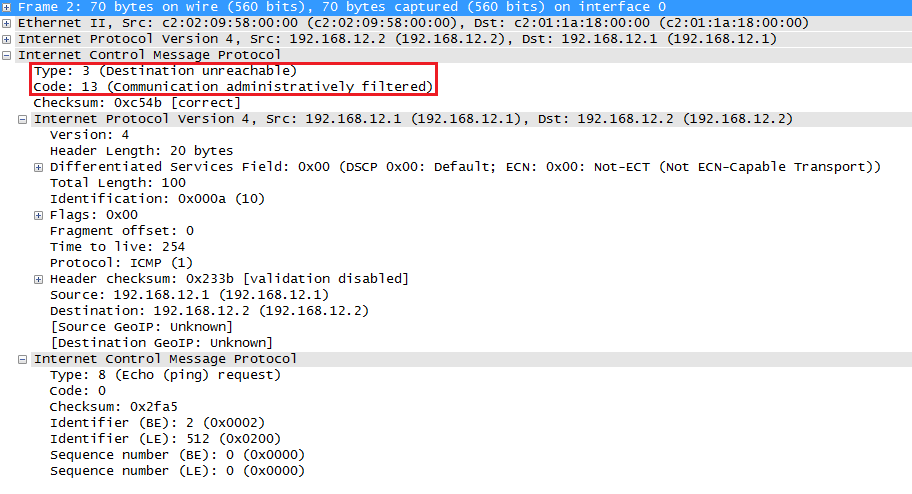
The ICMP destination unreachable message is a type 3 and it’s using code 13 because this packet was “administratively filtered” (acces-list).
Traceroute
Traceroute also uses ICMP messages, to demonstrate this we will use three routers:
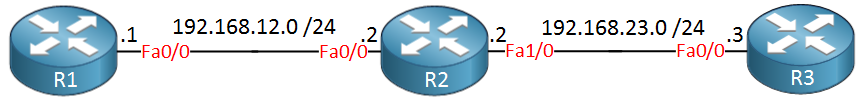
Let’s see what a traceroute from R1 to R3 looks like:
R1#traceroute 192.168.23.3 probe 1
Type escape sequence to abort.
Tracing the route to 192.168.23.3
1 192.168.12.2 52 msec
2 192.168.23.3 60 msecCisco IOS by default will send multiple probes. For this demonstration I only need one probe. Here’s the first packet that R1 sends:
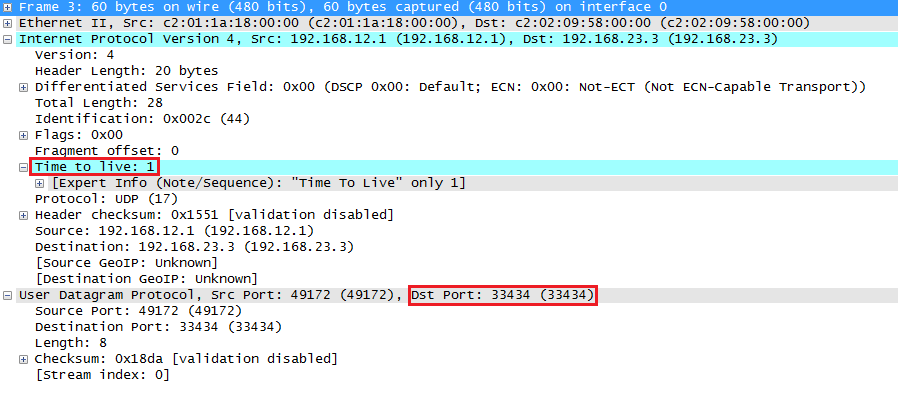
Cisco IOS uses UDP packets with a TTL value of 1 and destination port 33434. The TTL and destination port will increase for every hop. Once R2 receives this packet it will reply like this:
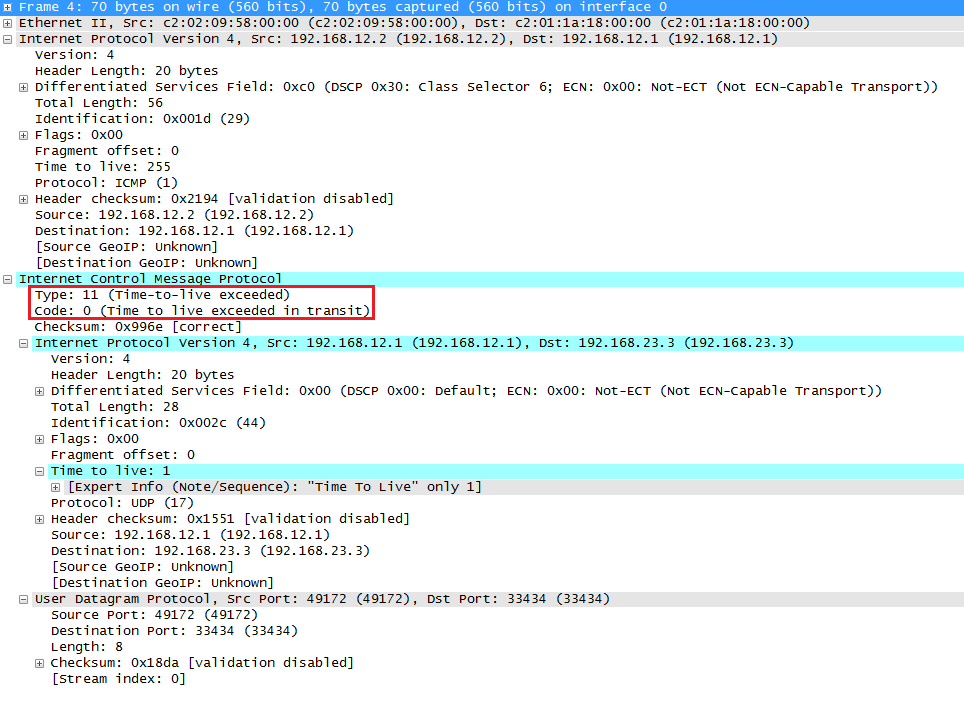
Here’s where ICMP comes into play. R2 will send an ICMP type 11 (time to live exceeded) message to R1. Once R1 receives this, it will send its second probe:
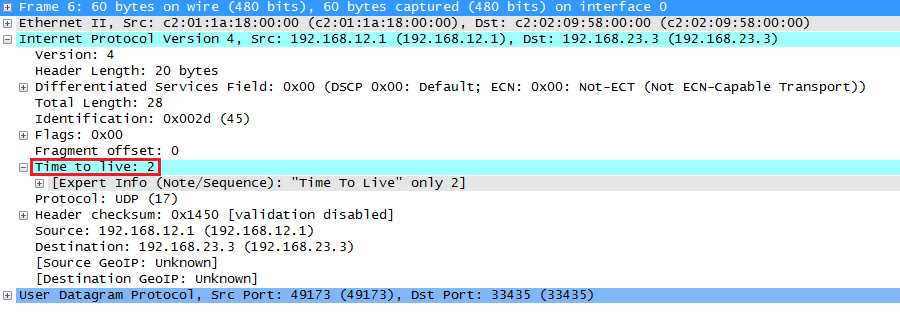
Above you can see that the TTL is now 2 and the destination port number has increased to 33435. Once R3 receives this packet it will reply like this:
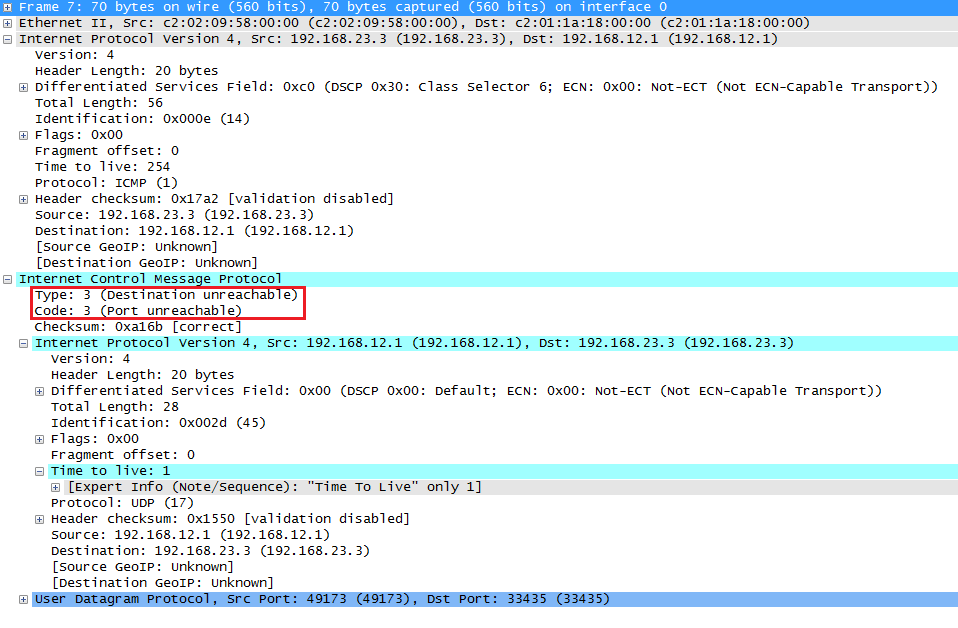
R3 will reply with a type 3 destination unreachable message. Take a close look at the type and code. The type tells us the destination is unreachable. This could mean that the remote host or network is unreachable.
However, the code is number 3 which means port unreachable. R3 uses this code because nothing is listening on UDP port 33435. R3 replies to R1 and sets this code, so R1 at least now knows that R3 (192.168.23.3) is reachable, it’s just not listening in UDP port 33435.
Conclusion
You have now seen what the ICMP is used for, what the header looks like and what some of the most popular messages look like. If you have any questions, feel free to leave a comment in our forum!


If R3 will reply with a type 3 destination unreachable message then how come you mentioned At least R1 now knows that 192.168.23.3 is reachable at the end?
Hi Lynkaran,
When R3 sends the IP packet, it will use 192.168.23.3 as the source address. You can see this in the wireshark capture.
Rene
Hi Rene,
How Can I block Traceroute, if dst port not fixed ?? What will be the exact Port number . You mentioned the dst port number will be 33434 and increase by 1 but I found from host the port is 51890 and dont increase by one . Please do me clear on it .Thanks a lot
br//
zaman
Hi Zaman,
It depends on which traceroute you want to block. Cisco IOS uses a different traceroute than Microsoft Windows does.
Rene
Hi Rene,
Why do we need to use UDP in traceroute? We have other commands like nmap to check if a particular port is listening for connections. I was thinking traceroute is used to just check IP connectivity, for which ICMP is sufficient.