Lesson Contents
Wireless encryption is important. We use radio frequency, so our signal goes everywhere. You can’t detect if someone is capturing your traffic.
Wired Equivalent Privacy (WEP) was the first encryption protocol and part of the original IEEE 802.11 standard. WEP had some serious weaknesses and vulnerabilities, which led to the creation of the 802.11i standard to deal with WEP and its vulnerabilities.
The 802.11i describes what we commonly know as Wi-Fi Protected Access (WPA). The Wi-Fi Alliance created WPA, which is based on the 802.11i standard.
Instead of using a single key for everything, WPA uses a hierarchy with many keys to encrypt and check the integrity of different 802.11 frames.
In this lesson, we’ll look at the different keys and the difference between TKIP and AES-CCMP. WPA version one uses TKIP, while WPA version two can use TKIP and/or AES-CCMP. There is also WPA version three, which is outside the scope of this lesson.
Understanding the different keys is important to understand the WPA 4-way handshake.
Terminology
There is quite some terminology in this lesson. First of all, there are many key names. If you research these keys, you’ll run into many different names for the same keys, which makes it confusing. I stick to the names as defined in the IEEE 802.11i standard.
There is also some wireless and 802.1X-related terminology. In wireless 802.11 terminology, a wireless client is officially called a station (STA).
With 802.1X, we have the supplicant, authenticator, and authentication server. With a wireless network, the wireless client is the supplicant, and the Access Point (AP) is the authenticator.
I’ll stick to wireless client and AP to keep it simple.
Pairwise and group keys
An AP has many wireless clients. Unicast traffic between a wireless client and the AP has to be private. You don’t want one client to be able to decrypt traffic between another wireless client and the AP. This is why you should have different keys between each wireless client and AP:
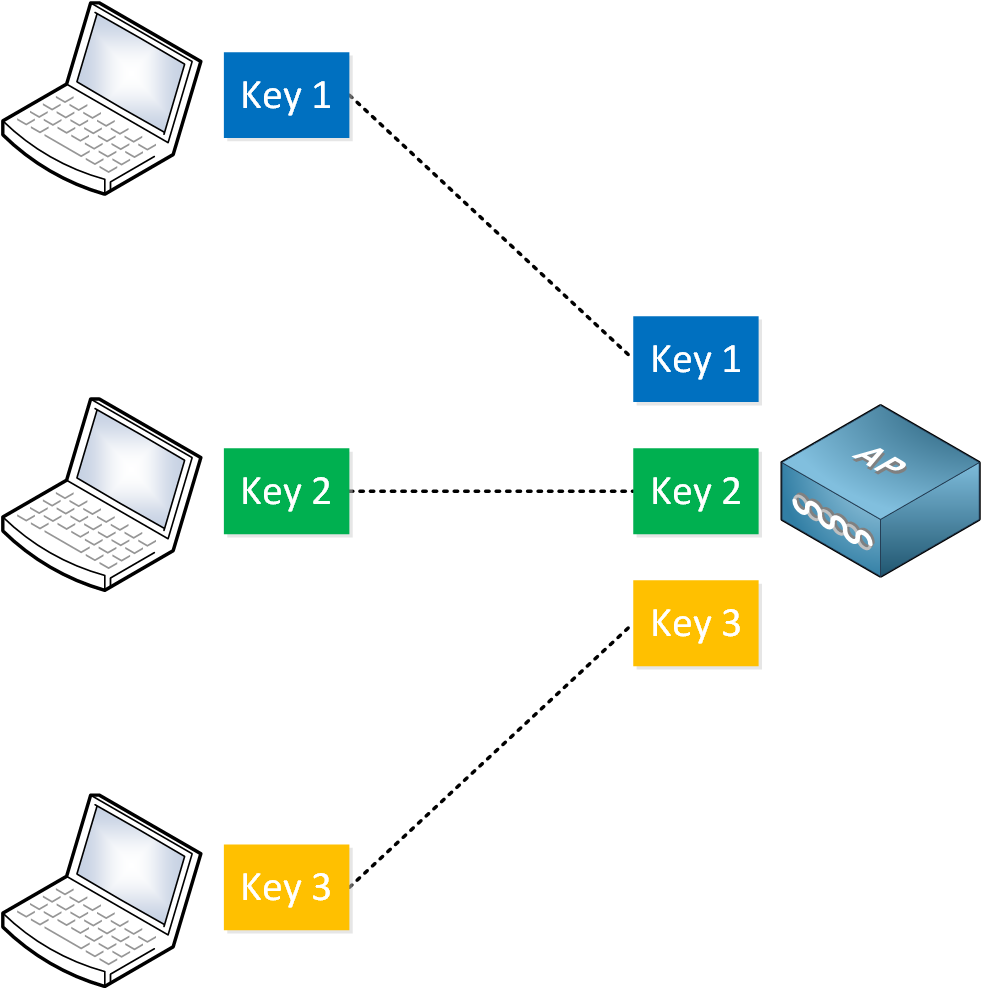
We call these pairwise keys because there is a pair of keys between each wireless client and the AP. The AP has multiple pairwise keys, one for each associated wireless client.
There is also broadcast and multicast traffic. All wireless clients should be able to encrypt and decrypt this traffic, so we need a shared key:
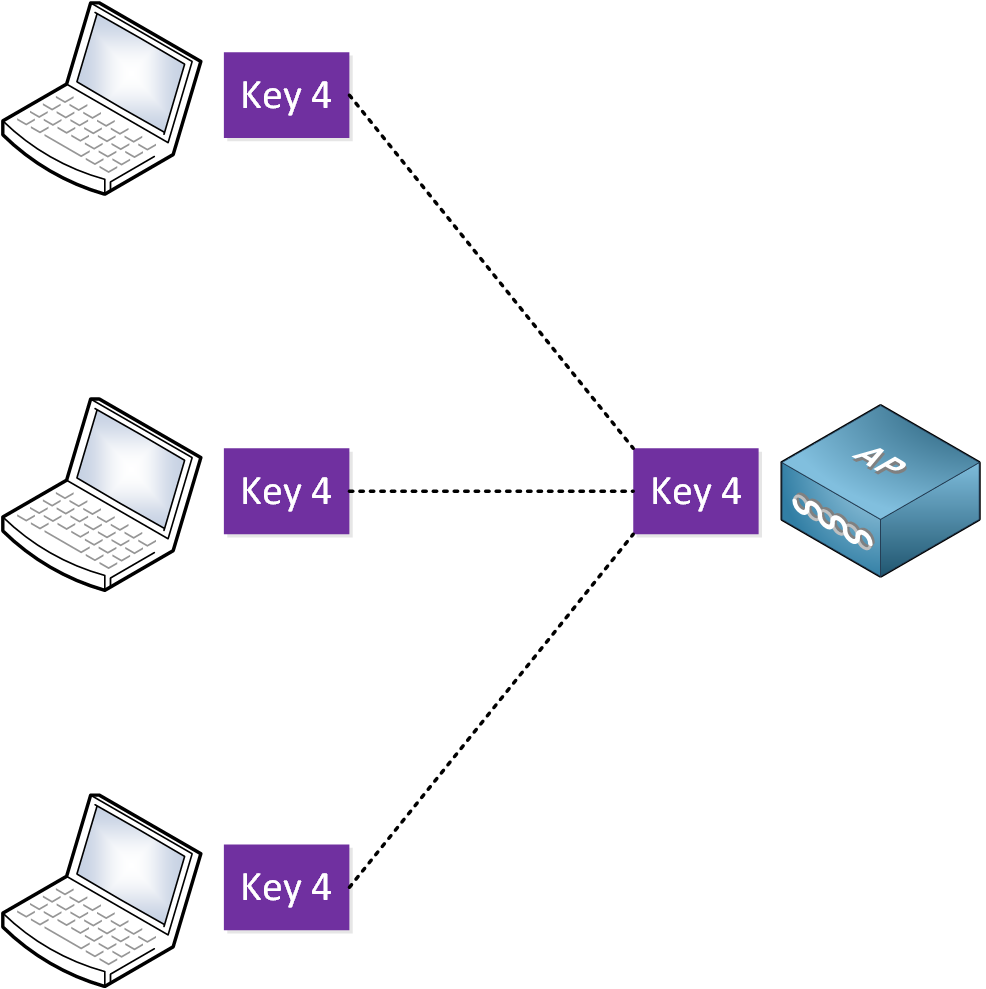
All associated wireless clients of the AP have the same key. We call this a group key. The Pairwise and group keys are created differently.
Key Derivation
Key derivation is a process used in cryptography to generate one or more cryptographic keys from one or more values, such as keys or a passphrase. The purpose of key derivation is to produce keys that are cryptographically strong and suitable for specific cryptographic applications, like encryption, authentication, or digital signatures. A Key Derivation Function (KDF) is a specific algorithm used for key derivation. Here’s how to visualize this:

When we look at the WPA keys, you’ll see that some keys are derived.
Key Partitioning
Key partitioning in cryptography means dividing (partitioning) a single key into a set of keys. One of the advantages of dividing a key into parts is that the security of the key improves. An attacker needs all parts of the partitioned keys to recover the original key.
Here is a simple example:
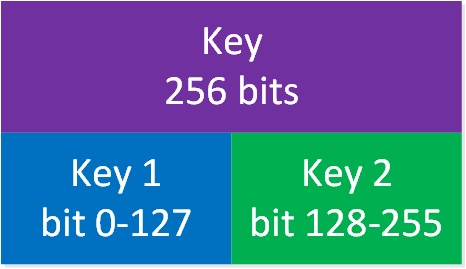
WPA uses key partitioning for many keys.
Pairwise Master Key (PMK)
The pairwise master key (PMK) is a 256-bit key at the top of the key hierarchy and is used indirectly for unicast traffic and the WPA 4-way handshake. The wireless client and AP have the PMK, which should last the entire session, so it should not be exposed. To accomplish this, we use different keys derived from the PMK.
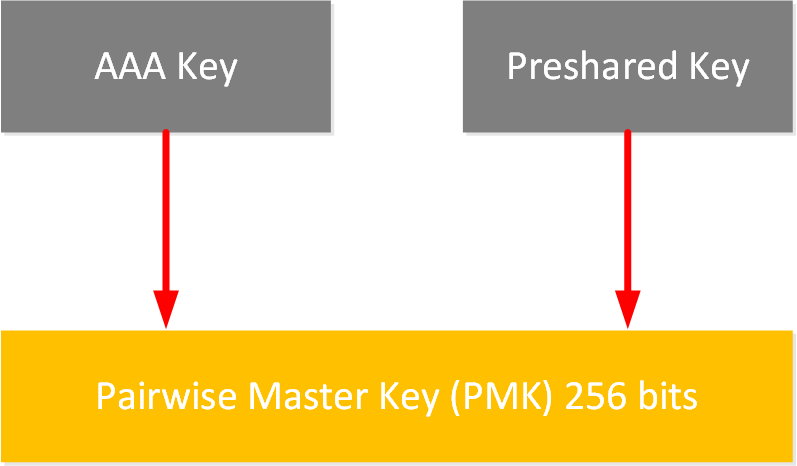
There are two options to define this key:
- Pre-shared key
- AAA key
Let’s look at both options.
Pre-shared Key
As the name implies, the pre-shared key is a key that you configure manually. This is used for WPA-personal. You have two options to set the pre-shared key:
- Hexadecimal
- ASCII passphrase
Let’s look at both.
Hexadecimal
You could manually configure 64 hexadecimal characters, which equals 256 bits needed for the PMK. Some APs support this. It is, however, not very user-friendly.
ASCII Passphrase
The ASCII passphrase is the most common method.
You can enter an 8-63 ASCII characters passphrase. Depending on how long or short the passphrase is, you might have too few or too many bits for the PMK. A Password-Based Key Derivation Function 2 (PBKDF2) is used to create a 256-bit PMK.
AAA Key
A pre-shared key is not a secure option if you have many wireless clients because everyone uses the same pre-shared key. It’s also not scalable if you have a large enterprise wireless network. We can also use Authentication, Authorization, and Accounting (AAA) and 802.1X, also known as WPA-enterprise.
The AAA key is also called the Master Session Key (MSK).
When you use 802.1X, the authentication server (typically RADIUS) derives the PMK and exports it to the wireless client and AP. This is done using RADIUS attribute MS-MPPE-Recv-key (vendor_id=17). Each EAP method defines its own way of deriving the PMK.
The advantage of this solution is that each wireless client and AP use their own PMK, and it is a central solution. The downside is that setting this up is more complex than pre-shared keys.
Pairwise Transient Key (PTK)
The Pairwise Transient Key (PTK) is used for encryption and integrity checks in unicast user data. It is also used for protecting the 4-way handshake. Here’s how to visualize this:
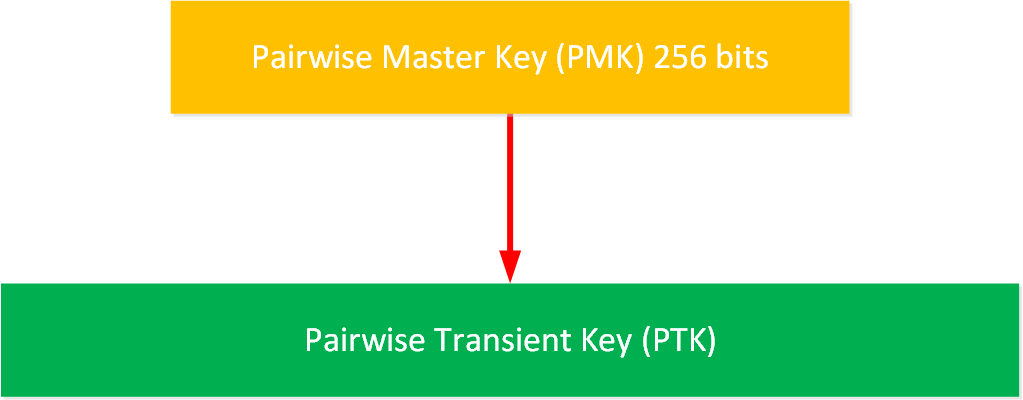
The PTK is derived by combining these attributes:
- PMK
- AP Nonce (Anonce)
- STA Nonce (Snonce)
- AP MAC address
- STA MAC address
These attributes are inserted in a pseudo-random function (PRF); the output is the PTK.
As you can see, the PMK is part of the input. The nonces are randomly generated values. Something extra is needed for the computation because if not, you would end up with the same temporal keys every time. This is achieved by adding nonces to the computation. The wireless client creates the STA Nonce (Snonce) and the AP the AP Nonce (Anonce).
The client’s and AP’s identities are also bound in the computation by including their MAC addresses.
The PTK is transient because every time a client associates with the AP, a new PTK is derived. The PTK key size depends on whether you use TKIP or AES-CCMP.
The PTK is used to protect two items:
- The WPA 4-way handshake
- User data
For these two items, we require encryption and integrity.
The WPA 4-way handshake creates the keys on the wireless client and AP and has to be protected.
The user data is the data that we encapsulate in 802.11 frames. More specifically, this is the MAC Service Data Unit (MSDU). The MSDU is the payload we receive from the network layer (layer three), sent to the data link layer (layer two). The Logical Link Control (LLC) sub-layer adds an LLC header. In a nutshell, it’s an IP packet with an LLC header.
The PTK is partitioned into multiple keys, and TKIP and AES-CCMP use different parts of the key differently. Let’s dive into this.
TKIP
Let’s start with TKIP. Here is an overview:
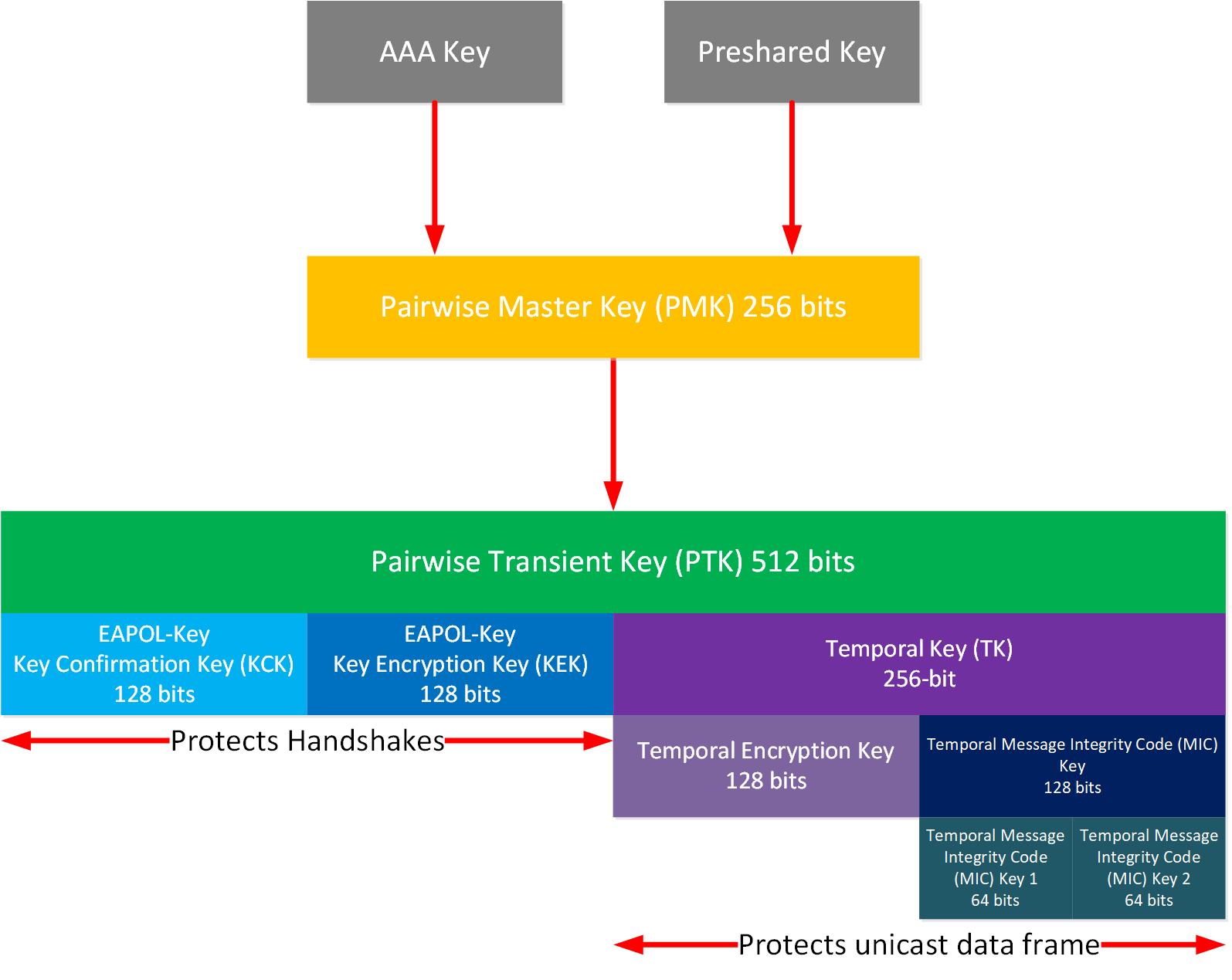
The PTK for TKIP is 512 bits and partitioned like this:
- EAPOL-Key Key Confirmation Key (KCK)
- EAPOL-Key Key Encryption Key (KEK)
- Temporal Key (TK)
- Temporal Encryption Key
- Temporal Message Integrity Code (MIC) Key
- Temporal MIC Key 1
- Temporal MIC Key 2
These are quite some keys. Let me walk you through them one by one.
EAPOL-Key Key Confirmation Key (KCK)
The first key is the EAPOL-Key Key Confirmation Key (KCK). This key is used for the integrity check of EAPOL-Key frames that we use in the WPA 4-way handshake. The KCK is 128 bits and uses bits 0-127 of the PTK.
EAPOL-Key Key Encryption Key (KEK)
The second key is the EAPOL-Key Key Encryption Key (KEK), which encrypts the Key Data field in an EAPOL-Key frame of the WPA 4-way handshake. The KEK is 128 bits and uses bits 128-255 of the PTK.
Temporal Key (TK)
The third key is the Temporal Key (TK), which we use for integrity checks and encryption in MSDUs. The TK is 256 bits and uses bits 256-511 of the PTK.
Let’s zoom in on this key:
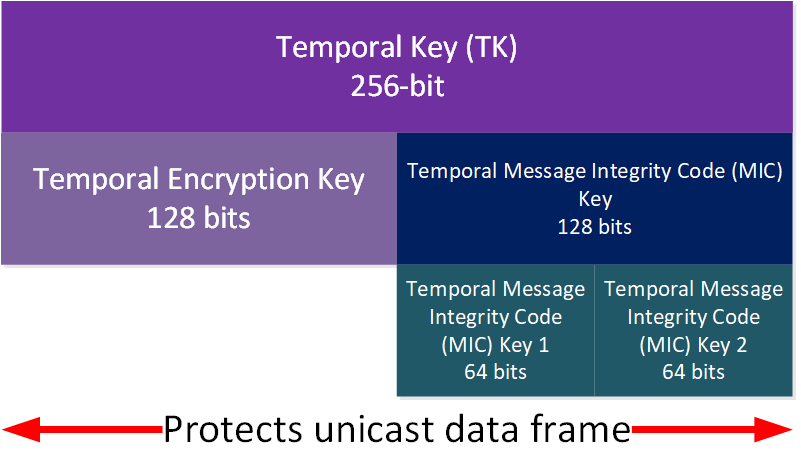
TKIP uses separate keys for encryption and integrity checks, so the TK is partitioned into the temporal encryption key and temporal message integrity code (MIC) key.
Temporal Encryption Key
This key is used to encrypt the MSDUs. Bits 0-127 of the TK are used for this.
Temporal Message Integrity Code (MIC) Keys
TKIP uses the Michael function. This is part of the temporal key we use for integrity checks of MSDUs or MPDUs. This key is partitioned into two MIC keys.
MIC Key 1
MIC Key 1 uses bits 128-191 of the TK as the Michael key for integrity checks in MSDUs sent from the AP to a wireless client.
MIC Key 2
MIC Key 2 uses bits 192-255 of the TK as the Michael key for integrity checks in MSDUs sent from the wireless client to the AP.
AES-CCMP
AES uses a more robust and modern cryptographic algorithm than TKIP and requires fewer keys and bits. Here is an overview:
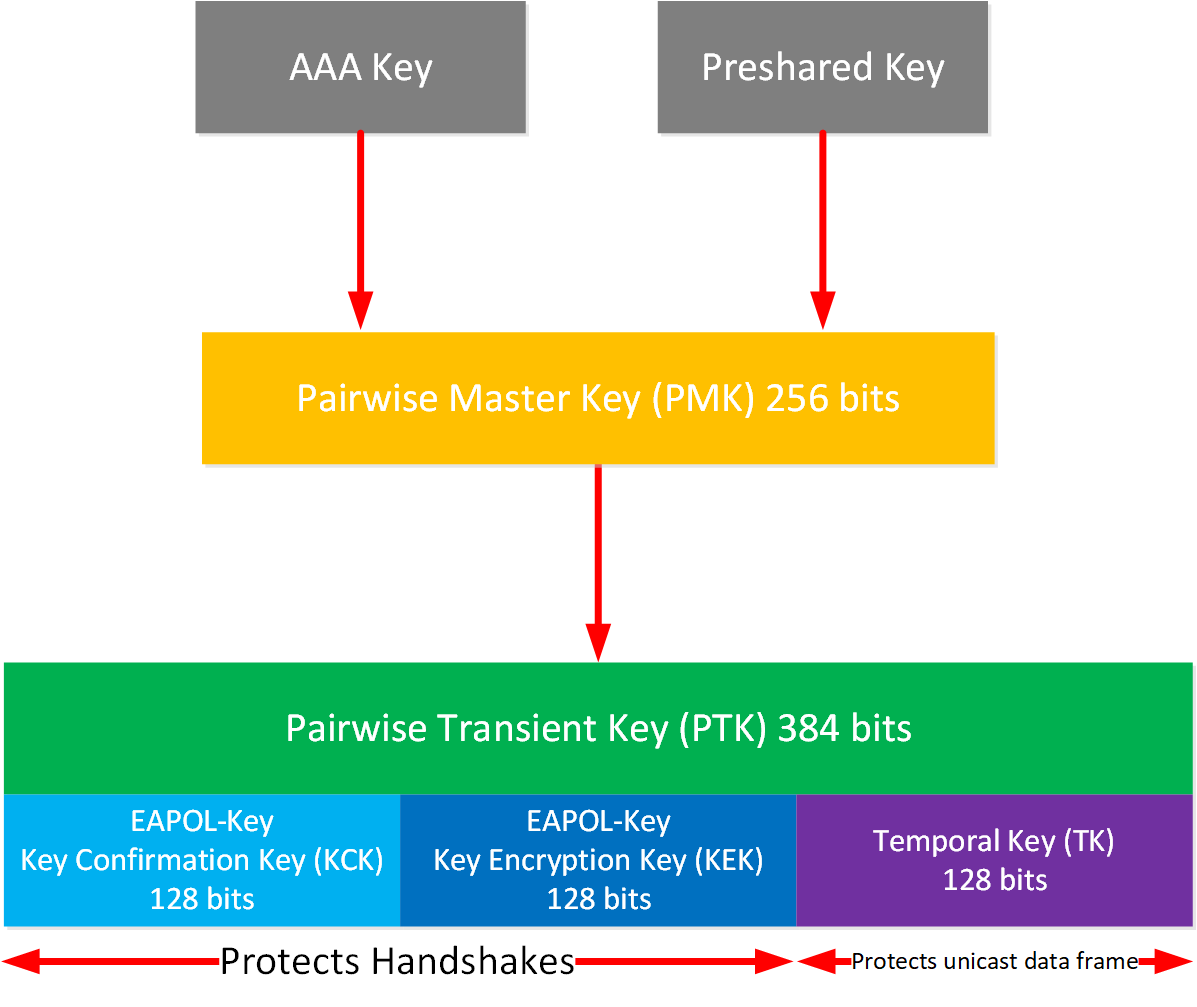
The PTK is 384 bits for AES-CCMP. It is partitioned like this:
- EAPOL-Key Key Confirmation Key (KCK)
- EAPOL-Key Key Encryption Key (KEK)
- Temporal Key (TK)
Let me walk you through these keys.
EAPOL-Key Key Confirmation Key (KCK)
The KCK is used for integrity checks in EAPOL-Key frames of the WPA 4-way handshake. This key is 128 bits, and we use bits 0-127 of the PTK.
EAPOL-Key Key Encryption Key (KEK)
The KEK is used for encryption in EAPOL-Key frames to protect the WPA 4-way handshake. This key is 128 bits, and we use bits 128-255 of the PTK.
Temporal Key (TK)
The TK is used for both encryption and integrity checks of MSDUs. This key is 128 bits, and we use bits 256-383 of the PTK.
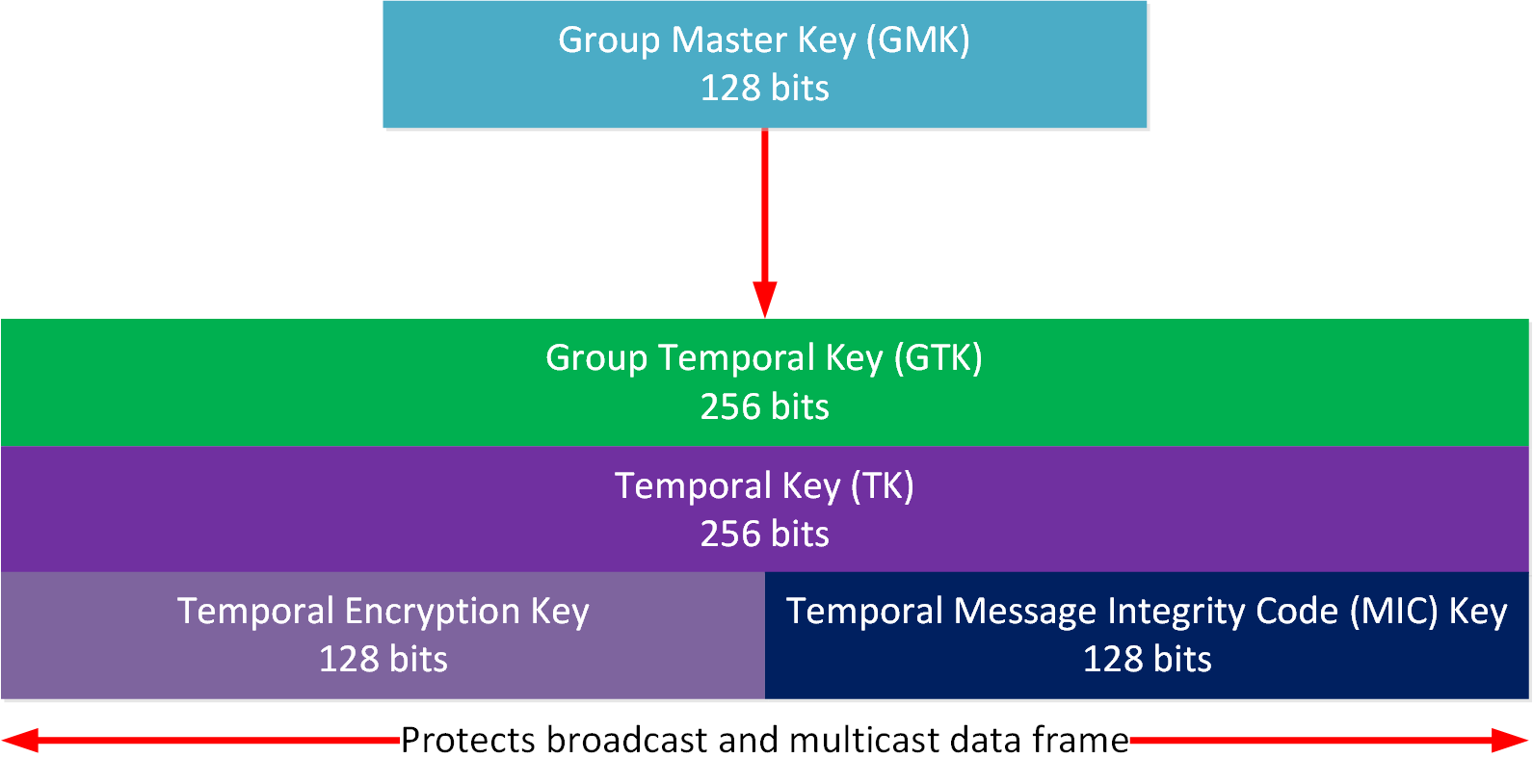
Group Master Key (GMK)
The group master key (GMK) is a 128-bit key at the top of the hierarchy for broadcast and multicast traffic. The AP generates a cryptographic-quality random number. The “cryptographic quality” part is important because some functions that generate random numbers are predictable. The GMK is not exchanged directly but is used to derive a group temporal key (GTK). The GMK can be regenerated periodically to reduce the risk of being compromised.
Group Temporal Key (GTK)
The GTK is derived from the GMK using a PRF and protects all broadcast and multicast traffic between the AP and wireless clients associated with the AP. All wireless clients use the same GTK.
During the WPA 4-way handshake, the GTK is sent from the AP to the wireless client. When the AP renews the GTK, it uses a group key handshake called a 2-way handshake.
The GTK is partitioned into multiple keys and differs for TKIP and AES-CCMP.
TKIP
Here’s what the TKIP keys look like:
Temporal Key (TK)
The GTK is partitioned into the 256-bit TK. The TK is further partitioned into two keys.
Temporal Encryption Key
The 128-bit temporal encryption key encrypts broadcast and multicast MSDU frames and uses bits 0-127 of the TK.
Temporal Message Integrity Code (MIC) Key
The temporal MIC key is 128 bits and is used for integrity checks in broadcast and multicast MSDU frames. It uses bits 128-255 from the TK.
AES-CCMP
Here are the AES-CCMP keys:
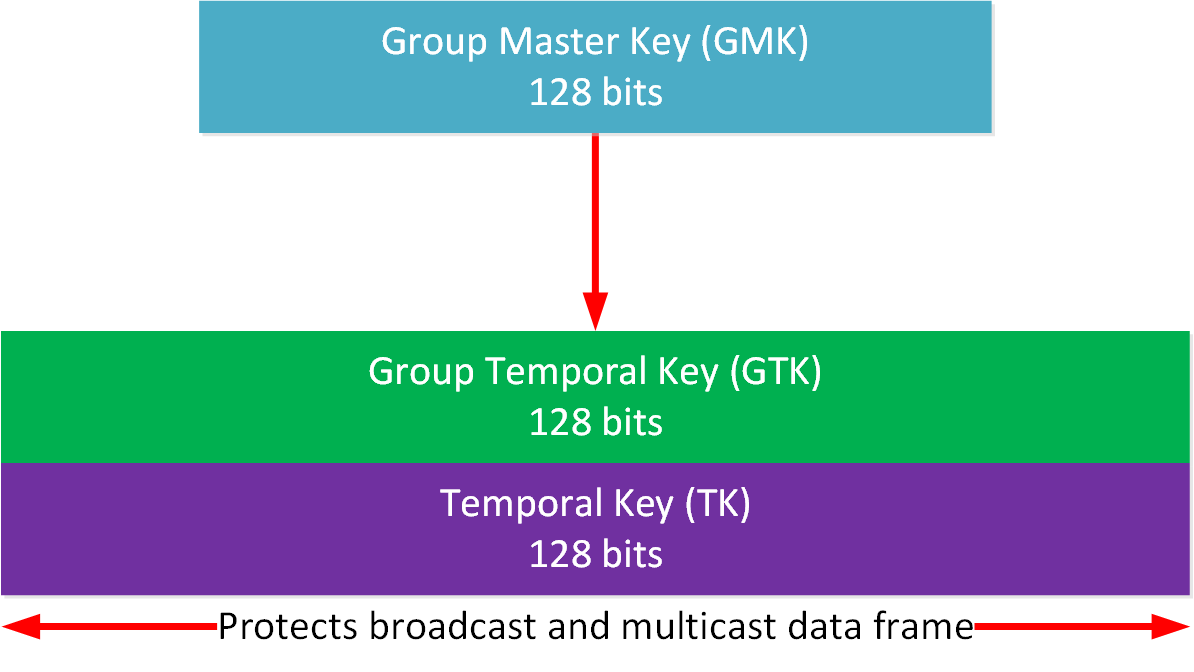
Temporal Key (TK)
Similar to the pairwise keys, AES-CCMP uses a single key for encryption and integrity. This key protects broadcast and multicast MSDU frames.
Conclusion
You have now learned what the WPA key hierarchy looks like and what the different keys are used for.
- Pairwise keys are used between a single wireless client and the AP.
- Group keys are used between multiple wireless clients and the AP.
- Key derivation is a cryptographic process that takes input and outputs a derived key.
- Key partitioning is the dividing of a key into a set of keys.
- The PMK is a 256-bit key created using a pre-shared or AAA key.
- The PTK is derived from the PMK with other attributes such as:
- Anonce
- Snonce
- AP MAC address
- STA MAC address.
- The PTK protects the WPA 4-way handshake and unicast traffic.
- The PTK is partitioned for TKIP like this:
- KCK
- KEK
- TK
- Temporal encryption key
- Temporal MIC key
- Temporal MIC key 1
- Temporal MIC key 2
- The PTK is partitioned for AES-CCMP like this:
- KCK
- KEK
- TK
- The GMK is generated by the AP and protects broadcast and multicast traffic.
- The GTK is derived from the GMK.
- The GTK is partitioned for TKIP like this:
- TK
- Temporal encryption key
- Temporal MIC key
- TK
- The GTK is partitioned for AES-CCMP like this:
- TK
- TKIP uses 768 bits in total:
- 512 bits for the PTK.
- 256 bits for the GTK.
- AES-CCMP uses 512 bits in total:
- 384 bits for the PTK.
- 128 bits for the GTK.
If you want to learn more about these keys, I suggest reading the IEEE 802.11i-2004 standard.
In the WPA 4-way lesson, we’ll see how these keys are actually created.
I hope you enjoyed this lesson. If you have any questions, feel free to leave a comment!
