Lesson Contents
VRRP (Virtual Router Redundancy Protocol) is an IETF standard protocol to create a redundant virtual gateway. It allows routers to create a virtual default gateway IP address where they share the same IP address. When the primary router fails, the backup router automatically takes over. This way, your end devices will always have a reachable default gateway. Without a virtual gateway, your end devices won’t be able to reach devices outside of their own subnet anymore unless you change their default gateway to another router.
VRRP is very similar to HSRP; if you understand HSRP, you’ll have no trouble with VRRP, which is a standard protocol defined by the IETF in RFC 3768. Configuration-wise it’s pretty much the same, but there are a couple of differences.
In this lesson, we will cover the key differences between VRRP and Hot Standby Routing Protocol (HSRP) and walk through the complete configuration and verification of VRRP on Cisco IOS devices.
Key Takeaways
- VRRP is an IETF standard protocol (RFC 3768)
- Uses master/backup terminology instead of active/standby
- Virtual MAC address format: 0000.5e00.01XX (where XX = group number)
- Default timers: hello timer 1 second, hold time 3 seconds
- Sends advertisements to multicast address 224.0.0.18
- Preemption is enabled by default (unlike HSRP)
- Virtual IP can be the same as a physical interface IP address
- Load balancing requires multiple VRRP groups with different priorities
- Default priority is 100 (higher wins master election)
- Supports object tracking but not direct interface tracking
Prerequisites
Before diving into VRRP, you should:
- Understand what a default gateway is.
- Understand what gateway redundancy is: You can read about this in our introduction to gateway redundancy lesson.
Configuration
Let’s see if we can configure it. This is the topology that I will use:
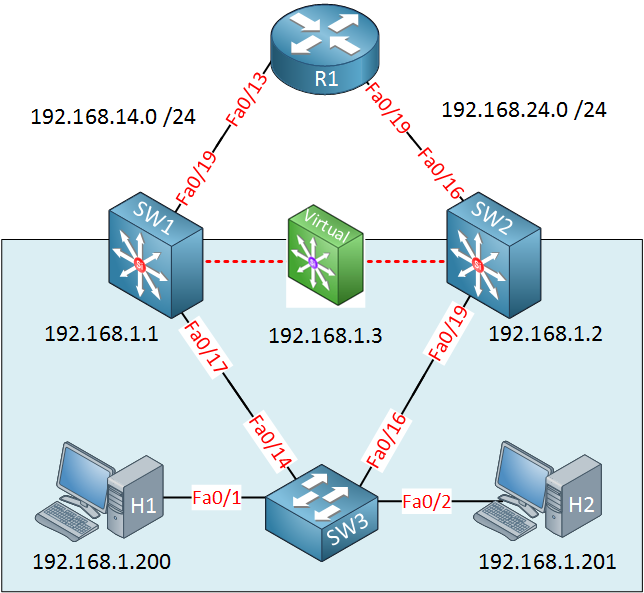
SW1 and SW2 are multilayer switches, and their interfaces are configured as routed ports. We will create a virtual gateway using VRRP on the interfaces facing SW3:
SW1(config)#interface fa0/17
SW1(config-if)#vrrp 1 ip 192.168.1.3
SW1(config-if)#vrrp 1 priority 150
SW1(config-if)#vrrp 1 authentication md5 key-string mykeySW2(config-if)#interface fa0/19
SW2(config-if)#vrrp 1 ip 192.168.1.3
SW2(config-if)#vrrp 1 authentication md5 key-string mykeyHere’s an example of how to configure VRRP. You can see the commands are pretty much the same, but I didn’t type standby but vrrp. I have changed the priority on SW1 to 150, and I’ve enabled MD5 authentication on both switches.
SW1#
%VRRP-6-STATECHANGE: Fa0/17 Grp 1 state Init -> Backup
%VRRP-6-STATECHANGE: Fa0/17 Grp 1 state Backup -> MasterSW2#
%VRRP-6-STATECHANGE: Fa0/19 Grp 1 state Init -> Backup
%VRRP-6-STATECHANGE: Fa0/19 Grp 1 state Backup -> Master
%VRRP-6-STATECHANGE: Fa0/19 Grp 1 state Master -> BackupYou will see these messages pop up in your console. VRRP uses different terminology than HSRP. SW1 has the best priority and will become the master router. SW2 will become a backup router. Let’s see what else we have:
SW1#show vrrp
FastEthernet0/17 - Group 1
State is Master
Virtual IP address is 192.168.1.3
Secondary Virtual IP address is 192.168.1.4
Virtual MAC address is 0000.5e00.0101
Advertisement interval is 1.000 sec
Preemption enabled
Priority is 150
Authentication MD5, key-string "mykey"
Master Router is 192.168.1.1 (local), priority is 150
Master Advertisement interval is 1.000 sec
Master Down interval is 3.414 secSW2#show vrrp
FastEthernet0/19 - Group 1
State is Backup
Virtual IP address is 192.168.1.3
Virtual MAC address is 0000.5e00.0101
Advertisement interval is 1.000 sec
Preemption enabled
Priority is 100
Authentication MD5, key-string "mykey"
Master Router is 192.168.1.1, priority is 150
Master Advertisement interval is 1.000 sec
Master Down interval is 3.609 sec (expires in 3.065 sec)Use show vrrp to verify your configuration. The output looks similar to HSRP; one of the differences is that VRRP uses another virtual MAC address:



You write the best articles of how to configure these things.
Well written, good job René!
Still how the computers uses both gateways in their configuration if we load balance between two groups?
Veerender
Hi Veerender,
For example, if you have 100 computers then you configure 50 of them to use 192.168.1.3 and the other 50 to use 192.168.1.4.
Rene
Hi Rene
I’m using for the lab Cisco Switches 3550 and 3750 as layer 3 switches, and those doesn’t seem to support VRRP or GLBP, what model are you using for this lab and the glbp lab, thank you and by the way, thank you for your last reply.
regards
Ramon
Hi Ramon,
The 3550 only supports HSRP while the 3750 supports HSRP + GLBP. I just checked my 3750 and this is the IOS image I am using:
c3750-advipservicesk9-mz.122-46.SE.bin
Funny thing is, I have a 3560 that runs the same IOS version but it only supports HSRP:
c3560-advipservicesk9-mz.122-46.SE.bin
Probably best to use some routers or GNS3 to test this.
Rene