Lesson Contents
Zone Based Firewall is the most advanced method of a stateful firewall available on Cisco IOS routers. The idea behind ZBF is that we don’t assign access-lists to interfaces, but we will create different zones. Interfaces will be assigned to the different zones, and security policies will be assigned to traffic between zones. To show you why ZBF is useful, let me show you a picture:
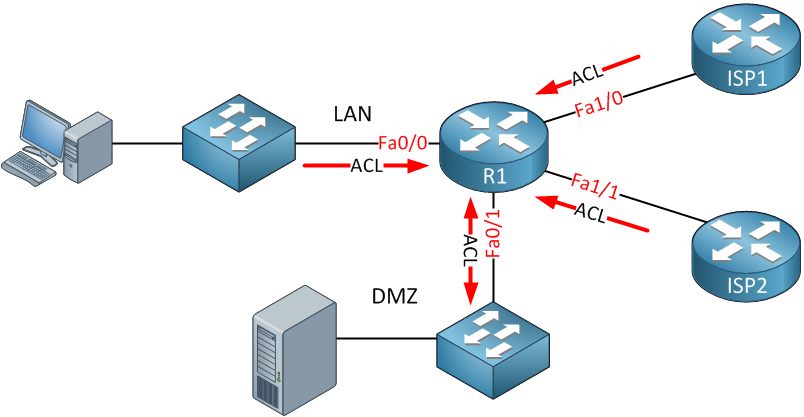
Above, you see a small network that has a LAN, DMZ, and WAN with two ISPs. Let’s say our security policy looks like this:
- Traffic from the LAN is allowed to the WAN but only to HTTP and HTTPS servers.
- Traffic from the LAN is allowed to the DMZ unrestricted.
- Traffic from the DMZ is not allowed to the LAN.
- Traffic from the DMZ is allowed to the WAN but only for the DNS and HTTP servers.
- Traffic from the WAN is allowed to the LAN but only to an FTP server.
If you want to achieve this using access lists, you’ll have to create multiple access lists and attach them to different interfaces inbound and/or outbound. To say the least, it becomes an administrative pain to do this. It’s possible but annoying.
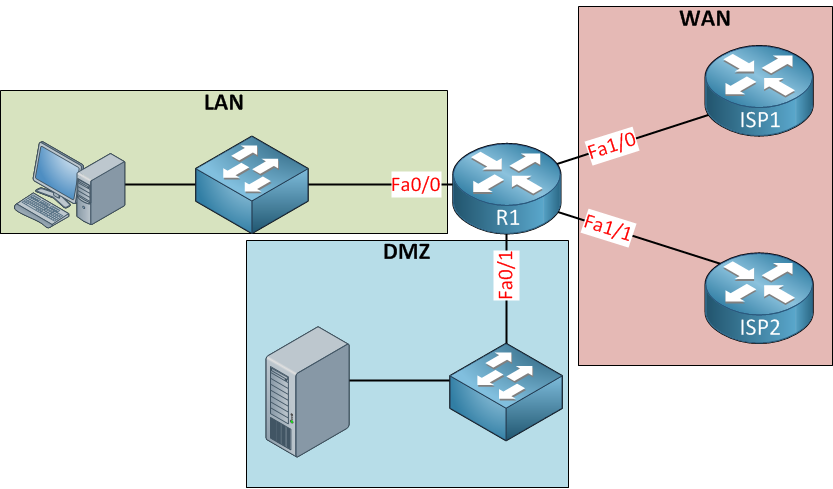
With the zone-based firewall, we won’t apply the security policies to the interfaces but to security zones. Interfaces will become members of the different zones. Here’s an example of the topology above with zones:
Above, you see three zones; LAN, WAN, and DMZ. The interfaces are assigned to the correct zone, and now we can apply security policies to traffic between zones. For example:
- LAN to WAN
- LAN to DMZ
- WAN to LAN
- WAN to DMZ
- DMZ to WAN
- DMZ to LAN
To create a security policy for traffic between zones we have to create a zone pair. We have to configure zone pairs and apply a security policy to them to determine what traffic is permitted from one zone to another. All security policies are attached to the zone pairs. Now you have an idea of what a zone-based firewall is, let me show you how to configure this.
Configuration
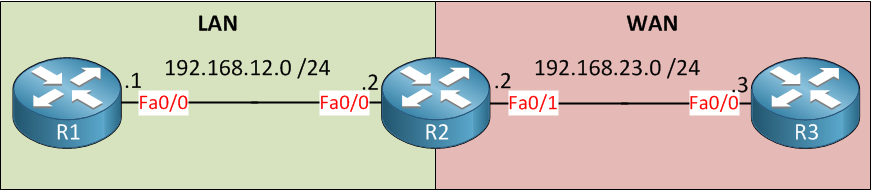
We will use the following topology:
Above, you see three routers and two zones called LAN and WAN. We will configure ZBF on R2. For connectivity, I’ll create a static route on R1 and R3 that points to R2:
R1(config)#ip route 0.0.0.0 0.0.0.0 192.168.12.2R3(config)#ip route 0.0.0.0 0.0.0.0 192.168.23.2Now we can configure the firewall.
Configure the Zones
First, we will create two zones. We only have two of them:
R2(config)#zone security LAN
R2(config)#zone security WANSecondly, we will assign the interfaces to the correct zone:
R2(config)#interface fastEthernet 0/0
R2(config-if)#zone-member security LANR2(config)#interface fastEthernet 0/1
R2(config-if)#zone-member security WANLet’s verify the configuration of the zones:
R2#show zone security
zone self
Description: System defined zone
zone LAN
Member Interfaces:
FastEthernet0/0
zone WAN
Member Interfaces:
FastEthernet0/1The zones are active, and interfaces have been assigned to them, now we can create the zone pairs.
Configure the Zone Pairs
R2(config)#zone-pair security LAN-TO-WAN source LAN destination WAN
R2(config-sec-zone-pair)#description LAN-TO-WAN TRAFFICR2(config)#zone-pair security WAN-TO-LAN source WAN destination LAN
R2(config-sec-zone-pair)#description WAN-TO-LAN TRAFFICAbove I create two zone pairs. One for traffic from our LAN to the WAN, and another for traffic from the WAN to our LAN. A description is optional but recommended if you have many zones. Let’s verify our configuration:
R2#show zone-pair security
Zone-pair name LAN-TO-WAN
Description: LAN-TO-WAN TRAFFIC
Source-Zone LAN Destination-Zone WAN
service-policy not configured
Zone-pair name WAN-TO-LAN
Description: WAN-TO-LAN TRAFFIC
Source-Zone WAN Destination-Zone LAN
service-policy not configuredNow we have zones, zone pairs, and interfaces that are assigned to the zones. By default, all traffic will be blocked. Let’s see if this is true:



Hello René
Networklessones.com is very informative…
thank you…
Glad you like it
Hi Rene,
Really good post to understand the concepts behind the zone based firewall.
Can you advise under what kind of network environments you would use zone based firewall?
Thank you,
Jay
Hi Jay,
The Zone Based Firewall is nice to use if you have an ISR with many interfaces that doesn’t run too much traffic and when you don’t have the budget to buy a separate firewall.
Rene
Thank you Rene . Clean , Simple and very informative.