Lesson Contents
In previous lessons I explained how you can filter routes within the OSPF area and how you can filter type 3 LSAs. This time we’ll take a look how you can filter type 5 LSAs using three different methods.
Here’s the topology we will use for this:
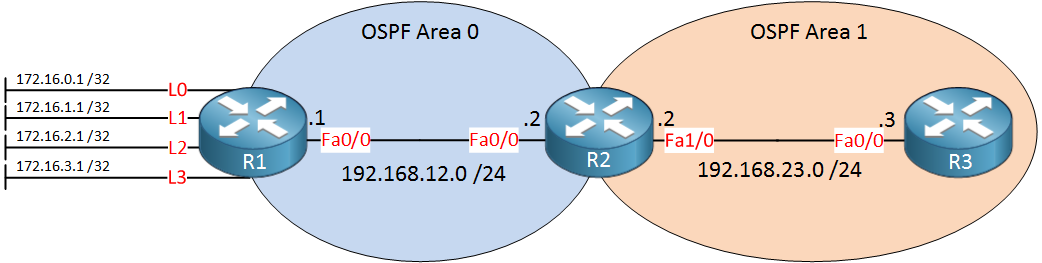
Above we have three routers in two different areas. R1 has some loopback interfaces that we will redistribute into OSPF. We’ll use these to play with some of the filtering techniques.
Configuration
Here’s the OSPF configuration of all routers:
R1#show running-config | section ospf
router ospf 1
redistribute connected subnets
network 192.168.12.0 0.0.0.255 area 0R2#show running-config | section ospf
router ospf 1
network 192.168.12.0 0.0.0.255 area 0
network 192.168.23.0 0.0.0.255 area 1R3#show running-config | section ospf
router ospf 1
network 192.168.23.0 0.0.0.255 area 1R1 is using the redistribute connected subnets command to get the networks on the loopback interfaces in OSPF. Let’s see if R2 and R3 have these networks in their routing table:
R2#show ip route ospf
172.16.0.0/32 is subnetted, 4 subnets
O E2 172.16.0.1 [110/20] via 192.168.12.1, 00:00:03, FastEthernet0/0
O E2 172.16.1.1 [110/20] via 192.168.12.1, 00:00:03, FastEthernet0/0
O E2 172.16.2.1 [110/20] via 192.168.12.1, 00:00:03, FastEthernet0/0
O E2 172.16.3.1 [110/20] via 192.168.12.1, 00:00:03, FastEthernet0/0R3#show ip route ospf
172.16.0.0/32 is subnetted, 4 subnets
O E2 172.16.0.1 [110/20] via 192.168.23.2, 00:00:07, FastEthernet0/0
O E2 172.16.1.1 [110/20] via 192.168.23.2, 00:00:07, FastEthernet0/0
O E2 172.16.2.1 [110/20] via 192.168.23.2, 00:00:07, FastEthernet0/0
O E2 172.16.3.1 [110/20] via 192.168.23.2, 00:00:07, FastEthernet0/0
O IA 192.168.12.0/24 [110/2] via 192.168.23.2, 00:04:25, FastEthernet0/0Everything is there. Now let’s see if we can filter these…
Distribute-list Filtering
The first method is the distribute-list. We can use this on the ASBR to filter certain networks from entering the area. Let’s configure one to get rid of 172.16.0.1 /32:
R1(config)#ip access-list standard R1_L0
R1(config-std-nacl)#deny host 172.16.0.1
R1(config-std-nacl)#permit any
R1(config)#router ospf 1
R1(config-router)#distribute-list R1_L0 outWe will use an outbound distribute-list with an access-list that matches the network (host route). Let’s see if it works:
R2#show ip route ospf
172.16.0.0/32 is subnetted, 3 subnets
O E2 172.16.1.1 [110/20] via 192.168.12.1, 00:10:12, FastEthernet0/0
O E2 172.16.2.1 [110/20] via 192.168.12.1, 00:10:12, FastEthernet0/0
O E2 172.16.3.1 [110/20] via 192.168.12.1, 00:10:12, FastEthernet0/0R3#show ip route ospf
172.16.0.0/32 is subnetted, 3 subnets
O E2 172.16.1.1 [110/20] via 192.168.23.2, 00:10:12, FastEthernet0/0
O E2 172.16.2.1 [110/20] via 192.168.23.2, 00:10:12, FastEthernet0/0
O E2 172.16.3.1 [110/20] via 192.168.23.2, 00:10:12, FastEthernet0/0
O IA 192.168.12.0/24 [110/2] via 192.168.23.2, 00:14:30, FastEthernet0/0The entry has dissapeared from the routing tables of R2 and R3.
Redistribution with Route-Map
The previous example works but there’s a better solution. Why not prevent certain routes from being redistributed in the first place? Technically this isn’t “filtering” but it works very well.
Let’s see what the current redistribute command looks like now:
R1#show running-config | include redistribute
redistribute connected subnetsWe’ll create a route-map that denies 172.16.1.1 /32 from being redistributed while we allow everything else. When it’s finished we’ll attach it to the redistribute command above:
R1(config)#ip access-list standard R1_L1
R1(config-std-nacl)#permit host 172.16.1.1
R1(config)#route-map CONNECTED_TO_OSPF deny 10
R1(config-route-map)#match ip address R1_L1
R1(config)#route-map CONNECTED_TO_OSPF permit 20
R1(config)#router ospf 1
R1(config-router)#redistribute connected subnets route-map CONNECTED_TO_OSPFThe route-map above will deny 172.16.1.1 /32 and permits everything else. After attaching it to the redistribute command you’ll see this on R2 and R3:
R2#show ip route ospf
172.16.0.0/32 is subnetted, 2 subnets
O E2 172.16.2.1 [110/20] via 192.168.12.1, 00:00:03, FastEthernet0/0
O E2 172.16.3.1 [110/20] via 192.168.12.1, 00:00:03, FastEthernet0/0R3#show ip route ospf
172.16.0.0/32 is subnetted, 2 subnets
O E2 172.16.2.1 [110/20] via 192.168.23.2, 00:00:07, FastEthernet0/0
O E2 172.16.3.1 [110/20] via 192.168.23.2, 00:00:07, FastEthernet0/0
O IA 192.168.12.0/24 [110/2] via 192.168.23.2, 00:20:34, FastEthernet0/0It’s gone from the routing table…mission accomplished! Let’s take a look at the final method…



Hello,
I know the using the distribute-list filters the route from getting to the RIB. But it still creates an LSA type 5. Regarding the other two methods does it stop the creation of the type 5 LSA and this filtering has to be done on the ASBR correct?
Thank you
Hello,
Just to be sure : It’s outbound distribute-list which have to be apply on the ASBR ospf configuration yes ?
Thank you
Hi Sebastien,
That’s right. I see a left a typo in the article, it says “inbound” while the distribute-list itself is outbound. Just fixed this.
Rene
Hi,
Please help me with below query:
what is the difference between “distribute list out” and “distribute list in” during redistruibution ?
Hello Pradeep!
In order to filter type 5 LSAs we must use the “out” keyword when implementing a distribute-list. The “out” keyword indicates that we are filtering LSA type 5, and thus we are filtering routes that are redistributed from external sources. Whereas the “in” keyword is used when we want to remove a route from from the routing table.
I hope this was helpful!
Laz