Lesson Contents
Router IP Traffic Export (RITE) which is also known as IP Traffic Export is useful to export IP packets to an interface or VLAN of choice. This is very useful when you have an IDS (Intrusion Detection System) and want to inspect your traffic.
RITE is similar to SPAN on the Cisco Catalyst Switches. In this lesson, I will explain how to configure RITE so you can export your IP packets.
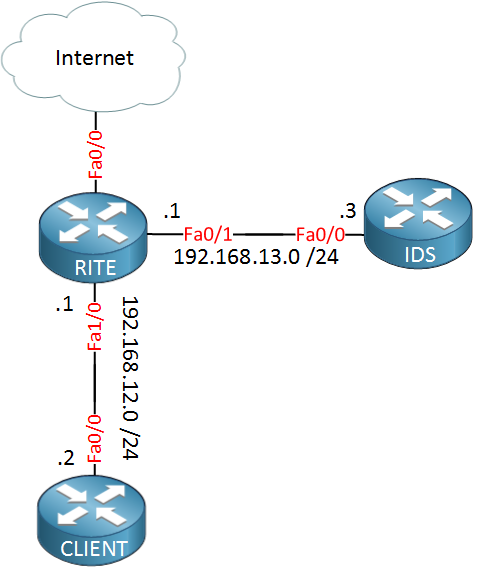
This is the topology I will use:
At the bottom we have a router that will simulate a client device that is accessing the Internet. On the right side you see a router called “IDS” which simulates our Intrusion Detection System. Whenever the client accesses the Internet, the router in the middle called “RITE” will export the IP packets towards the IDS. Let’s start with the configuration.
Configuration
When you configure Router IP Traffic Export you have to specify a name:
RITE(config)#ip traffic-export profile MY_RITE
RITE(conf-rite)#This takes you to the main RITE configuration. There are a couple of options here:
RITE(conf-rite)#?
IP traffic export profile configuration commands
bidirectional Enable bidirectional traffic export
exit Exit from ip traffic export profile sub mode
incoming Configure incoming IP traffic export
interface Specify outgoing interface for exporting traffic
mac-address Specify ethernet address of destination host
no Negate or set default values of a command
outgoing Configure outgoing IP traffic exportFirst, I will specify the interface where we want to export the IP packets to. This will be FastEthernet 0/1 which is connected to the IDS:
RITE(conf-rite)#interface fastEthernet 0/1If there are multiple devices behind the outgoing interface, then you should configure a destination MAC address. We’ll have to check the MAC address of the IDS first:
IDS#show interfaces fastEthernet 0/0
FastEthernet0/0 is up, line protocol is up
Hardware is Gt96k FE, address is c204.3bcc.0000And we’ll configure it in the RITE configuration:
RITE(conf-rite)#mac-address c204.3bcc.0000You can choose if you want to export inbound, outbound or both directions…I’ll pick both:
RITE(conf-rite)#bidirectionalInstead of copying all IP packets, we can also configure sampling. This means you will only export 1 out of X packets. Here’s an example:
RITE(conf-rite)#incoming sample one-in-every 5
RITE(conf-rite)#outgoing sample one-in-every 5Only 1 out of 5 IP packets will now be exported. The configuration is ready, but we still have the RITE profile on the interface where we want to capture traffic:
RITE(config)#interface FastEthernet 1/0
RITE(config-if)#ip traffic-export apply MY_RITEThis will capture traffic from the interface that is connected to the client. On your console, you’ll see something like this:
RITE#
%RITE-5-ACTIVATE: Activated IP traffic export on interface FastEthernet1/0That’s all there is to it. The only thing left to do is verify if it’s working…
Verification
To test RITE, I’ll enable a debug on the IDS router so we can see all incoming packets:
IDS#debug ip packet
IP packet debugging is onNow, we’ll generate some packets from the client, and if everything is configured correctly, some of these packets will be forwarded to the IDS router:



Hi Rene,
I think the interfaces on your diagram are wrong on the Router RITE cause you mentioned f0/1 but there is none.
Thanks
Thanks Alfredo, just fixed the image.
Hello Rene, thanks for the explanation. The question I have is: should returned traffic be inspected or forwarded to the IDS, instead of the client’s traffic? We assume internal traffic is trusted, right?
Hi Jose,
If you want to use RITE to forward traffic to an IDS/IPS then yes, it’s probably the traffic from outside to inside that you want to forward and inspect.
We don’t always trust internal traffic 100% btw. For example, a few weeks ago I used an ASA with firepower that is used to inspect all outgoing traffic. It can be used to drop certain traffic that the hosts are not allowed to use.
Rene
Hello Rene,
Nice. Is there any option to Monitor Traffic Remotely like RSPAN on Router port ??
br//
zaman