Lesson Contents
DHCP snooping is a technique where we configure our switch to listen in on DHCP traffic and stop any malicious DHCP packets. This is best explained with an example, so take a look at the picture below:
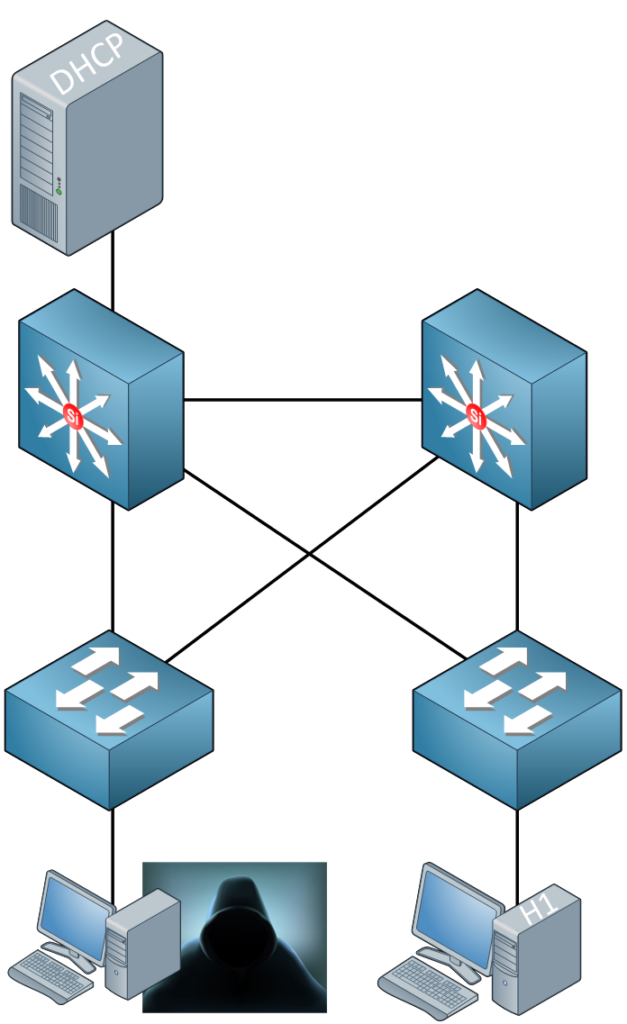
In the picture above, I have a DHCP server connected to the switch on the top left. At the bottom right, you see a legitimate client that would like to get an IP address. What if the l33t hacker script kiddy on the left would run DHCP server software on his computer? Who do you think will respond first to the DHCP discover message? The legitimate DHCP server or the script kiddy’s DHCP server software?
On larger networks, you will probably find a central DHCP server somewhere in the server farm. If an attacker runs a DHCP server in the same subnet, he will likely respond faster to the DHCP discover message of the client. If this succeeds, he might assign the client with the attacker’s IP address as the default gateway for a man-in-the-middle attack. Another option would be to send the attacker’s IP address as the DNS server so you can spoof websites, etc.
The attacker could also send DHCP discover messages to the DHCP server and try to deplete its DHCP pool. So what can we do to stop this madness? DHCP snooping to the rescue! We can configure our switches so they track the DHCP discover and DHCP offer messages. Here’s how:
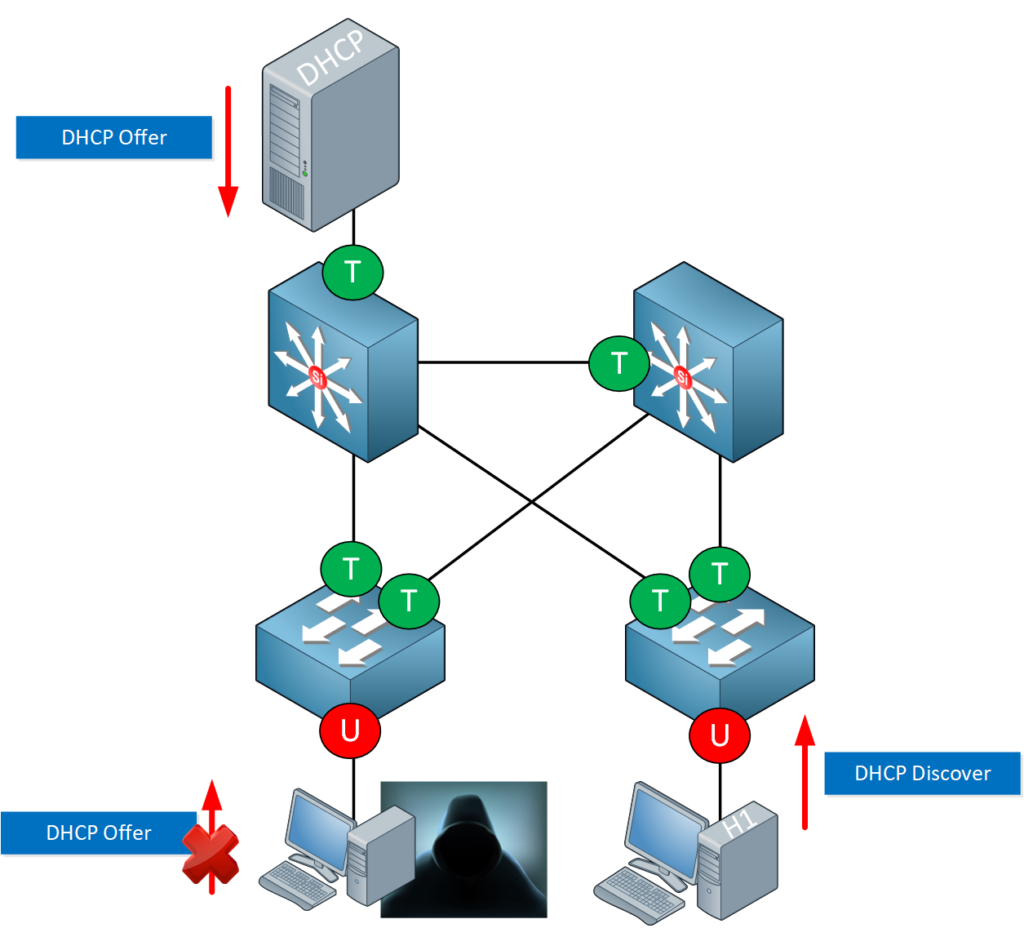
Interfaces that connect to clients should never be allowed to send a DHCP offer message. We can enforce this by making them untrusted. An untrusted interface will block DHCP offer messages. Only an interface configured as trusted is allowed to forward DHCP offer messages. We can also rate-limit interfaces so they can’t send an unlimited amount of DHCP discover messages. This will prevent attacks from depleting the DHCP pool.
Let’s see how we can configure DHCP snooping…



Hi Rene,
question, I’m working with cisco 3550 switch, version 12.1 (13) , (C3550-I5Q3L2-M), and it doesn’t have the option # ip dhcp snooping, under # ip dhcp just have this options (conflict, database, excluded-address, limited-broadcast-address, ping, pool, relay, smart-relay). what should i do, it seems to be a version issue, what version should i upgrade the switch or any other advice.
thanks
Ramon
Hi Ramon,
It’s probably the version since the 3550 does support DHCP snooping. It’s best to get one of the “IP services” images. This is what you should do:
Go to Cisco.com -> Support.
Select the 3550.
Select Download Software.
Select one of the EMI versions.
Select Downloads.
Select IOS Software.
The latest “IP services” version is “c3550-ipservices-mz.122-44.SE6.bin” but an older version would also work.
Here’s the direct link if you want:
... Continue reading in our forumhttps://software.cisco.com/download/release.html?mdfid=275935148&softwareid=280805680&os=&release=12.2.44-SE6
Hi Rene, could you describe using your simply language, for what we need option 82?
Hi Yevgeniy,
DHCP Option 82 stands for “DHCP Relay Agent Information Option”. If you haven’t seen how DHCP relay works before, take a look at this lesson:
https://networklessons.com/ip-services/cisco-ios-dhcp-relay-agent
Option 82 was originally created for really large (WAN) networks where we have a lot of DHCP relays and central DHCP servers. The idea behind it is that the DHCP relay can add extra information which the DHCP server can use to decide which pool to use for assigning an IP address. Option 82 has a “Circuit ID” and a “Remote ID”.
The Circuit ID h
... Continue reading in our forumHi Rene,
If we consider configuring DHCP SNOOPING on your first diagram with 4 switches and those switches are trunking, would you configure all those trunks or port-channels as dhcp snooping trusted? or will you configure the SVI’s on the Core switches as trusted? Which is the best way to configure them.
Please advise