External BGP uses a simple loop prevention mechanism: when you see your own AS number in the AS path, we don’t accept the prefix. There are some scenarios where this might be an issue. Take a look at the following topology:
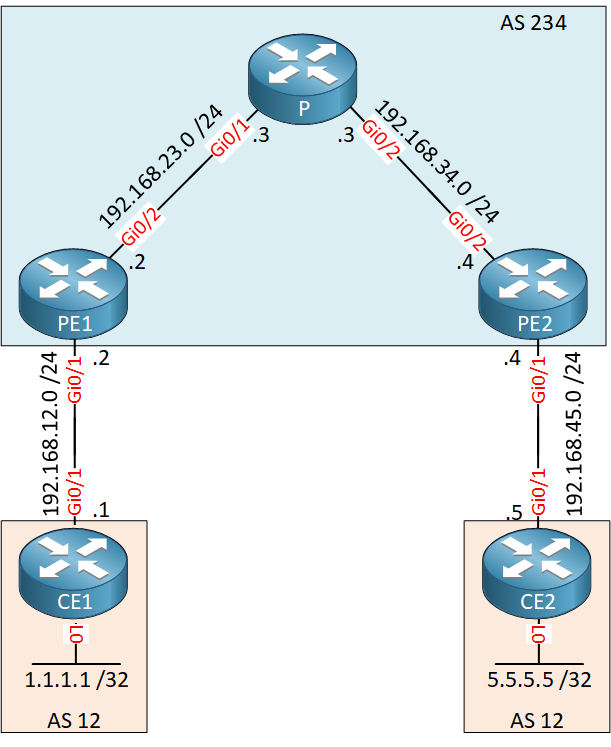
Above we have a MPLS VPN network where the customer is using the same AS number (12) on both sites. CE1 and CE2 will be unable to learn each others prefixes since they are using the same AS number.
Let’s see if this is true, here are the configurations of all routers if you want to test this yourself:
Configurations
Here you will find the startup configurations of each device.
CE1
hostname CE1
!
interface Loopback0
ip address 1.1.1.1 255.255.255.255
!
interface GigabitEthernet0/1
ip address 192.168.12.1 255.255.255.0
duplex auto
speed auto
media-type rj45
!
router bgp 12
bgp log-neighbor-changes
network 1.1.1.1 mask 255.255.255.255
neighbor 192.168.12.2 remote-as 234
!
end
PE1
hostname PE1
!
ip vrf CUSTOMER
rd 1:1
route-target export 1:1
route-target import 1:1
!
ip cef
!
interface Loopback0
ip address 2.2.2.2 255.255.255.255
!
interface GigabitEthernet0/1
ip vrf forwarding CUSTOMER
ip address 192.168.12.2 255.255.255.0
duplex auto
speed auto
!
interface GigabitEthernet0/2
ip address 192.168.23.2 255.255.255.0
duplex auto
speed auto
mpls ip
!
router ospf 1
network 2.2.2.2 0.0.0.0 area 0
network 192.168.23.0 0.0.0.255 area 0
!
router bgp 234
bgp log-neighbor-changes
neighbor 4.4.4.4 remote-as 234
neighbor 4.4.4.4 update-source Loopback0
!
address-family ipv4
no neighbor 4.4.4.4 activate
exit-address-family
!
address-family vpnv4
neighbor 4.4.4.4 activate
neighbor 4.4.4.4 send-community extended
exit-address-family
!
address-family ipv4 vrf CUSTOMER
neighbor 192.168.12.1 remote-as 12
neighbor 192.168.12.1 activate
exit-address-family
!
endP
hostname P
!
interface Loopback0
ip address 3.3.3.3 255.255.255.255
!
interface GigabitEthernet0/1
ip address 192.168.23.3 255.255.255.0
duplex auto
speed auto
mpls ip
!
interface GigabitEthernet0/2
ip address 192.168.34.3 255.255.255.0
duplex auto
speed auto
mpls ip
!
router ospf 1
network 3.3.3.3 0.0.0.0 area 0
network 192.168.23.0 0.0.0.255 area 0
network 192.168.34.0 0.0.0.255 area 0
!
endPE2
hostname PE2
!
ip vrf CUSTOMER
rd 1:1
route-target export 1:1
route-target import 1:1
!
ip cef
!
interface Loopback0
ip address 4.4.4.4 255.255.255.255
!
interface GigabitEthernet0/1
ip vrf forwarding CUSTOMER
ip address 192.168.45.4 255.255.255.0
duplex auto
speed auto
!
interface GigabitEthernet0/2
ip address 192.168.34.4 255.255.255.0
duplex auto
speed auto
mpls ip
!
router ospf 1
network 4.4.4.4 0.0.0.0 area 0
network 192.168.34.0 0.0.0.255 area 0
!
router bgp 234
bgp log-neighbor-changes
neighbor 2.2.2.2 remote-as 234
neighbor 2.2.2.2 update-source Loopback0
!
address-family ipv4
no neighbor 2.2.2.2 activate
exit-address-family
!
address-family vpnv4
neighbor 2.2.2.2 activate
neighbor 2.2.2.2 send-community extended
exit-address-family
!
address-family ipv4 vrf CUSTOMER
neighbor 192.168.45.5 remote-as 12
neighbor 192.168.45.5 activate
exit-address-family
!
endCE2
hostname CE2
!
ip cef
!
interface Loopback0
ip address 5.5.5.5 255.255.255.255
!
interface GigabitEthernet0/1
ip address 192.168.45.5 255.255.255.0
duplex auto
speed auto
!
router bgp 12
bgp log-neighbor-changes
network 5.5.5.5 mask 255.255.255.255
neighbor 192.168.45.4 remote-as 234
!
endEach CE router has a loopback interface that was advertised in BGP (1.1.1.1/32 and 5.5.5.5/32). The first thing to check is to see if the PE routers have learned the prefixes from our CE routers:
PE1#show ip bgp vpnv4 all
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 1:1 (default for vrf CUSTOMER)
*> 1.1.1.1/32 192.168.12.1 0 0 12 i
*>i 5.5.5.5/32 4.4.4.4 0 100 0 12 iPE2#show ip bgp vpnv4 all
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 1:1 (default for vrf CUSTOMER)
*>i 1.1.1.1/32 2.2.2.2 0 100 0 12 i
*> 5.5.5.5/32 192.168.45.5 0 0 12 iAbove you can see that both PE routers have a VPN route for these prefixes. Did they advertise these prefixes to our CE routers?
PE1#show ip bgp vpnv4 all neighbors 192.168.12.1 advertised-routes
BGP table version is 16, local router ID is 2.2.2.2
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 1:1 (default for vrf CUSTOMER)
*>i 5.5.5.5/32 4.4.4.4 0 100 0 12 i
Total number of prefixes 1PE2#show ip bgp vpnv4 all neighbors 192.168.45.5 advertised-routes
BGP table version is 18, local router ID is 4.4.4.4
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 1:1 (default for vrf CUSTOMER)
*>i 1.1.1.1/32 2.2.2.2 0 100 0 12 i
Total number of prefixes 1No issues there, our PE routers are advertising these prefixes to the CE routers. Let’s see what we find in the BGP tables of the CE routers:
CE1#show ip bgp
Network Next Hop Metric LocPrf Weight Path
*> 1.1.1.1/32 0.0.0.0 0 32768 iCE2#show ip bgp
Network Next Hop Metric LocPrf Weight Path
*> 5.5.5.5/32 0.0.0.0 0 32768 iThe CE routers only have their own prefixes in their BGP tables. Why did they refuse the updates from the PE routers? Time for a debug:
CE1#debug ip bgp all updates
BGP updates debugging is on for all address familiesLet’s reset the BGP neighbor adjacency:
CE1#clear ip bgp *Here’s what you will see on the CE1 router:
CE1# BGP(0): 192.168.12.2 rcv UPDATE about 5.5.5.5/32 -- DENIED due to: AS-PATH contains our own AS;
As expected, the CE1 router denies the update since it sees its own AS number in the AS path. If we don’t want to change our AS numbers then there’s two ways to deal with this:
- Use Allow-AS in to overrule the loop prevention mechanism of external BGP.
- Use AS override to change the AS number on the PE routers.
This lesson is about allow-AS in so that’s what we will do this time:
CE1(config)#router bgp 12
CE1(config-router)#neighbor 192.168.12.2 allowas-inCE1 is now configured to allow prefixes with its own AS number from the PE1 router. If you left the debug enabled then you will see this:
CE1#
BGP(0): Revise route installing 1 of 1 routes for 5.5.5.5/32 -> 192.168.12.2(global) to main IP tableThat should take care of our problem. Let’s see if the prefix has been installed:
CE1#show ip route 5.5.5.5
Routing entry for 5.5.5.5/32
Known via "bgp 12", distance 20, metric 0
Tag 234, type external
Last update from 192.168.12.2 00:01:13 ago
Routing Descriptor Blocks:
* 192.168.12.2, from 192.168.12.2, 00:01:13 ago
Route metric is 0, traffic share count is 1
AS Hops 2
Route tag 234
MPLS label: noneThere we go, it’s in the routing table. Don’t forget to configure the same change on CE2:
CE2(config)#router bgp 12
CE2(config-router)#neighbor 192.168.45.4 allowas-inCE2 should now accept 1.1.1.1/32:
CE2#show ip route 1.1.1.1
Routing entry for 1.1.1.1/32
Known via "bgp 12", distance 20, metric 0
Tag 234, type external
Last update from 192.168.45.4 00:00:45 ago
Routing Descriptor Blocks:
* 192.168.45.4, from 192.168.45.4, 00:00:45 ago
Route metric is 0, traffic share count is 1
AS Hops 2
Route tag 234
MPLS label: noneThat’s looking good. One final check left, let’s see if there is connectivity between 1.1.1.1 and 5.5.5.5:
CE1#ping 5.5.5.5 source loopback 0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 5.5.5.5, timeout is 2 seconds:
Packet sent with a source address of 1.1.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 7/9/11 msExcellent it’s working.
Want to take a look at the complete configurations yourself?


Hi Rene,
I want to know the configuration, where the customer will be using bgp protocol.
what will be the steps for CE1 to PE1, PE1-P-PE2, CE2to PE2.
kindly reply.
S Alladi
Hi S,
Here is a step-by-step walkthrough:
https://networklessons.com/mpls/mpls-layer-3-vpn-configuration
Rene
Hi Rene,
Thanks! Very Good explanation.
Davis
HI Rene,
you mentioned two methods to solve the two same AS issue.
Use Allow-AS in to overrule the loop prevention mechanism of external BGP.
Use AS override to change the AS number on the PE routers.
my question is that among both method which method should I use for which situation?
thanks,
Nyi Nyi.
Hi Nyi Nyi,
Both will get the job done, the main difference is that allow AS in is configured on the customer routers and AS override is done on the SP routers. In the real world you probably don’t have access to both the customer and SP routers so it’s possible that only one of the two options is available to you.
Rene