Lesson Contents
Cisco’s zone-based firewall is normally used with layer three interfaces, but you can also use it as a transparent firewall. If you have no idea what zone-based firewalls are, then I suggest you first take a look at my basic ZBF configuration example. If you haven’t configured layer two bridging before, you should start with the transparent IOS firewall example. Having said that, let’s configure a Zone based firewall in transparent mode. This is the topology that I will be using:
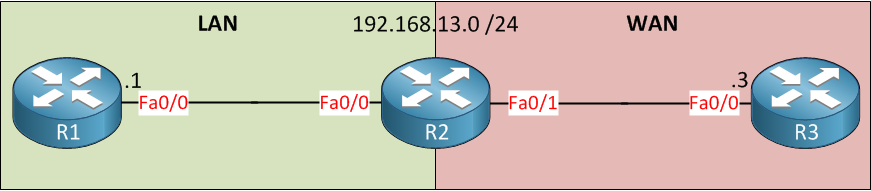
Above, we have three routers. R1 and R3 are in the same layer two segment because we’ll configure R2 to bridge the FastEthernet 0/0 and 0/1 interfaces. Once this is done, we’ll configure the Zone Based Firewall. I will use a very simple example, by default, all inter-zone traffic is denied. I want to configure R2 to permit only ICMP traffic from R1 to R3 (and the return traffic). Let’s get started!
Configuration
First, we’ll configure bridging:
R2(config)#bridge crb
R2(config)#bridge 1 protocol ieee
R2(config)#interface fastEthernet 0/0
R2(config-if)#bridge-group 1
R2(config)#interface fastEthernet 0/1
R2(config-if)#bridge-group 1I don’t need a layer three interface on R2, so we’ll go for concurrent routing and bridging with IEEE spanning tree. The two FastEhernet interfaces have been added to the bridge group.
bridge irb, the layer three bridge interface will automatically belong to the ZBF self zone.I will create a LAN and WAN zone. R1 will be in the LAN zone, and R3 in the WAN zone. We’ll also add the interfaces to the correct zone and create a zone pair for traffic from our LAN to the WAN.
R2(config)#zone security LAN
R2(config)#zone security WAN
R2(config)#interface fastEthernet 0/0
R2(config-if)#zone-member security LAN
R2(config)#interface fastEthernet 0/1
R2(config-if)#zone-member security WAN
R2(config)#zone-pair security LAN-TO-WAN source LAN destination WANWith the zones in place, we can create a security policy. We’ll use NBAR to match ICMP traffic and create a policy-map that uses the inspect rule:
R2(config)#class-map type inspect ICMP
R2(config-cmap)#match protocol icmp
R2(config)#policy-map type inspect LAN-TO-WAN
R2(config-pmap)#class ICMP
R2(config-pmap-c)#inspectLast but not least, we have to attach that policy-map to the zone pair:



Nice one…
hello mr.rene
thank you for this nice article
mr.rene i want to say something and wish you understand me because my english not strong too much
i love your way and your books it was so clear and helpful
i was wondering if you working on new books?
if not,so as one of people who loves your work i (kindly) suggest you make either
new “how to master” ccna/ccnp security books or “how to master” ccie r&s and recommend first one
i am sure there is people agree with me and i sure they trust in your work
so sorry that i talk too much
best wishes
Helpful to us.You carry us to key points.Thanks Mr.Rene Molenaar.
Best Regards,
Herbert.
Hi Rene,
Please help, I lab it up and it is not working. As shown in the show command below there is no icmp packet seen.
... Continue reading in our forumHi Kenneth,
The config looks ok. Without ZBF, can you ping between R1 and R3?
What did you use to test this? On Cisco VIRL, it doesn’t work for me. On real hardware it does.
Rene