CBAC (Context-Based Access Control) is a firewall for Cisco IOS routers that offers some more features than a simple access-list. CBAC is able to inspect up to layer 7 of the OSI model and can dynamically create rules to allow return traffic. It is similar to the reflexive access-list, but one of the key differences is that the reflexive ACL only inspects up to layer 4.
In this lesson, I’ll give you an example of CBAC, and you’ll see why this firewall feature is very useful. I’ll be using three routers for this:
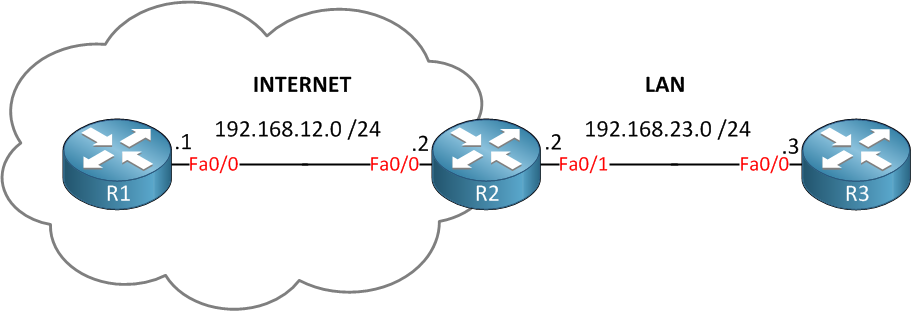
In the example above, we have three routers. Imagine the router on the left side (R1) is some device on the internet while R3 is a host on our LAN. R2 will be the router that is protecting us from traffic on the Internet, this is where we configure CBAC. Let’s start with the basic configuration…setting up IP addresses and some static routes for connectivity:
R1(config)#interface fastethernet 0/0
R1(config-if)#no shutdown
R1(config-if)#ip address 192.168.12.1 255.255.255.0R2(config)#interface fastethernet 0/0
R2(config-if)#no shutdown
R2(config-if)#ip address 192.168.12.2 255.255.255.0
R2(config-if)#interface fastethernet 0/1
R2(config-if)#no shutdown
R2(config-if)#ip address 192.168.23.2 255.255.255.0R3(config)#interface fastethernet 0/0
R3(config-if)#no shutdown
R3(config-if)#ip address 192.168.23.3 255.255.255.0And two static routes so R1 and R3 can reach each other:
R1(config)#ip route 0.0.0.0 0.0.0.0 192.168.12.2R3(config)#ip route 0.0.0.0 0.0.0.0 192.168.23.2Our idea is to protect our LAN from all the evil stuff on the Internet. In order to do so, we’ll create an access-list that drops everything from the Internet. The access-list looks like this:
R2(config)#ip access-list extended DENY_ALL_FROM_INTERNET
R2(config-ext-nacl)#deny ip any any log
R2(config)#interface fastEthernet 0/0
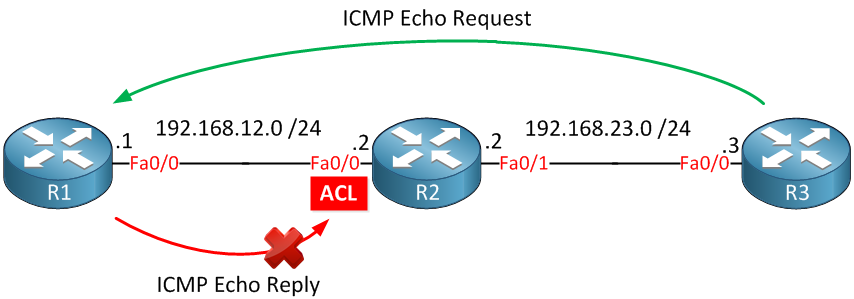
R2(config-if)#ip access-group DENY_ALL_FROM_INTERNET inThis access-list is very effective…it will drop everything from the Internet! I added the deny ip any any log so you can see dropped packets on the console. You don’t have to add it because everything is dropped by default, but it helps to show dropped packets. There’s one problem with this ACL; however, let’s see what happens when I send a ping from R3 to R1:
R3#ping 192.168.12.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.12.1, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)These pings are failing, and this is what you see on the console of R2:
R2#
%SEC-6-IPACCESSLOGDP: list DENY_ALL_FROM_INTERNET denied icmp 192.168.12.1 -> 192.168.23.3 (0/0), 1 packetThese packets are dropped by the inbound ACL on R2, as illustrated below:
If we want to solve this problem, we would have to add a permit statement in the access-list so the ping makes it through. That’s not a scalable solution since we don’t know what kind of traffic we have on our LAN, and we don’t want a big access-list with hundreds of permit statements.
What we are going to do is configure CBAC so it will inspect the traffic and automatically allows the return traffic through. I’ll give you an example of how you can do this for HTTP traffic:



Great post , very informative
Great post RENE!! CBAC is kind of obsolte but it’s a key in order to understand zone-based FW or as I named It ZOMBIES FIREWAL, thanks for all your help!!
Thanks Miguel!
Hi Rene,
I tried simple ACL in packet tracer and I found at least one explicit ACE entry is needed in acces-list to make implicit " deny ip any any" effective, otherwise it allows all the traffic if
it is an empty access-list.
Thanks,
Srini
Hi Srini,
That’s right, it’s strange that they programmed it like this but that’s the way it works
Rene