Lesson Contents
The reflexive access-list is the poor man’s stateful firewall. By default, an access-list on a Cisco router doesn’t keep track of any connections. The only thing it cares about is whether an incoming packet matches a specific statement or not. When it matches a statement it will perform an action (permit or deny) and if it doesn’t match…it’ll check the next statement. If none of the statements match, it will hit the implicit deny any, and the packet will be dropped.
When using the reflexive access-list, your Cisco IOS router will keep track of the outgoing connection(s) and it will automatically allow the return traffic. It’s best to explain this with an example, so let’s take a look at the following topology:
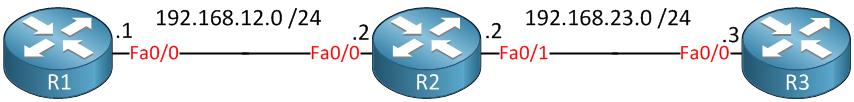
Above we have 3 routers…nothing fancy. Let’s say I want to protect R1 and R2 from whatever traffic R3 might send. I could do this with a very simple but effective access-list:
R2(config)#ip access-list extended 100
R2(config-ext-nacl)#deny ip any any
R2(config)#interface fastEthernet 0/1
R2(config-if)#ip access-group 100 inThe access-list above will drop all traffic from R3. Problem solved, right?
Now, what if there’s an HTTP server behind R3 that I want to reach from R1?
R1#telnet 192.168.23.3 80
Trying 192.168.23.3, 80 ...
% Connection timed out; remote host not respondingPerhaps our network is a bit too secure…The packets from R1 will make it to R3, but the return traffic will be dropped. If I want to allow this return traffic, I have to punch a hole in that access-list I just created. There’s a better method, and that’s the reflexive access-list…let’s take a look.
Configuration
Forget about the access-list that I just created. We start with fresh routers that don’t have any access lists applied to them.
I’m going to create an access-list that will track all outgoing connections. This is how we do it:
R2(config)#ip access-list extended OUTBOUND
R2(config-ext-nacl)#permit ip any any reflect EVALUATE
R2(config)#interface fastEthernet 0/1
R2(config-if)#ip access-group OUTBOUND outAbove, you saw an access-list called OUTBOUND that will permit everything, but I’ve added the reflect keyword. This means that the router keeps track of this outgoing connection, and it will automatically create a statement for the return traffic. It will save this statement in a temporary access-list called EVALUATE. We are halfway done. There’s one more access-list to create:



hi, great website ! i’m still learning basic guides cisco autodidact. i hope i can catch this section soon.
Thanks Rene..
This was a very helpful explanation to me. I´m a regular visitor of gns3vault.com and didn´t know about this one; congrats man you´re awesome!
Rene,
I have been working on access-lists and NAT on my little lab. I have a Cisco router connected to a D Link router that is in turn connected to a vonage router which in turn connects to a Cable mode - my gateway to the internet. I am able to ping the D Link IP address from the cisco router and also the internet. The D link using 192.168.0.0/24 subnet. I configured other subnets behind the cisco router. I managed to use NAT to be able to ping the D Link router but could never be able to ping anythin on the internet. All my other subnets behind the cisco
... Continue reading in our forumI have 1 question for you !
what different between Reflexive ACL, CBAC and Zone Base Access List ?