Lesson Contents
Networks have many components that work together to create a functioning network. Just think of the different protocols that operate on the different layers of the OSI model. For example, to name a few:
- Layer two:
- VLANs
- Spanning tree
- Trunks
- Layer three:
- IP
- Routing
- Routing Protocols
- Layer four:
Not to mention the dozens of applications on the application layer. Besides network equipment like routers, switches, and firewalls, we also have client devices, servers, printers, etc.
In an ideal world, we only have legitimate users who access our network. Unfortunately, not everyone who connects to your network has good intentions. Therefore, we need to protect our network and our legitimate users. Before you can secure something, you need to have an understanding of:
- Protocols and applications that run on your network and their possible issues.
- Different attacks and vulnerabilities.
You can’t protect what you don’t know or understand. In this lesson, we’ll go through an overview of different attacks and vulnerabilities, and countermeasures.
Attacks
There are many different attacks. Here is an overview:
- Address spoofing
- Reconnaissance attacks
- Buffer overflow attacks
- Malware
Address spoofing
In a normal situation, we trust that everyone on the network uses a legitimate MAC and IP address. Furthermore, we trust that the DHCP server is legitimate and that the DNS servers return legitimate IP addresses to our queries.
MAC and IP addresses, however, can be spoofed. For example, an attacker could spoof the MAC address of the default gateway. In doing so, other devices might forward their traffic to the attacker, not the default gateway.
Spoofing the MAC address also influences the switch MAC address table. For example, you could send many Ethernet frames with random source MAC addresses. The switch will learn MAC addresses until its MAC address table is full.
We can also spoof our MAC address and request an IP address from a DHCP server. Do this repeatedly, and the DHCP server won’t have any free IP addresses left in its DHCP server pool. Some of these attacks can be prevented with the following solutions:
DoS attacks
In a normal situation, we have clients that make connections to other clients, servers, or network devices like printers. Servers have enough RAM and CPU power for the users they intend to serve. Our routers and switches have enough capacity to forward Ethernet frames and route IP packets.
With a DoS attack, we attempt to deplete resources, causing systems to become unavailable or crash. There are many ways to do this. It could be as simple as a ping flood where we send many ICMP echo (ping) packets. We can also attempt to flood a target with UDP or TCP packets.
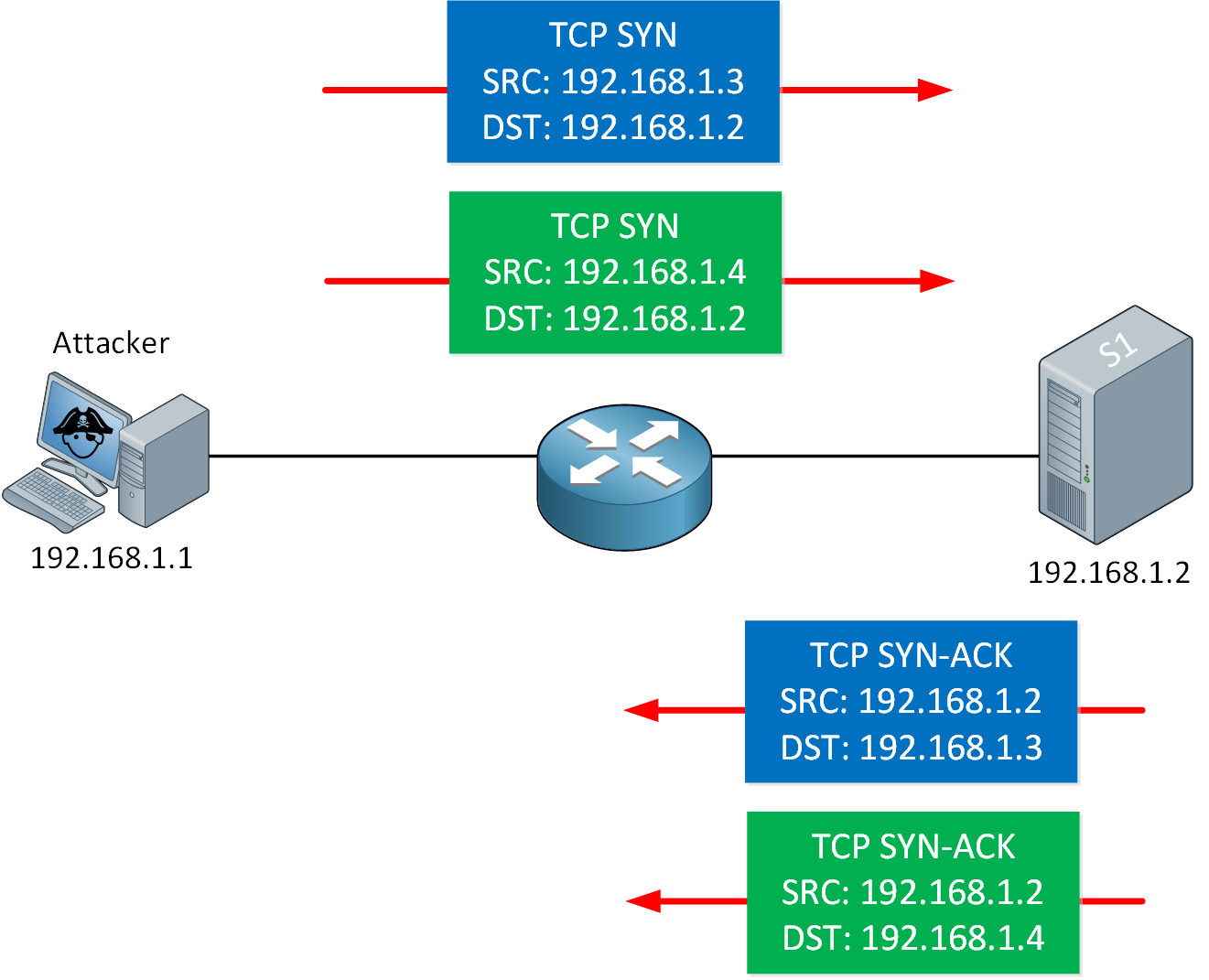
For example, think about the TCP three-way handshake for a minute. An attacker could send many TCP SYNs to a server, usually with a spoofed source IP address. The server replies with an SYN-ACK, but this packet will never make it back to the source to complete the three-way handshake. These incomplete connections will remain in the server until they time out. Do this enough times, and the server will be unable to accept new connections.
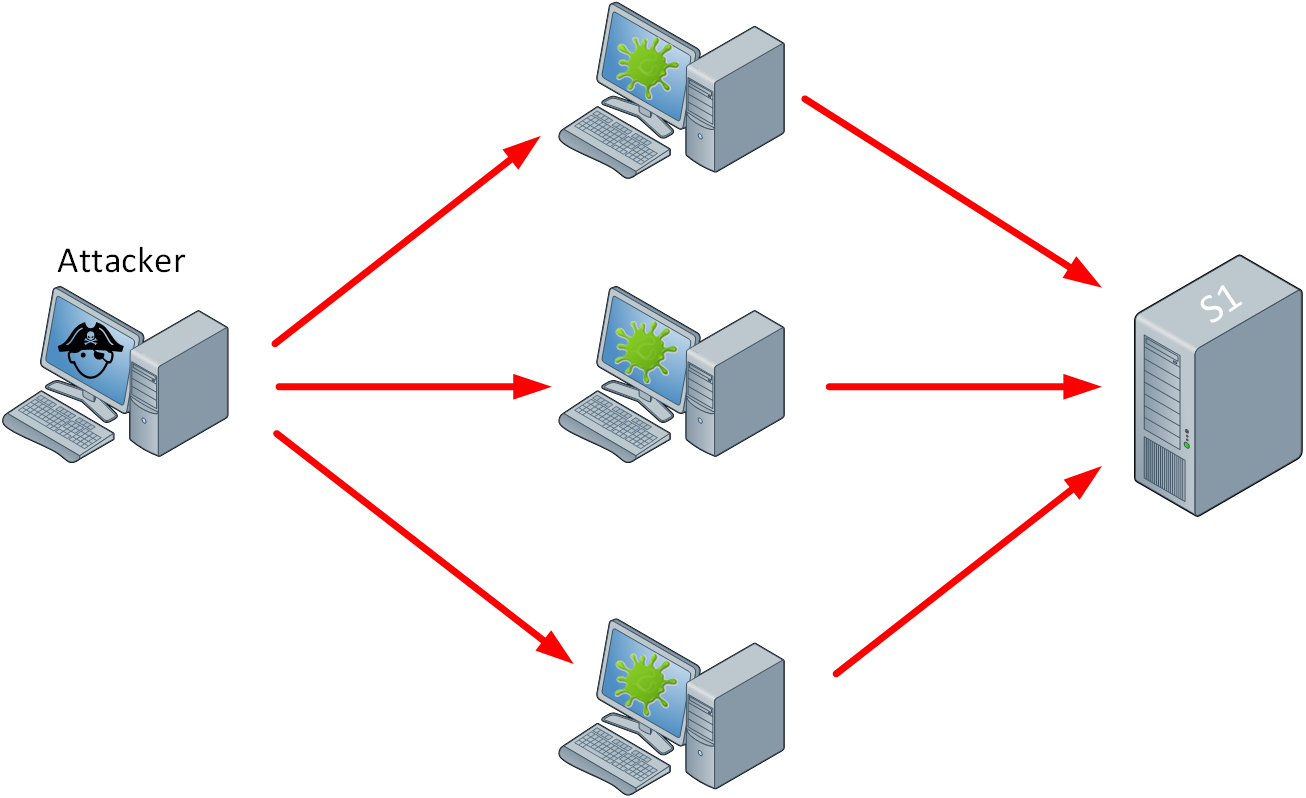
The next level of a DoS attack is a distributed DoS (DDoS) attack. The attacker has a master “controller” and looks for computers or devices with vulnerabilities to infect. An infected device joins the master controller and becomes a “bot”. The attacker can use these bots to launch an attack. DDoS attacks can be difficult to deal with. At the time of writing, the largest DDoS attack (against Microsoft) was 3.47 Tbps and originated from 10,000 sources.
Reflection and amplification attacks
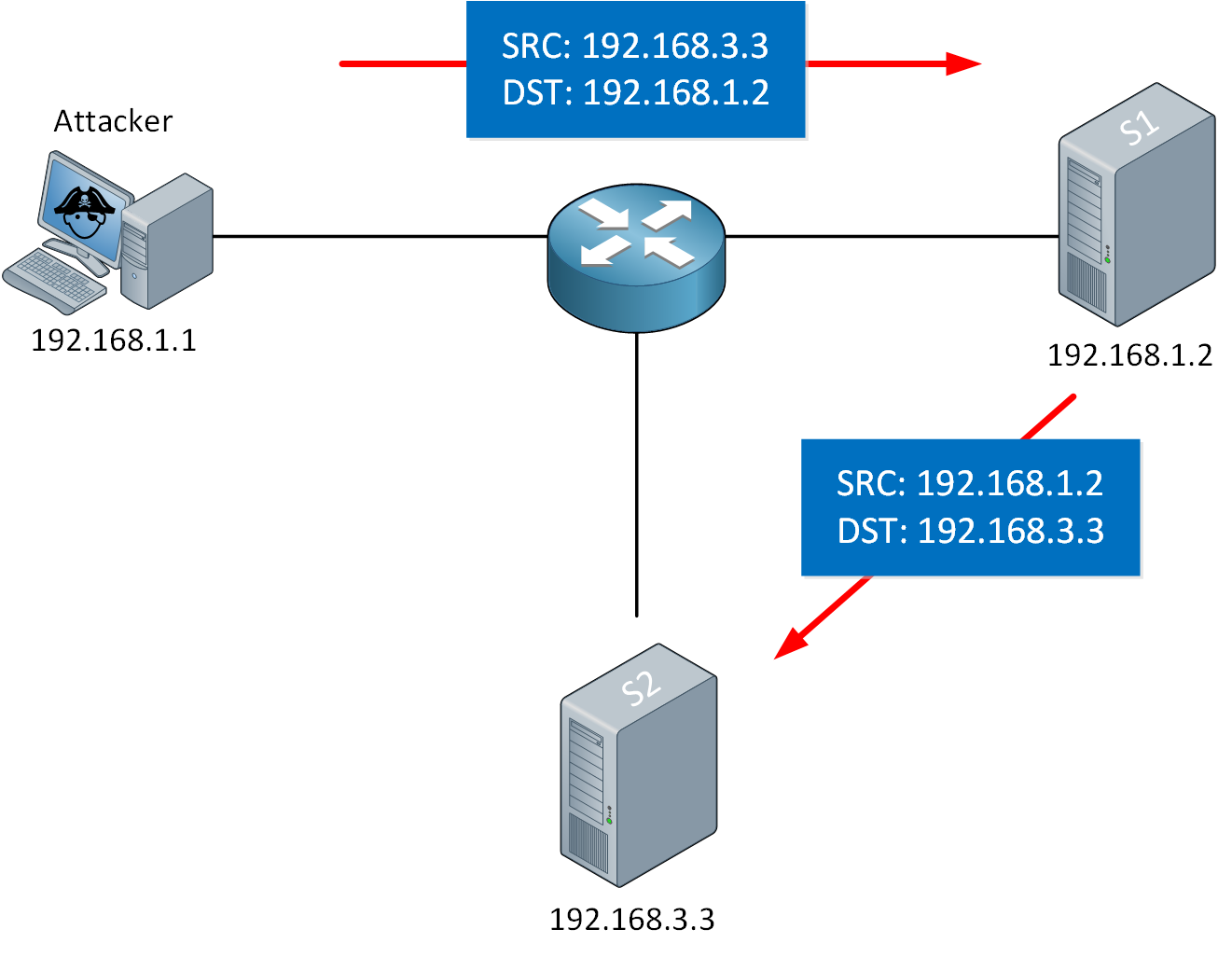
A reflection attack uses address spoofing and a reflector to forward traffic to another target. Here is an example:
In the picture above, our attacker targets S2. The attacker sends an IP packet with spoofed source IP address 192.168.3.3 to S1, our reflector. When S1 replies, it replies to IP address 192.168.3.3 and forwards the packet to S2.
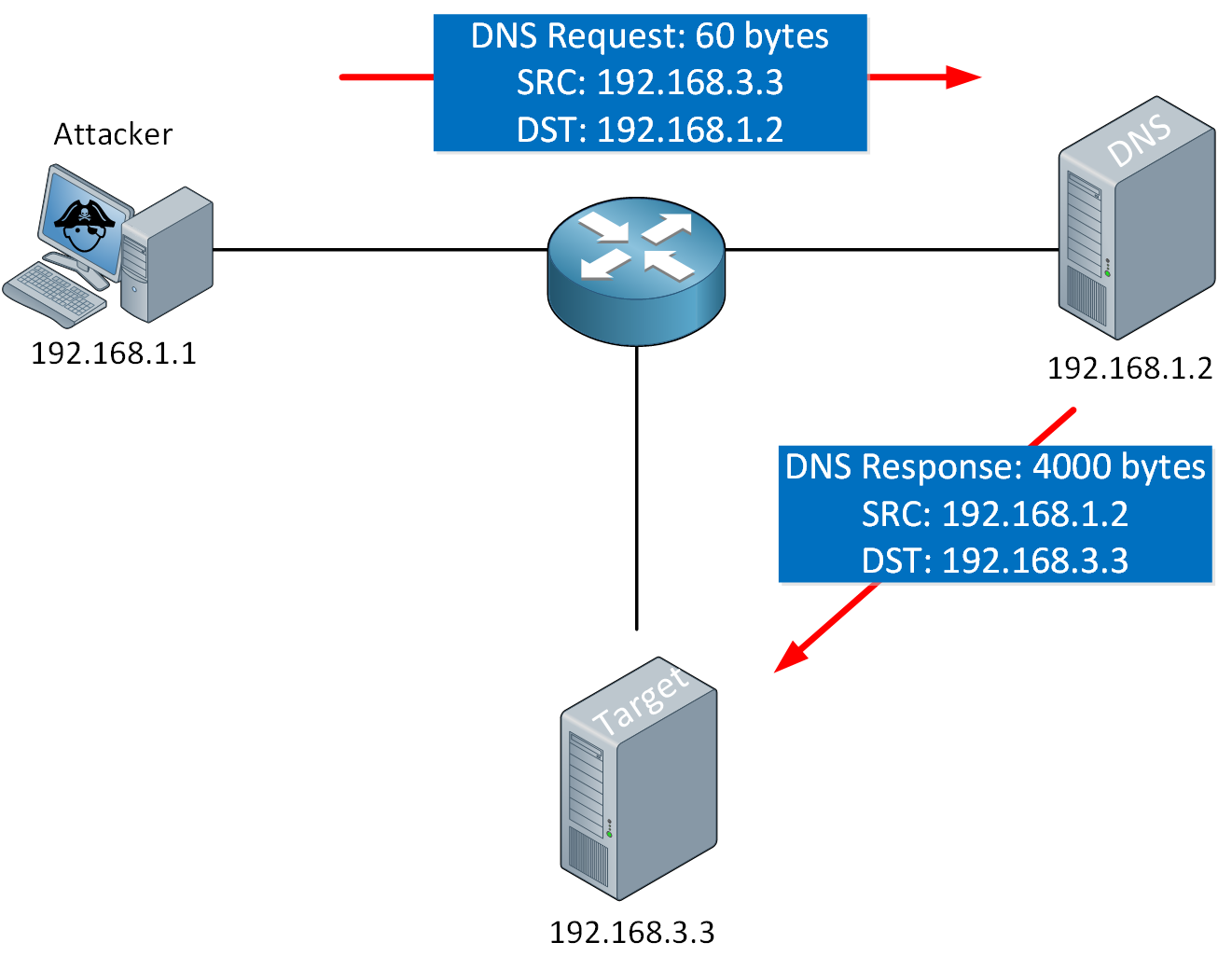
An amplification attack is a type of reflection attack. The attacker sends a small amount of data to a reflector which results in a reply with a large amount of data. DNS is sometimes misused for amplification attacks. A DNS request of about ~60 bytes can be configured to receive a reply of up to ~ 4000 bytes. That’s a 1:66 amplification.
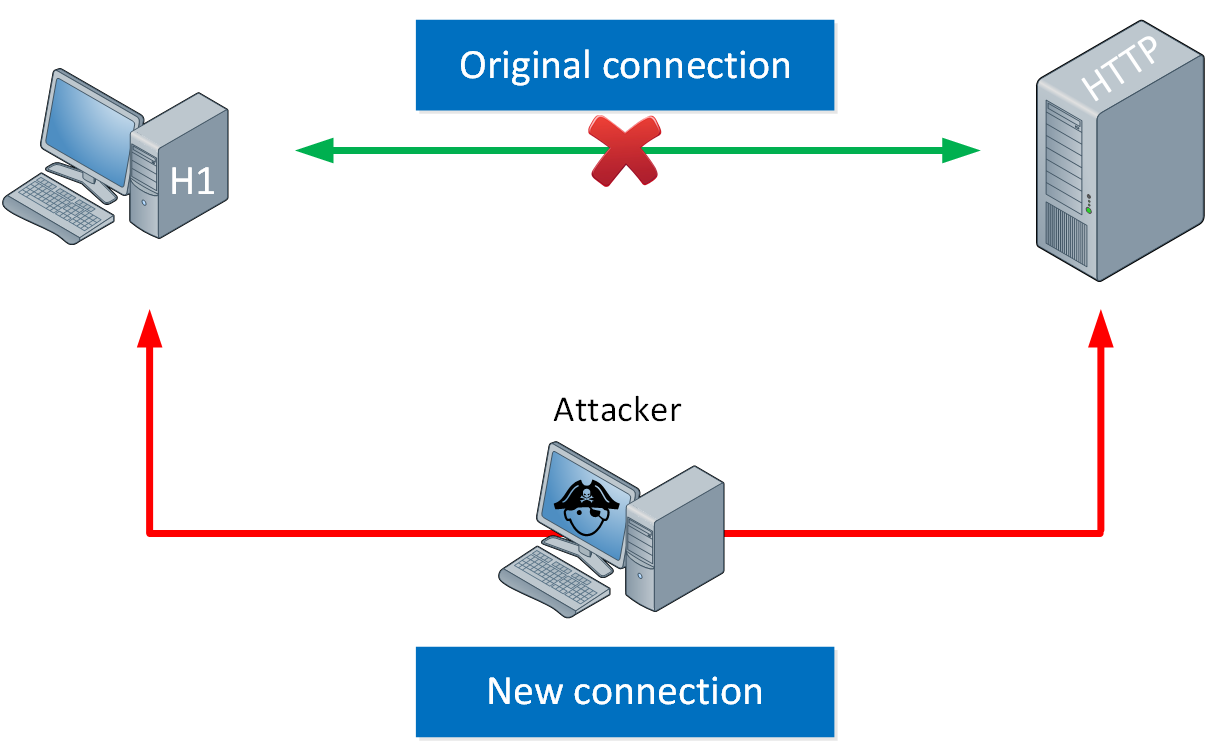
Man in the middle (MiTM) attacks
A man in the middle (MiTM) attack allows an attacker to eavesdrop on the communication between two devices. We do this by being in the middle of the communication path of the two devices. There are many ways to perform MiTM attacks. One example of a MiTM attack is ARP poisoning.
Besides eavesdropping, an attack might attempt to modify data that is sent between the two devices.
Reconnaissance attacks
A reconnaissance attack is not a “real” attack. Before an attacker launches an attack, he or she might want as much information as possible. The attacker will learn as much as possible about the target. For example:
- Information about the company:
- Contact information
- Public IP addresses
- Use scanning tools like Nmap to find:
- IP addresses
- Open ports
- The OS version
- Use tools like ZAP to find security vulnerabilities.
All information found can be used for an actual attack.
Buffer overflow attacks
A buffer is a temporary area for data storage. In operating systems, applications, and in hardware we use buffers. When data is stored within the buffer boundaries, everything works as it should. A buffer overflow occurs when a process tries to write more data to the buffer than the buffer can hold.
When data overflows outside of the buffer space, data can get stored in adjacent memory locations, overwriting data in those locations.
An attacker could cause a service or system to crash, or include malicious code and attempt to run it.
Developers can prevent buffer overflows from happening by fixing their code or using programming languages with built-in protection.
Malware
Malware is a catch-all term for all malicious software designed to access systems, and cause damage, and disruptions. Malware comes in many forms:
- Viruses and worms
- Ransomware
- Trojan attacks
- Spyware
Viruses and worms
Viruses and worms are types of malware. These are malicious software programs that can replicate from one system to another. Viruses are usually attached to executable files. Once the target opens the file, the virus infects the computer and attempts to spread through the network, infected email attachments, removable drives, etc. The difference between a virus and a worm, is that a worm is standalone software that usually replicates itself by infecting systems with vulnerabilities.
Ransomware
Ransomware encrypts files and folders on your computer and notifies the victim that the decryption key can be purchased to unlock the data.
Trojan attacks
Trojans are malicious programs designed to mislead users. This could be a program that you install that also includes malicious code. It could be a USB stick that executes code when you insert it into your computer. Unlike viruses or worms, trojans don’t replicate themselves.
Spyware
Spyware is malware that is installed on your computer with or without your permission. Spyware collects information about the user, computer usage, browsing habits, etc. This information is forwarded to an external location.
Vulnerabilities
Besides attacks, there are different vulnerabilities. We’ll take a look at human and password vulnerabilities.
Human
The attacks we looked at so far are about attacks against systems. There are also attacks that exploit weaknesses in humans who use the systems that the attacker is interested in.
Social Engineering
Social engineering is about exploiting trust and social behavior. When an attacker contacts a user and claims to be from the company’s helpdesk, asking for something, the user might feel obliged to comply with the request. Social engineering is used in some of the attacks described below.
Phishing
With a phishing attack, the attacker tries to lure victims into sharing confidential information (passwords, credit card numbers, etc.) with the attacker. There are many different ways to do this:
- Emails: we’ve all seen these before. Fake invoices, system upgrades, parcel deliveries, etc. The email contains a request and a link from the attacker.
- Vishing: this is a voice call where the attacker claims to be from some bank or helpdesk, asking the victim to perform specific actions on their computer or phone.
- Smishing: fake SMS messages that include links from the attacker.
There are two variations when it comes to phishing:
- Spear phishing: target a specific group of people. These could be people working for the same company or in the same department.
- Whaling: target high profile individuals. For example, a CEO, CTO, etc.
Pharming
With pharming, the attacker uses techniques like DNS hijacking, DNS cache poisoning, or DNS spoofing to redirect users to a fake website that mimics the appearance of the legitimate website. This can be difficult to spot when the domain name matches and the website looks legitimate. Just like with phishing, the attacker will attempt to obtain confidential information from users.
Watering hole
With a watering hole attack, the attacker figures out what websites are commonly used by a specific user or group of people. The attacker tries to compromise and infect the website and waits for the users to use the website. The end goal is to infect the website’s users.
Password
When you want to access a network, application, or server it’s likely that you need some form of authentication. The most common option is a username and password. The username could be easy to guess. Perhaps it’s a default username like root or admin. It could also be the name of a real user.
There are different ways to attack a password:
- Guessing: you could try the default password or simple passwords like “password”, “123456”, etc.
- Dictionary attack: you can use a dictionary or word list thousands or millions of words and try them one by one. You can use a combination of words with uppercase, lowercase, camelcase, etc.
- Brute force: try every possible combination one by one.
Password attacks can be online or offline. With an online attack, it’s likely that you get rate-limited after entering the wrong password a couple of times. With an offline attack, nobody will know that you are attempting to crack the password. An example of an offline attack is capturing the WPA four-way handshake and attempting to crack it.
To mitigate password attacks, we have different options. You could implement password policies where you require complex passwords. Passwords should include:
- Upper- and lowercase characters.
- Numbers
- Special characters
The idea is to make passwords complex enough so that dictionary or brute attacks won’t be able to crack the password. Passwords should also be changed multiple times per year. The disadvantage of complex passwords is that it makes passwords difficult to remember for your users. Users might write down their passwords so they don’t forget them.
Multi-factor authentication
Multi-factor authentication increases security by requiring an extra form of authentication.
Besides using something you know (password), we can add something you have. Hardware tokens were a popular option in the past. Nowadays, authenticator apps on phones are a popular option. For example:
- Authy
- Microsoft authenticator
- Google authenticator
Many websites promote the usage of multi-factor authentication.



Hi,
How to protect from the amplification attack
Thanks
Hello Sims
An amplification attack is a type of Denial of Service (DoS) attack that uses certain characteristics of particular services to amplify or magnify the amount of traffic that is directed towards a victim, resulting in it being overwhelmed and not able to respond. Amplification takes advantage of “reflectors” which are systems that legitimately respond to an attack, but in doing so, inadvertently add to the volume of DoS traffic. Such attacks typically take advantage of vulnerabilities found in certain firmwares or network OSes, or in protocols and s
... Continue reading in our forum