Lesson Contents
There are many different methods you can use to authenticate wireless clients. Some of these methods are outdated and have security weaknesses. They have been replaced with newer, more secure authentication methods.
In this lesson, we’ll discuss the most common authentication methods.
Open Authentication
Open authentication is one of the two authentication methods from the first 802.11 standard. As the name implies, open authentication offers open authentication to a wireless network. The wireless client sends an authentication request to the AP, which the AP accepts without question. You don’t need a pre-shared key or credentials. After authentication, the wireless client associates with the AP.
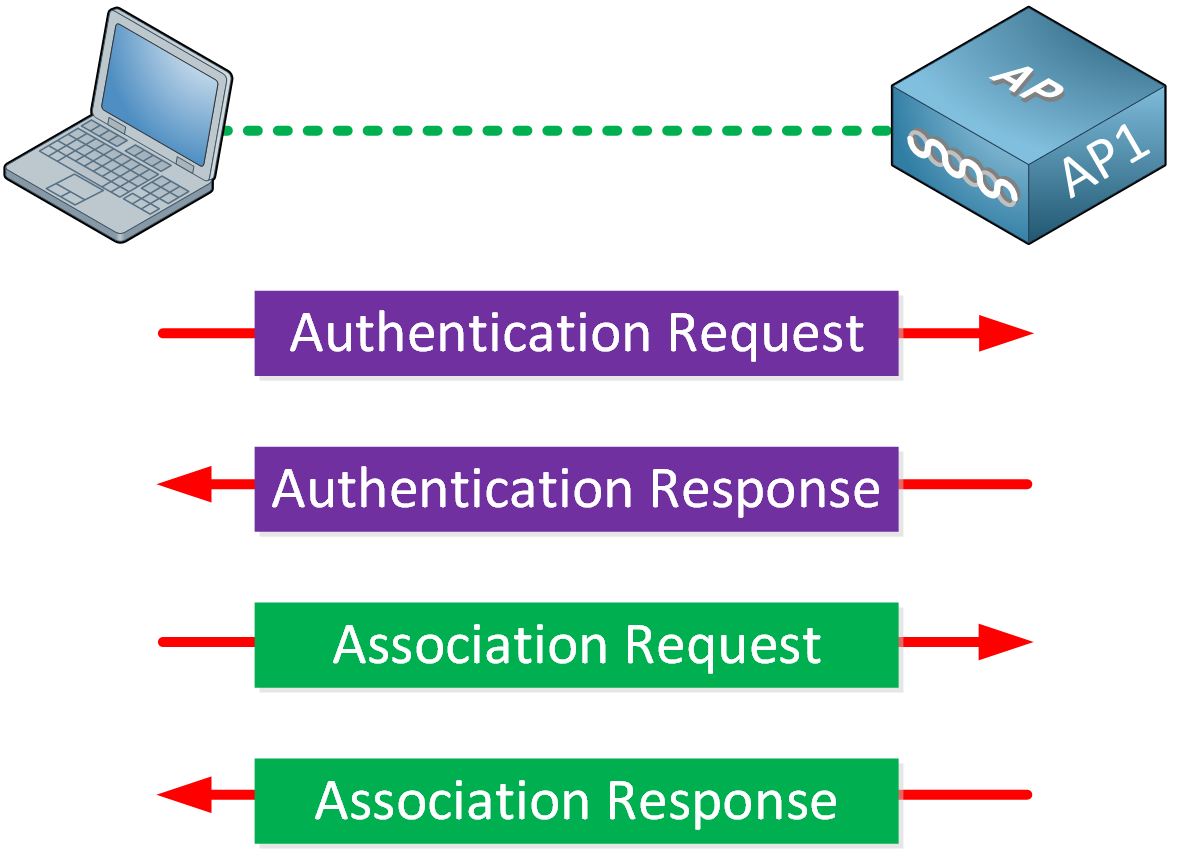
Using open authentication doesn’t automatically mean that there is no authentication at all. You can still authenticate wireless users on another level. If you have ever used a public wireless network at an airport, hotel, or fast food restaurant, you know what I’m talking about.
You can connect to the network without any issues, but as soon as you open your web browser, you see a web page where you have to enter your credentials. Until you enter your credentials, all traffic is blocked. On the wireless level, there is no authentication, but there is on the upper layers.
WEP
Wired Equivalent Privacy (WEP) is a security algorithm and the second authentication option that the first 802.11 standard supports. The idea behind WEP is to make a wireless network as secure as a wired link. WEP uses the RC4 cipher algorithm to encrypt every frame so that eavesdroppers can’t read the contents.
The algorithm uses a WEP key to create other encryption keys, one for each wireless frame. When the sender and receiver use the same WEP key, they can decrypt each other’s frames.
WEP supports two authentication methods:
- Open authentication
- Shared key authentication
With open authentication, the wireless client doesn’t provide any credentials. It’s the same open authentication, as I described before. The wireless client can authenticate to the AP without any issues. We only use WEP encryption to encrypt data frames.
With shared key authentication, we also use the WEP key for authentication and encryption. You can use this to test if the wireless client has the correct key. The AP sends a random challenge to the wireless client. The client encrypts the challenge phrase with WEP and sends the result to the AP. The AP compares the result from the client with its own to see if both ends use the same WEP key. If not, the wireless client can’t associate with the AP.
WEP keys are 64 or 128 bits and represented with a string of 10 or 26 hex digits. The longer the key, the more unique bits, which results in stronger encryption.
Unfortunately, WEP is a broken protocol. The original 802.11 standard is from 1999. Researchers discovered some weaknesses in 2001, which make it very easy to decrypt any WEP encrypted traffic and to retrieve the pre-shared key.
WEP is officially deprecated since 2004, in the 802.11i amendment.
802.1X/EAP
The original 802.11 standard only supported open authentication and WEP. It was time for more secure authentication methods.
Instead of adding new authentication methods into the 802.11 standard, IEEE chose the Extensible Authentication Protocol (EAP) framework to add new authentication options. EAP has functions that multiple authentication methods can use, and it integrates with 802.1X port-based access control.
An 802.1X-enabled port limits access to the network until the client successfully authenticates. For wireless networks, it means that a wireless client can associate with an AP, but it won’t be able to do anything else until authentication succeeds.
Here’s what 802.1X EAP authentication looks like:
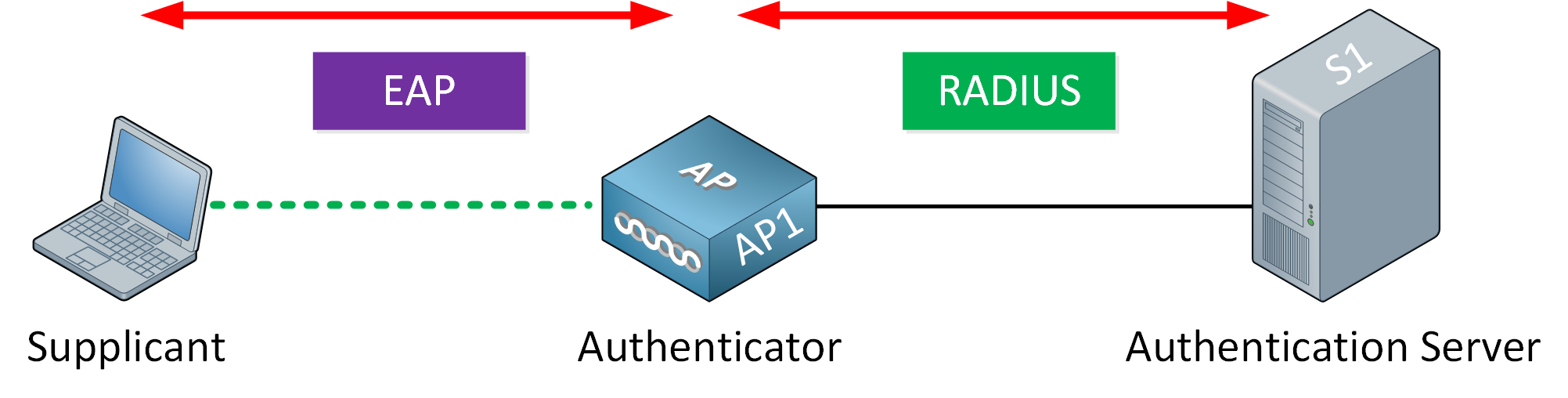
There are three device roles:
- Supplicant
- Authenticator
- Authentication Server
The supplicant (wireless client) uses open authentication and associates with the AP. It doesn’t end there, though; the supplicant communicates with an external authentication server to authenticate itself. The authentication server is usually a RADIUS server. The authenticator in the middle is the AP or WLC, which blocks all traffic, except for authentication traffic. When the authentication server verifies the credentials of the end user, the authenticator unblocks the traffic and permits all wireless traffic.
Now you understand the basics of 802.1X/EAP, let’s take a look at some popular EAP authentication methods.
LEAP
Cisco developed a proprietary wireless authentication method called Lightweight EAP (LEAP) as an attempt to create a more secure authentication method than WEP. It uses two features:
- Dynamic WEP keys
- Mutual authentication
LEAP allows clients to re-authenticate. Each time the client re-authenticates, the client receives a new WEP key. The idea behind this is that the temporary WEP key doesn’t live long enough to be cracked.
With mutual authentication, the client sends a username and password. The client and the authentication server also send each other a challenge message. When they can decrypt each other’s messages, they’ll have authenticated each other.
One of the issues with LEAP is that it uses a modified version of MS-CHAP, a weak authentication protocol. It’s vulnerable to an offline attack if you use weak passwords. Users should use strong passwords, which doesn’t often happen because those are difficult to remember.
You can still configure LEAP, but you shouldn’t use it anymore. There are more secure EAP options.
EAP-FAST
Cisco developed another EAP method called EAP Flexible Authentication by Secure Tunneling (EAP-FAST).
EAP-FAST protects credentials by exchanging a shared secret generated by the authentication server. This shared secret is called a protected access credential (PAC) and used for mutual authentication. There are three phases:
- Phase 0: The authentication server generates the PAC and transmits it to the wireless client (supplicant).
- Phase 1: The authentication server and supplicant authenticate each other and negotiate a TLS tunnel.
- Phase 2: The end user is authenticated through the TLS tunnel.
What happens is that we have two authentication processes, an inner and outer authentication:
- First authentication is used to build the TLS tunnel.
- Second authentication happens inside the TLS tunnel, and we use this to authenticate the end user.
To make EAP-FAST work, you need a RADIUS server. However, the RADIUS server also needs to act as an EAP-FAST server because it needs to generate PACs. If you already have Cisco Secure Access (ACS) or Identity Services Engine (ISE) in your network, EAP-FAST might be an option.
PEAP
Similar to EAP-FAST, Protected EAP (PEAP) uses inner and outer authentication. However, instead of a PAC, the authentication server presents a digital certificate to the supplicant for the outer authentication.
We can use the certificate to verify whether the wireless network is legitimate or not. This helps to prevent the end users from connecting to rogue APs, as long as they don’t accept the certificate if they don’t trust it. End users should not be responsible for checking if the certificate is legit or not. Checking the validity of a certificate can be a difficult for an end user. Instead, you should configure the operating system of the wireless client to trust only specific certificates and only to connect to trusted wireless networks with matching certificates.
If the wireless client accepts the digital certificate, the supplicant and authentication server build the TLS tunnel. We can authenticate the end user through the TLS tunnel using multiple protocols, including MS-CHAPv2.
PEAP is a popular method for wireless authentication. You only need a certificate for the authentication server, not on the wireless clients. This makes it quite easy to implement PEAP.



Hello Michael
I understand your confusion, and I believe it is an issue with terminology. WEP is actually defined as a security algorithm that is used in the IEEE 802.11 standard wireless networks. This algorithm has several configuration parameters, one of which is the type of supported authentication. This simply refers to how the WEP algorithm is applied to a wireless communication.
The first, which is Open authentication, doesn’t require credentials, so anyone can connect to an Open Authentication WEP access point, so any client within range can freely c
... Continue reading in our forumDear sir,
How to enable cert in my PC ? Unable to connect the WIFI network since authentication have failed.
Please help .
Thank you
Regards,
Mani
https://cdn-forum.networklessons.com/uploads/default/original/2X/3/3e2e27fcc0401a26aca37a6181df6d0dca7034ca.jpeg
https://cdn-forum.networklessons.com/uploads/default/original/2X/c/ca611038441412bd99f25c5907b7cf7f449e43d1.jpeg
https://cdn-forum.networklessons.com/uploads/default/original/2X/3/3e2e27fcc0401a26aca37a6181df6d0dca7034ca.jpeg
Hello Mani
After doing some research I have found that this error appears whenever a device attempts multiple failed authentications within a specified period of time. This makes the “Client suppression mechanism” of the ISE kick in. This prevents DoS attacks. You can disable this feature in Administration > System > Settings > Radius, Suppress Anomalous Clients. You can also change the settings such as how long a client should be blocked.
More info about this can be found at this Cisco community thread:
https://community.cisco.com/t5/network-access-control/
... Continue reading in our forumHi,
I am trying to find some reference that states EAP-FAST requires a radius server. Most resources that I have seen online state ‘authentication server’ and haven’t explicitly stated radius.
Hello Shashank
EAP-FAST can indeed be used with RADIUS and you can see how this can be achieved in the following Cisco documentation:
https://www.cisco.com/c/en/us/support/docs/wireless/4400-series-wireless-lan-controllers/99791-eapfast-wlc-rad-config.html#anc11
In it, it refers specifically to RADIUS as the authentication server. This is a typical setup, although other documentation that talks about an overview of EAP-FAST as a technology, does not refer specifically to RADIUS, but it states “authentication server” as you said, much like what you will find i
... Continue reading in our forum