Dynamic ARP Inspection (DAI) is a security feature that protects ARP (Address Resolution Protocol) which is vulnerable to an attack like ARP poisoning.
DAI checks all ARP packets on untrusted interfaces, it will compare the information in the ARP packet with the DHCP snooping database and/or an ARP access-list. If the information in the ARP packet doesn’t matter, it will be dropped. In this lesson I’ll show you how to configure DAI. Here’s the topology we will use:
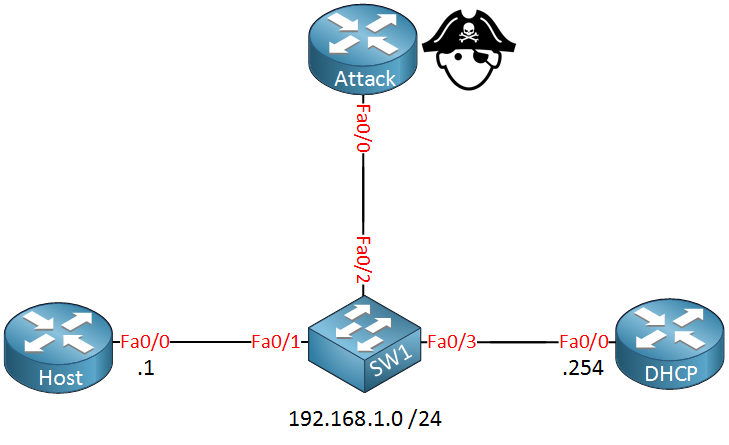
Above we have four devices, the router on the left side called “host” will be a DHCP client, the router on the right side is our DHCP server and on top we have a router that will be used as an attacker. The switch in the middle will be configured for dynamic ARP inspection.
Configuration
We’ll start with the switch, first we need to make sure that all interfaces are in the same VLAN:
SW1(config)#interface range fa0/1 - 3
SW1(config-if-range)#switchport mode access
SW1(config-if-range)#switchport access vlan 123
SW1(config-if-range)#spanning-tree portfastNow we can configure DHCP snooping:
SW1(config)#ip dhcp snooping
SW1(config)#ip dhcp snooping vlan 123
SW1(config)#no ip dhcp snooping information optionThe commands above will enable DHCP snooping globally, for VLAN 123 and disables the insertion of option 82 in DHCP packets. Don’t forget to make the interface that connects to the DHCP server trusted:
SW1(config)#interface FastEthernet 0/3
SW1(config-if)#ip dhcp snooping trustThe switch will now keep track of DHCP messages. Let’s configure a DHCP server on the router on the right side:
DHCP(config)#ip dhcp pool MY_POOL
DHCP(dhcp-config)#network 192.168.1.0 255.255.255.0That’s all we need, let’s see if the host is able to get an IP address:
HOST(config)#interface FastEthernet 0/0
HOST(config-if)#ip address dhcpA few seconds later we see this message:
%DHCP-6-ADDRESS_ASSIGN: Interface FastEthernet0/0 assigned DHCP address 192.168.1.1, mask 255.255.255.0, hostname HOSTLet’s check if our switch has stored something in the DHCP snooping database:
SW1#show ip dhcp snooping binding
MacAddress IpAddress Lease(sec) Type VLAN Interface
------------------ --------------- ---------- ------------- ---- --------------------
00:1D:A1:8B:36:D0 192.168.1.1 86330 dhcp-snooping 123 FastEthernet0/1
Total number of bindings: 1There it is, an entry with the MAC address and IP address of our host. Now we can continue with the configuration of DAI. There’s only one command required to activate it:
SW1(config)#ip arp inspection vlan 123The switch will now check all ARP packets on untrusted interfaces, all interfaces are untrusted by default. Let’s see if this will work or not…I’ll configure the IP address of our host on our attacker:
ATTACK(config)#interface FastEthernet 0/0
ATTACK(config-if)#ip address 192.168.1.1 255.255.255.0Now let’s see what happens when we try to send a ping from the attacker to our DHCP router:
ATTACK#ping 192.168.1.254
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.254, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)The ping is failing…what does our switch think of this?
SW1#
%SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Req) on Fa0/2, vlan 123.([0017.5aed.7af0/192.168.1.1/0000.0000.0000/192.168.1.254/01:20:08 UTC Tue Mar 2 1993])
%SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Req) on Fa0/2, vlan 123.([0017.5aed.7af0/192.168.1.1/0000.0000.0000/192.168.1.254/01:20:10 UTC Tue Mar 2 1993])
%SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Req) on Fa0/2, vlan 123.([0017.5aed.7af0/192.168.1.1/0000.0000.0000/192.168.1.254/01:20:10 UTC Tue Mar 2 1993])
%SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Req) on Fa0/2, vlan 123.([0017.5aed.7af0/192.168.1.1/0000.0000.0000/192.168.1.254/01:20:10 UTC Tue Mar 2 1993])Above you can see that all ARP requests from our attacker are dropped. The switch checks the information found in the ARP request and compares it with the information in the DHCP snooping database. Since it doesn’t match, these packets are discarded. You can find the number of dropped ARP packets with the following command:
SW1#show ip arp inspection
Source Mac Validation : Disabled
Destination Mac Validation : Disabled
IP Address Validation : Disabled
Vlan Configuration Operation ACL Match Static ACL
---- ------------- --------- --------- ----------
123 Enabled Active
Vlan ACL Logging DHCP Logging Probe Logging
---- ----------- ------------ -------------
123 Deny Deny Off
Vlan Forwarded Dropped DHCP Drops ACL Drops
---- --------- ------- ---------- ---------
123 0 5 5 0
Vlan DHCP Permits ACL Permits Probe Permits Source MAC Failures
---- ------------ ----------- ------------- -------------------
123 0 0 0 0
Vlan Dest MAC Failures IP Validation Failures Invalid Protocol Data
---- ----------------- ---------------------- ---------------------
Vlan Dest MAC Failures IP Validation Failures Invalid Protocol Data
---- ----------------- ---------------------- ---------------------
123 0 0 0Above you see the number of drops increase. So far so good, our attacker has been stopped. We still have one problem though, let me first shut the interface on our attacker before we continue:
ATTACK(config)#interface FastEthernet 0/0
ATTACK(config-if)#shutdownLet me show you what happens when we try to send a ping from the host to our DHCP router:
HOST#ping 192.168.1.254
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.254, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)This ping is failing but why? We are not spoofing anything…here’s what the switch tells us:



Hi rene, I don´t have a DHCP server. My users have Ip address static. Do I need configure ip arp inspection filter?
Hi Alberto,
If you feel ARP poisoning is a risk on your network then you could implement it. However if you use static addresses then it’s probably not worth the effort.
DAI is very useful when you use DHCP as it relies on the DHCP snooping database. When you use DHCP then DAI will work for all address leases and we use the static entries only for some static devices like routers or servers.
If you have to implement this for all your users then it might be quite some work…
Rene
Hi Rene,
Cisco Packet tracer switches do not have the ip dhcp snooping function. Does this mean I have to do it via GNS3 ?
Cheers
Neil
Hello Rene,
ARP poisoning attack can mitigate DAI and DAI works on DHCP snooping Database. So If there is no DHCP server, how can we mitigate ARP Poisoning attack?? Its like that if we want to mitigate ARP poisoning then must have to enable DHCP environment or any other way to mitigate ARP POISONING.
BR//
ZAMAN
Sachy,
I haven’t had much luck with GNS3 on this switching topic–certainly not on the native GNS3 (because there are no real switches). It might be possible via the GNS3 IOU, but I haven’t tried it. Here’s more info on that:
http://srijit.com/how-to-configure-iou-in-gns3-for-real-cisco-switching-labs/
If you can’t get that to work, I believe VIRL supports this feature (which isn’t free). Your other options would be to use a Rack Rental (like with INE.com) or borrow some actual switches if you can.