Lesson Contents
When you use a private WAN connection from a service provider, you trust them that they treat your data confidential. The service provider will make sure that they separate traffic from different customers and that nobody else is able to see your data.
What about the Internet? When you send traffic from A to B using the Internet, you have no control at all which networks are used to get from the source to the destination. Someone in between the traffic path might be capturing your packets and you wouldn’t know.
VPNs (Virtual Private Network) help by establishing a secure connection over an insecure network, such as the Internet. This is a great alternative to private WAN connections since Internet access is usually cheaper and it’s available pretty much everywhere.
VPNs provide a couple of features such as:
- Confidentiality: preventing anyone from reading your data. This is implemented with encryption.
- Authentication: verifying that the router/firewall or remote user that is sending VPN traffic is a legitimate device or router.
- Integrity: verifying that the VPN packet wasn’t changed somehow during transit.
- Anti-replay: preventing someone from capturing traffic and resending it, trying to appear as a legitimate device/user.
VPN Types
There are two common VPN types that we use:
- site-to-site VPN
- client-to-site VPN (remote user)
Let me give you some examples.
Site-to-site VPN
With the site-to-site VPN, we have a network device at each site, between these two network devices we build a VPN tunnel. Each end of the VPN tunnel will encrypt the original IP packet, adds a VPN header, a new IP header and then forwards the encrypted packet to the other end of the tunnel.
Here’s an example of a VPN tunnel:
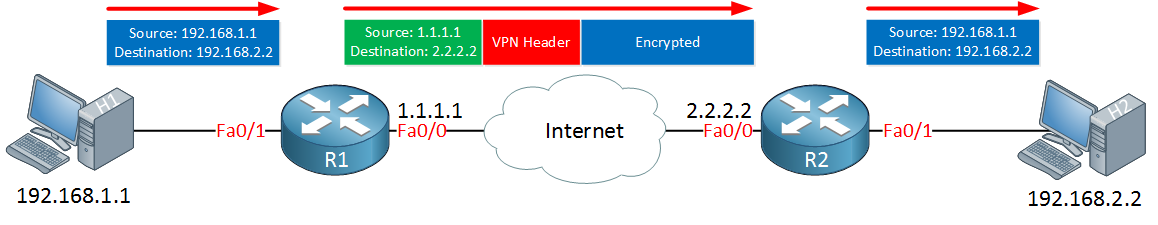
Here’s what happens in the picture above:
- H1 sends an IP packet with source 192.168.1.1 and destination 192.168.2.2.
- R1 encrypts the IP packet, adds a VPN header and creates a new IP header with its own public IP address as the source and 2.2.2.2 as the destination.
- R1 sends the new packet to R2.
- R2 receives the packet, checks if the packet really came from R1, decrypts it and forwards it to H2.
- H2 receives the original IP packet.
In the example above I used two routers but firewalls like the Cisco ASA firewall are often used for VPN tunnels.
Client-to-site VPN
The client-to-site VPN is also called the remote user VPN. The user installs a VPN client on his/her computer, laptop, smartphone or tablet. The VPN tunnel is established between the user’s device and the remote network device. Here’s an example:
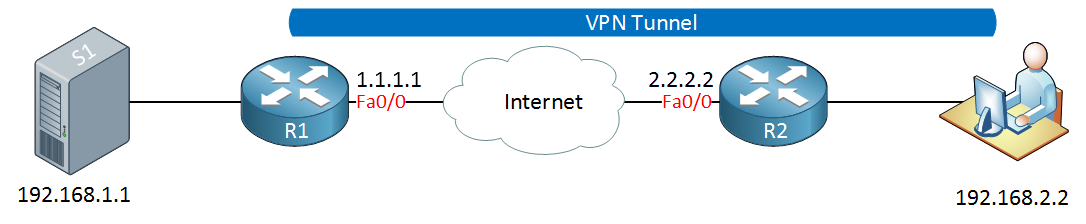
In the picture above, the user has established a VPN tunnel between its VPN client and R1. This allows the user to access a remote server.
VPN Protocols
There are a couple of VPN protocols, the most common ones are:
- IPSec
- PPTP
- L2TP
- SSL VPN
Let me give you an overview of each protocol.
IPSec
The IP protocol itself doesn’t have any security features at all, which is why IPSec was created. IPSec is not a protocol but it’s a framework and offers confidentiality, integrity, authentication and anti-replay features on layer three of the OSI model.
It uses a variety of protocols and the advantage of a framework is that the protocols it uses can change in the future. For example, currently, we can use encryption algorithms like DES, 3DES or AES but if a new algorithm is created, IPSec might use it in the future.
You can use IPSec for:
- Creating a site-to-site VPN tunnel.
- Creating a client-to-site (remote user) VPN tunnel.
- Between two servers to authenticate and/or encrypt traffic.
For an in-depth explanation of IPSec, you can take a look at my IPSec lesson.
PPTP
PPTP (Point to Point Tunneling Protocol) is one of the older VPN protocols, it was released around 1995. It uses a GRE tunnel for tunneling and PPP for authentication (using MS-Chap or MS-Chap v2). Encryption is done with the MPPE protocol.
Since it’s been around for a while, PPTP is supported on many clients and operating systems. PPTP, however, has been proven insecure so you shouldn’t use this protocol anymore if you want to protect your data.
L2TP
L2TP (Layer Two Tunneling Protocol) is an extension of PPTP and as the name implies, allows us to tunnel layer two traffic over layer three connections. L2TP can be used if you need to “bridge” two remote LANs together and you want to use a single subnet on both sites. L2TP itself does not offer any encryption or anything, which is why we use often use it together with IPSec. When you use L2TP and IPSec together, it’s often referred to as L2TP/IPSec
SSL VPN
SSL (Secure Sockets Layer) is a protocol that is normally used to encrypt traffic between a web browser and web server. When you surf the web using HTTP, everything is clear text. For secure connections, we use HTTPS. We can use the same technology for VPNs.
One of the advantages of SSL VPN is that since it uses HTTPS, you can use it pretty much everywhere. Most public wifi hotspots do permit HTTPS traffic while some might block other traffic like IPSec. Another reason why SSL VPN is popular is that you don’t always have to use a software client.


Hi Rene,
Thank you for the excellent intro on VPN. I like the way you teach and make the concept simple.
I also heard about other types of VPN like Easy VPN, Anyconnect VPN and many more. If you can throw some lights on that and let us know their use in real networks.
Hello Bharath
EasyVPN is a wizard that can be used either on the router (using Cisco Configuration Professional) or at the client to simplify the creation of VPNs. Using a wizard it allows you to enter information in a GUI to create your VPN. There are three components that can be used: Easy VPN Client, Remote and Server. You can find out more information about it here.
Cisco AnyConnect is a secure mobility client that allows you to connect securely (via VPN) to a VPN server. It is essentially Cisco’s VPN client software for PC, laptop and mobile devices.
... Continue reading in our forumHi lazaros,
What is the difference between Tunnel, DMVPN and VPN?
Hello Muhammad
A VPN is a method by which you can establish a secure connection between two points over an inherently insecure network. For example, you may have a corporation headquarters and a branch office, and you create a connection between these two over the Internet. Now the Internet is considered an insecure environment, as you have no control over who can see the traffic that may be traversing any portion of the Internet. However, with a VPN, you can encrypt the data you send so that any intercepted packets will be unreadable and ultimately useless
... Continue reading in our forumThanks Lazaros,
Great and clear explanation as I expected.