Lesson Contents
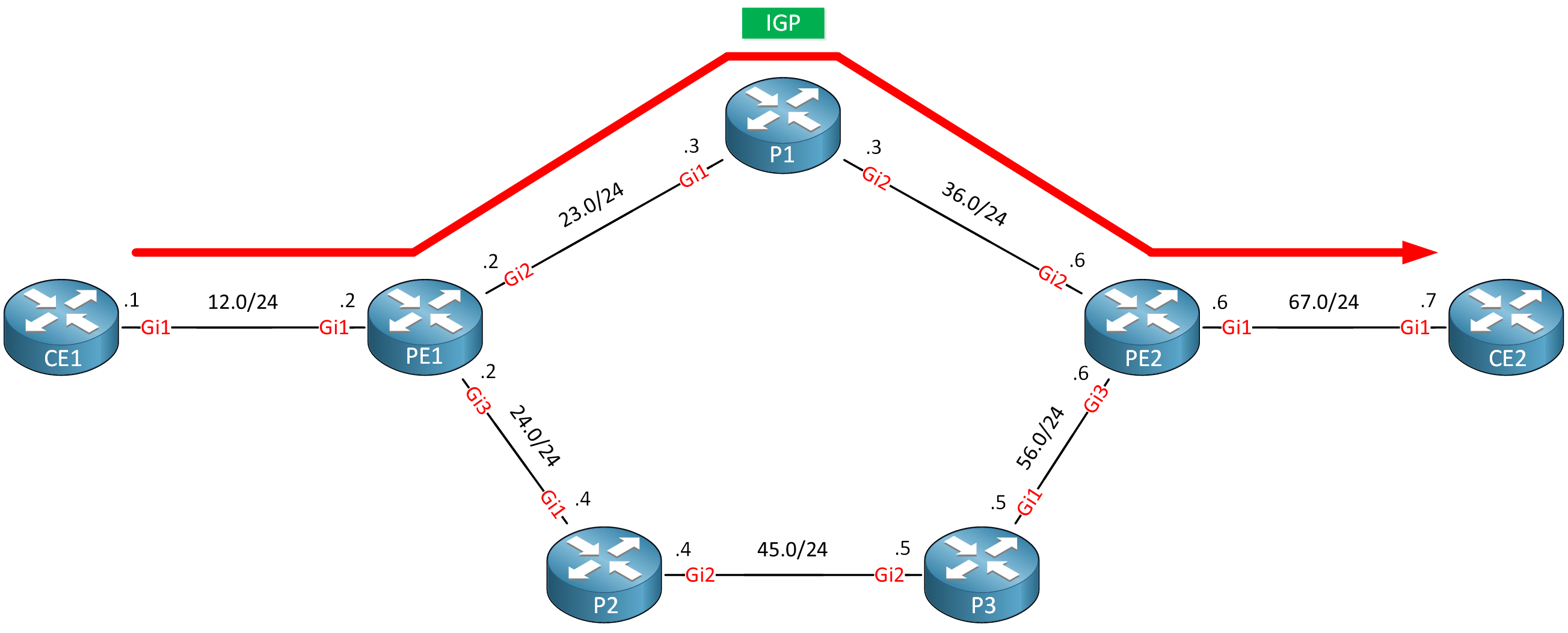
MPLS Traffic Engineering (TE) allows network operators to define how traffic flows through an MPLS core network. You can steer traffic to maximize the efficient use of available bandwidth between routers.
With traditional IP routing and IGPs, we calculate the least cost path based on a metric. The metric is a simple static value based on the interface bandwidth. The problem is that we only use that path with the lowest cost and nothing else. If you have two paths with the same metric, we can use equal cost load balancing, but that’s it.
Other links won’t be used. That is a waste of bandwidth. The only thing we can do to send traffic another way is to manipulate the metric. Changing the metric is not always possible or feasible.
To use the network as efficiently as possible, we need to know the conditions of the network. You need to know which interfaces are utilized or underutilized. You need to know the available bandwidth in the network.
MPLS TE uses “constraint-based routing” which means that we use the shortest path that meets certain criteria. This could be a bandwidth requirement, or perhaps you want to include/exclude certain interfaces or routers in the path.
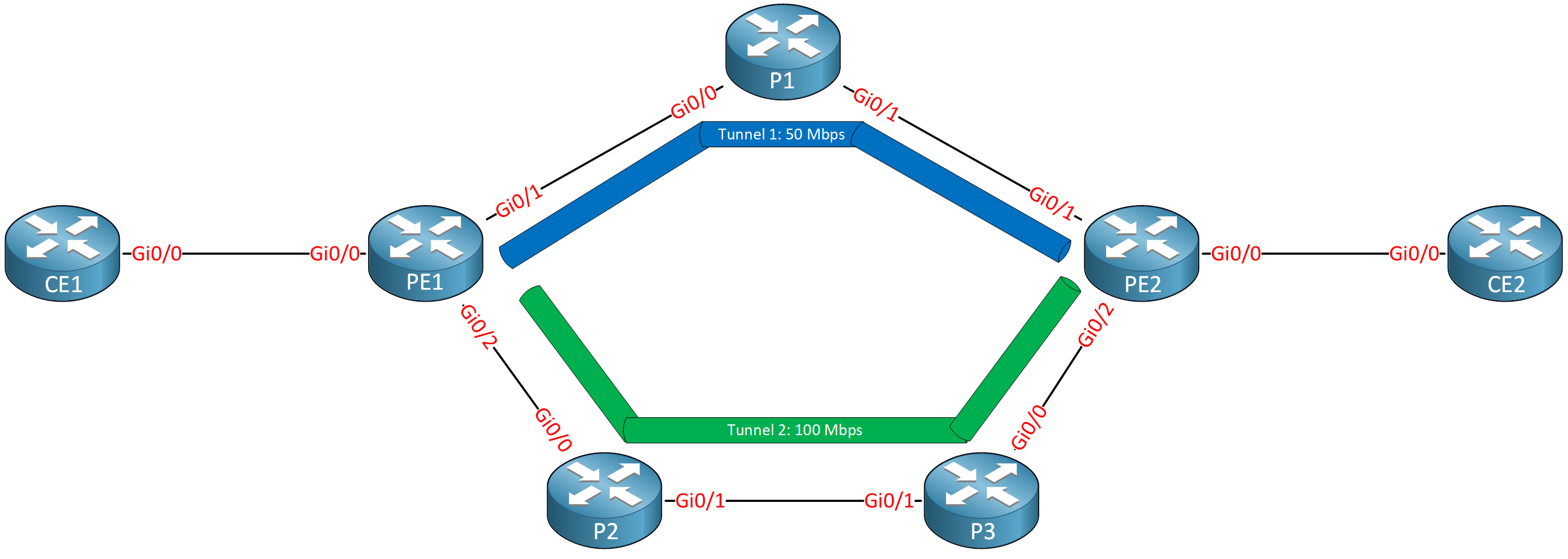
To send traffic down a certain path, MPLS TE builds unidirectional tunnels from a source to the destination using Label Switched Paths (LSPs). These tunnels can have requirements such as bandwidth, affinity, or priority.
We send traffic down these tunnels. For example, in the picture above we could perhaps use Tunnel 1 for packets marked with DSCP EF, and tunnel two for high-priority data traffic. Regular traffic can still be routed through the IGP.
MPLS TE builds unidirectional tunnels (LSPs) from source to destination, which we use for traffic forwarding:
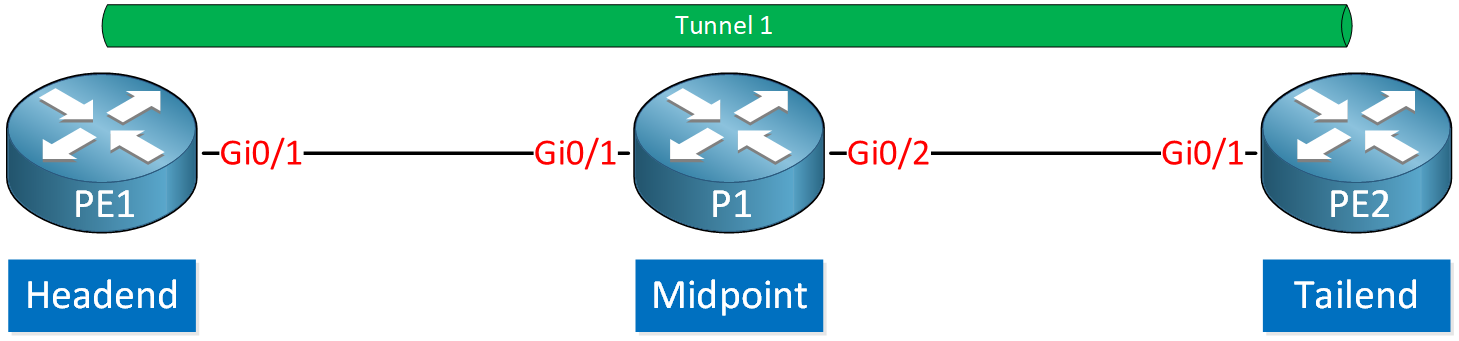
Here is the terminology we use for these routers:
-
The source of the tunnel is called the headend router.
- The destination of the tunnel is called the tailend router.
- Routers in the tunnel path are the midpoint routers.
Components
Let’s take a closer look at how MPLS TE works. There are four main components:
- Link information distribution
- Path calculation (CSPF)
- Path Setup (RSVP-TE)
- Forwarding traffic through TE tunnels
We’ll walk through these components one by one.
Link Information Distribution
IGPs only use an interface metric to find the shortest path to a destination. This is not enough for traffic engineering. We need to advertise additional link attributes such as:
- The total available bandwidth of an interface.
- The maximum reservable bandwidth (MRM) of an interface.
- This could be 100% of the available interface bandwidth or a percentage.
- TE Metric:
- A separate TE metric allows us to use a different metric than the IGP metric. By default, the TE metric is set to the IGP metric.
- Attribute flags (Link affinity):
- We can use attribute flags for link coloring. This allows us to add properties to links that we define ourselves. It allows you to include or exclude certain links.
- Shared Risk Link Group (SRLG):
- A set of links that share the same physical resource, such as a fiber link.
A link-state routing protocol can be easily adjusted to include this additional information and flood it within the area. OSPF and IS-IS both have extensions to include this extra information:
- OSPF supports this by adding an opaque LSA (type 10).
- IS-IS supports a new TLV with sub-TLVs.
This additional information is flooded throughout the area and routers store it in the Traffic Engineering Database (TED).
The LSDB and TED are two different databases. They both collect routing information flooded by IGPs. The TED, however, contains TE information next to all information from the LSDB.
Path Calculation (CSPF)
Regular SPF calculates the shortest path for every destination and installs this in the routing table.
Constrained Shortest Path First (CSPF) algorithm is an advanced version of the SPF algorithm we use for OSPF and IS-IS. We use it to calculate the shortest path with one or more constraints. These can be:
- Bandwidth requirements for the TE tunnel.
- Available bandwidth on interfaces.
- Explicit routes where it has to include or exclude specific interfaces or routers.
- Setup and hold priority for TE tunnels.
- Administrative groups (link coloring)
The tunnel headend router does CSPF path calculation. Other routers don’t.
The headend router takes the information from the TED and the constraints you configured. For example, it could look for a path for a TE tunnel that requires 50 Mbps and shouldn’t use link X or go through router Y.
When regular SPF finishes a calculation, we use the end result to add entries to the routing table. This is not the case with CSPF.
The result of a CSPF calculation is an ordered list of IP addresses with next hops for the path of the TE tunnel. We then use RSVP-TE to signal the path.
Path Setup (RSVP-TE)
To set up a path for our TE tunnel, we need a signaling protocol that reserves resources and establishes an LSP for a tunnel.
Resource Reservation Protocol (RSVP) was created for IntServ in the past, which never took off because of scalability issues. RSVP has been extended to use for MPLS TE and is called RSVP-TE.
After calculating a TE tunnel path with CSPF, the router will signal the tunnel with RSVP-TE.
RSVP-TE has three primary functions:
- Path setup and maintenance
- Path teardown
- Error signaling
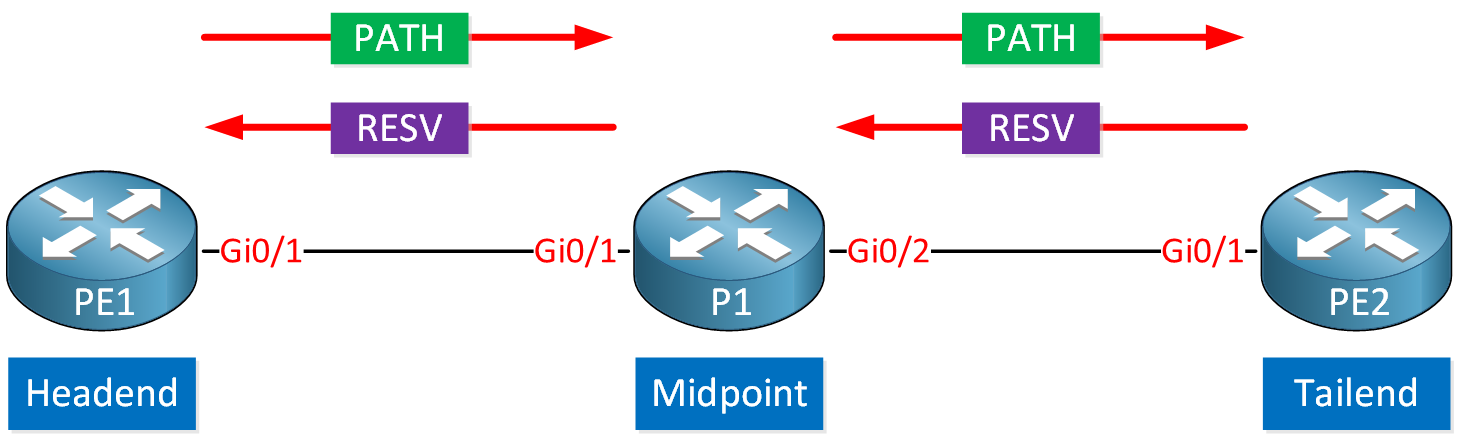
When the headend router wants to signal a TE tunnel, it sends a PATH message downstream to the tailend router. When the tailend router receives a PATH message, it replies with a RESV message, including the label we’ll use for the TE tunnel. Routers on the path that receive the RESV message reserve the required bandwidth and forward the message upstream to the headend router.
The LFIB is populated with RSVP labels that are allocated by RESV messages.
To accomplish all of this, RSVP-TE uses different messages and objects. I will cover these in the RSVP-TE lesson.
Forwarding Traffic Through TE Tunnels
Once the tunnel is established, it doesn’t do anything. It’s the same as with a simple GRE tunnel. You need to route traffic down the TE tunnel.
There are some “regular” routing options that you are already familiar with, such as:
And we have routing options that are specific to MPLS TE:
- Autoroute announce
- Autoroute destination
- Forwarding adjacency
- Policy-based tunnel selection (PBTS)
- Class-based tunnel selection (CBTS)
We’ll cover these in different lessons.


Hi All,
Can anyone plz tell me why IGP protocols require in MPLS-TE?
Hello Rajasekhar
IGPs are vital for the operation of MPLS in general. An MPLS network involves an overlay network composed of MPLS label switched paths that are established between MPLS routers. This is where the MPLS mechanisms operate. It also includes an underlay network which is the physical infrastructure and the IP network that supports it. This includes routers as well as the IP routing protocols running to make the underlay operational. Protocols such as OSPF, IS-IS, as well as EIGRP can be used for this purpose.
Strictly speaking, it is technicall
... Continue reading in our forumIf I set the mpls router-id on a router, do I need to also set the router-id for the mpls-te config as well?
Hello Leo
The quick and short answer is yes. Now let me explain further.
You must configure the MPLS-TE router-id separately from the MPLS LDP router-id. They are independent configurations that serve different protocols, though best practice is to set both to the same stable loopback interface.
I hope this has been helpful!
Laz
Make sense thank you