Lesson Contents
MPLS TE Fast Reroute (FRR) protects MPLS TE LSPs from link and node failures. We can do this with backup tunnels that repair the LSP of a primary (protected) tunnel. When the primary LSP is broken, we can continue to forward traffic down the backup tunnel until the headend router figures out a new best path. This takes less than ~50 ms. There are two protection types:
- Link protection
- Node protection
In the previous lesson, we covered link protection. In this lesson, we’ll look at node protection. The configuration is very similar, but some things are different behind the scenes.
Configuration
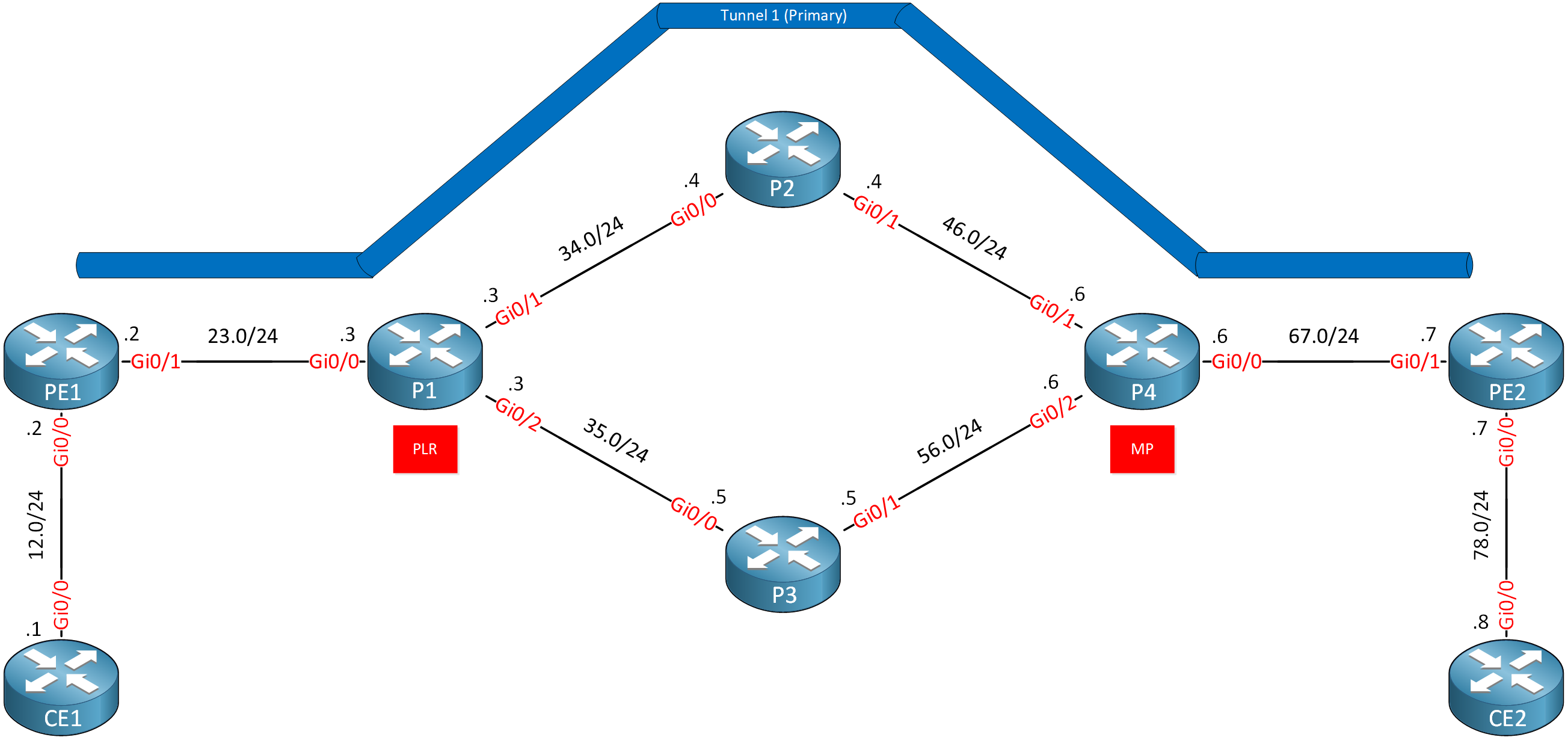
Here is the topology we’ll use:
All PE and P routers run MPLS TE. We have a TE tunnel from router PE1 to PE2. Traffic for this tunnel goes through P2. We want to create a backup tunnel to work around a node failure (P2). Here’s what it looks like:
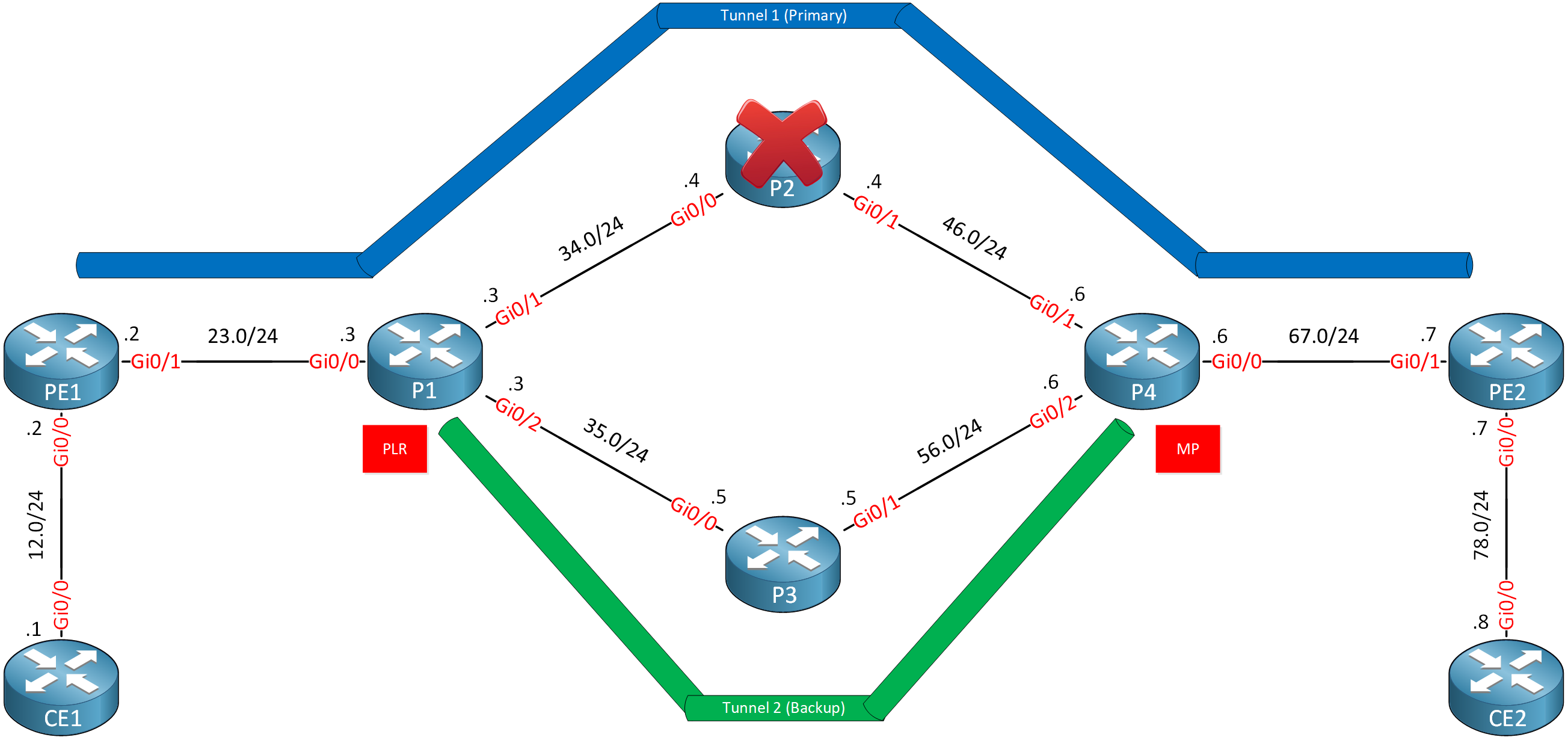
When P2 goes down, we want to send traffic down a backup tunnel that we configure on P1 and terminates on P4. This makes P1 the Point of Local Repair (PLR) and P4 the Merge Point (MP). We call this kind of backup tunnel a Next Next Hop (NNHOP) tunnel. From P1’s perspective, P4 is the next hop behind our next hop (P2).
Configurations
Want to take a look for yourself? Here you will find the startup configuration of each device.
CE1
hostname CE1
!
ip cef
!
interface Loopback0
ip address 1.1.1.1 255.255.255.255
ip router isis
isis circuit-type level-2-only
!
interface GigabitEthernet0/0
ip address 192.168.12.1 255.255.255.0
ip router isis
isis circuit-type level-2-only
!
router isis
net 49.0001.0001.0001.0001.0001.00
is-type level-2-only
metric-style wide
!
endCE2
hostname CE2
!
ip cef
!
interface Loopback0
ip address 8.8.8.8 255.255.255.255
ip router isis
isis circuit-type level-2-only
!
interface GigabitEthernet0/0
ip address 192.168.78.8 255.255.255.0
ip router isis
!
router isis
net 49.0001.0008.0008.0008.0008.00
is-type level-2-only
metric-style wide
!
endP1
hostname P1
!
ip cef
!
mpls traffic-eng tunnels
!
interface Loopback0
ip address 3.3.3.3 255.255.255.255
ip router isis
isis circuit-type level-2-only
!
interface GigabitEthernet0/0
ip address 192.168.23.3 255.255.255.0
ip router isis
mpls traffic-eng tunnels
mpls ip
isis circuit-type level-2-only
ip rsvp bandwidth 1000000
!
interface GigabitEthernet0/1
ip address 192.168.34.3 255.255.255.0
ip router isis
mpls traffic-eng tunnels
mpls ip
isis circuit-type level-2-only
ip rsvp bandwidth 1000000
!
interface GigabitEthernet0/2
ip address 192.168.35.3 255.255.255.0
ip router isis
mpls traffic-eng tunnels
mpls ip
isis circuit-type level-2-only
ip rsvp bandwidth 1000000
!
router isis
mpls traffic-eng router-id Loopback0
mpls traffic-eng level-2
net 49.0001.0003.0003.0003.0003.00
is-type level-2-only
metric-style wide
!
mpls ldp router-id Loopback0 force
!
endP2
hostname P2
!
ip cef
!
mpls traffic-eng tunnels
!
interface Loopback0
ip address 4.4.4.4 255.255.255.255
ip router isis
isis circuit-type level-2-only
!
interface GigabitEthernet0/0
ip address 192.168.34.4 255.255.255.0
ip router isis
mpls traffic-eng tunnels
mpls ip
isis circuit-type level-2-only
ip rsvp bandwidth 1000000
!
interface GigabitEthernet0/1
ip address 192.168.46.4 255.255.255.0
ip router isis
mpls traffic-eng tunnels
mpls ip
isis circuit-type level-2-only
ip rsvp bandwidth 1000000
!
router isis
mpls traffic-eng router-id Loopback0
mpls traffic-eng level-2
net 49.0001.0004.0004.0004.0004.00
is-type level-2-only
metric-style wide
!
mpls ldp router-id Loopback0 force
!
endP3
hostname P3
!
ip cef
!
mpls traffic-eng tunnels
!
interface Loopback0
ip address 5.5.5.5 255.255.255.255
ip router isis
isis circuit-type level-2-only
!
interface GigabitEthernet0/0
ip address 192.168.35.5 255.255.255.0
ip router isis
mpls traffic-eng tunnels
mpls ip
isis circuit-type level-2-only
ip rsvp bandwidth 1000000
!
interface GigabitEthernet0/1
ip address 192.168.56.5 255.255.255.0
ip router isis
mpls traffic-eng tunnels
mpls ip
isis circuit-type level-2-only
ip rsvp bandwidth 1000000
!
router isis
mpls traffic-eng router-id Loopback0
mpls traffic-eng level-2
net 49.0001.0005.0005.0005.0005.00
is-type level-2-only
metric-style wide
!
mpls ldp router-id Loopback0 force
!
endP4
hostname P4
!
ip cef
!
mpls traffic-eng tunnels
!
interface Loopback0
ip address 6.6.6.6 255.255.255.255
ip router isis
isis circuit-type level-2-only
!
interface GigabitEthernet0/0
ip address 192.168.67.6 255.255.255.0
ip router isis
mpls traffic-eng tunnels
mpls ip
isis circuit-type level-2-only
ip rsvp bandwidth 1000000
!
interface GigabitEthernet0/1
ip address 192.168.46.6 255.255.255.0
ip router isis
mpls traffic-eng tunnels
mpls ip
isis circuit-type level-2-only
ip rsvp bandwidth 1000000
!
interface GigabitEthernet0/2
ip address 192.168.56.6 255.255.255.0
ip router isis
mpls traffic-eng tunnels
mpls ip
isis circuit-type level-2-only
ip rsvp bandwidth 1000000
!
router isis
mpls traffic-eng router-id Loopback0
mpls traffic-eng level-2
net 49.0001.0006.0006.0006.0006.00
is-type level-2-only
metric-style wide
!
mpls ldp router-id Loopback0 force
!
endPE1
hostname PE1
!
ip cef
!
mpls traffic-eng tunnels
!
interface Loopback0
ip address 2.2.2.2 255.255.255.255
ip router isis
isis circuit-type level-2-only
!
interface Tunnel1
ip unnumbered Loopback0
tunnel mode mpls traffic-eng
tunnel destination 7.7.7.7
tunnel mpls traffic-eng autoroute announce
tunnel mpls traffic-eng priority 7 7
tunnel mpls traffic-eng bandwidth 750
tunnel mpls traffic-eng path-option 1 explicit name EXCLUDE_P3
no routing dynamic
!
interface GigabitEthernet0/0
ip address 192.168.12.2 255.255.255.0
ip router isis
isis circuit-type level-2-only
!
interface GigabitEthernet0/1
ip address 192.168.23.2 255.255.255.0
ip router isis
mpls traffic-eng tunnels
mpls ip
isis circuit-type level-2-only
ip rsvp bandwidth 1000000
!
router isis
mpls traffic-eng router-id Loopback0
mpls traffic-eng level-2
net 49.0001.0002.0002.0002.0002.00
is-type level-2-only
metric-style wide
!
ip explicit-path name EXCLUDE_P3 enable
exclude-address 5.5.5.5
!
mpls ldp router-id Loopback0 force
!
endPE2
hostname PE2
!
ip cef
!
mpls traffic-eng tunnels
!
interface Loopback0
ip address 7.7.7.7 255.255.255.255
ip router isis
isis circuit-type level-2-only
!
interface GigabitEthernet0/0
ip address 192.168.78.7 255.255.255.0
ip router isis
isis circuit-type level-2-only
!
interface GigabitEthernet0/1
ip address 192.168.67.7 255.255.255.0
ip router isis
mpls traffic-eng tunnels
mpls ip
isis circuit-type level-2-only
ip rsvp bandwidth 1000000
!
router isis
mpls traffic-eng router-id Loopback0
mpls traffic-eng level-2
net 49.0001.0007.0007.0007.0007.00
is-type level-2-only
metric-style wide
!
mpls ldp router-id Loopback0 force
!
endI use IOSv Software (VIOS-ADVENTERPRISEK9-M), Version 15.9(3)M4 on all routers. I have an explicit path on PE1 for the primary tunnel:
PE1#show ip explicit-paths
PATH EXCLUDE_P3 (strict source route, path complete, generation 6)
1: exclude-address 5.5.5.5This explicit path forces the traffic through P2. When P2 is unavailable, the tunnel will go down. This is important for this lab because, otherwise, once fast reroute is enabled, you’ll see that PE1 will use the backup tunnel only for a few seconds before switching over to a new path because of recalculation.
Without Fast Reroute
Before we enable fast reroute, I’d like to show you a packet capture of the RSVP PATH message. To capture this, we’ll restart the tunnel interface on PE1:
PE1(config)#interface Tunnel 1
PE1(config-if)#shutdown
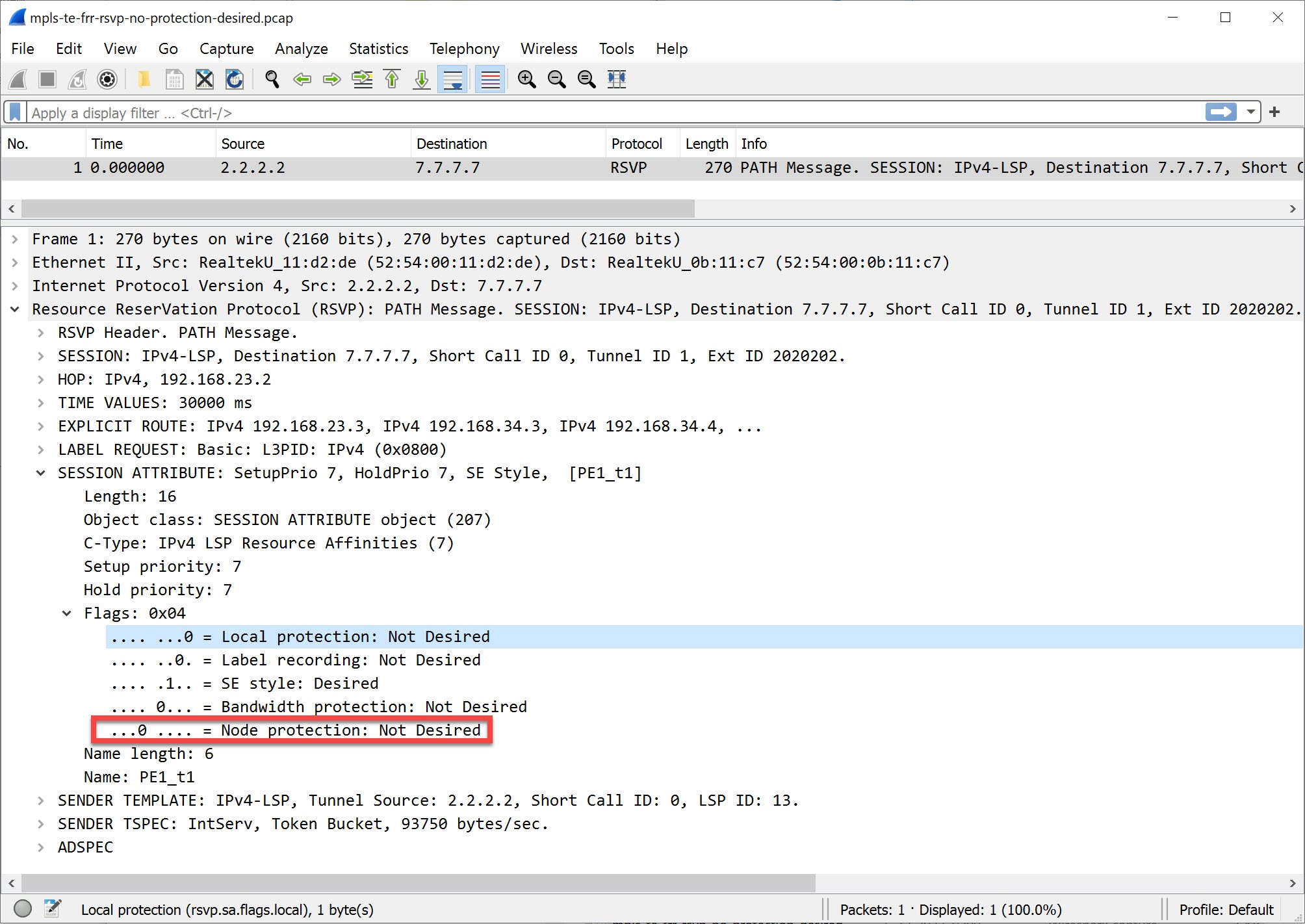
PE1(config-if)#no shutdownIn the RSVP PATH message, you’ll see this under the session attribute:
Packet Capture: MPLS TE FRR RSVP No Protection Desired
Above, you can see that PE1 doesn’t require node protection.
With Fast Reroute
Let’s configure MPLS TE fast reroute node protection for this network.
PE1
We’ll start with PE1. We need to add one command to the tunnel interface:
PE1(config)#interface Tunnel 1
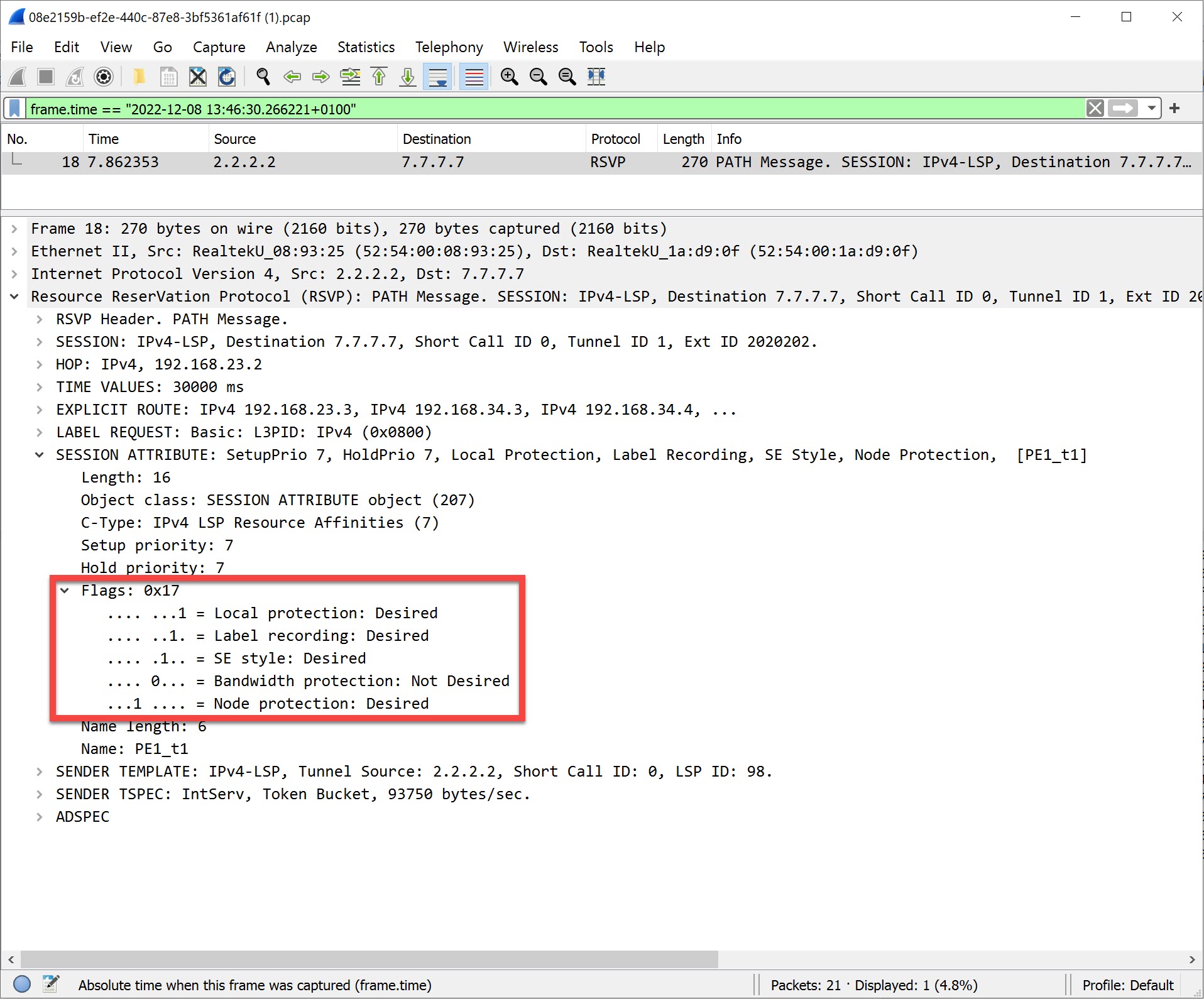
PE1(config-if)#tunnel mpls traffic-eng fast-reroute node-protectThe only difference with link protection is that we add the node-protect keyword. Let’s take another look at the RSVP PATH message:
Packet Capture: MPLS TE FRR RSVP Node Protection Desired
You can now see that PE1 desires node protection for its tunnel. When you enable node protection, you also have link protection.
P1
Let’s configure P1. Our backup tunnel should never use P2. This means the backup tunnel should go from P1 to P3 and terminate at P4. To accomplish this, I’ll configure an explicit path that excludes P2:
P1(config)#ip explicit-path name EXCLUDE_P2
P1(cfg-ip-expl-path)# exclude-address 4.4.4.4Now we can configure a backup tunnel interface:



Hi Rene, thanks for sharing these examples for for FRR (link/node protection). I found them very useful! In both examples I see that you are manually creating the backup tunnels. That would be an enormous task in a large Service Provider Network which may have many alternative paths. it is quite common to have the backup tunnels created automatically. Its probably worth mentioning, or showing an example of how to create them automatically in IOS.
Hello Douglas
Thanks for your useful suggestion! I will pass it on to Rene.
Thanks again!
Laz
Hello Anudeep
Indeed you are correct. This seems to be a typo in the lesson. I will let Rene know to take a look and make the necessary modifications.
Thanks for pointing that out!
Laz
Hello @cdeepu702 ,
Which one do you mean? We have this:
We exclude 4.4.4.4 (P2 loopback) and the tunnel 2 destination is 6.6.6.6 (P4).
Rene
My Bad I think I am confused with routers and their IP addresses.