Lesson Contents
When you use the route-target export command for a VRF, it adds the same route-target to all VPN routes. With an export map, you can use the power of a route-map to decide which VPN routes should get exported and what route-targets to use.
Let’s look at an example. Consider the following topology:
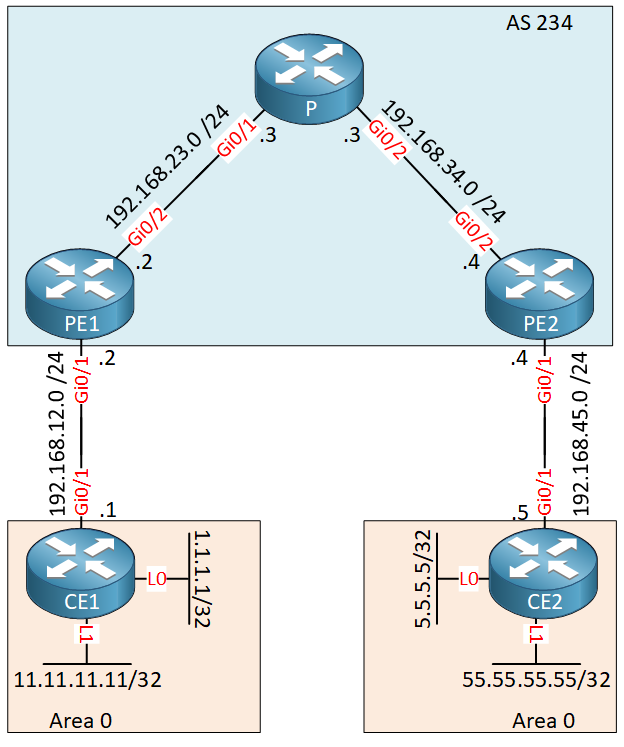
We have a simple MPLS VPN PE CE topology with a single customer that has two sites. Each site has a router with two loopback interfaces. Take a look at the VRF configuration of PE1 and PE2:
PE1#show running-config | begin ip vrf
ip vrf CUSTOMER
rd 1:1
route-target export 1:1
route-target import 2:2PE2#show running-config | begin ip vrf
ip vrf CUSTOMER
rd 1:1
route-target export 2:2
route-target import 1:1VPN routes on PE1 are exported with RT 1:1 and PE2 exports its VPN routes with RT 2:2.
With the route-target export command, all VPN routes are exported. There is no way to filter anything. This means that CE1 and CE2 will learn about each other’s routes that they advertise:
CE1#show ip route ospf
5.0.0.0/32 is subnetted, 1 subnets
O IA 5.5.5.5 [110/3] via 192.168.12.2, 00:09:03, GigabitEthernet0/1
55.0.0.0/32 is subnetted, 1 subnets
O IA 55.55.55.55 [110/3] via 192.168.12.2, 00:00:02, GigabitEthernet0/1
O IA 192.168.45.0/24 [110/2] via 192.168.12.2, 00:09:03, GigabitEthernet0/1CE2#show ip route ospf
1.0.0.0/32 is subnetted, 1 subnets
O IA 1.1.1.1 [110/3] via 192.168.45.4, 00:09:31, GigabitEthernet0/1
11.0.0.0/32 is subnetted, 1 subnets
O IA 11.11.11.11 [110/3] via 192.168.45.4, 00:00:45, GigabitEthernet0/1
O IA 192.168.12.0/24 [110/2] via 192.168.45.4, 00:09:31, GigabitEthernet0/1We can see the RT that was added. For example, here’s PE1:
PE1#show ip bgp vpnv4 all 1.1.1.1/32 | include Extended
Extended Community: RT:1:1 OSPF DOMAIN ID:0x0005:0x000000020200PE1#show ip bgp vpnv4 all 11.11.11.11/32 | include Extended
Extended Community: RT:1:1 OSPF DOMAIN ID:0x0005:0x000000020200PE1#show ip bgp vpnv4 all 192.168.12.0/24 | include Extended
Extended Community: RT:1:1 OSPF DOMAIN ID:0x0005:0x000000020200What if I want to filter some of these VPN routes? Or use a different route-target for some of them? That’s what we have export maps for…
Configuration
I will use the topology from above to demonstrate the export map. If you want to follow along, you can use my configurations:
Configurations
Want to take a look for yourself? Here you will find the startup configuration of each device.
CE1
hostname CE1
!
ip cef
!
interface Loopback0
ip address 1.1.1.1 255.255.255.255
!
interface Loopback1
ip address 11.11.11.11 255.255.255.255
!
interface GigabitEthernet0/1
ip address 192.168.12.1 255.255.255.0
!
router ospf 1
network 1.1.1.1 0.0.0.0 area 0
network 11.11.11.11 0.0.0.0 area 0
network 192.168.12.0 0.0.0.255 area 0
!
endCE2
hostname CE2
!
ip cef
!
interface Loopback0
ip address 5.5.5.5 255.255.255.255
!
interface Loopback1
ip address 55.55.55.55 255.255.255.255
!
interface GigabitEthernet0/1
ip address 192.168.45.5 255.255.255.0
!
router ospf 1
network 5.5.5.5 0.0.0.0 area 0
network 55.55.55.55 0.0.0.0 area 0
network 192.168.45.0 0.0.0.255 area 0
!
endP
hostname P
!
ip cef
!
interface Loopback0
ip address 3.3.3.3 255.255.255.255
!
interface GigabitEthernet0/1
ip address 192.168.23.3 255.255.255.0
mpls ip
!
interface GigabitEthernet0/2
ip address 192.168.34.3 255.255.255.0
mpls ip
!
router ospf 1
network 3.3.3.3 0.0.0.0 area 0
network 192.168.23.0 0.0.0.255 area 0
network 192.168.34.0 0.0.0.255 area 0
!
endPE1
hostname PE1
!
ip vrf CUSTOMER
rd 1:1
route-target export 1:1
route-target import 2:2
!
ip cef
!
interface Loopback0
ip address 2.2.2.2 255.255.255.255
!
interface GigabitEthernet0/1
ip vrf forwarding CUSTOMER
ip address 192.168.12.2 255.255.255.0
!
interface GigabitEthernet0/2
ip address 192.168.23.2 255.255.255.0
!
router ospf 2 vrf CUSTOMER
redistribute bgp 234 subnets
network 192.168.12.0 0.0.0.255 area 0
!
router ospf 1
mpls ldp autoconfig
network 2.2.2.2 0.0.0.0 area 0
network 192.168.23.0 0.0.0.255 area 0
!
router bgp 234
bgp log-neighbor-changes
neighbor 4.4.4.4 remote-as 234
neighbor 4.4.4.4 update-source Loopback0
!
address-family ipv4
no neighbor 4.4.4.4 activate
exit-address-family
!
address-family vpnv4
neighbor 4.4.4.4 activate
neighbor 4.4.4.4 send-community extended
exit-address-family
!
address-family ipv4 vrf CUSTOMER
redistribute ospf 2
exit-address-family
!
endPE2
hostname PE2
!
ip vrf CUSTOMER
rd 1:1
route-target export 2:2
route-target import 1:1
!
ip cef
!
interface Loopback0
ip address 4.4.4.4 255.255.255.255
!
interface GigabitEthernet0/1
ip vrf forwarding CUSTOMER
ip address 192.168.45.4 255.255.255.0
!
interface GigabitEthernet0/2
ip address 192.168.34.4 255.255.255.0
!
router ospf 2 vrf CUSTOMER
redistribute bgp 234 subnets
network 192.168.45.0 0.0.0.255 area 0
!
router ospf 1
mpls ldp autoconfig
network 4.4.4.4 0.0.0.0 area 0
network 192.168.34.0 0.0.0.255 area 0
!
router bgp 234
bgp log-neighbor-changes
neighbor 2.2.2.2 remote-as 234
neighbor 2.2.2.2 update-source Loopback0
!
address-family ipv4
no neighbor 2.2.2.2 activate
exit-address-family
!
address-family vpnv4
neighbor 2.2.2.2 activate
neighbor 2.2.2.2 send-community extended
exit-address-family
!
address-family ipv4 vrf CUSTOMER
redistribute ospf 2
exit-address-family
!
endEmpty Export Map
Let’s start with a simple example. I will create a new route-map that permits everything and sets the route-target to 3:3:
PE1(config)#route-map EXPORT_MAP permit 10
PE1(config-route-map)#set extcommunity rt 3:3You activate it under the VRF configuration with the export map command:
PE1(config)#ip vrf CUSTOMER
PE1(config-vrf)#export map EXPORT_MAPLet’s look at the result:
PE1#show ip bgp vpnv4 all 1.1.1.1/32 | include Extended
Extended Community: RT:3:3 OSPF DOMAIN ID:0x0005:0x000000020200PE1#show ip bgp vpnv4 all 11.11.11.11/32 | include Extended
Extended Community: RT:3:3 OSPF DOMAIN ID:0x0005:0x000000020200PE1#show ip bgp vpnv4 all 192.168.12.0/24 | include Extended
Extended Community: RT:3:3 OSPF DOMAIN ID:0x0005:0x000000020200As you can see above, it overwrites the RT that is set with the route-target export command. All routes now have an RT of 3:3.
Export Map with Prefix-list
The output we just saw might not be what we are looking for. Let’s try something else. What if we only want to set the RT to 3:3 for the 1.1.1.1/32 prefix from CE1?
We can do this with an access-list or prefix-list. I’ll use a prefix-list:
PE1(config)#ip prefix-list CE1_L0 permit 1.1.1.1/32PE1(config)#route-map EXPORT_MAP permit 10
PE1(config-route-map)#match ip address prefix-list CE1_L0Here’s what the VPN routes now look like on PE1:
PE1#show ip bgp vpnv4 all 1.1.1.1/32 | include Extended
Extended Community: RT:3:3 OSPF DOMAIN ID:0x0005:0x000000020200PE1#show ip bgp vpnv4 all 11.11.11.11/32 | include Extended
Extended Community: RT:1:1 OSPF DOMAIN ID:0x0005:0x000000020200PE1#show ip bgp vpnv4 all 192.168.12.0/24 | include Extended
Extended Community: RT:1:1 OSPF DOMAIN ID:0x0005:0x000000020200This is looking better. 1.1.1.1/32 has the RT of 3:3 and all other VPN routes still have RT 1:1 that was set with the route-target export command.
Because of the new RT, CE2 no longer has 1.1.1.1/32:
CE2#show ip route 1.1.1.1
% Network not in tableIf we want CE2 to have this route, we’ll have to import the new RT on PE2:
PE2(config)#ip vrf CUSTOMER
PE2(config-vrf)#route-target import 3:3Now it’s back:
CE2#show ip route 1.1.1.1
Routing entry for 1.1.1.1/32
Known via "ospf 1", distance 110, metric 3, type inter area
Last update from 192.168.45.4 on GigabitEthernet0/1, 00:00:21 ago
Routing Descriptor Blocks:
* 192.168.45.4, from 192.168.45.4, 00:00:21 ago, via GigabitEthernet0/1
Route metric is 3, traffic share count is 1Export Map Additive
In the previous two examples, the export map has overwritten our RT. It’s also possible to add an additional RT. You only have to add the additive parameter in your route-map:



Thanks Rene - so am I right in thinking there is no implicit deny on a route map used as an export map in this process? Anything not matched on the route-map will just use the default settings configured.
Normally when applying a route-map to a neighbour in IPv4 (e.g. neighbor X route-map Y) if something isn’t positively matched in the route-map, it will get dropped?
Hi Chris,
It still has the implicit deny but when you use a route-map as an export-map, it only tells the router which route-targets to add. When you use a route-map with a neighbor for a routing protocol, it works as a filter for routes.
For example, this is the default route-target on PE1:
And we use this export-map:
Then we end up with:
... Continue reading in our forumHi Rene,
Thank you for your nice lesson . Need to know more about the “Additive” keyword functionality . Can you please more brief on it?
BR//ZAMAN
Hello Zaman
The additive keyword will allow you to add an export map without overwriting the previously configured ones. For example, if you configure the following:
and then at a later time you configure this:
The result is that the 1:1 entry will be overwritten by the 3:3 entry. However, if you use the
... Continue reading in our forumadditivekeyword like this instead:Hi @lagapidis
So will this additive keyword still cause my routes to stay at the other end PE orwill it be removed from the far end PE node ?