Lesson Contents
In my introduction to MPLS I explained why we use MPLS and explained some of the basics of how we use labels for forwarding decisions. In this lesson, we’ll take a closer look at the MPLS labels, the devices that we use and how IP packets travel through the MPLS network.
MPLS Label Format
The MPLS header has been standardized, you can find it in RFC 3032. The header is pretty simple, here’s what it looks like:
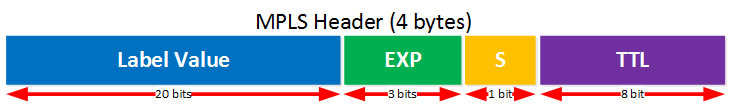
Here’s what the different fields are used for:
- Label value: the name says it all, this is where you will find the value of the label.
- EXP: these are the three experimental bits. These are used for QoS, normally the IP precedence value of the IP packet will be copied here.
- S: this is the “bottom of stack” bit. With MPLS it’s possible to add more than one label, you’ll see why in some of the MPLS VPN lessons. When this bit is set to one, it’s the last MPLS header. When it’s set to zero then there is one or more MPLS headers left.
- TTL: just like in the IP header, this is the time to live field. You can use this for traces in the MPLS network. Each hop decrements the TTL by one.
The MPLS header is added in between the L2 and L3 header:

That’s why we call it a “layer 2.5” protocol. Here’s an example of what it looks like in wireshark:
Frame 5: 118 bytes on wire (944 bits), 118 bytes captured (944 bits)
Ethernet II, Src: Cisco_c4:f3:22 (00:23:04:c4:f3:22), Dst: Cisco_be:0e:c9 (00:16:c7:be:0e:c9)
Destination: Cisco_be:0e:c9 (00:16:c7:be:0e:c9)
Source: Cisco_c4:f3:22 (00:23:04:c4:f3:22)
Type: MPLS label switched packet (0x8847)
MultiProtocol Label Switching Header, Label: 16, Exp: 0, S: 1, TTL: 254
0000 0000 0000 0001 0000 .... .... .... = MPLS Label: 16
.... .... .... .... .... 000. .... .... = MPLS Experimental Bits: 0
.... .... .... .... .... ...1 .... .... = MPLS Bottom Of Label Stack: 1
.... .... .... .... .... .... 1111 1110 = MPLS TTL: 254
Internet Protocol version 4, Src: 5.5.5.5 (5.5.5.5), Dst: 1.1.1.1 (1.1.1.1)
Version: 4
Header Length: 20 bytes
Differentiated Services Field: 0x00 (DSCP 0x00: Default; ECN: 0x00: Not-ECT (Not ECN-Capable Transport))
Total Length: 100
Identification: 0x006e (110)
Flags: 0x00
Fragment offset: 0
Time to live: 254
Protocol: ICMP (1)
Header checksum: 0xb01f [validation disabled]
Source: 5.5.5.5 (5.5.5.5)
Destination: 1.1.1.1 (1.1.1.1)
[Source GeoIP: Unknown]
[Destination GeoIP: Unknown]
Internet Control Message ProtocolAbove you have an example of the MPLS header in between the Ethernet and IP header. You can also see the different fields, this header uses label value 16. We don’t use QoS and since there is only one MPLS header, the bottom of label stack bit has been set.
MPLS Devices and Operations
Now you know what the MPLS labels look like, let’s talk about a bit about the different devices you will encounter in a MPLS network. Here’s an overview:
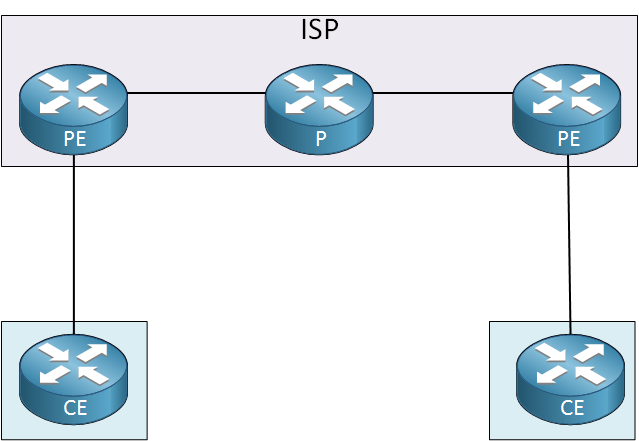
Above you will find three different routers:
- CE (Customer Edge): this device is the last device in the customer’s network, it could be a L2 or L3 device. In my picture I used a router but for example, it could be a switch. This device does not use MPLS.
- PE (Provider Edge): this device is owned by the ISP and sits at the edge of the ISP’s network. It has an important role…it receives packets or frames from the customer and will then add a MPLS label to it and forwards towards the core. Another common name for this device is LER (Label Edge Router).
- P (Provider): this device connects to PE routers and other P routers. It has a simple job, it switches packets based on their labels or removes the labels. Another common name for this device is the LSR (Label Switch Router) or transit router.
There are three actions we can perform with labels:
- Label push: when we add a label to a packet, we call it a label push.
- Label swap: replacing a label with another value is called a label swap.
- Label pop: removing the label is called a label pop.
Let’s look at an example of how labels are pushed, swapped and popped in a MPLS network:

Let me add some more detail to the picture above:


Rene,
Great lesson however, I have a question about MPLS TTL =254. It means there are 254 hops from CE1 to CE2 for each hop TTL decreases by 1 is that correct? How do we determine or define TTL value?
Thanks
Hamood
Hi Hamood,
That’s right, the TTL for the MPLS label works the same as the TTL for the IP packet.
When the PE router receives an IP packet then it will copy the TTL of the IP packet into the MPLS label TTL. Within the MPLS Core, the TTL of the label decreases at each hop. When the MPLS label is popped, it’s TTL value is copied into the TTL of the IP packet.
Rene
Hi Rene,
Thank you for the excellent explanation.
Question is regarding the frame-size, with the MPLS header and the ethernet frame the MTU would be maximum 1504 bytes.
It this going to be fragmented?
Rgd,
Hans
Hi Hans,
Most interfaces nowadays support Jumbo frames (9000 bytes) so the extra label(s) from MPLS shouldn’t be a problem. You should check this though and increase the MTU if required.
Rene
Dear Rene,
What is the best practice to configure the MTU for MPLS? I see some need 1504, some 1508, some 1522 or 1526.
Davis