Prefixes that are advertised by routing protocols like OSPF, EIGRP, or RIP can be filtered. One way of doing this is by using a distribute list. In this lesson, I’ll give you an example of how to filter certain prefixes with a distribute-list.
Filtering can occur inbound or outbound. If you have an inbound route filter, we will first check if the network is permitted or not before we will accept it. Let’s take a look at a network topology so I can give you a demonstration:
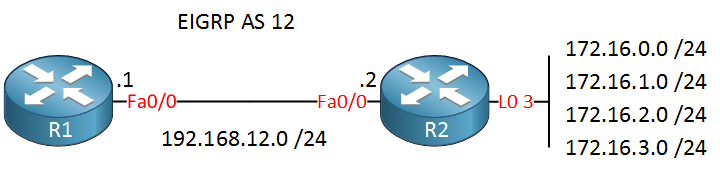
R1 and R2 are connected and run EIGRP. On R2, I have added a couple of loopback interfaces with prefixes that we will advertise in EIGRP. Here is the configuration:
R1(config)#router eigrp 12
R1(config-router)#no auto-summary
R1(config-router)#network 192.168.12.0R2(config)#router eigrp 12
R2(config-router)#no auto-summary
R2(config-router)#network 192.168.12.0
R2(config-router)#network 172.16.0.0 0.0.3.255Above, you can see that we advertise all prefixes in EIGRP.
R1#show ip route eigrp
172.16.0.0/24 is subnetted, 4 subnets
D 172.16.0.0 [90/156160] via 192.168.12.2, 00:01:07, FastEthernet0/0
D 172.16.1.0 [90/156160] via 192.168.12.2, 00:01:07, FastEthernet0/0
D 172.16.2.0 [90/156160] via 192.168.12.2, 00:01:07, FastEthernet0/0
D 172.16.3.0 [90/156160] via 192.168.12.2, 00:01:07, FastEthernet0/0If we look at the routing table of router R1, we can see all those networks on the loopback interfaces as they should be. Now we’ll see if we can do some filtering.
R1(config)#router eigrp 12
R1(config-router)#distribute-list ?
<1-199> IP access list number
<1300-2699> IP expanded access list number
WORD Access-list name
gateway Filtering incoming updates based on gateway
prefix Filter prefixes in routing updates
route-map Filter prefixes based on the route-mapGo to the configuration of the EIGRP process and use the distribute-list command to see your options. As you can see, we can choose between an access-list, a prefix list, or a route-map. Let’s start with the access-list. You are probably familiar with access lists if you studied CCNA.
R1(config-router)#distribute-list 1 ?
in Filter incoming routing updates
out Filter outgoing routing updatesIf you specify an access-list number, you can choose if this route filter has to be inbound or outbound.
R1(config-router)#distribute-list 1 in ?
Async Async interface
BVI Bridge-Group Virtual Interface
CDMA-Ix CDMA Ix interface
CTunnel CTunnel interface
Dialer Dialer interface
FastEthernet FastEthernet IEEE 802.3
Lex Lex interface
Loopback Loopback interface
MFR Multilink Frame Relay bundle interface
Multilink Multilink-group interface
Null Null interface
Port-channel Ethernet Channel of interfaces
Tunnel Tunnel interface
Vif PGM Multicast Host interface
Virtual-PPP Virtual PPP interface
Virtual-Template Virtual Template interface
Virtual-TokenRing Virtual TokenRing
<cr>
If you want, you can choose the interface to which to apply the inbound route filter to. If you don’t specify an interface, it will apply to all interfaces.



Hey, what is the difference in using route-maps or access-lists or prefixlists when applied to distribute-list ? they all do the same in regards to filtering routes in ospf or eigrp ? are there any minor difference between those ? can you please explain in detail. Thank you.
Hi Sri T,
All three of them will filter routers but there are some big differences…
If you haven’t seen my distribute-list with prefix-list tutorial then take a look at this link:
https://networklessons.com/ip-routing/how-to-configure-prefix-list-on-cisco-router
It will explain the prefix-list in detail.
The route-map is also very powerful…while access-lists and prefix-lists are both used to match on IP addresses or network addresses, route-maps can match on many other things including:
Incoming interface
... Continue reading in our forumNext hop IP address
Source of route
Metrics
Route-type
Rene , this is wrong lesson link
you have to links referring to the same lesson
this lesson should be for EIGRP filtering with prefix-list
Hi Rene, I have a question regarding recusive routing and the filtering of routing interfaces.
... Continue reading in our forumI have a network similar to the one shown in the EIGRP Route-MAP Filtering lesson. The difference I have in my network is that the Tunnel areas has two ASAs so that if the primary route fails routing information can be sent over a tunnel to the remote site via the internet. Routing on this network is provided bt EIGRP. Currently when the primary route fails the link that goes over the internet goes into recursive routing and fails.
Hi @Robhorseman101,
The EIGRP route-map filtering lesson only has two routers with a single link so I think you had something else in mind?
In your config, I see the tunnel interfaces of your routers:
And:
Not sure on which router you get the recursive routing error but for example, if it’s the first one th
... Continue reading in our forum