Lesson Contents
In a previous lesson, I explained how to configure dynamic NAT from the inside to the outside. In this lesson, we add a DMZ and some more NAT translations. Here’s the topology that we will use:
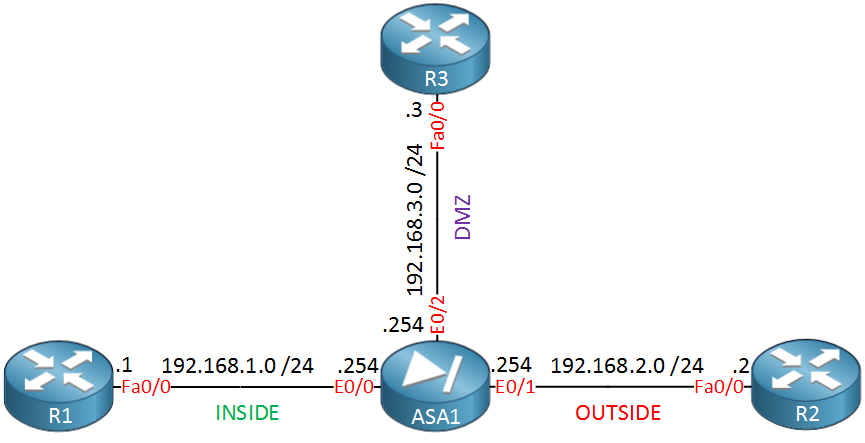
In this example, we have our INSIDE, OUTSIDE, and DMZ interfaces. The security levels of these interfaces are:
- INSIDE: 100
- OUTSIDE: 0
- DMZ: 50
We can go from a “high” security level to a “low” security level, so hosts from the INSIDE can reach the DMZ and OUTSIDE. Hosts from the DMZ will also be able to reach the OUTSIDE. We will configure NAT for the following traffic patterns:
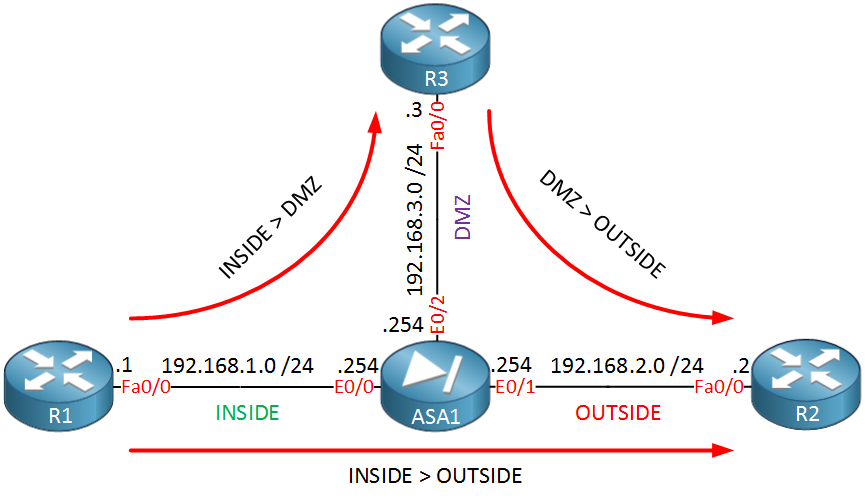
- Traffic from hosts on the INSIDE to the OUTSIDE: we’ll use a “public” pool for this.
- Traffic from hosts on the INSIDE to the DMZ: we’ll use a “DMZ” pool for this.
- Traffic from hosts on the DMZ to the OUTSIDE: we’ll use the same public pool for this.
Here’s what a visualization of these NAT rules look like:
ASA1(config)# interface e0/0
ASA1(config-if)# nameif INSIDE
ASA1(config-if)# ip address 192.168.1.254 255.255.255.0
ASA1(config-if)# no shutdownASA1(config)# interface e0/1
ASA1(config-if)# nameif OUTSIDE
ASA1(config-if)# ip address 192.168.2.254 255.255.255.0
ASA1(config-if)# no shutdownASA1(config)# int e0/2
ASA1(config-if)# nameif DMZ
ASA1(config-if)# security-level 50
ASA1(config-if)# ip address 192.168.3.254 255.255.255.0
ASA1(config-if)# no shutdownThe INSIDE and OUTSIDE security levels have a default value. The DMZ I configured to 50 myself. Now, let’s look at the dynamic NAT configuration…
Dynamic NAT with three Interfaces
First, we will create the pools:
ASA1(config)# object network PUBLIC_POOL
ASA1(config-network-object)# range 192.168.2.100 192.168.2.200ASA1(config)# object network DMZ_POOL
ASA1(config-network-object)# range 192.168.3.100 192.168.3.200I will use a range of IP addresses from the subnet configured on the OUTSIDE and DMZ interface. Now, we can create some network objects for the NAT translations:
ASA1(config)# object network INSIDE_TO_DMZ
ASA1(config-network-object)# subnet 192.168.1.0 255.255.255.0
ASA1(config-network-object)# nat (INSIDE,DMZ) dynamic DMZ_POOLThe first network object is INSIDE_TO_DMZ and specifies the subnet of the INSIDE hosts. The NAT entry translates the 192.168.1.0 /24 subnet to IP addresses in the pool called DMZ_POOL. The other network objects are similar:
ASA1(config)# object network INSIDE_TO_OUTSIDE
ASA1(config-network-object)# subnet 192.168.1.0 255.255.255.0
ASA1(config-network-object)# nat (INSIDE,OUTSIDE) dynamic PUBLIC_POOLThis one is for traffic from the INSIDE to the OUTSIDE. It uses the PUBLIC_POOL. The last one is for traffic from our DMZ to the OUTSIDE:
ASA1(config)# object network DMZ_TO_OUTSIDE
ASA1(config-network-object)# subnet 192.168.3.0 255.255.255.0
ASA1(config-network-object)# nat (DMZ,OUTSIDE) dynamic PUBLIC_POOLThat’s all we have to configure. Let’s verify our work…
Verification
We’ll generate traffic between the routers and see if their IP packets are correctly translated. Let’s send something from R1 to R2 (INSIDE to OUTSIDE):
R1#telnet 192.168.2.2
Trying 192.168.2.2 ... OpenWe have a connection, so let’s see if we have a translation:
ASA1# show xlate
1 in use, 1 most used
Flags: D - DNS, e - extended, I - identity, i - dynamic, r - portmap,
s - static, T - twice, N - net-to-net
NAT from INSIDE:192.168.1.1 to OUTSIDE:192.168.2.166 flags i idle 0:00:33 timeout 3:00:00Great, IP address 192.168.1.1 was translated to 192.168.2.166. Let’s also generate some traffic from R1 to R3 (INSIDE to DMZ):
R1#telnet 192.168.3.3
Trying 192.168.3.3 ... OpenIt’s working, let’s check the translation:
ASA1# show xlate
2 in use, 2 most used
Flags: D - DNS, e - extended, I - identity, i - dynamic, r - portmap,
s - static, T - twice, N - net-to-net
NAT from INSIDE:192.168.1.1 to DMZ:192.168.3.146 flags i idle 0:00:14 timeout 3:00:00
NAT from INSIDE:192.168.1.1 to OUTSIDE:192.168.2.166 flags i idle 0:00:23 timeout 3:00:00So far, so good. It was translated from 192.168.1.1 to 192.168.3.146. Last but not least, let’s try some packets from R3 to R2 (DMZ to OUTSIDE):


Hi Rene,
Do we need to nat from inside to dmz ?
Thanks
Hi Sims,
Below is part of the config and yes it does require that the lan is natt’d to the DMZ_POOL.
You could also use no-natcontrol which exempts you from having to do nat across the asa’s interfaces.
Hi Sims & Paul,
NAT control was used on ASA versions before 8.3. Basically it meant that when you wanted to go from a high security level to a lower one (for example LAN to DMZ) that it had to be NAT translated.
With ASA 8.3 and higher, NAT control is disabled and unavailable. You don’t have to configure NAT if you want to access the DMZ from your LAN.
Rene
Good to Know thanks Rene
There is no need to configure an access-list ?