Lesson Contents
Each interface on a Cisco ASA firewall is a security zone so normally this means that the number of security zones is limited to the number of physical interfaces that we have. For example, the ASA 5510 has 4 physical interfaces and often you will only see the following three security zones:
- Inside
- Outside
- DMZ
For a simple scenario this is more than enough but sometimes it’s useful to create additional security zones. For example, maybe you don’t want one “big” DMZ with all your servers but more separation. You could create a security zone with all your mail servers, another one with all the DNS servers and one more with all web servers. This is a good security practice but we’ll need more interfaces to accomplish this.
Luckily the ASA supports trunking and logical interfaces which means we can create multiple logical sub-interfaces on a single physical interface. Each sub-interface can be assigned to a different security zone and they are separated by VLANs.
This means you can create way more than 4 security zones, depending on your ASA model you can create up to 1024 VLANs.
The physical interface on the ASA will become a trunk interface which is not assigned to any security zone. Each sub-interface will be configured for a VLAN, security zone and security level.
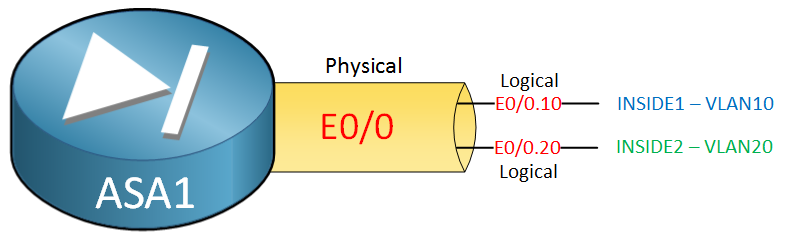
Here’s a picture to visualize this:
In the example above we have a Ethernet 0/0 physical interface and two sub-interfaces:
- Ethernet 0/0.10 will be used for security zone “INSIDE1” and uses VLAN 10.
- Ethernet 0/0.20 will be used for security zone “INSIDE2” and uses VLAN 20.
- The physical interface is not configured for any security zone.
Basically this is the same thing as the router on a stick configuration on Cisco IOS routers but on the ASA we also have security zones.
Configuration
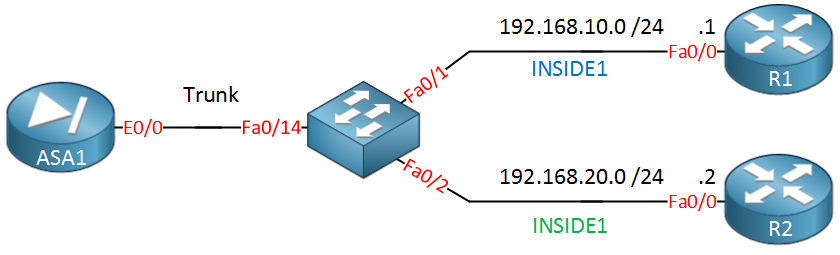
Let’s take a look at a configuration example for this. I’ll use the following topology:
On the left side we have our ASA, it’s Ethernet 0/0 interface will be used for trunking. The switch in the middle is connected to two routers, R1 and R2. Each router represents a host in a different security zone:
- INSIDE1 which uses VLAN 10 and has a security level of 70.
- INSIDE2 which uses VLAN 20 and has a security level of 80.
Let’s start with the ASA configuration…
ASA Configuration
ASA1(config)# interface Ethernet 0/0
ASA1(config-if)# no nameif
ASA1(config-if)# no security-level
ASA1(config-if)# no ip address
ASA1(config-if)# no shutdownThe configuration above is the default configuration for an interface on the ASA, there should be no security zone, no security-level and no IP address. Make sure the interface is not in shutdown and we can continue with the sub-interfaces:



Question:
Why I can not create sub-interfaces if I have the security plus license?
... Continue reading in our forumMaximum Physical Interfaces : 8 perpetual
VLANs : 20 DMZ Unrestricted
Dual ISPs : Enabled perpetual
VLAN Trunk Ports : 8 perpetual
Inside Hosts : Unlimited perpetual
Failover : Active/Standby perpetual
VPN-DES : Enabled perpetual
VPN-3DES-AES : Enabled
Hi Alfredo,
The ASA 5505 only has switchports and it doesn’t support sub-interfaces. To make it work, you should make one of the interfaces a trunk that connects to the switch and then use SVI interfaces. For example:
interface Ethernet 0/0
switchport mode trunk
interface vlan 10
nameif INSIDE
security-level 100
ip address 192.168.10.254 255.255.255.0
Did this from memory but that should do the job.
Rene
If I have an existing interface on an ASA5580 redundant pair and want to create subinterfaces on that interface are there any production challenges I will face? Let say I have Gi8/2 with an existing ip 172.21.16.254, now I want to create two subinterface on Gi8/2 one for 172.21.16.x and one for 10.248.80.x. I know how to create sub-interfaces however not sure of the impact, I know when I move 172.21.16 to a subinterface I will lose connectivity while I reconfig the interface but I am wondering if I need to reload the ASA once the config is done or will it updat
... Continue reading in our forumHi Bill,
It shouldn’t be a problem and downtime should be minimum. Once you move the configuration from the physical interface to the sub-interface and set the switchport to trunk, it will work immediately. No need to reboot the ASA or anything.
Rene
Hello Rene,
This seems to work on the 5506 so far, Is there a way to specify a native VLAN on the ASA port?
Thanks,
Chris