Lesson Contents
In a previous lesson, I explained how to configure a site-to-site IPsec IKEv1 VPN between two Cisco ASA firewalls. What if one of the ASA firewalls has a dynamic IP address?
You could take a gamble and configure the IP address manually but as soon as your ISP gives you another IP address, your VPN will collapse.
In this lesson, I’ll show you how to configure a site-to-site IPsec VPN but we’ll use a dynamic IP address on one of the ASAs. Here’s the topology we will use:
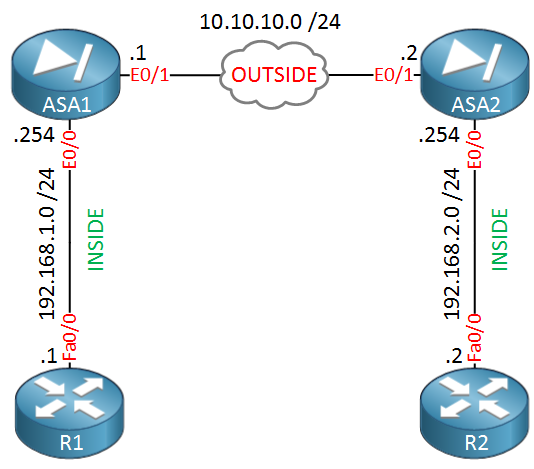
ASA1 will use a static IP, ASA2 will use a dynamic IP address.
Configuration
We’ll have to configure phase 1 and 2. I’ll show you the similarities and differences between the two ASA firewalls.
Phase 1 Configuration
We will start with the IKEv1 policy. This will be the same on both ASAs so let’s create a policy:
ASA1 & ASA2
(config)# crypto ikev1 policy 10
(config-ikev1-policy)# authentication pre-share
(config-ikev1-policy)# encryption aes
(config-ikev1-policy)# hash sha
(config-ikev1-policy)# group 2
(config-ikev1-policy)# lifetime 3600And we will enable it on both firewalls:
ASA1 & ASA2
(config)# crypto isakmp identity address
(config)# crypto ikev1 enable OUTSIDENow we have to configure a tunnel-group. This will be different…
Tunnel-Group Static Peer ASA1
Normally we configure an IP address of the remote peer in our tunnel-group. Since the remote peer is using a dynamic IP address, this is no option. One option is to use the “DefaultL2LGroup” tunnel-group for this. This is a built-in tunnel-group and all connections that don’t match another tunnel-group will belong to this group:
ASA1(config)# tunnel-group DefaultL2LGroup ipsec-attributes
ASA1(config-tunnel-ipsec)# ikev1 pre-shared-key MY_SHARED_KEYThe advantage of using the DefaultL2LGroup is that it’s simple to configure. We add a pre-shared key and that’s it. The downside is that you can only configure a single pre-shared key for all dynamic peers. If you have more than one dynamic peer then it’s probably a better idea to create multiple tunnel-groups. This is something I will explain in another lesson.
Tunnel-Group ASA2 Dynamic Peer
On ASA2 we can use a “normal” tunnel-group where we specify our IP address:
ASA2(config)# tunnel-group 10.10.10.1 type ipsec-l2l
ASA2(config)# tunnel-group 10.10.10.1 ipsec-attributes
ASA2(config-tunnel-ipsec)# ikev1 pre-shared-key MY_SHARED_KEYThis completes the phase 1 configuration. Let’s work on phase 2…
Phase 2 configuration
We will start with the transform-set. We can use the same on both ASAs:
ASA1 & ASA2
(config)# crypto ipsec ikev1 transform-set MY_TRANSFORM_SET esp-aes-256 esp-sha-hmacOur next step is to create some access-lists that define what traffic should be encrypted:
ASA1(config)# access-list LAN1_LAN2 extended permit ip 192.168.1.0 255.255.255.0 192.168.2.0 255.255.255.0ASA2(config)# access-list LAN2_LAN1 extended permit ip 192.168.2.0 255.255.255.0 192.168.1.0 255.255.255.0Now we should configure the crypto map. This part will be different.
Crypto Map Static Peer ASA1
Normally we have to specify the remote peer IP address in the crypto map but that’s something we can’t do on ASA1. We have to use a dynamic map:



Hi Rene !
Are you using GNS3 beacuase i have some truoble to get the config saved. After i reopen it doesnt stay.
/Oskar
Hi Oskar,
I use Cisco VIRL for pretty much all labs nowadays, including the ASA labs.
Rene
Thats great Rene .Thx
Hi, Rene
How are you? I have similar topology at work and issue we see is remote end db servers SQL db servers makes call to collect logs from home office SQL db server and sometimes it droops. End to end host connectivity is there as well as IPSEC is all up, VPN is up too. Even I see net flow via LIVE action network analyzer tool.
From home office ASA 5505, I have loggedout /in site to site vpn session which reestablishes with in 30 se . ASDM packet tracer would isolate issue ? I am not sure if that could be something high on CPU or memory to spike ?
... Continue reading in our forumWould Cl
Hi, Rene
Any update on my post above? I am trying to isolate issue that customer server is sending calls to SQL sever at home office and it gets error message on server side at customer end that connections has failed, and call has not completed , 3 call out of 1000 does that however it is important to isolate this issue.