Lesson Contents
In previous lessons, I explained how you can use dynamic NAT or PAT so that your hosts or servers on the inside of your network are able to access the outside world. This is great, but it’s only for outbound traffic or, in “ASA terminology,”…traffic from a higher security level going to a lower security level.
What if an outside host on the Internet wants to reach a server on our inside or DMZ? This is impossible with only dynamic NAT or PAT. When we want to achieve this, we have to do two things:
- Configure static NAT so the internal server is reachable through an outside public IP address.
- Configure an access-list so that the traffic is allowed.
To demonstrate static NAT, I will use the following topology:
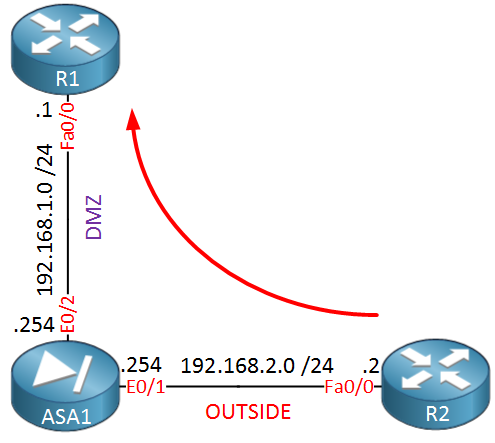 Above we have our ASA firewall with two interfaces: one for the DMZ and another one for the outside world. Imagine that R1 is a web server on the DMZ while R2 is some host on the Internet that wants to reach our web server. Let’s configure our firewall so that this is possible…
Above we have our ASA firewall with two interfaces: one for the DMZ and another one for the outside world. Imagine that R1 is a web server on the DMZ while R2 is some host on the Internet that wants to reach our web server. Let’s configure our firewall so that this is possible…
Static NAT Configuration
First, we will create a network object that defines our “webserver” in the DMZ and also configure to what IP address it should be translated. This configuration is for ASA version 8.3 and later:
ASA1(config)# object network WEB_SERVER
ASA1(config-network-object)# host 192.168.1.1
ASA1(config-network-object)# nat (DMZ,OUTSIDE) static 192.168.2.200The configuration above tells the ASA that whenever an outside device connects to IP address 192.168.2.200, it should be translated to IP address 192.168.1.1. This takes care of NAT, but we still have to create an access-list or traffic will be dropped:
ASA1(config)# access-list OUTSIDE_TO_DMZ extended permit tcp any host 192.168.1.1The access-list above allows any source IP address to connect to IP address 192.168.1.1. When using ASA version 8.3 or later, you need to specify the “real” IP address, not the “NAT translated” address. Let’s activate this access-list:
ASA1(config)# access-group OUTSIDE_TO_DMZ in interface OUTSIDEThis enables the access-list on the outside interface. Let’s telnet from R2 to R1 on TCP port 80 to see if it works:
R2#telnet 192.168.2.200
Trying 192.168.2.200 ... OpenGreat, we can connect from R2 to R1, let’s take a look at the ASA to verify some things:
ASA1# show xlate
1 in use, 1 most used
Flags: D - DNS, e - extended, I - identity, i - dynamic, r - portmap,
s - static, T - twice, N - net-to-net
NAT from DMZ:192.168.1.1 to OUTSIDE:192.168.2.200
flags s idle 0:08:44 timeout 0:00:00ASA1# show access-list
access-list cached ACL log flows: total 0, denied 0 (deny-flow-max 4096)
alert-interval 300
access-list OUTSIDE_TO_DMZ; 1 elements; name hash: 0xe96c1ef3
access-list OUTSIDE_TO_DMZ line 1 extended permit tcp any host 192.168.1.1 eq www (hitcnt=6) 0x408b914eAbove you can see the static NAT entry and also the hit on the access-list. Everything is working as it is supposed to be.
Static NAT for the entire subnet
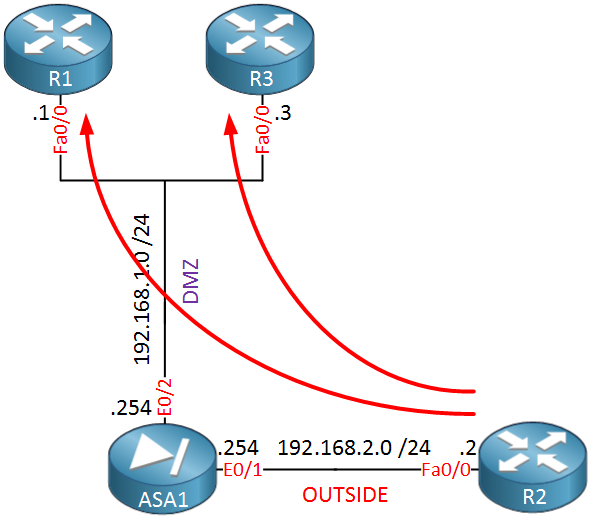
The previous example was fine if you have only a few servers since you can create a couple of static NAT translations and be done with it. There is another option, though, it’s also possible to translate an entire subnet to an entire pool of IP addresses. Let me give you an example of what I’m talking about:
The topology above is the exact same as the previous example, but I have added R3 to the DMZ. Now imagine that our ISP gave us a pool of IP addresses, let’s say 10.10.10.0 /24. We can use this pool to translate all the servers in the DMZ. Let me show you how:



Hi Rene ,
Could you explain twice nat and use cases also ?
Thank you
Hi Sims,
I will, added it to the list.
Rene
Hi Rene,
Need help again, So its NAT this time.
Let’s call this statement A.
The configuration above tells the ASA that whenever an outside device connects to IP address 192.168.2.200
that it should be translated to IP address 192.168.1.1.
Let’s call
... Continue reading in our forumHi Asi,
The first statement tells the ASA that a device with IP address 192.168.1.1 on the DMZ has to be translated to 192.168.2.200 which is on the outside. On the interfaces we configured to which security-zone it belongs (INSIDE, DMZ or OUTSIDE).
The direction doesn’t matter…from the outside you can connect to 192.168.2.200 and it will be translated to 192.168.1.1. When 192.168.1.1 initiates traffic that goes from DMZ > outside then it also gets translated to 192.168.2.200. The only thing the ASA cares about is what to translate.
The same thing applies to th
... Continue reading in our forumhi Rene Thanks for the reply
i got most of it ,Actually my confusion started by reading the following configuration from cisco. For last if you can explain short and simple on waht is REAL_ifc and MAPPED_ifc from the below example this will make it crystal clear
Thanks in Advance
nat (real_ifc,mapped_ifc) dynamic mapped_obj [interface] [dns]
Example:
hostname (config-network-object)# nat (inside,outside) dynamic MAPPED_IPS interface
Configures dynamic NAT for the object IP addresses. See the following guidelines:
***Interfaces —If you do not specify the real
... Continue reading in our forum