Lesson Contents
In this lesson we’ll take a look how to configure remote access IPsec VPN using the Cisco VPN client. This allows remote users to connect to the ASA and access the remote network through an IPsec encrypted tunnel.
The remote user requires the Cisco VPN client software on his/her computer, once the connection is established the user will receive a private IP address from the ASA and has access to the network.
The Cisco VPN client is end-of-life and has been replaced by the Cisco Anyconnect Secure Mobility Client. It’s not supported any more but still widely in use nowadays.
This is the topology that we will use for this example:
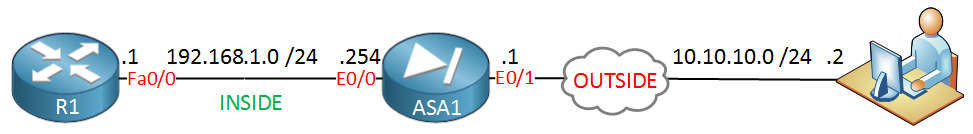
The ASA has two interfaces: inside and outside. Imagine the outside interface is connected to the Internet where a remote user wants to connect to the ASA. On the inside we find R1, I will only use this router so the remote user has something to connect to on the inside network. Let’s look at the configuration!
Configuration
VPN Pool
First we will configure a pool with IP addresses that we will assign to remote VPN users:
ASA1(config)# ip local pool VPN_POOL 192.168.10.100-192.168.10.200I will use IP address 192.168.10.100 – 192.168.10.200 for our VPN users. We need to tell the ASA that we will use this local pool for remote VPN users:
ASA1(config)# vpn-addr-assign localThis is done with the vpn-addr-assign command.
NAT Exemption
If you have NAT enabled on the ASA then we need to make sure that traffic between 192.168.1.0 /24 (the local network) and 192.168.10.0 /24 (our remote VPN users) doesn’t get translated. To accomplish this we will configure NAT excemption. The example below is for ASA version 8.3 or higher:
ASA1(config)# object network LAN
ASA1(config-network-object)# subnet 192.168.1.0 255.255.255.0
ASA1(config)# object network VPN_POOL
ASA1(config-network-object)# subnet 192.168.10.0 255.255.255.0
ASA1(config)# nat (INSIDE,OUTSIDE) source static LAN LAN destination static VPN_POOL VPN_POOLWe create two network objects, one for our local network and another one for the remote VPN users. The NAT rule tells the ASA not to translate traffic between the two networks.
Group Policy
When the remote user has established the VPN, he or she will be unable to access anything on the Internet…only the remote network is reachable. For security reasons this is a good practice as it forces you to send all traffic through the ASA. If you don’t want this then you can enable split tunneling. With split tunneling enabled, we will use the VPN only for access to the remote network. Here’s how to enable it:
ASA1(config)# access-list SPLIT_TUNNEL standard permit 192.168.1.0 255.255.255.0Now we can create a group policy. This allows you to assign different remote users to different groups with different attributes. You might want to have a group policy for “network engineers” and another one for “regular users” each with different DNS servers, timeout settings, etc. Here’s an example:
ASA1(config)# group-policy VPN_POLICY internal
ASA1(config)# group-policy VPN_POLICY attributes
ASA1(config-group-policy)# dns-server value 8.8.8.8
ASA1(config-group-policy)# vpn-idle-timeout 15
ASA1(config-group-policy)# split-tunnel-policy tunnelspecified
ASA1(config-group-policy)# split-tunnel-network-list value SPLIT_TUNNELThe group policy is called VPN_POLICY and it’s an internal group policy which means it is created locally on the ASA. You can also specify an external group policy on a RADIUS server. I added some attributes, for example a DNS server and an idle timeout (15 minutes). Split tunneling is optional but I added it to show you how to use it, it refers to the access-list we created earlier.
If you want to configure an access-list so the remote VPN users can only reach certain networks, IP addresses or ports then you can apply this under the group policy.
Let’s continue and create a user for remote access:
Username
ASA1(config)# username VPN_USER password MY_PASSWORDWe configured a group policy and user but we haven’t configured any IPsec settings yet. Let’s configure phase 1…
IPsec Phase 1
ASA1(config)# crypto ikev1 policy 10
ASA1(config-ikev1-policy)# encryption aes
ASA1(config-ikev1-policy)# hash sha
ASA1(config-ikev1-policy)# authentication pre-share
ASA1(config-ikev1-policy)# group 2
ASA1(config-ikev1-policy)# lifetime 86400This is just a basic example. We will use AES for encryption, SHA for integrity, a pre-shared key and Diffie-Hellman group 2 for key exchange. The lifetime before we have to do a renegotiation is 86400 seconds. Let’s enable this IKEv1 policy on the outside interface:
ASA1(config)# crypto ikev1 enable OUTSIDE
ASA1(config)# crypto isakmp identity addressAnd we can continue with phase 2:
IPsec Phase 2
ASA1(config)# crypto ipsec ikev1 transform-set MY_TRANSFORM_SET esp-aes esp-sha-hmacWe will configure a transform set called “MY_TRANSFORM_SET” and we use ESP with AES/SHA. The next step is to configure a crypto map, this has to be a dynamic crypto map since the remote VPN users probably are behind dynamic IP addresses and we don’t know which ones:



Would , Remote Access VPN work with dynamic ip address within or behind Comcast module ? I tried, it did work.
Hi Max,
What is the comcast module? You can use dynamic IP addresses, it’s no problem.
You can use dynamic IP addresses, it’s no problem.
Rene
Thank
s for you feedbackHi
rene
I need to create the remote access vpn in my ASA but it has already site to site vpn running on it , so if i follow the above steps will that effect the site to site vpn please advice,
Regards
Ahmed
Hi Ahmed,
It’s no problem, just make sure you don’t overwrite your current policies. At the bottom of your crypto map you can add an entry for the remote access VPN:
Rene