Lesson Contents
In a previous lesson, I explained how to configure a site-to-site IPsec VPN between an ASA with a static IP and one with a dynamic IP address. What if you have multiple peers with dynamic IP addresses?
If you want, you can land all these VPN connections on a single tunnel-group, but it might be a better idea to use different tunnel-groups. This allows you to use different pre-shared keys and policies.
In this lesson, you will learn how to configure site-to-site IPsec VPNs with multiple dynamic peers. Here’s the topology we will use:
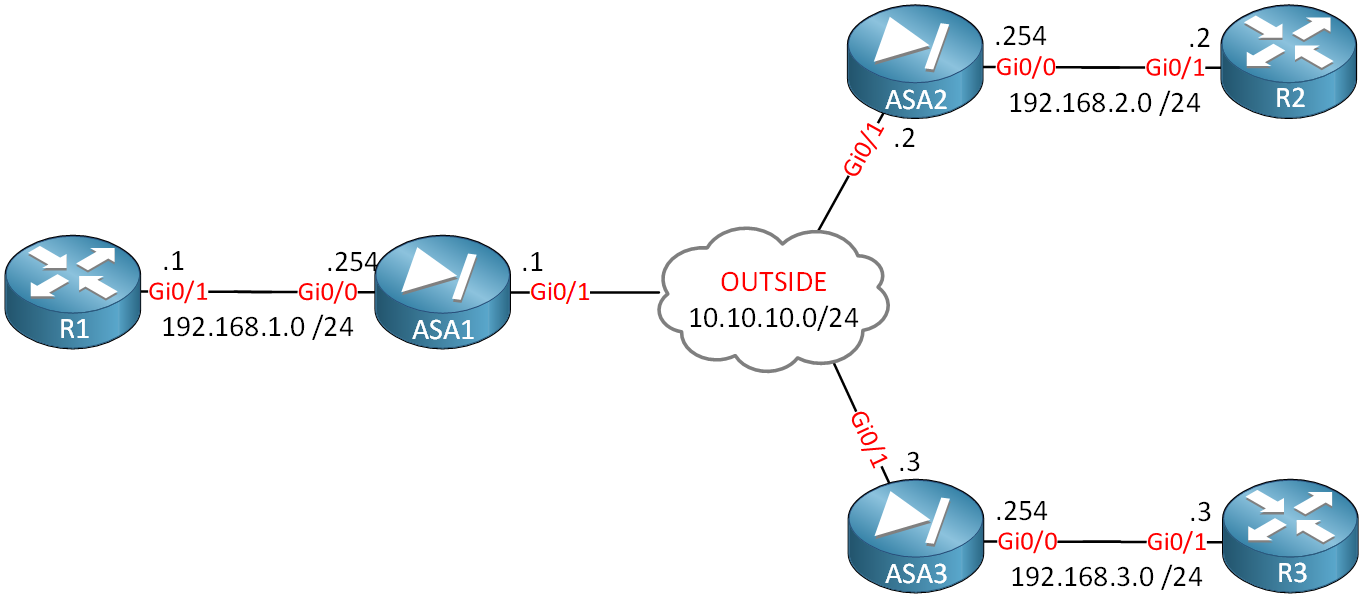
We will configure two VPN tunnels:
- Between ASA1 and ASA2.
- Between ASA1 and ASA3.
ASA1 will use a static IP address, and ASA2/ASA3 have dynamic IP addresses. Let’s look at the configuration…
Configuration
Most of our work will be on ASA1. Let’s start there.
ASA1 – Static IP
First, we have to configure the IKEv1 policy:
ASA1(config)# crypto ikev1 policy 10
ASA1(config-ikev1-policy)# authentication pre-share
ASA1(config-ikev1-policy)# encryption aes-256
ASA1(config-ikev1-policy)# hash sha
ASA1(config-ikev1-policy)# group 2It doesn’t matter what we use here, just make sure it’s the same on all ASAs. Since ASA1 is using a static IP address, we can use its address as the identity:
ASA1(config)# crypto isakmp identity address
ASA1(config)# crypto ikev1 enable OUTSIDEMake sure you enable this policy on the outside interface. Now we can configure the tunnel-groups, one for each ASA:
ASA1(config)# tunnel-group ASA1_ASA2 type ipsec-l2l
ASA1(config)# tunnel-group ASA1_ASA2 ipsec-attributes
ASA1(config-tunnel-ipsec)# ikev1 pre-shared-key ASA1_ASA2_KEYASA1(config)# tunnel-group ASA1_ASA3 type ipsec-l2l
ASA1(config)# tunnel-group ASA1_ASA3 ipsec-attributes
ASA1(config-tunnel-ipsec)# ikev1 pre-shared-key ASA1_ASA3_KEYWe will use a different pre-shared key for each ASA. When you configure the tunnel-groups, you’ll get a warning like this:
WARNING: For IKEv1, L2L tunnel-groups that have names which are not an IP
address may only be used if the tunnel authentication
method is Digital Certificates and/or The peer is
configured to use Aggressive ModeThis is something you need to keep in mind. Since we are using dynamic IP addresses and pre-shared keys on ASA2 and ASA3, we’ll have to use aggressive mode.
Let’s continue; we’ll have to create a transform-set. It doesn’t matter what security parameters we pick as long as it matches with ASA2 and ASA3:
ASA1(config)# crypto ipsec ikev1 transform-set MY_TRANSFORM_SET esp-aes-256 esp-sha-hmacLet’s add two access-lists that define the traffic that we want to encrypt:
ASA1(config)# access-list LAN1_LAN2 extended permit ip 192.168.1.0 255.255.255.0 192.168.2.0 255.255.255.0
ASA1(config)# access-list LAN1_LAN3 extended permit ip 192.168.1.0 255.255.255.0 192.168.3.0 255.255.255.0We can only attach a single crypto map to the outside interface, so when we have multiple dynamic peers, we’ll have to use multiple dynamic maps. Let’s create two, one of each ASA:



Hi Rene,
I can’t understand How ASA1 recognizes dynamically the peer IP address with the command
ASA1(config)# tunnel-group DefaultL2LGroup ipsec-attributesand
Could you please help me to describe how they are working ??
br/
zaman
Hi Zaman,
On ASA2 you will find this line:
ASA2(config)# crypto isakmp identity key-id ASA1_ASA2When ASA2 tries to connect to ASA1, it will use “ASA1_ASA2” to identify itself. This will help ASA1 to decide which tunnel group to pick:
ASA1(config)# tunnel-group ASA1_ASA2 type ipsec-l2lASA1 will accept connections from any IP address.
Rene
Hi Rene,
I have a one question for site to site ipsec vpn. I have two ASA 5525-x firewall and using Active/Standby in production. But I have a one public ip address in WAN interface. I want to use site to site ipsec vpn now. Could I use one public ip address for active/standby design and Is it possible? How to work failover? This design we can get failover when active firewall is down. Is there any recommendation reference?
Thanks
Hi Mark,
Configure the ASAs without the standby IP on the outside interface is no problem. The standby IP is used for management and to monitor the interface (by sending hello packets). If you do specify a standby IP on the inside interfaces then you can use that to access your standby ASA. When your primary ASA fails, it will be notified through the failover link and your standby ASA will take over.
Rene
Hi Rene,
Thanks for your reply.