Lesson Contents
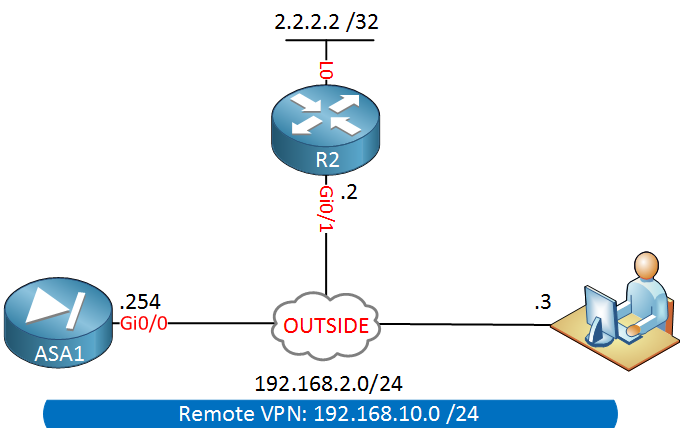
The Cisco ASA firewall doesn’t like traffic that enters and exits the same interface. This behavior is typically known as “hairpin” or “u-turn”. Sometimes however we need our ASA to permit this kind of traffic. Here’s an example:
Above we have an ASA firewall on the left side, there’s a remote VPN uses that connects to our firewall. This remote VPN user is not using split tunneling so all traffic is being tunneled to the ASA. Let’s say this user wants to reach some webserver (2.2.2.2) on the Internet behind R2.
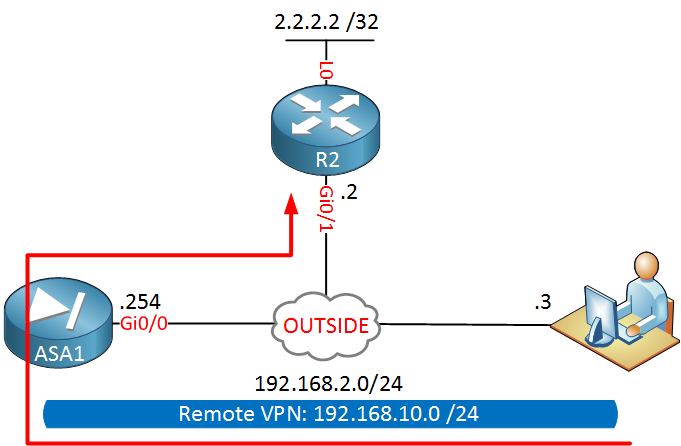
Here’s what our traffic pattern will look like:
Our traffic will enter the ASA on its outside Gigabit 0/0 interface and exits the same interface. By default, the ASA will drop this traffic. The second issue with this setup is that the source IP address will be from the 192.168.10.0/24 subnet. Since this is a private range, R2 will drop the traffic when it has to be routed to the Internet.
Let’s see what we have to do to fix this issue…
Startup Configurations
Want to take a look for yourself? Here you will find the startup configuration of each device.
R2
hostname R2
!
interface Loopback0
ip address 2.2.2.2 255.255.255.255
!
interface GigabitEthernet0/1
ip address 192.168.2.2 255.255.255.0
duplex auto
speed auto
media-type rj45
!
ip http server
!
endASA1
hostname ASA1
!
ip local pool VPN_POOL 192.168.10.100-192.168.10.200
!
interface GigabitEthernet0/0
nameif OUTSIDE
security-level 0
ip address 192.168.2.254 255.255.255.0
!
ftp mode passive
object network VPN_POOL
subnet 192.168.10.0 255.255.255.0
!
route OUTSIDE 0.0.0.0 0.0.0.0 192.168.2.2 1
!
crypto ipsec ikev1 transform-set MY_TRANSFORM_SET esp-aes esp-sha-hmac
crypto ipsec security-association pmtu-aging infinite
crypto dynamic-map MY_DYNA_MAP 10 set ikev1 transform-set MY_TRANSFORM_SET
crypto map MY_CRYPTO_MAP 10 ipsec-isakmp dynamic MY_DYNA_MAP
crypto map MY_CRYPTO_MAP interface OUTSIDE
crypto isakmp identity address
crypto ikev1 enable OUTSIDE
crypto ikev1 policy 10
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
!
group-policy VPN_POLICY internal
group-policy VPN_POLICY attributes
vpn-idle-timeout 15
dynamic-access-policy-record DfltAccessPolicy
username VPN_USER password E5PbZWWQ.j3bJJHz encrypted
tunnel-group MY_TUNNEL type remote-access
tunnel-group MY_TUNNEL general-attributes
address-pool VPN_POOL
default-group-policy VPN_POLICY
tunnel-group MY_TUNNEL ipsec-attributes
ikev1 pre-shared-key *****
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect ip-options
inspect netbios
inspect rtsp
inspect sunrpc
inspect tftp
inspect xdmcp
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect esmtp
inspect sqlnet
inspect sip
inspect skinny
inspect icmp
policy-map type inspect dns migrated_dns_map_1
parameters
message-length maximum client auto
message-length maximum 512
!
service-policy global_policy global
!
: endLet’s take a look at the configuration…
Configuration
There are two things we have to fix here:
- We need to configure the ASA to permit traffic that enters and exits the same interface.
- Traffic from the 192.168.10.0/24 subnet has to be NAT translated.
Before we make any changes, let’s try a ping from our remote VPN user:
C:\Users\H1>ping 2.2.2.2
Pinging 2.2.2.2 with 32 bytes of data:
Request timed out.
Request timed out.
Request timed out.
Request timed out.
Ping statistics for 2.2.2.2:
Packets: Sent = 4, Received = 0, Lost = 4 (100% loss),As expected these pings are failing. Let’s configure the ASA to permit traffic that enters and exits the same interface:
ASA1(config)# same-security-traffic permit intra-interfaceThe command above will allow the traffic to be routed. The second thing to do is to configure a NAT rule:



Hi Rene,
Nice Article . Please carry on .
br/
zaman
Hi Rene,
ASA1(config)# nat (OUTSIDE,OUTSIDE) source dynamic VPN_POOL interfaceI got few doubt about the above statements
[1] Why is the key word SOURCE used in the NAT statement
[2] waht effect it would make if the Dynamic is changed to Static in NAT statment
STATIC is a one to 1 mapping ie public 8.8.8.8 maps to private 10.10.10.1 all the time.
DYNAMIC would be used if you had multiple connections that needed to be NATTed as you can then define a range of IP addresses using an access list and when a NAT translation needed to be made, then it would use a free public IP address from the access list.
Rene,
I was thinking through how to lab up this lesson and was having trouble on the layout for the cloud that labeled outside and the vpn user. I was thinking the cloud was a router with regular ospf passing all traffic and the vpn user… Could you point me in the right direction (configs) on how to lab up this lesson
thank you
Hello Christopher
Yes, actually, you’re on the right track. You can create a router with three interfaces, each on a different subnet. Say something like this:
https://cdn-forum.networklessons.com/uploads/default/original/1X/faa6c2a873f74ae636d9ace51661a2d25e161669.jpg
In this case, all of the 10.10.X.X address space can be considered “the Internet.”
You can use OSPF if you like to convey routing information to all routers involved, or you could use static routing if you like as well. Just keep in mind that both the ASA and R2 must be informed of each other’
... Continue reading in our forum