Lesson Contents
The Cisco ASA firewall is often an important device in the network. We use it for (remote access) VPNs, NAT/PAT, filtering and more. Since it’s such an important device it’s a good idea to have a second ASA in case the first one fails.
The ASA supports active/standby failover which means one ASA becomes the active device, it handles everything while the backup ASA is the standby device. It doesn’t do anything unless the active ASA fails.
The failover mechanism is stateful which means that the active ASA sends all stateful connection information state to the standby ASA. This includes TCP/UDP states, NAT translation tables, ARP table, VPN information and more.
When the active ASA fails, the standby ASA will take over and since it has all connection information, your users won’t notice anything…
There are a number of requirements if you want to use failover:
- Platform has to be the same: for example 2x ASA 5510 or 2x ASA 5520.
- Hardware must be the same: same number and type of interfaces. Flash memory and RAM has to be the same.
- Same operating mode: routed or transparent mode and single or multiple context mode.
- License has to be the same..number of VPN peers, encryption supported, etc.
- Correct license. Some of the “lower” models require the Security Plus license for failover (the ASA 5510 is an example).
In this lesson we’ll take a look how to configure active/standby failover. Here’s the topology I will use:
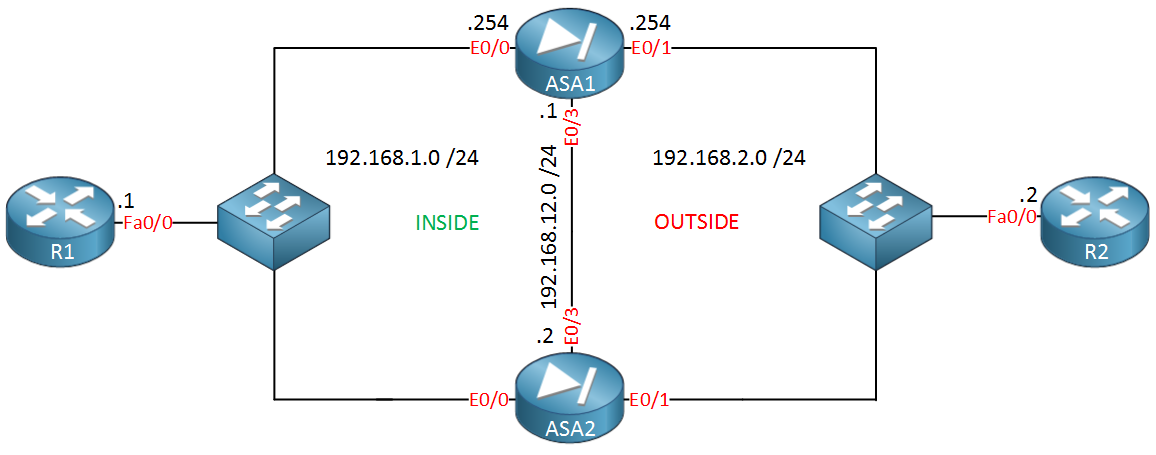
We have two ASA firewalls…ASA1 and ASA2. ASA1 will be the active firewall and ASA2 will be in standby mode. Their Ethernet 0/0 interfaces are connected to the “INSIDE” security zone while the Ethernet 0/1 interfaces are connected to the “OUTSIDE” security zone. The Ethernet 0/3 interface in the middle will be used to synchronize connection information for failover. R1 and R2 are only used so we can generate some traffic.
Configuration
We will start with the failover interface on ASA1. Make sure it’s not shut:
ASA1(config)# interface Ethernet 0/3
ASA1(config-if)# no shutdownAnd then we configure this ASA to be the active (primary) device:
ASA1(config)# failover lan unit primaryNow we will configure Ethernet 0/3 to be the failover interface:



Hi
Why do I need to assign a standby IP to inside and outside interfaces ? And will the secondary ASA copy all of the running config from the primary ASA once fail over is enabled ? as on my secondary ASA i have different interface configuration due to me having stacked switches ?
Hi Aaron,
You can make failover work without the standby IP address, the only issue is that you will be unable to monitor the interface of the second ASA.
The standby ASA will synchronize its configuration with the active ASA and it won’t do anything until your active ASA fails.
Rene
hi
When i configure the primary asa to monitor inside interface the secondry asa says failed
when I un monitor the inside interface it shows as standby state
any ideas ??
Hi Aaron,
Are there any differences between the two ASAs? Model, interfaces, image?
Rene
hi
no both the exact same models ,the error only comes when I configure the active asa to monitor the inside and outside interfaces
as soon as I remove the command the asa assume active / stand by roles with no issues