Lesson Contents
NAT exemption allows you to exclude traffic from being translated with NAT. One scenario where you usually need this is when you have a site-to-site VPN tunnel.
In this lesson, I’ll walk you through a scenario and explain what happens with and without NAT exemption.
Configuration
We’ll use the following topology:
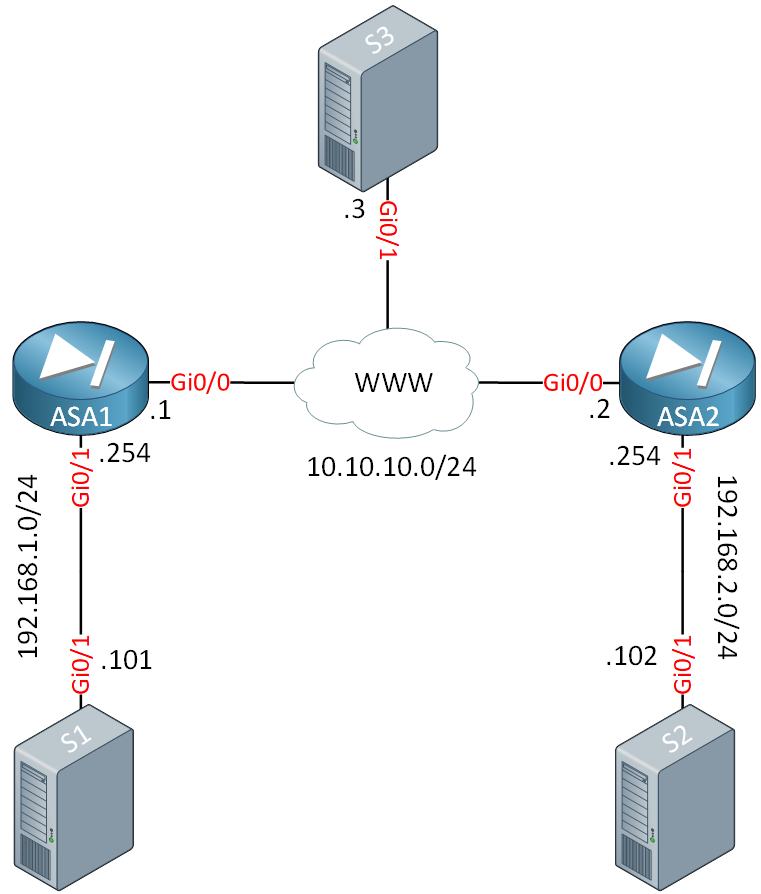
Let me explain what we have above:
- S1 and S2 are servers on internal networks.
- S3 is a server on the Internet.
- ASA1 and ASA2 use NAT to translate traffic from S1 and S2 to the IP address on their GigabitEthernet 0/0 interfaces.
- We use an IPSec IKEv2 VPN tunnel between ASA1 and ASA2 for traffic between S1 and S2.
- HTTP server runs on S1, S2, and S3, so that we have something to connect to.
I use ASAv 9.9(2) for this example.
Configurations
Want to take a look for yourself? Here you will find the startup configuration of each device.
ASA1
hostname ASA1
!
interface GigabitEthernet0/0
nameif OUTSIDE
security-level 0
ip address 10.10.10.1 255.255.255.0
!
interface GigabitEthernet0/1
nameif INSIDE
security-level 100
ip address 192.168.1.254 255.255.255.0ASA2
hostname ASA2
!
interface GigabitEthernet0/0
nameif OUTSIDE
security-level 0
ip address 10.10.10.2 255.255.255.0
!
interface GigabitEthernet0/1
nameif INSIDE
security-level 100
ip address 192.168.2.254 255.255.255.0S1
hostname S1
!
no ip routing
!
no ip cef
!
interface GigabitEthernet0/1
ip address 192.168.1.101 255.255.255.0
!
ip default-gateway 192.168.1.254
!
ip http server
!
endS2
hostname S2
!
no ip routing
!
no ip cef
!
interface GigabitEthernet0/1
ip address 192.168.2.102 255.255.255.0
!
ip default-gateway 192.168.2.254
!
ip http server
!
endS3
hostname S3
!
ip cef
!
interface GigabitEthernet0/1
ip address 10.10.10.3 255.255.255.0
!
ip http server
!
endPAT
Let’s start with the PAT configuration, explained in detail in the Cisco ASA PAT configuration lesson.
We translate all traffic from the subnets where the hosts reside to the outside interface of the ASAs:
ASA1(config)# object network INSIDE
ASA1(config-network-object)# subnet 192.168.1.0 255.255.255.0
ASA1(config-network-object)# nat (INSIDE,OUTSIDE) dynamic interface ASA2(config)# object network INSIDE
ASA2(config-network-object)# subnet 192.168.2.0 255.255.255.0
ASA2(config-network-object)# nat (INSIDE,OUTSIDE) dynamic interfaceThis completes our PAT configuration.
IPSec Site-to-Site VPN
Let’s configure a VPN tunnel between ASA1 and ASA2, as explained in detail in the ASA site-to-site IKEv2 IPSec VPN lesson.
We configure an IKEv2 policy on both ASAs:
ASA1 & ASA2#
(config)# crypto ikev2 policy 10
ASA1(config-ikev2-policy)# encryption aes
ASA1(config-ikev2-policy)# group 2
ASA1(config-ikev2-policy)# prf sha
ASA1(config-ikev2-policy)# lifetime seconds 86400And an IPSec proposal:
ASA1 & ASA2#
(config)# crypto ipsec ikev2 ipsec-proposal MY_PROPOSAL
(config-ipsec-proposal)# protocol esp encryption aes
(config-ipsec-proposal)# protocol esp integrity sha-1We need an access-list to define the traffic we want to encrypt. In this example, we’ll encrypt all traffic between the 192.168.1.0/24 and 192.168.2.0/24 subnets:
ASA1(config)# access-list LAN1_LAN2 extended permit ip 192.168.1.0 255.255.255.0 192.168.2.0 255.255.255.0ASA2(config)# access-list LAN2_LAN1 extended permit ip 192.168.2.0 255.255.255.0 192.168.1.0 255.255.255.0We need a crypto map to set the remote peer IP address, to combine the access-list with the proposal, and activate it on the outside interface:
ASA1(config)# crypto map MY_CRYPTO_MAP 1 match address LAN1_LAN2
ASA1(config)# crypto map MY_CRYPTO_MAP 1 set peer 10.10.10.2
ASA1(config)# crypto map MY_CRYPTO_MAP 1 set ikev2 ipsec-proposal MY_PROPOSAL
ASA1(config)# crypto map MY_CRYPTO_MAP interface OUTSIDEASA2(config)# crypto map MY_CRYPTO_MAP 1 match address LAN2_LAN1
ASA2(config)# crypto map MY_CRYPTO_MAP 1 set peer 10.10.10.1
ASA2(config)# crypto map MY_CRYPTO_MAP 1 set ikev2 ipsec-proposal MY_PROPOSAL
ASA2(config)# crypto map MY_CRYPTO_MAP interface OUTSIDEWe configure the tunnel-group to configure pre-shared keys:
ASA1(config)# tunnel-group 10.10.10.2 type ipsec-l2l
ASA1(config)# tunnel-group 10.10.10.2 ipsec-attributes
ASA1(config-tunnel-ipsec)# ikev2 local-authentication pre-shared-key CISCO123
ASA1(config-tunnel-ipsec)# ikev2 remote-authentication pre-shared-key CISCO456ASA2(config)# tunnel-group 10.10.10.1 type ipsec-l2l
ASA2(config)# tunnel-group 10.10.10.1 ipsec-attributes
ASA2(config-tunnel-ipsec)# ikev2 local-authentication pre-shared-key CISCO456
ASA2(config-tunnel-ipsec)# ikev2 remote-authentication pre-shared-key CISCO123Enable IKEv2 on the outside interface:
ASA1 & ASA2
(config)# crypto ikev2 enable OUTSIDEAnd last but not least, make sure each ASA has a route to the subnet on the other side:
ASA1(config)# route OUTSIDE 192.168.2.0 255.255.255.0 10.10.10.2ASA2(config)# route OUTSIDE 192.168.1.0 255.255.255.0 10.10.10.1This completes our VPN configuration.
NAT Exemption
We now have a working configuration where we use PAT to translate traffic from our hosts and a site-to-site IPSec IKEv2 VPN tunnel.
Without NAT Exemption
Let’s see what happens without NAT exemption. Let’s try what happens when we connect from S1 to S3:
S1#telnet 10.10.10.3 80
Trying 10.10.10.3, 80 ... OpenWe can connect. No issues there. Let’s check our PAT translation:
ASA1# show xlate
1 in use, 2 most used
Flags: D - DNS, e - extended, I - identity, i - dynamic, r - portmap,
s - static, T - twice, N - net-to-net
TCP PAT from INSIDE:192.168.1.101/51796 to OUTSIDE:10.10.10.1/51796 flags ri idle 0:00:39 timeout 0:00:30Above, we see that traffic from 192.168.1.101 is translated to 10.10.10.1. Let’s try something else. I’ll clear the NAT table first:
ASA1# clear xlate
INFO: 1 xlate deletedLet’s see what happens when we try to connect from S1 to S2:
S1#telnet 192.168.2.102 80
Trying 192.168.2.102, 80 ...
% Connection timed out; remote host not respondingThis isn’t working. There are no IKEv2 security associations:
ASA1# show crypto isakmp sa
There are no IKEv1 SAs
There are no IKEv2 SAsWhat is going on? Assuming our VPN configuration is correct, something else must be going on. Let’s take a look at the NAT table:
ASA1# show xlate
1 in use, 2 most used
Flags: D - DNS, e - extended, I - identity, i - dynamic, r - portmap,
s - static, T - twice, N - net-to-net
TCP PAT from INSIDE:192.168.1.101/63774 to OUTSIDE:10.10.10.1/63774 flags ri idle 0:00:03 timeout 0:00:30The output above tells us something. Traffic from S1 is translated to 10.10.10.1.
The ASA’s order of operation is that it first translates a packet with NAT, then checks if the packet should be encrypted or not. This packet doesn’t match our LAN1_LAN2 access-list, so it won’t be encrypted.
ASA2 drops the packet because no access-list permits traffic from the outside to the inside.
With NAT Exemption
To fix this, we need to make an exception so that traffic between 192.168.1.101 and 192.168.2.102 won’t be translated with NAT. We can do this with NAT exemption.



Hello Patrice
Because the two ASAs and the S3 server are on the same subnet in the topology, you can simply use a switch to represent the cloud. The prerequisite is that connectivity is achievable between those devices.
I hope this has been helpful!
Laz
Hi Rene and staff,
i lab this lesson in GNS3 like this
https://cdn-forum.networklessons.com/uploads/default/original/2X/f/f8d5f174a6ef4074edf5c8508c24fe025fe29d67.png
S1,S2, S3 are build with GNS3 appliance Networkers’s toolkit
https://cdn-forum.networklessons.com/uploads/default/original/2X/0/0ebdbd494d8f369cd937ed83123f4ca7f5309660.png
Guest-webterm is a linux GUI client with firefox, build with the GNS3 appliance Webterm
My lab works fine, but i want to add these comments and questions
... Continue reading in our forum1)
i prefer to name the internal subnet object as “INTERNAL” rather than
For your NAT, you’re saying this.
NAT the following:
NAT (INTERNAL IP) and change to (INTERNAL IP) in this case do not change it!
NAT (LAN2) and change to (LAN2) in this case do not change it!
NAT on ASA are broken the down like this every time.
Original Source IP:
Translated Source IP:
Destination IP:
Translated Destination IP:
If both source/destination stay the same, we are exempting them from all NAT statements, especially our PAT statement for internet traffic so they match our crypto ACL for a tunnel. This is called a NAT exemption for this reason.
You ne
... Continue reading in our forumHello Dominique
What’s happening here is something called “twice NAT” and is used to identify both the source and destination address in a single rule. As stated in this Cisco documentation:
... Continue reading in our forumHello Laz,
I’ve tried this same config but the exemption only works on my topology when the NAT exemption statement is above the NAT statement for internet connection.
Basically this 3 order of statement works for me:
1st for DMZ to OUTSIDE statement (DMZ to INTERNET)
2nd for INSIDE to OUTSIDE exemption statement
3rd for INSIDE to OUTSIDE dynamic statement (INTERNAL TO INTERNET)
but when I swapped the 2nd and 3rd, the traffic coming from behind of the ASA will go through 2nd statement, not to the 3rd which is for the exemption.