Lesson Contents
Your government has asked you to help design its vision of govNet, a large private network that will be used to interconnect all of the region’s public sector services. Schools, hospitals, universities, museums, government offices, and various other types of public buildings and services will be connected to this network. govNet will essentially function as the ISP for these public sector institutions. The network will provide Internet connectivity, telephony, and various other network services required for the public sector to operate.
govNet will be separated into several geographically defined administrative areas, each served by a BGP Autonomous System (AS). The whole network will connect to the Internet via a Tier 1 ISP.
Your job is to set up and configure all of the main BGP routers to fulfill the needs of the network. Your work will include:
- Basic BGP configuration of routers including eBGP peerings and iBGP peerings as shown in the topology diagram.
- Manipulation of various BGP attributes to achieve the required advertising of particular networks.
- The implementation of BGP communities to implement traffic engineering and dynamic routing policies.
- Additional advanced BGP configurations including confederations, route filtering, peer groups, and multipath among others, to achieve the required network behavior and capabilities.
- In preparation for migration to IPv6, you will introduce some IPv6 routes to be advertised by the BGP topology.
Your expertise will play a key role in advancing govNet to become one of the most sophisticated government networks in the world. This is your chance to demonstrate your potential and contribute to building a network that is not only scalable and reliable but also instrumental in achieving the regional government’s ambitious goals.
This lab will give you tasks to configure, and it’s up to you to figure out how to accomplish them. This helps you learn how to apply your theoretical knowledge to real-world scenarios. It’s created to be challenging and deepen your understanding of BGP.
The lab also assumes you know what BGP is and how it operates. When you go through the lab and get stuck, you can follow the links to the different lessons in the solution section. You will get maximum value out of this when you try to solve everything on your own and only refer to the solution when you get stuck.
Topology
Here is the topology for this lab:
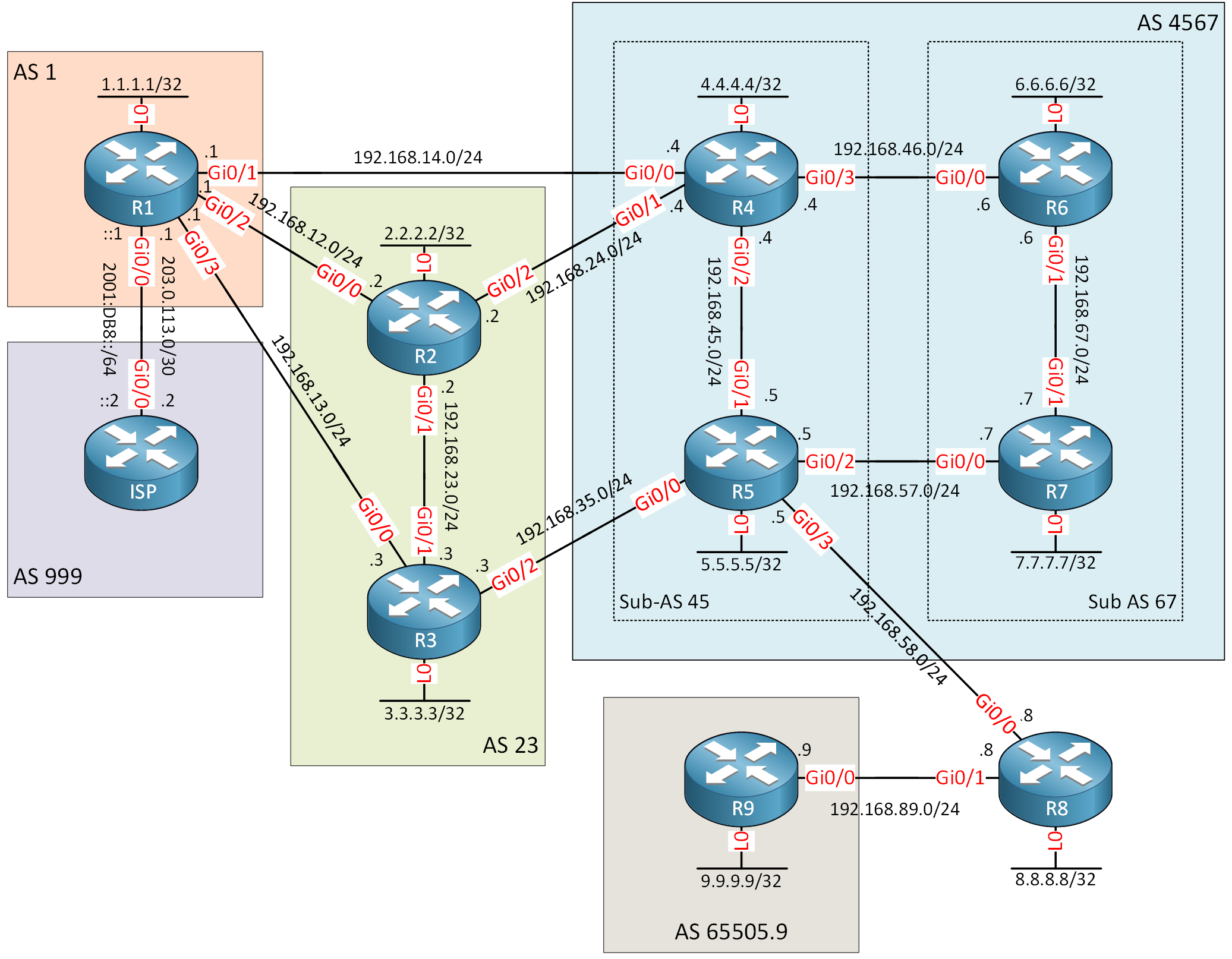
Let me explain this topology:
- Nine routers belong to govNet.
- govNet uses these AS numbers:
- AS 1
- AS 23
- AS 4567
- This is a confederation that contains sub-ASes 45 and 67.
- AS 65505.9
- The ISP router belongs to the Tier 1 ISP.
- The ISP router contains several public networks in its BGP table.
- All routers except for R8 participate in BGP.
- AS 999 belongs to the Tier 1 ISP.
The following startup configs include the configuration of all hostnames, interfaces, IPv4 addresses, and IPv6 addresses. You can load these on your own hardware or your favorite emulator.
Configurations
Want to take a look for yourself? Here, you will find the startup configuration of each device.
ISP
hostname ISP
!
ip cef
ipv6 unicast-routing
ipv6 cef
!
interface Loopback0
ip address 10.0.0.1 255.255.255.255
ipv6 address 2001:DB8:1::1/128
!
interface Loopback1
ip address 12.34.0.1 255.255.0.0
ipv6 address 2001:DB8:12:34::1/64
!
interface Loopback2
ip address 23.45.0.1 255.255.0.0
ipv6 address 2001:DB8:23:45::1/64
!
interface Loopback3
ip address 66.77.0.1 255.255.128.0
ipv6 address 2001:DB8:66:77::1/64
!
interface Loopback4
ip address 89.100.0.1 255.255.192.0
ipv6 address 2001:DB8:89:100::1/64
!
interface Loopback5
ip address 91.200.0.1 255.255.192.0
ipv6 address 2001:DB8:91:200::1/64
!
interface Loopback6
ip address 102.64.0.1 255.255.192.0
ipv6 address 2001:DB8:102:64::1/64
!
interface Loopback7
ip address 123.45.0.1 255.255.128.0
ipv6 address 2001:DB8:123:45::1/64
!
interface Loopback8
ip address 130.25.0.1 255.255.192.0
ipv6 address 2001:DB8:130:25::1/64
!
interface Loopback9
ip address 175.45.200.1 255.255.248.0
ipv6 address 2001:DB8:175:45::1/64
!
interface Loopback10
ip address 183.77.220.1 255.255.252.0
ipv6 address 2001:DB8:183:77::1/64
!
interface Loopback11
ip address 185.100.0.1 255.255.224.0
ipv6 address 2001:DB8:185:100::1/64
!
interface Loopback12
ip address 190.30.128.1 255.255.128.0
ipv6 address 2001:DB8:190:32::1/64
!
interface Loopback13
ip address 195.225.0.1 255.255.224.0
ipv6 address 2001:DB8:195:225::1/64
!
interface Loopback14
ip address 199.10.192.1 255.255.252.0
ipv6 address 2001:DB8:199:10::1/64
!
interface Loopback15
ip address 210.45.128.1 255.255.254.0
ipv6 address 2001:DB8:210:45::1/64
!
interface Loopback16
ip address 212.12.16.1 255.255.248.0
ipv6 address 2001:DB8:212:12::1/64
!
interface Loopback17
ip address 216.80.192.1 255.255.252.0
ipv6 address 2001:DB8:216:80::1/64
!
interface Loopback18
ip address 220.85.200.1 255.255.254.0
ipv6 address 2001:DB8:220:85::1/64
!
interface Loopback19
ip address 221.25.0.1 255.255.224.0
ipv6 address 2001:DB8:225:25::1/64
!
interface GigabitEthernet0/0
ip address 203.0.113.2 255.255.255.252
ipv6 address 2001:DB8::2/64
!
endR1
hostname R1
!
ip cef
ipv6 unicast-routing
ipv6 cef
!
interface Loopback0
ip address 1.1.1.1 255.255.255.255
!
interface GigabitEthernet0/0
ip address 203.0.113.1 255.255.255.252
ipv6 address 2001:DB8::1/64
!
interface GigabitEthernet0/1
ip address 192.168.14.1 255.255.255.0
!
interface GigabitEthernet0/2
ip address 192.168.12.1 255.255.255.0
!
interface GigabitEthernet0/3
ip address 192.168.13.1 255.255.255.0
!
endR2
hostname R2
!
ip cef
ipv6 unicast-routing
ipv6 cef
!
interface Loopback0
ip address 2.2.2.2 255.255.255.255
!
interface GigabitEthernet0/0
ip address 192.168.12.2 255.255.255.0
!
interface GigabitEthernet0/1
ip address 192.168.23.2 255.255.255.0
!
interface GigabitEthernet0/2
ip address 192.168.24.2 255.255.255.0
!
endR3
hostname R3
!
ip cef
ipv6 unicast-routing
ipv6 cef
!
interface Loopback0
ip address 3.3.3.3 255.255.255.255
!
interface GigabitEthernet0/0
ip address 192.168.13.3 255.255.255.0
!
interface GigabitEthernet0/1
ip address 192.168.23.3 255.255.255.0
!
interface GigabitEthernet0/2
ip address 192.168.35.3 255.255.255.0
!
endR4
hostname R4
!
ip cef
!
interface Loopback0
ip address 4.4.4.4 255.255.255.255
!
interface GigabitEthernet0/0
ip address 192.168.14.4 255.255.255.0
!
interface GigabitEthernet0/1
ip address 192.168.24.4 255.255.255.0
!
interface GigabitEthernet0/2
ip address 192.168.45.4 255.255.255.0
!
interface GigabitEthernet0/3
ip address 192.168.46.4 255.255.255.0
!
endR5
hostname R5
!
ip cef
!
interface Loopback0
ip address 5.5.5.5 255.255.255.255
!
interface GigabitEthernet0/0
ip address 192.168.35.5 255.255.255.0
!
interface GigabitEthernet0/1
ip address 192.168.45.5 255.255.255.0
!
interface GigabitEthernet0/2
ip address 192.168.57.5 255.255.255.0
!
interface GigabitEthernet0/3
ip address 192.168.58.5 255.255.255.0
!
endR6
hostname R6
!
ip cef
!
interface Loopback0
ip address 6.6.6.6 255.255.255.255
!
interface GigabitEthernet0/0
ip address 192.168.46.6 255.255.255.0
!
interface GigabitEthernet0/1
ip address 192.168.67.6 255.255.255.0
!
endR7
hostname R7
!
ip cef
!
interface Loopback0
ip address 7.7.7.7 255.255.255.255
!
interface GigabitEthernet0/0
ip address 192.168.57.7 255.255.255.0
!
interface GigabitEthernet0/1
ip address 192.168.67.7 255.255.255.0
!
endR8
hostname R8
!
ip cef
!
interface Loopback0
ip address 8.8.8.8 255.255.255.255
!
interface GigabitEthernet0/0
ip address 192.168.58.8 255.255.255.0
!
interface GigabitEthernet0/1
ip address 192.168.89.8 255.255.255.0
!
endR9
hostname R9
!
ip cef
!
interface Loopback0
ip address 9.9.9.9 255.255.255.255
!
interface GigabitEthernet0/0
ip address 192.168.89.9 255.255.255.0
!
endTasks
The tasks are described as if you are on the job, and someone asks you to configure this network. It’s not a cookbook where we tell you exactly what to do and in what order. You will have to decide for yourself. This will help you think through what is needed instead of just typing the commands we tell you to.
OSPF
We require an IGP such as OSPF for the iBGP peerings.
- Configure OSPF in ASes 23 and 4567 to prepare for the iBGP peerings.
Tunnel
R8 doesn’t have an AS number yet, but R5 and R9 must establish a BGP neighbor adjacency. It’s up to you to come up with a solution.
- Configure a tunnel solution so that R5 and R9 can establish a neighbor adjacency using their loopback interfaces.
- You are not allowed to make any changes to R8 except for two static routes.
- You are allowed to create two static routes on R5 and R9.
BGP Fundamentals
This section describes the fundamental BGP configurations that must be implemented.
Create iBGP and eBGP IPv4 peerings
Next, you will create the BGP peerings as shown in the network topology:
- Configure iBGP peerings with loopback interfaces. Do not use physical interfaces.
- Configure eBGP peerings with physical interfaces, with one exception.
Here is an overview of all required BGP peerings:
- eBGP peering between R1 and the ISP router.
- eBGP peering between R1 and R2.
- eBGP peering between R1 and R3.
- eBGP peering between R1 and R4.
- iBGP peering between R2 and R3.
- eBGP peering between R2 and R4.
- eBGP peering between R3 and R5.
- Peerings between routers in the confederation AS 4567 and their sub ASes.
- eBGP multi-hop peering between R5 and R9:
- Use loopback interfaces as the source for eBGP.
- Ensure that the 4-byte AS number is correctly interpreted by R5 and the rest of the BGP topology.
Create eBGP IPv6 peering
govNet wants to prepare for IPv6, luckily the ISP supports this.
- Configure a second eBGP peering between the ISP and R1 router using IPv6.
- Advertise the IPv6 networks on the ISP router in BGP.
- Use the IPv6 addresses on the physical interface for the BGP peering.
Advertise Routes
Next, you will ensure that routes are advertised within the BGP topology like so:
- Advertise the directly connected IPv4 networks on the ISP router using redistribution.
- Advertise the IPv4 network of Loopback 0 on the ISP router into BGP using the
networkcommand. - Advertise the IPv6 prefixes on loopbacks 0 to 19 on the ISP router into BGP via the IPv6 peering using the
networkcommand. - Configure AS23 to receive IPv6 routes over the IPv4 eBGP peerings with R1.
- Configure the network so that IPv6 routes are propagated into AS 1 and AS 23 but not beyond.
- Advertise the IPv4 address on the loopback interfaces of all BGP routers into BGP using the
networkcommand.
Next-Hop Self
- Configure next hop self for IPv4 BGP peerings on all routers that require this so that traffic can be routed outside of the local AS.
Advanced BGP Features
The next step is to configure some more advanced BGP features.
BGP Auto Summary
The R9 router is expected to contain multiple networks in the future that will be advertised to the rest of the network. These networks will fall within the 9.0.0.0/8 address range.
- Configure auto-summary on R9 to make BGP routing more efficient in the future.
BGP Summarization
The ISP router advertises several networks, which can be summarized. To make BGP tables smaller, you must summarize some of the ISP’s networks:
- Summarize the networks on loopback 10,11 and 12 using the most specific summary address.
- Ensure that only the summary network is added to the BGP table. Other networks that fall within the range of the summary have to be suppressed.
BGP Weight Attribute
You are asked to ensure that the 12.34.0.0/16 be routed from R4 via AS 23 rather than directly via AS 1. To achieve this, you must use the weight attribute.
- Configure the weight attribute of the route with a route map configuration on R4.
BGP Local Preference Attribute
AS 23 is expected to grow in size in the coming months, and additional iBGP routers will be added in the future. We want to make sure traffic is routed in an optimal way.
- Configure BGP so that packets destined for network 23.45.0.0/16 from within AS 23 always exit AS 23 via router R2.
- Ensure no other networks are influenced.
BGP AS Path Prepending
You are asked to ensure that any traffic from R1 that is destined to the loopback address of R9 be routed via AS 23 rather than via AS 4567.
- Configure AS path prepending on R4 and make the path via AS 4567 three times as long as the path via AS 23.
- Ensure no other networks are influenced.
BGP Origin Code Attribute
Because the 66.77.0.0/17 network advertised by the ISP router may also be advertised elsewhere in the network, you have been asked to modify the way it is injected into BGP.
- Configure the ISP router so that other routers see network 66.77.0.0/17 with an origin code similar to a network that is not injected with redistribution.
- Ensure no other networks are influenced.
BGP MED Attribute
In a previous task, you configured AS path prepending so that traffic from R1 to R9’s loopback would be routed via AS 23. There are two paths via AS 23 to reach that destination.
- Configure MED on R3 so that the path via R2 is preferred over the path via R3.
- Ensure that no other networks are influenced.
BGP Prefer eBGP over iBGP
Take a look at the 91.200.0.0/18 route, as it has been advertised by BGP to R3. Examine the various entries in the routing table. There should be three.
- Determine which of those possible BGP paths has been chosen as the best path and verify the reason for this using the appropriate verification commands.
BGP Communities
You are asked to adjust how various advertised routes are distributed throughout the network using BGP communities. Specifically, you are asked to use the appropriate BGP community to:
- Prevent the 102.64.0.0/18 network from being advertised further downstream by R2, R3, and R4. This configuration has to be applied to R1.
- Ensure that the 123.45.0.0/17 network is advertised from R1 to ASes 23 and 4567 so that the eBGP peers will not readvertise this route to other eBGP peers.
- Ensure that the 130.25.0.0/18 network is advertised into sub-AS 45 but not into sub-AS 67 or beyond.
BGP Route Filtering
You are asked to filter out some routes in the BGP topology. Specifically, you are asked to:
- Filter out all networks with a /18 prefix length:
- These routes should not appear in the BGP table of R9.
- All configurations should be applied using prefix lists configured on R5.
- Filter out any routes with a prefix length ranging between /22 and /32:
- These routes should not appear in the BGP table of R9.
- All configurations should be applied using BGP extended access list filtering prefix lists configured on R9.
BGP Transit AS
You are asked to ensure that AS 23 will never be used as a transit AS for the 175.45.200.0/21 network.
- Use distribute list filtering with an access list to achieve this.
BGP AS Path Filter
Employ AS Path Filtering to perform the following:
- Ensure that any routes that pass through AS 23 are filtered and thus are prevented from entering the BGP table of R6 using AS path filtering.
- Configure AS path filtering on R3 to remove any routers that have passed through AS 4567 but keep any routes that have originated from AS 4567.
BGP Route Dampening
To prevent many changes to the BGP tables, you must implement route dampening.
- Enable route dampening on R2 for the networks on loopback 13, 14, and 15 of the ISP route.
- Use the following parameters:
- Half-life: 15
- Reuse: 750
- Suppress: 2000
- Max-suppress-time: 60
BGP Peer Groups
R1 will connect to more routers in AS 23 in the future.
- Configure peer groups on R1 and group as many of R1’s neighbors into peer groups as possible.
BGP Soft Reconfiguration and Route Refresh
- Configure routers R6 and R7 such that their inter-sub-AS peerings are enabled with soft reconfiguration in an inbound direction.
BGP Multipath
The 192.168.23.0/24 network between routers R2 and R3 must be advertised via BGP by both R2 and R3. This network is expected to be expanded in the near future, as more devices will be connected to it. The services running on that subnet must be accessible from the R1 router with redundant routing via both R2 and R3.
- Configure BGP multipath so that both paths (via R2 and R3) from R1 will be chosen as the best path.
- No more than two paths should be chosen as the best paths.
- Any other paths found in the BGP table of R1 that appear multiple times and have the same Weight, Local Preference, AS Path, Origin code, MED and IGP metric should also be routed redundantly using BGP.
BGP Next-Hop Tracking
- Configure BGP next hop tracking on R2 so that the next hop IP addresses of R2 and R3 are actively tracked.
- Modify the next hop trigger delay to 10 seconds for the IPv4 address family.
Solution
The lab was configured using the following router image for all devices:
Cisco IOS Software, IOSv Software (VIOS-ADVENTERPRISEK9-M), Version 15.9(3)M6, RELEASE SOFTWARE (fc1).The following sections show how to achieve the requirements as described in the tasks section above.
OSPF
The iBGP routers in AS 23 and AS 4567 use loopback interfaces for the neighbor adjacency so we need an IGP such as OSPF to advertise these loopback interfaces. This is how to do it:
R2(config)#router ospf 1
R2(config-router)#network 2.2.2.2 0.0.0.0 area 0
R2(config-router)#network 192.168.23.0 0.0.0.255 area 0R3(config)#router ospf 1
R3(config-router)#network 3.3.3.3 0.0.0.0 area 0
R3(config-router)#network 192.168.23.0 0.0.0.255 area 0R4(config)#router ospf 1
R4(config-router)#network 4.4.4.4 0.0.0.0 area 0
R4(config-router)#network 192.168.45.0 0.0.0.255 area 0
R4(config-router)#network 192.168.46.0 0.0.0.255 area 0R5(config)#router ospf 1
R5(config-router)#network 5.5.5.5 0.0.0.0 area 0
R5(config-router)#network 192.168.45.0 0.0.0.255 area 0
R5(config-router)#network 192.168.57.0 0.0.0.255 area 0R6(config)#router ospf 1
R6(config-router)#network 6.6.6.6 0.0.0.0 area 0
R6(config-router)#network 192.168.46.0 0.0.0.255 area 0
R6(config-router)#network 192.168.67.0 0.0.0.255 area 0R7(config)#router ospf 1
R7(config-router)#network 7.7.7.7 0.0.0.0 area 0
R7(config-router)#network 192.168.57.0 0.0.0.255 area 0
R7(config-router)#network 192.168.67.0 0.0.0.255 area 0This takes care of all required OSPF neighbor adjacencies and advertises the loopback interfaces:
R2#show ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface
3.3.3.3 1 FULL/DR 00:00:31 192.168.23.3 GigabitEthernet0/1R3#show ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface
2.2.2.2 1 FULL/BDR 00:00:39 192.168.23.2 GigabitEthernet0/1R4#show ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface
6.6.6.6 1 FULL/DR 00:00:35 192.168.46.6 GigabitEthernet0/3
5.5.5.5 1 FULL/DR 00:00:38 192.168.45.5 GigabitEthernet0/2R5#show ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface
7.7.7.7 1 FULL/DR 00:00:32 192.168.57.7 GigabitEthernet0/2
4.4.4.4 1 FULL/BDR 00:00:39 192.168.45.4 GigabitEthernet0/1R6#show ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface
7.7.7.7 1 FULL/DR 00:00:34 192.168.67.7 GigabitEthernet0/1
4.4.4.4 1 FULL/BDR 00:00:35 192.168.46.4 GigabitEthernet0/0R7#show ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface
6.6.6.6 1 FULL/BDR 00:00:34 192.168.67.6 GigabitEthernet0/1
5.5.5.5 1 FULL/BDR 00:00:36 192.168.57.5 GigabitEthernet0/0Tunnel
We can create a GRE tunnel between R5 and R9 so they can establish a neighbor adjacency. Without a tunnel, R8 would drop traffic because it doesn’t run BGP.
First, create two static routes so R5 and R9 know how to reach each others tunnel endpoints:
R5(config)#ip route 192.168.89.9 255.255.255.255 192.168.58.8R9(config-if)#ip route 192.168.58.5 255.255.255.255 192.168.89.8Now we can configure the tunnel interfaces:
R5(config)#interface Tunnel 0
R5(config-if)#tunnel source 192.168.58.5
R5(config-if)#tunnel destination 192.168.89.9
R5(config-if)#ip address 192.168.59.5 255.255.255.0R9(config)#interface Tunnel 0
R9(config-if)#tunnel source 192.168.89.9
R9(config-if)#tunnel destination 192.168.58.5
R9(config-if)#ip address 192.168.59.9 255.255.255.0The tunnel now works:
R5#show interfaces Tunnel 0 | include up
Tunnel0 is up, line protocol is up
Tunnel linestate evaluation upLet’s make sure the tunnel works:
R5#ping 192.168.59.9
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.59.9, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2/2/3 msThe last thing to do is to create two more static routes so that R5 and R9 can reach each other’s loopback interfaces through the tunnel:
R5(config)#ip route 9.9.9.9 255.255.255.255 192.168.59.9R9(config)#ip route 5.5.5.5 255.255.255.255 192.168.59.5Let’s send a quick ping:
R5#ping 9.9.9.9 source 5.5.5.5
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 9.9.9.9, timeout is 2 seconds:
Packet sent with a source address of 5.5.5.5
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2/2/3 msThe tunnel is now ready, and R5 and R9 can reach each other’s loopback interfaces through the tunnel. We can use this later for the BGP neighbor adjacency.
BGP Fundamentals
The following sections describe the solution to the requirements for the fundamental BGP configurations.
Create iBGP and eBGP IPv4 peerings
To fulfill the stated requirements for the configuration of eBGP and eBGP IPv4 peerings, perform the following configurations:
iBGP Peerings in AS 23
For the establishment of iBGP peerings in AS 23, use the Loopback 0 interfaces as the source of BGP messages.
R2(config)#router bgp 23
R2(config-router)#neighbor 3.3.3.3 remote-as 23
R2(config-router)#neighbor 3.3.3.3 update-source Loopback0R3(config)#router bgp 23
R3(config-router)#neighbor 2.2.2.2 remote-as 23
R3(config-router)#neighbor 2.2.2.2 update-source Loopback0To verify that the iBGP peerings have been established, issue the following command on each BGP peer:
R2#show ip bgp summary
BGP router identifier 2.2.2.2, local AS number 23
BGP table version is 1, main routing table version 1
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
3.3.3.3 4 23 6 6 1 0 0 00:02:00 0R3#show ip bgp summary
BGP router identifier 3.3.3.3, local AS number 23
BGP table version is 1, main routing table version 1
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
2.2.2.2 4 23 5 5 1 0 0 00:01:29 0Notice the AS 23 that appears as the AS of the remote peer in both cases. This indicates that the AS is the same as the one in the local router, which ensures that these are iBGP peerings.
iBGP peerings within the Confederation AS 4567
To create a confederation in AS 4567 as described in the task requirements, perform the following configuration steps. Remember to use the Loopback 0 interfaces as the source of BGP messages:
R4(config)#router bgp 45
R4(config-router)#bgp confederation identifier 4567
R4(config-router)#bgp confederation peers 67
R4(config-router)#neighbor 5.5.5.5 remote-as 45
R4(config-router)#neighbor 5.5.5.5 update-source Loopback0
R4(config-router)#neighbor 6.6.6.6 remote-as 67
R4(config-router)#neighbor 6.6.6.6 update-source Loopback0
R4(config-router)#neighbor 6.6.6.6 ebgp-multihop 2R5(config)#router bgp 45
R5(config-router)#bgp confederation identifier 4567
R5(config-router)#bgp confederation peers 67
R5(config-router)#neighbor 4.4.4.4 remote-as 45
R5(config-router)#neighbor 4.4.4.4 update-source Loopback0
R5(config-router)#neighbor 7.7.7.7 remote-as 67
R5(config-router)#neighbor 7.7.7.7 update-source Loopback0
R5(config-router)#neighbor 7.7.7.7 ebgp-multihop 2R6(config)#router bgp 67
R6(config-router)#bgp confederation identifier 4567
R6(config-router)#bgp confederation peers 45
R6(config-router)#neighbor 7.7.7.7 remote-as 67
R6(config-router)#neighbor 7.7.7.7 update-source Loopback0
R6(config-router)#neighbor 4.4.4.4 remote-as 45
R6(config-router)#neighbor 4.4.4.4 update-source Loopback0
R6(config-router)#neighbor 4.4.4.4 ebgp-multihop 2R7(config)#router bgp 67
R7(config-router)#bgp confederation identifier 4567
R7(config-router)#bgp confederation peers 45
R7(config-router)#neighbor 6.6.6.6 remote-as 67
R7(config-router)#neighbor 6.6.6.6 update-source Loopback0
R7(config-router)#neighbor 5.5.5.5 remote-as 45
R7(config-router)#neighbor 5.5.5.5 update-source Loopback0
R7(config-router)#neighbor 5.5.5.5 ebgp-multihop 2The above configurations have now created AS 4567 as a confederation:
-
-
- Sub-AS 45 with R4 and R5.
- Sub-AS 67 with R6 and R7.
-
To verify this, use the following command on each of the routers to determine the BGP peerings:
R4#show ip bgp summary
BGP router identifier 4.4.4.4, local AS number 45
BGP table version is 1, main routing table version 1
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
5.5.5.5 4 45 96 96 1 0 0 01:24:42 0
6.6.6.6 4 67 33 33 1 0 0 00:26:30 0R5#show ip bgp summary
BGP router identifier 5.5.5.5, local AS number 45
BGP table version is 1, main routing table version 1
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
4.4.4.4 4 45 101 101 1 0 0 01:29:05 0
7.7.7.7 4 67 31 32 1 0 0 00:25:30 0Notice the ASes that appear for each neighbor are those of the sub-ASes and not of the confederation AS. Similarly, you can see the results of these commands on routers R6 and R7:
R6#show ip bgp summary
BGP router identifier 6.6.6.6, local AS number 67
BGP table version is 1, main routing table version 1
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
4.4.4.4 4 45 41 40 1 0 0 00:32:52 0
7.7.7.7 4 67 34 35 1 0 0 00:28:09 0R7#show ip bgp summary
BGP router identifier 7.7.7.7, local AS number 67
BGP table version is 1, main routing table version 1
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
5.5.5.5 4 45 35 34 1 0 0 00:27:55 0
6.6.6.6 4 67 35 35 1 0 0 00:28:36 0eBGP Peerings
For the establishment of eBGP peerings, as with the iBGP peerings, use the Loopback 0 interfaces as the source of BGP messages. This means you need to configure eBGP Multihop to make this work.
There are two eBGP peerings that require a closer look:
- R5 and R9 where R9 uses a 4-byte ASN and is two hops away.
- R4 and R5 are within the BGP confederation.
Here is the configuration:
ISP(config)#router bgp 999
ISP(config-router)#neighbor 203.0.113.1 remote-as 1R1(config)#router bgp 1
R1(config-router)#neighbor 203.0.113.2 remote-as 999
R1(config-router)#neighbor 192.168.12.2 remote-as 23
R1(config-router)#neighbor 192.168.13.3 remote-as 23
R1(config-router)#neighbor 192.168.14.4 remote-as 4567R2(config)#router bgp 23
R2(config-router)#neighbor 192.168.12.1 remote-as 1
R2(config-router)#neighbor 192.168.24.4 remote-as 4567R3(config)#router bgp 23
R3(config-router)#neighbor 192.168.13.1 remote-as 1
R3(config-router)#neighbor 192.168.35.5 remote-as 4567R4(config)#router bgp 45
R4(config-router)#neighbor 192.168.14.1 remote-as 1
R4(config-router)#neighbor 192.168.24.2 remote-as 23R5(config)#router bgp 45
R5(config-router)#neighbor 192.168.35.3 remote-as 23
R5(config-router)#neighbor 9.9.9.9 remote-as 65505.9
R5(config-router)#neighbor 9.9.9.9 update-source Loopback0
R5(config-router)#neighbor 9.9.9.9 ebgp-multihop 2R9(config)#router bgp 65505.9
R9(config-router)#neighbor 5.5.5.5 remote-as 4567
R9(config-router)#neighbor 5.5.5.5 update-source Loopback0
R9(config-router)#neighbor 5.5.5.5 ebgp-multihop 2At this point, all eBGP peerings should be established. To verify this, use the following command on each eBGP peer:
ISP#show ip bgp summary
BGP router identifier 221.25.0.1, local AS number 999
BGP table version is 1, main routing table version 1
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
203.0.113.1 4 1 43 43 1 0 0 00:36:02 0Ensure that the neighbor Up/Down state has a time value that indicates that the peering is up. This should be done from both sides of the peering:
R1#show ip bgp summary
BGP router identifier 1.1.1.1, local AS number 1
BGP table version is 1, main routing table version 1
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
192.168.12.2 4 23 32 30 1 0 0 00:25:53 0
192.168.13.3 4 23 27 25 1 0 0 00:21:45 0
192.168.14.4 4 4567 23 20 1 0 0 00:17:20 0
203.0.113.2 4 999 46 46 1 0 0 00:38:30 0Ensure that all expected eBGP peerings are up, including the peerings within the confederation AS of 4567 as well as between R5 and R9 which are not directly connected:
R4#show ip bgp summary
BGP router identifier 4.4.4.4, local AS number 45
BGP table version is 1, main routing table version 1
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
192.168.14.1 4 1 69 72 1 0 0 01:01:42 0
192.168.24.2 4 23 70 70 1 0 0 01:01:10 0
5.5.5.5 4 45 179 178 1 0 0 02:39:21 0
6.6.6.6 4 67 115 116 1 0 0 01:41:10 0R6#show ip bgp summary
BGP router identifier 6.6.6.6, local AS number 67
BGP table version is 1, main routing table version 1
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
4.4.4.4 4 45 118 117 1 0 0 01:42:44 0
7.7.7.7 4 67 111 111 1 0 0 01:38:01 0R7#show ip bgp summary
BGP router identifier 7.7.7.7, local AS number 67
BGP table version is 1, main routing table version 1
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
5.5.5.5 4 45 111 112 1 0 0 01:37:46 0
6.6.6.6 4 67 111 112 1 0 0 01:38:27 0R5#show ip bgp summary
BGP router identifier 5.5.5.5, local AS number 45
BGP table version is 1, main routing table version 1
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
4.4.4.4 4 45 6329 6334 1 0 0 00:21:47 0
7.7.7.7 4 67 6269 6271 1 0 0 00:18:18 0
9.9.9.9 4 4292935689 6169 6174 1 0 0 00:12:19 0
192.168.35.3 4 23 16 16 1 0 0 00:13:45 0R9#show ip bgp summary
BGP router identifier 9.9.9.9, local AS number 4292935689
BGP table version is 1, main routing table version 1
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
5.5.5.5 4 4567 22 23 1 0 0 00:17:51 0At this point, all iBGP and eBGP peerings have been established, including within the BGP confederation 4567 and the multihop peering between R5 and R9.
It’s important to note that at this moment, no routes have yet been exchanged by BGP. Only OSPF and static routes within each AS have been established such that BGP routers can reach their intended peers.
Create eBGP IPv6 peering
To create an IPv6 eBGP peering between the ISP and R1 routers, perform the following configurations:
ISP(config)#ipv6 unicast-routingR1(config)#ipv6 unicast-routingISP(config)#router bgp 999
ISP(config-router)#neighbor 2001:db8::1 remote-as 1
ISP(config-router)#address-family ipv4
ISP(config-router-af)#no neighbor 2001:db8::1 activate
ISP(config-router-af)#exit
ISP(config-router)#address-family ipv6
ISP(config-router-af)#neighbor 2001:db8::1 activateR1(config)#router bgp 1
R1(config-router)#neighbor 2001:db8::2 remote-as 999
R1(config-router)#address-family ipv4
R1(config-router-af)#no neighbor 2001:db8::2 activate
R1(config-router-af)#exit
R1(config-router)#address-family ipv6
R1(config-router-af)#neighbor 2001:db8::2 activateTo verify this IPv6 eBGP peering, use the following command on both routers:
ISP#show bgp ipv6 unicast summary
BGP router identifier 221.25.0.1, local AS number 999
BGP table version is 1, main routing table version 1
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
2001:DB8::1 4 1 3150 3146 1 0 0 00:15:55 0R1#show bgp ipv6 unicast summary
BGP router identifier 1.1.1.1, local AS number 1
BGP table version is 1, main routing table version 1
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
2001:DB8::2 4 999 3147 3151 1 0 0 00:14:31 0It may be a good idea at this point to ensure that the IPv4 eBGP peering is still up an running, using the same verification commands as described in the previous section.
Advertise Routes in BGP
The following sections show how to fulfill the requirements as described in the task list.
IPv4 prefixes on ISP Router
To advertise the IPv4 address spaces on the loopback interfaces of the ISP router as described in the task list, perform the following configurations.
ISP(config)#router bgp 999
ISP(config-router)#address-family ipv4
ISP(config-router-af)#redistribute connected
ISP(config-router-af)#network 10.0.0.1 mask 255.255.255.255To verify that these addresses are being advertised via eBGP, issue the following command:
R1#show ip bgp
BGP table version is 23, local router ID is 1.1.1.1
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
*> 10.0.0.1/32 203.0.113.2 0 0 999 i
*> 12.34.0.0/16 203.0.113.2 0 0 999 ?
*> 23.45.0.0/16 203.0.113.2 0 0 999 ?
*> 66.77.0.0/17 203.0.113.2 0 0 999 ?
*> 89.100.0.0/18 203.0.113.2 0 0 999 ?
*> 91.200.0.0/18 203.0.113.2 0 0 999 ?
*> 102.64.0.0/18 203.0.113.2 0 0 999 ?
*> 123.45.0.0/17 203.0.113.2 0 0 999 ?
*> 130.25.0.0/18 203.0.113.2 0 0 999 ?
*> 175.45.200.0/21 203.0.113.2 0 0 999 ?
*> 183.77.220.0/22 203.0.113.2 0 0 999 ?
*> 185.100.0.0/19 203.0.113.2 0 0 999 ?
*> 190.30.128.0/17 203.0.113.2 0 0 999 ?
*> 195.225.0.0/19 203.0.113.2 0 0 999 ?
*> 199.10.192.0/22 203.0.113.2 0 0 999 ?
r> 203.0.113.0/30 203.0.113.2 0 0 999 ?
*> 210.45.128.0/23 203.0.113.2 0 0 999 ?
*> 212.12.16.0/21 203.0.113.2 0 0 999 ?
*> 216.80.192.0/22 203.0.113.2 0 0 999 ?
*> 220.85.200.0/23 203.0.113.2 0 0 999 ?
*> 221.25.0.0/19 203.0.113.2 0 0 999 ?Ensure that all routes have been learned via the redistribution of routes (within an origin code of “?”) except for the network of Loopback0 of the ISP router (origin code of “i”). Also, note that the 203.0.113.0/30 network was learned via BGP, but it wasn’t installed into the routing table (status code “r”). This is because R1 has a directly connected interface to that network, via which the network was added to the routing table. This directly connected route has a lower AD than eBGP.
Perform the same command on the ISP router to view the results there as well.
IPv6 prefixes on ISP Router
To advertise IPv6 addresses on the ISP router and fulfill the requirements of this task, perform the following configurations:
ISP(config)#router bgp 999
ISP(config-router)#address-family ipv6
ISP(config-router-af)#network 2001:0db8:23:45::/64
ISP(config-router-af)#network 2001:0db8:66:77::/64
ISP(config-router-af)#network 2001:0db8:89:100::/64
ISP(config-router-af)#network 2001:0db8:91:200::/64
ISP(config-router-af)#network 2001:0db8:102:64::/64
ISP(config-router-af)#network 2001:0db8:123:45::/64
ISP(config-router-af)#network 2001:0db8:130:25::/64
ISP(config-router-af)#network 2001:0db8:175:45::/64
ISP(config-router-af)#network 2001:0db8:183:77::/64
ISP(config-router-af)#network 2001:0db8:185:100::/64
ISP(config-router-af)#network 2001:0db8:190:32::/64
ISP(config-router-af)#network 2001:0db8:195:225::/64
ISP(config-router-af)#network 2001:0db8:199:10::/64
ISP(config-router-af)#network 2001:0db8:210:45::/64
ISP(config-router-af)#network 2001:0db8:212:12::/64
ISP(config-router-af)#network 2001:0db8:216:80::/64
ISP(config-router-af)#network 2001:0db8:220:85::/64
ISP(config-router-af)#network 2001:0db8:225:25::/64To verify that these networks are being advertised to R1 via the IPv6 eBGP peering, issue the following command:
R1#show bgp ipv6 unicast
BGP table version is 21, local router ID is 1.1.1.1
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
*> 2001:DB8:1::1/128
2001:DB8::2 0 0 999 i
*> 2001:DB8:12:34::/64
2001:DB8::2 0 0 999 i
*> 2001:DB8:23:45::/64
2001:DB8::2 0 0 999 i
*> 2001:DB8:66:77::/64
2001:DB8::2 0 0 999 i
*> 2001:DB8:89:100::/64
2001:DB8::2 0 0 999 i
*> 2001:DB8:91:200::/64
2001:DB8::2 0 0 999 i
*> 2001:DB8:102:64::/64
2001:DB8::2 0 0 999 i
*> 2001:DB8:123:45::/64
2001:DB8::2 0 0 999 i
*> 2001:DB8:130:25::/64
2001:DB8::2 0 0 999 i
*> 2001:DB8:175:45::/64
2001:DB8::2 0 0 999 i
*> 2001:DB8:183:77::/64
2001:DB8::2 0 0 999 i
*> 2001:DB8:185:100::/64
2001:DB8::2 0 0 999 i
*> 2001:DB8:190:32::/64
2001:DB8::2 0 0 999 i
*> 2001:DB8:195:225::/64
2001:DB8::2 0 0 999 i
*> 2001:DB8:199:10::/64
2001:DB8::2 0 0 999 i
*> 2001:DB8:210:45::/64
2001:DB8::2 0 0 999 i
*> 2001:DB8:212:12::/64
2001:DB8::2 0 0 999 i
*> 2001:DB8:216:80::/64
2001:DB8::2 0 0 999 i
*> 2001:DB8:220:85::/64
2001:DB8::2 0 0 999 i
*> 2001:DB8:225:25::/64
2001:DB8::2 0 0 999 iNotice that all learned routes have an origin code of “i” which indicates that they were added using the network command. Also note that the next hop router is indicated by an IPv6 address, which means that the routes have been learned via the IPv6 eBGP peering with the ISP router.
Issue this same command on the ISP router to see similar results.
IPv6 prefixes into AS 23
To prepare AS 23 to receive IPv6 routes via IPv4 eBGP peerings with R1, perform the following configurations:
R1(config)#router bgp 1
R1(config-router)#address-family ipv6
R1(config-router-af)#neighbor 192.168.12.2 activate
R1(config-router-af)#neighbor 192.168.13.3 activateR2(config)#ipv6 unicast-routing
R2(config)#router bgp 23
R2(config-router)#address-family ipv6
R2(config-router-af)#neighbor 192.168.12.1 activate
R2(config-router-af)#neighbor 3.3.3.3 activateR3(config)#ipv6 unicast-routing
R3(config)#router bgp 23
R3(config-router)#address-family ipv6
R3(config-router-af)#neighbor 192.168.13.1 activate
R3(config-router-af)#neighbor 2.2.2.2 activateTo verify that the IPv4 eBGP and iBGP peerings have been enabled to share IPv6 routes within AS 23, issue the following commands:
R2#show bgp ipv6 unicast summary
BGP router identifier 2.2.2.2, local AS number 23
BGP table version is 1, main routing table version 1
20 network entries using 3360 bytes of memory
20 path entries using 2160 bytes of memory
1/0 BGP path/bestpath attribute entries using 160 bytes of memory
4 BGP AS-PATH entries using 96 bytes of memory
0 BGP route-map cache entries using 0 bytes of memory
0 BGP filter-list cache entries using 0 bytes of memory
BGP using 5776 total bytes of memory
BGP activity 42/0 prefixes, 218/132 paths, scan interval 60 secs
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
3.3.3.3 4 23 14 14 1 0 0 00:05:23 0
192.168.12.1 4 1 37 38 1 0 0 00:23:21 20R3#show bgp ipv6 unicast summary
BGP router identifier 3.3.3.3, local AS number 23
BGP table version is 1, main routing table version 1
20 network entries using 3360 bytes of memory
20 path entries using 2160 bytes of memory
1/0 BGP path/bestpath attribute entries using 160 bytes of memory
2 BGP AS-PATH entries using 48 bytes of memory
0 BGP route-map cache entries using 0 bytes of memory
0 BGP filter-list cache entries using 0 bytes of memory
BGP using 5728 total bytes of memory
BGP activity 42/0 prefixes, 152/88 paths, scan interval 60 secs
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
2.2.2.2 4 23 14 14 1 0 0 00:05:51 0
192.168.13.1 4 1 25 22 1 0 0 00:11:40 20R1#show bgp ipv6 unicast summary
BGP router identifier 1.1.1.1, local AS number 1
BGP table version is 21, main routing table version 21
20 network entries using 3360 bytes of memory
20 path entries using 2160 bytes of memory
1/1 BGP path/bestpath attribute entries using 160 bytes of memory
1 BGP AS-PATH entries using 24 bytes of memory
0 BGP route-map cache entries using 0 bytes of memory
0 BGP filter-list cache entries using 0 bytes of memory
BGP using 5704 total bytes of memory
BGP activity 42/0 prefixes, 42/0 paths, scan interval 60 secs
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
2001:DB8::2 4 999 3423 3422 21 0 0 2d03h 20
192.168.12.2 4 23 40 40 21 0 0 00:25:23 0
192.168.13.3 4 23 23 26 21 0 0 00:13:14 0Note that the entries with an IPv4 address in the neighbor column indicate that IPv6 routes are being shared across an IPv4 BGP peering.
To view the routes that have been advertised via BGP into AS 23, issue the following command:
R2#show bgp ipv6 unicast
BGP table version is 1, local router ID is 2.2.2.2
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
* 2001:DB8:1::1/128
::FFFF:192.168.12.1
0 1 999 i
* 2001:DB8:12:34::/64
::FFFF:192.168.12.1
0 1 999 i
* 2001:DB8:23:45::/64
::FFFF:192.168.12.1
0 1 999 i
* 2001:DB8:66:77::/64
::FFFF:192.168.12.1
0 1 999 i
* 2001:DB8:89:100::/64
::FFFF:192.168.12.1
0 1 999 i
* 2001:DB8:91:200::/64
::FFFF:192.168.12.1
0 1 999 i
* 2001:DB8:102:64::/64
::FFFF:192.168.12.1
0 1 999 i
* 2001:DB8:123:45::/64
::FFFF:192.168.12.1
0 1 999 i
* 2001:DB8:130:25::/64
::FFFF:192.168.12.1
0 1 999 i
* 2001:DB8:175:45::/64
::FFFF:192.168.12.1
0 1 999 i
* 2001:DB8:183:77::/64
::FFFF:192.168.12.1
0 1 999 i
* 2001:DB8:185:100::/64
::FFFF:192.168.12.1
0 1 999 i
* 2001:DB8:190:32::/64
::FFFF:192.168.12.1
0 1 999 i
* 2001:DB8:195:225::/64
::FFFF:192.168.12.1
0 1 999 i
* 2001:DB8:199:10::/64
::FFFF:192.168.12.1
0 1 999 i
* 2001:DB8:210:45::/64
::FFFF:192.168.12.1
0 1 999 i
* 2001:DB8:212:12::/64
::FFFF:192.168.12.1
0 1 999 i
* 2001:DB8:216:80::/64
::FFFF:192.168.12.1
0 1 999 i
* 2001:DB8:220:85::/64
::FFFF:192.168.12.1
0 1 999 i
* 2001:DB8:225:25::/64
::FFFF:192.168.12.1
0 1 999 iNotice that all IPv6 routes are valid routes, but none have been selected as the best path, nor have they been entered into the routing table. This is because there is no reachable next hop IP. The next hop IP address that appears in the BGP table is FFFF:192.168.12.1. This is a placeholder used to indicate that IPv4 is being used to propagate the IPv6 routes. To route IPv6 traffic, we will need to implement an IPv6 network within AS 23, which is outside the scope of this lab.
Loopback IPv4 prefixes on all BGP routers
To advertise the IPv4 addresses of the loopback interfaces of the rest of the BGP peers in the network as described in the task list, perform the following configurations:
R1(config)#router bgp 1
R1(config-router)#address-family ipv4
R1(config-router-af)#network 1.1.1.1 mask 255.255.255.255R2(config)#router bgp 23
R2(config-router)#network 2.2.2.2 mask 255.255.255.255R3(config)#router bgp 23
R3(config-router)#network 3.3.3.3 mask 255.255.255.255R4(config)#router bgp 45
R4(config-router)#network 4.4.4.4 mask 255.255.255.255R5(config)#router bgp 45
R5(config-router)#network 5.5.5.5 mask 255.255.255.255R6(config)#router bgp 67
R6(config-router)#network 6.6.6.6 mask 255.255.255.255R7(config)#router bgp 67
R7(config-router)#network 7.7.7.7 mask 255.255.255.255R9(config)#router bgp 65505.9
R9(config-router)#network 9.9.9.9 mask 255.255.255.255To verify that these networks are being advertised throughout the network, issue the following command on various BGP routers:
R9#show ip bgp
BGP table version is 119, local router ID is 9.9.9.9
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
*> 1.1.1.1/32 5.5.5.5 0 4567 23 1 i
*> 2.2.2.2/32 5.5.5.5 0 4567 23 i
*> 3.3.3.3/32 5.5.5.5 0 4567 23 i
*> 4.4.4.4/32 5.5.5.5 0 4567 i
r> 5.5.5.5/32 5.5.5.5 0 0 4567 i
*> 6.6.6.6/32 5.5.5.5 0 4567 i
*> 7.7.7.7/32 5.5.5.5 0 4567 i
*> 9.9.9.9/32 0.0.0.0 0 32768 i
*> 10.0.0.1/32 5.5.5.5 0 4567 23 1 999 i
! >-- output omitted --<R6#show ip bgp
BGP table version is 5, local router ID is 6.6.6.6
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
* 1.1.1.1/32 192.168.14.1 0 100 0 (45) 1 i
* 2.2.2.2/32 192.168.24.2 0 100 0 (45) 23 i
* 3.3.3.3/32 192.168.24.2 0 100 0 (45) 23 i
r i 4.4.4.4/32 4.4.4.4 0 100 0 (45) i
r> 4.4.4.4 0 100 0 (45) i
r i 5.5.5.5/32 5.5.5.5 0 100 0 (45) i
r> 5.5.5.5 0 100 0 (45) i
*> 6.6.6.6/32 0.0.0.0 0 32768 i
r>i 7.7.7.7/32 7.7.7.7 0 100 0 i
* 10.0.0.1/32 192.168.14.1 0 100 0 (45) 1 999 i
! >-- output omitted --<R3#show ip bgp
BGP table version is 120, local router ID is 3.3.3.3
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
* i 1.1.1.1/32 192.168.12.1 0 100 0 1 i
*> 192.168.13.1 0 0 1 i
r>i 2.2.2.2/32 2.2.2.2 0 100 0 i
*> 3.3.3.3/32 0.0.0.0 0 32768 i
* 4.4.4.4/32 192.168.13.1 0 1 4567 i
*> 192.168.35.5 0 4567 i
* i 192.168.24.4 0 100 0 4567 i
* i 5.5.5.5/32 192.168.24.4 0 100 0 4567 i
* 192.168.13.1 0 1 4567 i
*> 192.168.35.5 0 0 4567 i
*> 6.6.6.6/32 192.168.35.5 0 4567 i
* i 192.168.24.4 0 100 0 4567 i
* 192.168.13.1 0 1 4567 i
* 7.7.7.7/32 192.168.13.1 0 1 4567 i
* i 192.168.24.4 0 100 0 4567 i
*> 192.168.35.5 0 4567 i
*> 9.9.9.9/32 192.168.35.5 0 4567 4292935689 i
* i 10.0.0.1/32 192.168.12.1 0 100 0 1 999 i
! >-- output omitted --<Examine all of the above output and see if you can decipher the reasons behind the various indicators for these particular routes in the BGP table of each router.
Next-Hop-Self
To apply the next hop self feature within ASes 23 and 4567 so that the next hop IP for BGP routes is correct, issue the following commands:
R2(config)#router bgp 23
R2(config-router)#address-family ipv4
R2(config-router-af)#neighbor 3.3.3.3 next-hop-selfR3(config)#router bgp 23
R3(config-router)#address-family ipv4
R3(config-router-af)#neighbor 2.2.2.2 next-hop-self R4(config)#router bgp 45
R4(config-router)#neighbor 5.5.5.5 next-hop-self
R4(config-router)#neighbor 6.6.6.6 next-hop-self R5(config)#router bgp 45
R5(config-router)#neighbor 4.4.4.4 next-hop-self
R5(config-router)#neighbor 7.7.7.7 next-hop-self To verify that the next hop self feature has been successfully configured, issue the following commands:
R2#show ip bgp 1.1.1.1
BGP routing table entry for 1.1.1.1/32, version 162
Paths: (3 available, best #1, table default)
Advertised to update-groups:
7 8
Refresh Epoch 2
1
192.168.12.1 from 192.168.12.1 (1.1.1.1)
Origin IGP, metric 0, localpref 100, valid, external, best
rx pathid: 0, tx pathid: 0x0
Refresh Epoch 1
1
3.3.3.3 (metric 2) from 3.3.3.3 (3.3.3.3)
Origin IGP, metric 0, localpref 100, valid, internal
rx pathid: 0, tx pathid: 0
Refresh Epoch 3
4567 1
192.168.24.4 from 192.168.24.4 (4.4.4.4)
Origin IGP, localpref 100, valid, external
rx pathid: 0, tx pathid: 0Note that although the best route to the 1.1.1.1 network from R2 remains via a next hop of 192.168.12.1 (which is via the R1 router), the alternate path learned from its iBGP neighbor R3 has a next hop of 3.3.3.3. This means that R3 placed its own IP address as the next hop IP address for that route when it advertised it to R2.
R6#show ip bgp
BGP table version is 132, local router ID is 6.6.6.6
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
* i 1.1.1.1/32 5.5.5.5 0 100 0 (45) 1 i
*> 4.4.4.4 0 100 0 (45) 1 i
* i 2.2.2.2/32 5.5.5.5 0 100 0 (45) 23 i
*> 4.4.4.4 0 100 0 (45) 23 i
* i 3.3.3.3/32 5.5.5.5 0 100 0 (45) 23 i
*> 4.4.4.4 0 100 0 (45) 23 i
! >-- output omitted --<Notice that each of these entries has been learned via an iBGP peer, indicated by “* i” at the beginning of the entry, and an eBGP peer, indicated by the absence of an “i” at the beginning. Each of the routes shown above was learned from the eBGP peering that has a next hop IP of 4.4.4.4 (R4).
This means that R4 replaced the IP address of its eBGP peer (R1) from which it learned the route (192.168.14.1) with its own IP address (4.4.4.4). So, the next hop self feature was configured correctly. You can see this on R5 as well:
R5#show ip bgp
BGP table version is 155, local router ID is 5.5.5.5
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
!
! >-- output omitted --< ! * 12.34.0.0/16 192.168.35.3 0 23 1 999 ? *>i 4.4.4.4 0 100 0 1 999 ?
* 23.45.0.0/16 192.168.35.3 0 23 1 999 ?
*>i 4.4.4.4 0 100 0 1 999 ?
* 66.77.0.0/17 192.168.35.3 0 23 1 999 ?
*>i 4.4.4.4 0 100 0 1 999 ?
* 89.100.0.0/18 192.168.35.3 0 23 1 999 ?
*>i 4.4.4.4 0 100 0 1 999 ?
* 91.200.0.0/18 192.168.35.3 0 23 1 999 ?
*>i 4.4.4.4 0 100 0 1 999 ?
* 102.64.0.0/18 192.168.35.3 0 23 1 999 ?
*>i 4.4.4.4 0 100 0 1 999 ?
* 123.45.0.0/17 192.168.35.3 0 23 1 999 ?
*>i 4.4.4.4 0 100 0 1 999 ?
* 130.25.0.0/18 192.168.35.3 0 23 1 999 ?
*>i 4.4.4.4 0 100 0 1 999 ?
* 175.45.200.0/21 192.168.35.3 0 23 1 999 ?
*>i 4.4.4.4 0 100 0 1 999 ?
* 183.77.220.0/22 192.168.35.3 0 23 1 999 ?
*>i 4.4.4.4 0 100 0 1 999 ?
* 185.100.0.0/19 192.168.35.3 0 23 1 999 ?
*>i 4.4.4.4 0 100 0 1 999 ?
* 190.30.128.0/17 192.168.35.3 0 23 1 999 ?
*>i 4.4.4.4 0 100 0 1 999 ?
* 195.225.0.0/19 192.168.35.3 0 23 1 999 ?
*>i 4.4.4.4 0 100 0 1 999 ?
* 199.10.192.0/22 192.168.35.3 0 23 1 999 ?
*>i 4.4.4.4 0 100 0 1 999 ?
* 203.0.113.0/30 192.168.35.3 0 23 1 999 ?
*>i 4.4.4.4 0 100 0 1 999 ?
* 210.45.128.0/23 192.168.35.3 0 23 1 999 ?
*>i 4.4.4.4 0 100 0 1 999 ?
* 212.12.16.0/21 192.168.35.3 0 23 1 999 ?
*>i 4.4.4.4 0 100 0 1 999 ?
* 216.80.192.0/22 192.168.35.3 0 23 1 999 ?
*>i 4.4.4.4 0 100 0 1 999 ?
* 220.85.200.0/23 192.168.35.3 0 23 1 999 ?
*>i 4.4.4.4 0 100 0 1 999 ?
* 221.25.0.0/19 192.168.35.3 0 23 1 999 ?
*>i 4.4.4.4 0 100 0 1 999 ?Once again, notice the next hop IPs of all of the routes that have been learned via iBGP. You can see that R4 replaced the next hop IP address with its own.
Examine some more of the BGP tables of the various routers to ensure that the next hop self feature is functioning correctly.
Verification of Basic BGP Topology
To test this basic BGP topology, you can perform several checks to ensure that the appropriate routes are being advertised. Note that testing is primarily achieved by examining how the BGP routes have been advertised to each BGP.
ping and traceroute. You may see something in the BGP table, but it’s not installed in the routing table. Also, make sure you specify a source, because it’s possible that your packet makes it to the destination, but the return traffic is dropped because one of the routers doesn’t know about your source.Examine BGP Table IPv4 R9
To view router R9’s BGP table, issue the following command. You should see something similar to the following:
R9#show ip bgp
BGP table version is 141, local router ID is 9.9.9.9
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
*> 1.1.1.1/32 5.5.5.5 0 4567 1 i
*> 2.2.2.2/32 5.5.5.5 0 4567 23 i
*> 3.3.3.3/32 5.5.5.5 0 4567 23 i
*> 4.4.4.4/32 5.5.5.5 0 4567 i
r> 5.5.5.5/32 5.5.5.5 0 0 4567 i
*> 6.6.6.6/32 5.5.5.5 0 4567 i
*> 7.7.7.7/32 5.5.5.5 0 4567 i
*> 9.9.9.9/32 0.0.0.0 0 32768 i
*> 10.0.0.1/32 5.5.5.5 0 4567 1 999 i
*> 12.34.0.0/16 5.5.5.5 0 4567 1 999 ?
*> 23.45.0.0/16 5.5.5.5 0 4567 1 999 ?
*> 66.77.0.0/17 5.5.5.5 0 4567 1 999 ?
*> 89.100.0.0/18 5.5.5.5 0 4567 1 999 ?
*> 91.200.0.0/18 5.5.5.5 0 4567 1 999 ?
*> 102.64.0.0/18 5.5.5.5 0 4567 1 999 ?
*> 123.45.0.0/17 5.5.5.5 0 4567 1 999 ?
*> 130.25.0.0/18 5.5.5.5 0 4567 1 999 ?
*> 175.45.200.0/21 5.5.5.5 0 4567 1 999 ?
*> 183.77.220.0/22 5.5.5.5 0 4567 1 999 ?
*> 185.100.0.0/19 5.5.5.5 0 4567 1 999 ?
*> 190.30.128.0/17 5.5.5.5 0 4567 1 999 ?
*> 195.225.0.0/19 5.5.5.5 0 4567 1 999 ?
*> 199.10.192.0/22 5.5.5.5 0 4567 1 999 ?
*> 203.0.113.0/30 5.5.5.5 0 4567 1 999 ?
*> 210.45.128.0/23 5.5.5.5 0 4567 1 999 ?
*> 212.12.16.0/21 5.5.5.5 0 4567 1 999 ?
*> 216.80.192.0/22 5.5.5.5 0 4567 1 999 ?
*> 220.85.200.0/23 5.5.5.5 0 4567 1 999 ?
*> 221.25.0.0/19 5.5.5.5 0 4567 1 999 ?Note that:
- All loopback0 interface IPv4 addresses of all routers (including the ISP router) have been successfully learned via BGP, except for R8, which does not participate in BGP.
- The next hop IP address for all loopback0 addresses is R5, which is R9’s only eBGP neighbor.
- The 5.5.5.5/32 network was learned via eBGP from R5 and is considered the best BGP route. However, it indicates a RIB failure with the “r” status code. This is because a static route to 5.5.5.5 exists within the routing table, superseding the Administrative Distance (AD) of the eBGP learned route; thus, it is not installed in the routing table.
- The 9.9.9.9/32 route has a next hop of 0.0.0.0, which indicates that it was learned via the local router. This has been given a default Weight of 32768 as expected, unlike the rest of the routes, which are given a Weight of 0.
- The AS Paths of each route are correct, based on the location of each individual router and the actual ASes that must be traversed to reach each route.
- All of the loopback addresses advertised by the ISP router are also found within the BGP table, all learned via the AS Path 4567 1 999. This is as expected because this is the shortest AS Path. They are also learned via another AS Path, which is 4567 23 1 999, but that path is longer.
- Even though the routes have been learned through an AS, which is a Confederation (4567), all internal AS numbers have been stripped from the AS Path.
- All of the loopback addresses advertised via the ISP router (except for the 10.0.0.1/32 address) have been learned via redistribution. That is why we see the “?” origin code at the end of each entry. The 10.0.0.1/32 route was injected into BGP using the
networkcommand, and thus, its origin code is “i”.
Examine BGP Table IPv4 R6
To view router R6’s BGP table, issue the following command. You should see something similar to the following:
R6#show ip bgp
BGP table version is 132, local router ID is 6.6.6.6
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
* i 1.1.1.1/32 5.5.5.5 0 100 0 (45) 1 i
*> 4.4.4.4 0 100 0 (45) 1 i
* i 2.2.2.2/32 5.5.5.5 0 100 0 (45) 23 i
*> 4.4.4.4 0 100 0 (45) 23 i
* i 3.3.3.3/32 5.5.5.5 0 100 0 (45) 23 i
*> 4.4.4.4 0 100 0 (45) 23 i
r i 4.4.4.4/32 5.5.5.5 0 100 0 (45) i
r> 4.4.4.4 0 100 0 (45) i
r i 5.5.5.5/32 5.5.5.5 0 100 0 (45) i
r> 4.4.4.4 0 100 0 (45) i
*> 6.6.6.6/32 0.0.0.0 0 32768 i
r>i 7.7.7.7/32 7.7.7.7 0 100 0 i
* i 9.9.9.9/32 5.5.5.5 0 100 0 (45) 4292935689 i
*> 4.4.4.4 0 100 0 (45) 4292935689 i
* i 10.0.0.1/32 5.5.5.5 0 100 0 (45) 1 999 i
*> 4.4.4.4 0 100 0 (45) 1 999 i
* i 12.34.0.0/16 5.5.5.5 0 100 0 (45) 1 999 ?
*> 4.4.4.4 0 100 0 (45) 1 999 ?
* i 23.45.0.0/16 5.5.5.5 0 100 0 (45) 1 999 ?
*> 4.4.4.4 0 100 0 (45) 1 999 ?
* i 66.77.0.0/17 5.5.5.5 0 100 0 (45) 1 999 ?
*> 4.4.4.4 0 100 0 (45) 1 999 ?
* i 89.100.0.0/18 5.5.5.5 0 100 0 (45) 1 999 ?
*> 4.4.4.4 0 100 0 (45) 1 999 ?
* i 91.200.0.0/18 5.5.5.5 0 100 0 (45) 1 999 ?
*> 4.4.4.4 0 100 0 (45) 1 999 ?
* i 102.64.0.0/18 5.5.5.5 0 100 0 (45) 1 999 ?
*> 4.4.4.4 0 100 0 (45) 1 999 ?
* i 123.45.0.0/17 5.5.5.5 0 100 0 (45) 1 999 ?
*> 4.4.4.4 0 100 0 (45) 1 999 ?
* i 130.25.0.0/18 5.5.5.5 0 100 0 (45) 1 999 ?
*> 4.4.4.4 0 100 0 (45) 1 999 ?
* i 175.45.200.0/21 5.5.5.5 0 100 0 (45) 1 999 ?
*> 4.4.4.4 0 100 0 (45) 1 999 ?
* i 183.77.220.0/22 5.5.5.5 0 100 0 (45) 1 999 ?
*> 4.4.4.4 0 100 0 (45) 1 999 ?
* i 185.100.0.0/19 5.5.5.5 0 100 0 (45) 1 999 ?
*> 4.4.4.4 0 100 0 (45) 1 999 ?
* i 190.30.128.0/17 5.5.5.5 0 100 0 (45) 1 999 ?
*> 4.4.4.4 0 100 0 (45) 1 999 ?
* i 195.225.0.0/19 5.5.5.5 0 100 0 (45) 1 999 ?
*> 4.4.4.4 0 100 0 (45) 1 999 ?
* i 199.10.192.0/22 5.5.5.5 0 100 0 (45) 1 999 ?
*> 4.4.4.4 0 100 0 (45) 1 999 ?
* i 203.0.113.0/30 5.5.5.5 0 100 0 (45) 1 999 ?
*> 4.4.4.4 0 100 0 (45) 1 999 ?
* i 210.45.128.0/23 5.5.5.5 0 100 0 (45) 1 999 ?
*> 4.4.4.4 0 100 0 (45) 1 999 ?
* i 212.12.16.0/21 5.5.5.5 0 100 0 (45) 1 999 ?
*> 4.4.4.4 0 100 0 (45) 1 999 ?
* i 216.80.192.0/22 5.5.5.5 0 100 0 (45) 1 999 ?
*> 4.4.4.4 0 100 0 (45) 1 999 ?
* i 220.85.200.0/23 5.5.5.5 0 100 0 (45) 1 999 ?
*> 4.4.4.4 0 100 0 (45) 1 999 ?
* i 221.25.0.0/19 5.5.5.5 0 100 0 (45) 1 999 ?
*> 4.4.4.4 0 100 0 (45) 1 999 ?You can use the following command to see from which routers the routes are being learned:
R6#show ip bgp 1.1.1.1
BGP routing table entry for 1.1.1.1/32, version 110
Paths: (2 available, best #2, table default)
Advertised to update-groups:
2
Refresh Epoch 1
(45) 1
5.5.5.5 (metric 3) from 7.7.7.7 (7.7.7.7)
Origin IGP, metric 0, localpref 100, valid, confed-internal
rx pathid: 0, tx pathid: 0
Refresh Epoch 1
(45) 1
4.4.4.4 (metric 2) from 4.4.4.4 (4.4.4.4)
Origin IGP, metric 0, localpref 100, valid, confed-external, best
rx pathid: 0, tx pathid: 0x0Note that:
- All loopback0 interface IPv4 addresses of all routers (including the ISP router) have been successfully learned via BGP, except for R8 which is not participating in BGP.
- All of these loopback0 interface addresses have been learned via eBGP and via iBGP except for the 6.6.6.6/32 and 7.7.7.7/32 networks which belong to the local sub-AS.
- Note that the eBGP learned routes are being learned from R4 in the neighboring sub-AS which the iBGP routes are being learned from R7.
- In all cases, the eBGP routes are preferred as the best.
- The next hop IP address for all of the loopback0 addresses is either R4 or R5, where in all cases, R4 is chosen as the preferred path.
- The IP addresses of R4. R5, and R7 are in the BGP table, but indicate a RIB failure with the “r” status code. This is because these routes are found within the routing table using a preferred routing source, and thus a RIB failure is indicated.
- The 9.9.9.9/32 route uses a 4-byte AS number as expected.
- The AS Paths of each route are correct, based on the location of each individual router and the actual ASes that must be traversed to reach each route.
- All of the loopback addresses advertised by the ISP router are also found within the BGP table, all learned via the AS Path (45) 1 999. This is as expected, because internally in the Confederation, the sub-AS 45 appears in parentheses.
- All of the loopback addresses advertised via the ISP router (except for the 10.0.0.1/32 address) have been learned via redistribution. That is why we see the “?” origin code at the end of each entry. The 10.0.0.1/32 route was injected into BGP using the
networkcommand, and thus, its origin code is “i”.
Examine BGP Table IPv4 R2
To view router R2’s BGP table, issue the following command. You should see something similar to the following:
R2#show ip bgp
BGP table version is 208, local router ID is 2.2.2.2
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
*> 1.1.1.1/32 192.168.12.1 0 0 1 i
* i 3.3.3.3 0 100 0 1 i
* 192.168.24.4 0 4567 1 i
*> 2.2.2.2/32 0.0.0.0 0 32768 i
r>i 3.3.3.3/32 3.3.3.3 0 100 0 i
* 4.4.4.4/32 192.168.12.1 0 1 4567 i
* i 3.3.3.3 0 100 0 4567 i
*> 192.168.24.4 0 0 4567 i
* 5.5.5.5/32 192.168.12.1 0 1 4567 i
* i 3.3.3.3 0 100 0 4567 i
*> 192.168.24.4 0 4567 i
* 6.6.6.6/32 192.168.12.1 0 1 4567 i
* i 3.3.3.3 0 100 0 4567 i
*> 192.168.24.4 0 4567 i
* 7.7.7.7/32 192.168.12.1 0 1 4567 i
* i 3.3.3.3 0 100 0 4567 i
*> 192.168.24.4 0 4567 i
* 9.9.9.9/32 192.168.12.1 0 1 4567 4292935689 i
*> 192.168.24.4 0 4567 4292935689 i
* i 3.3.3.3 0 100 0 4567 4292935689 i
*> 10.0.0.1/32 192.168.12.1 0 1 999 i
* i 3.3.3.3 0 100 0 1 999 i
* 192.168.24.4 0 4567 1 999 i
*> 12.34.0.0/16 192.168.12.1 0 1 999 ?
* i 3.3.3.3 0 100 0 1 999 ?
* 192.168.24.4 0 4567 1 999 ?
*> 23.45.0.0/16 192.168.12.1 0 1 999 ?
* i 3.3.3.3 0 100 0 1 999 ?
* 192.168.24.4 0 4567 1 999 ?
*> 66.77.0.0/17 192.168.12.1 0 1 999 ?
* i 3.3.3.3 0 100 0 1 999 ?
* 192.168.24.4 0 4567 1 999 ?
*> 89.100.0.0/18 192.168.12.1 0 1 999 ?
* i 3.3.3.3 0 100 0 1 999 ?
* 192.168.24.4 0 4567 1 999 ?
*> 91.200.0.0/18 192.168.12.1 0 1 999 ?
* i 3.3.3.3 0 100 0 1 999 ?
* 192.168.24.4 0 4567 1 999 ?
*> 102.64.0.0/18 192.168.12.1 0 1 999 ?
* i 3.3.3.3 0 100 0 1 999 ?
* 192.168.24.4 0 4567 1 999 ?
*> 123.45.0.0/17 192.168.12.1 0 1 999 ?
* i 3.3.3.3 0 100 0 1 999 ?
* 192.168.24.4 0 4567 1 999 ?
*> 130.25.0.0/18 192.168.12.1 0 1 999 ?
* i 3.3.3.3 0 100 0 1 999 ?
* 192.168.24.4 0 4567 1 999 ?
*> 175.45.200.0/21 192.168.12.1 0 1 999 ?
* i 3.3.3.3 0 100 0 1 999 ?
* 192.168.24.4 0 4567 1 999 ?
*> 183.77.220.0/22 192.168.12.1 0 1 999 ?
* i 3.3.3.3 0 100 0 1 999 ?
* 192.168.24.4 0 4567 1 999 ?
*> 185.100.0.0/19 192.168.12.1 0 1 999 ?
* i 3.3.3.3 0 100 0 1 999 ?
* 192.168.24.4 0 4567 1 999 ?
*> 190.30.128.0/17 192.168.12.1 0 1 999 ?
* i 3.3.3.3 0 100 0 1 999 ?
* 192.168.24.4 0 4567 1 999 ?
*> 195.225.0.0/19 192.168.12.1 0 1 999 ?
* i 3.3.3.3 0 100 0 1 999 ?
* 192.168.24.4 0 4567 1 999 ?
*> 199.10.192.0/22 192.168.12.1 0 1 999 ?
* i 3.3.3.3 0 100 0 1 999 ?
* 192.168.24.4 0 4567 1 999 ?
*> 203.0.113.0/30 192.168.12.1 0 1 999 ?
* i 3.3.3.3 0 100 0 1 999 ?
* 192.168.24.4 0 4567 1 999 ?
*> 210.45.128.0/23 192.168.12.1 0 1 999 ?
* i 3.3.3.3 0 100 0 1 999 ?
* 192.168.24.4 0 4567 1 999 ?
*> 212.12.16.0/21 192.168.12.1 0 1 999 ?
* i 3.3.3.3 0 100 0 1 999 ?
* 192.168.24.4 0 4567 1 999 ?
*> 216.80.192.0/22 192.168.12.1 0 1 999 ?
* i 3.3.3.3 0 100 0 1 999 ?
* 192.168.24.4 0 4567 1 999 ?
*> 220.85.200.0/23 192.168.12.1 0 1 999 ?
* i 3.3.3.3 0 100 0 1 999 ?
* 192.168.24.4 0 4567 1 999 ?
*> 221.25.0.0/19 192.168.12.1 0 1 999 ?
* i 3.3.3.3 0 100 0 1 999 ?
* 192.168.24.4 0 4567 1 999 ?Note that:
- Routes are learned from three sources:
- One iBGP source which is R3.
- Two eBGP sources which are R1 and R4.
- Except for the 3.3.3.3/32 network, all other networks choose the best path as the one learned via eBGP. And among the eBGP paths, the best path is the one with the shortest AS path.
- Much of the results that you can see are similar to what you saw in the previous routers.
Examine BGP Table IPv6 R2
To view router R2’s BGP table containing IPv6 networks, issue the following command. You should see something similar to the following:
R2#show bgp ipv6 unicast
BGP table version is 1, local router ID is 2.2.2.2
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
* 2001:DB8:1::1/128
::FFFF:192.168.12.1
0 1 999 i
* 2001:DB8:12:34::/64
::FFFF:192.168.12.1
0 1 999 i
* 2001:DB8:23:45::/64
::FFFF:192.168.12.1
0 1 999 i
* 2001:DB8:66:77::/64
::FFFF:192.168.12.1
0 1 999 i
* 2001:DB8:89:100::/64
::FFFF:192.168.12.1
0 1 999 i
* 2001:DB8:91:200::/64
::FFFF:192.168.12.1
0 1 999 i
* 2001:DB8:102:64::/64
::FFFF:192.168.12.1
0 1 999 i
* 2001:DB8:123:45::/64
::FFFF:192.168.12.1
0 1 999 i
* 2001:DB8:130:25::/64
::FFFF:192.168.12.1
0 1 999 i
* 2001:DB8:175:45::/64
::FFFF:192.168.12.1
0 1 999 i
* 2001:DB8:183:77::/64
::FFFF:192.168.12.1
0 1 999 i
* 2001:DB8:185:100::/64
::FFFF:192.168.12.1
0 1 999 i
* 2001:DB8:190:32::/64
::FFFF:192.168.12.1
0 1 999 i
* 2001:DB8:195:225::/64
::FFFF:192.168.12.1
0 1 999 i
* 2001:DB8:199:10::/64
::FFFF:192.168.12.1
0 1 999 i
* 2001:DB8:210:45::/64
::FFFF:192.168.12.1
0 1 999 i
* 2001:DB8:212:12::/64
::FFFF:192.168.12.1
0 1 999 i
* 2001:DB8:216:80::/64
::FFFF:192.168.12.1
0 1 999 i
* 2001:DB8:220:85::/64
::FFFF:192.168.12.1
0 1 999 i
* 2001:DB8:225:25::/64
::FFFF:192.168.12.1
0 1 999 iNote that:
- R2’s BGP table contains all of the IPv6 routes created in the ISP router and the address of the Loopback0 interface on R1.
- These routes are given a next hop IP address of ::FFFF:192.168.12.1 which indicates they are learned via IPv4 from R1.
- The AS path for all these routes is considered valid, but it is not considered the “best” because the next hop IP is not reachable.
- All the routes are considered valid, but they are not considered the “best” because the next hop IP is not reachable.
Advanced BGP Features
Once you have configured the above and verified their correct implementation, the next step is to tweak and adjust additional features
BGP Auto Summary
To fulfill the requirements of the implementation of BGP Auto-Summary on R9, perform the following configurations:
R9(config)#router bgp 65505.9
R9(config-router)#auto-summary
R9(config-router)#no network 9.9.9.9 mask 255.255.255.255
R9(config-router)#network 9.0.0.0To verify that the classful network has entered the routing table of R9, use the following verification command:
R9#show ip bgp 9.0.0.0
BGP routing table entry for 9.0.0.0/8, version 143
Paths: (1 available, best #1, table default)
Advertised to update-groups:
2
Refresh Epoch 1
Local
0.0.0.0 from 0.0.0.0 (9.9.9.9)
Origin IGP, metric 0, localpref 100, weight 32768, valid, sourced, local, best
rx pathid: 0, tx pathid: 0x0As you can see, the network in the local routing table appears as a class A network. To examine how this network has been advertised to the rest of the network, take a look at the BGP tables of other routers. The following shows the BGP table of R2 and indicates how it perceives the network advertised from R9:
R2#show ip bgp 9.0.0.0
BGP routing table entry for 9.0.0.0/8, version 212
Paths: (3 available, best #2, table default)
Advertised to update-groups:
7 8
Refresh Epoch 2
1 4567 4292935689
192.168.12.1 from 192.168.12.1 (1.1.1.1)
Origin IGP, localpref 100, valid, external
rx pathid: 0, tx pathid: 0
Refresh Epoch 3
4567 4292935689
192.168.24.4 from 192.168.24.4 (4.4.4.4)
Origin IGP, localpref 100, valid, external, best
rx pathid: 0, tx pathid: 0x0
Refresh Epoch 1
4567 4292935689
3.3.3.3 (metric 2) from 3.3.3.3 (3.3.3.3)
Origin IGP, metric 0, localpref 100, valid, internal
rx pathid: 0, tx pathid: 0You can check the BGP tables of other routers to see that the table entry has been installed in a classful manner.
BGP Summarization
To perform the required route summarization and fulfill the requirements of this task, perform the following configurations:
You are asked to summarize the networks found on Loopbacks 10, 11, and 12 of the ISP router:
- Loopback10 183.77.220.1
- Loopback11 185.100.0.1
- Loopback12 190.30.128.1
The summary address for these networks is 176.0.0.0/4. You can attempt to calculate it yourself as well.
The task requires that only the summary address be installed in the ISP router’s local routing table and that all member routes of the summary be marked as “suppressed” routes in the BGP routing table.
To fulfill these requirements, do the following:
ISP(config)#router bgp 999
ISP(config-router)#address-family ipv4
ISP(config-router-af)#aggregate-address 176.0.0.0 240.0.0.0 summary-onlyRemember that because the ISP router is configured with multiple address families, the command must be applied under the IPv4 address family configuration mode. The summary-only keyword is used to ensure that the member prefixes are suppressed within the BGP table. To verify this, take a look at the BGP table of the ISP router like so:
ISP#show ip bgp
BGP table version is 45, local router ID is 221.25.0.1
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
*> 1.1.1.1/32 203.0.113.1 0 0 1 i
*> 2.2.2.2/32 203.0.113.1 0 1 23 i
*> 3.3.3.3/32 203.0.113.1 0 1 23 i
*> 4.4.4.4/32 203.0.113.1 0 1 4567 i
*> 5.5.5.5/32 203.0.113.1 0 1 4567 i
*> 6.6.6.6/32 203.0.113.1 0 1 4567 i
*> 7.7.7.7/32 203.0.113.1 0 1 4567 i
*> 9.0.0.0 203.0.113.1 0 1 4567 4292935689 i
*> 10.0.0.1/32 0.0.0.0 0 32768 i
*> 12.34.0.0/16 0.0.0.0 0 32768 ?
*> 23.45.0.0/16 0.0.0.0 0 32768 ?
*> 66.77.0.0/17 0.0.0.0 0 32768 ?
*> 89.100.0.0/18 0.0.0.0 0 32768 ?
*> 91.200.0.0/18 0.0.0.0 0 32768 ?
*> 102.64.0.0/18 0.0.0.0 0 32768 ?
*> 123.45.0.0/17 0.0.0.0 0 32768 ?
*> 130.25.0.0/18 0.0.0.0 0 32768 ?
*> 175.45.200.0/21 0.0.0.0 0 32768 ?
*> 176.0.0.0/4 0.0.0.0 32768 i
s> 183.77.220.0/22 0.0.0.0 0 32768 ?
s> 185.100.0.0/19 0.0.0.0 0 32768 ?
s> 190.30.128.0/17 0.0.0.0 0 32768 ?
*> 195.225.0.0/19 0.0.0.0 0 32768 ?
*> 199.10.192.0/22 0.0.0.0 0 32768 ?
*> 203.0.113.0/30 0.0.0.0 0 32768 ?
*> 210.45.128.0/23 0.0.0.0 0 32768 ?
*> 212.12.16.0/21 0.0.0.0 0 32768 ?
*> 216.80.192.0/22 0.0.0.0 0 32768 ?
*> 220.85.200.0/23 0.0.0.0 0 32768 ?
*> 221.25.0.0/19 0.0.0.0 0 32768 ?Notice that the summary route has been installed, and that the three member routes of that summary route have been marked with an “s” which means “suppressed”. Let’s also ensure these routes have not been further advertised to routers outside of AS 999. Let’s take a look at the BGP table of R1:
R1#show ip bgp
BGP table version is 47, local router ID is 1.1.1.1
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
t secondary path,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
*> 1.1.1.1/32 0.0.0.0 0 32768 i
* 2.2.2.2/32 192.168.12.2 0 0 23 i
* 192.168.14.4 0 4567 23 i
*> 192.168.13.3 0 23 i
* 3.3.3.3/32 192.168.12.2 0 23 i
* 192.168.14.4 0 4567 23 i
*> 192.168.13.3 0 0 23 i
* 4.4.4.4/32 192.168.12.2 0 23 4567 i
* 192.168.13.3 0 23 4567 i
*> 192.168.14.4 0 0 4567 i
* 5.5.5.5/32 192.168.12.2 0 23 4567 i
* 192.168.13.3 0 23 4567 i
*> 192.168.14.4 0 4567 i
* 6.6.6.6/32 192.168.12.2 0 23 4567 i
* 192.168.13.3 0 23 4567 i
*> 192.168.14.4 0 4567 i
* 7.7.7.7/32 192.168.12.2 0 23 4567 i
* 192.168.13.3 0 23 4567 i
*> 192.168.14.4 0 4567 i
* 9.0.0.0 192.168.13.3 0 23 4567 4292935689 i
* 192.168.12.2 0 23 4567 4292935689 i
*> 192.168.14.4 0 4567 4292935689 i
*> 10.0.0.1/32 203.0.113.2 0 0 999 i
*> 12.34.0.0/16 203.0.113.2 0 0 999 ?
*> 23.45.0.0/16 203.0.113.2 0 0 999 ?
*> 66.77.0.0/17 203.0.113.2 0 0 999 ?
*> 89.100.0.0/18 203.0.113.2 0 0 999 ?
*> 91.200.0.0/18 203.0.113.2 0 0 999 ?
*> 102.64.0.0/18 203.0.113.2 0 0 999 ?
*> 123.45.0.0/17 203.0.113.2 0 0 999 ?
*> 130.25.0.0/18 203.0.113.2 0 0 999 ?
*> 175.45.200.0/21 203.0.113.2 0 0 999 ?
*> 176.0.0.0/4 203.0.113.2 0 0 999 i
*> 195.225.0.0/19 203.0.113.2 0 0 999 ?
*> 199.10.192.0/22 203.0.113.2 0 0 999 ?
r> 203.0.113.0/30 203.0.113.2 0 0 999 ?
*> 210.45.128.0/23 203.0.113.2 0 0 999 ?
*> 212.12.16.0/21 203.0.113.2 0 0 999 ?
*> 216.80.192.0/22 203.0.113.2 0 0 999 ?
*> 220.85.200.0/23 203.0.113.2 0 0 999 ?
*> 221.25.0.0/19 203.0.113.2 0 0 999 ?Notice that the summary route can be found in the BGP table of R1, but the member routes cannot be found. You can check other routers within the network as well to ensure that the summary route has been propagated throughout the network.
BGP Weight Attribute
To ensure that the 12.34.0.0/16 network is routed from R4 via AS 23 instead of AS 1, you must modify the Weight attribute on R4 using a route map.
To check the current best path for this network, take a look at the BGP table of R4 for this route:
R4#show ip bgp 12.34.0.0
BGP routing table entry for 12.34.0.0/16, version 3
Paths: (2 available, best #2, table default)
Advertised to update-groups:
6 7 10
Refresh Epoch 5
23 1 999
192.168.24.2 from 192.168.24.2 (2.2.2.2)
Origin incomplete, localpref 100, valid, external
rx pathid: 0, tx pathid: 0
Refresh Epoch 1
1 999
192.168.14.1 from 192.168.14.1 (1.1.1.1)
Origin incomplete, localpref 100, valid, external, best
rx pathid: 0, tx pathid: 0x0As you can see, there are two routes to the destination from R4, via R1 and via R2. Via R1 is chosen as the best path because the AS Path Length is shorter.
To use the Weight attribute to change this behavior as the task describes, issue the following commands. First, configure the route map that will modify the weight of the route that matches ACL 1, and will leave all other routes unmodified:
R4(config)#route-map SETWEIGHT permit 10
R4(config-route-map)#match ip address 1
R4(config-route-map)#set weight 500
R4(config-route-map)#route-map SETWEIGHT permit 20Next, configure the access list that will match the route in question:
R4(config)#access-list 1 permit 12.34.0.0 0.0.255.255Finally, apply the route map in an inbound direction on the eBGP peer of R2:
R4(config)#router bgp 45
R4(config-router)#neighbor 192.168.24.2 route-map SETWEIGHT inThe changes will take some time to take effect. To speed up the process, use the following command on R4:
R4#clear ip bgp *After a few moments, you can check to see the results of the change using the following command:
R4#show ip bgp 12.34.0.0
BGP routing table entry for 12.34.0.0/16, version 11
Paths: (3 available, best #3, table default)
Advertised to update-groups:
20 21 22
Refresh Epoch 2
1 999
192.168.14.1 from 192.168.14.1 (1.1.1.1)
Origin incomplete, localpref 100, valid, external
rx pathid: 0, tx pathid: 0
Refresh Epoch 1
23 1 999
5.5.5.5 (metric 2) from 5.5.5.5 (5.5.5.5)
Origin incomplete, metric 0, localpref 100, valid, confed-internal
rx pathid: 0, tx pathid: 0
Refresh Epoch 3
23 1 999
192.168.24.2 from 192.168.24.2 (2.2.2.2)
Origin incomplete, localpref 100, weight 500, valid, external, best
rx pathid: 0, tx pathid: 0x0You can see that the best path is now the one via R2, with a weight of 500.
BGP Local Preference Attribute
To ensure that BGP operates such that packets destined for the 23.45.0.0/16 network from within AS 23 will always exit that AS via the R2 router by modifying the Local Preference attribute, perform the following. First, configure the route map that will modify the Local Preference of the route that matches ACL 1, and will leave all other routes unmodified:



I’m really loving this new addition to the courses with these labs. They truly help us bridge everything together and provide a better understanding of the concepts, which is crucial for our education and careers. The hands-on experience is indispensable. I can only hope you continue to develop more labs like this, focusing on BGP, MPLS, IGPs, DMVPNs, and other key technologies. These labs allow us to experiment and fully advance our knowledge. Keep up the great work!
Hello Sahakt
Your feedback is invaluable. It’s great to hear that these labs are so useful to you and the whole community. There are plans to create more such labs so that the skills you learn in the lessons can be applied in a hands-on and practical way.
Thanks again!
Laz
Hey all, I’m loving this lab! Have a quick question regarding 3.4.10 BGP Route Filtering. Looks like the task is to filter out all /22 and above but the output of R9 shows routes with both /22 and /23. My mask and wildcard differed from the solution and I filtered out any prefix with a mask of /22 or greater. I was just wondering if I misunderstood the ask. Thanks again for the lab!
Notice that all prefixes ranging from /22 to /32 have been removed from the BGP table. The task is complete.
... Continue reading in our forumGood morning Joshua
Thanks for pointing this out. Those two routes should indeed be removed. I’m not sure why they weren’t at that particular point during the preparation of this lab. I have to own this error , since I had put this lab together. As we prepare these labs we often go back and forth and sometimes the copying and pasting may contain a typo because it comes from a slightly different point in time. Those should be removed, and I will let Rene know to make the correction.
, since I had put this lab together. As we prepare these labs we often go back and forth and sometimes the copying and pasting may contain a typo because it comes from a slightly different point in time. Those should be removed, and I will let Rene know to make the correction.
However, I would like to ask, beyond the output as it appears in the lab, d
... Continue reading in our forumMorning Lazarus!
... Continue reading in our forumI have learned so much with this lab! The only incorrect result that I’ve noticed thus far is the mac and wildcard for this particular solution (3.4.10) and it could still be that I just misapplied the answer. I used
deny ip 0.0.0.0 255.255.255.255 255.255.252.0 0.0.3.255to catch anddeny anything ge /22and my output is this: