Sometimes it might be useful to block certain traffic on specific days or during business hours. For example, maybe you want to block all facebook traffic from monday to friday between 9:00 – 17:00.
We can achieve this by using time ranges in our access-lists. When you use these, the statement in the access-list will only be active during the time range that you specified. Let’s take a look at an example!
Configuration
To demonstrate the time based access-list I will use the following topology:
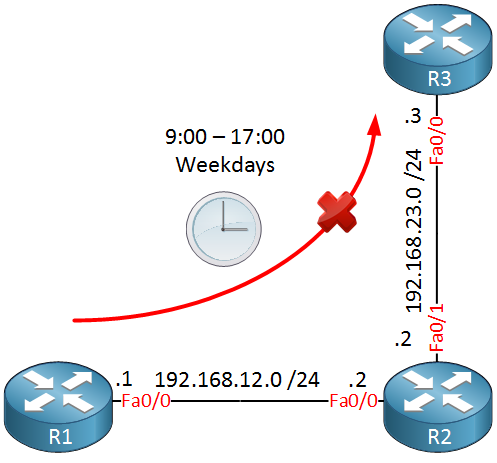
Above we have three routers, imagine that R1 is a user on a computer and R3 is some webserver. We want to prevent access from R1 to the webserver on R3 on business days between 9:00 – 17:00. We will configure the time based access-list on R2.
The time range command relies on the clock so make sure the time and date is correct:
R2#clock set 12:48:00 14 July 2015Normally it would be better to use NTP but for this example I’ll configure it manually. Now we can configure a time range:
R2(config)#time-range WORK_HOURS
R2(config-time-range)#periodic ?
Friday Friday
Monday Monday
Saturday Saturday
Sunday Sunday
Thursday Thursday
Tuesday Tuesday
Wednesday Wednesday
daily Every day of the week
weekdays Monday thru Friday
weekend Saturday and SundayThere are quite some options, we can select a specific day or you can use some ranges like weekdays, weekend, etc. Let’s go for the weekdays:
R2(config-time-range)#periodic weekdays 09:00 to 17:00We now have a time range called “WORK_HOURS” for business hours. Let’s create an access-list:
R2(config)#ip access-list extended NO_FACEBOOK
R2(config-ext-nacl)#deny tcp any host 192.168.23.3 eq 80 time-range WORK_HOURS
R2(config-ext-nacl)#permit ip any anyThe access-list above has a statement that blocks traffic to TCP port 80 on 192.168.23.3 but only for the time range that we specified. Let’s activate it on the interface:
R2(config)#interface FastEthernet 0/0
R2(config-if)#ip access-group NO_FACEBOOK inNow we can try to connect to R3 from R1:
R1#telnet 192.168.23.3 80
Trying 192.168.23.3, 80 ...
% Destination unreachable; gateway or host downWe can’t connect to the webserver on R3. Is this because of our time range? Let’s find out:



is this how most companies block access, i think we use something called websense?
also with facbeook having so many webservers in a farm for redundancy would you in real world scendario block by ip, or hostname?
Hi Ruby,
The time based access-list is basically the “poor man’s” solution to block access on routers. You can use access-lists only to filter on L3/L4 information (IP addresses, protocols and port numbers) so you can’t filter based on hostnames.
One way to get around this is to block all prefixes that belong to a certain AS. For example, facebook uses AS 32934. We can find their prefixes with whois:
... Continue reading in our forumDear Rene,
Thanks for your article..
What will be the command periodic if we want to block traffic from Sunday to Thrusday ?
br//
zaman
Hi Zaman,
You can use some of the default periodic options:
Including “weekend”.
Rene
Hi Rene,
In our client network,
The Cisco Layer 2 Switch 2960G port 15 which is connected to the L2VPN MPLS-TP network and each month or time not remembering , the port is getting down and they are changing the port to other 16 Which was also configured for the same service. Once contractor was done this but client want to know if there is any time based port security is enable or no, Kindly share your advise.