In a previous lesson, I covered the standard access-list, now it’s time to take a look at the extended access-list. This is the topology we’ll use:
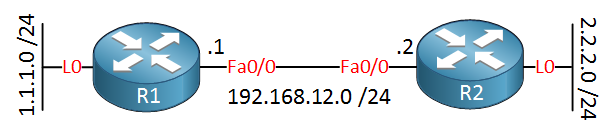
Using the extended access-list, we can create far more complex statements. Let’s say we have the following requirement:
- Traffic from network 1.1.1.0 /24 is allowed to connect to the HTTP server on R2, but they are only allowed to connect to IP address 2.2.2.2.
- All other traffic has to be denied.
Now we need to translate this to an extended access-list statement. Basically, they look like this:
[source] + [ source port] to [destination] + [destination port]Let’s walk through the configuration together:
R2(config)#access-list 100 ?
deny Specify packets to reject
dynamic Specify a DYNAMIC list of PERMITs or DENYs
permit Specify packets to forward
remark Access list entry commentFirst of all, we need to select a permit or deny. By the way, you can also use a remark. You can use this to add a comment to your access-list statements. I’ll select the permit:
R2(config)#access-list 100 permit ?
<0-255> An IP protocol number
ahp Authentication Header Protocol
eigrp Cisco's EIGRP routing protocol
esp Encapsulation Security Payload
gre Cisco's GRE tunneling
icmp Internet Control Message Protocol
igmp Internet Gateway Message Protocol
ip Any Internet Protocol
ipinip IP in IP tunneling
nos KA9Q NOS compatible IP over IP tunneling
ospf OSPF routing protocol
pcp Payload Compression Protocol
pim Protocol Independent Multicast
tcp Transmission Control Protocol
udp User Datagram ProtocolNow we have a lot more options. Since I want something that permits HTTP traffic we’ll have to select TCP. Let’s continue:
R2(config)#access-list 100 permit tcp ?
A.B.C.D Source address
any Any source host
host A single source hostNow we have to select a source. I can either type in a network address with a wildcard or I can use the any or host keyword. These two keywords are “shortcuts”. Let me explain:
- If you type “0.0.0.0 255.255.255.255,” you have all networks. Instead of typing this, we can use any keyword.
- If you type something like “2.2.2.2 0.0.0.0” we are matching a single IP address. Instead of typing the “0.0.0.0” wildcard, we can use the keyword host.
I want to select network 1.1.1.0 /24 as the source, so this is what we will do:
R2(config)#access-list 100 permit tcp 1.1.1.0 0.0.0.255 ?
A.B.C.D Destination address
any Any destination host
eq Match only packets on a given port number
gt Match only packets with a greater port number
host A single destination host
lt Match only packets with a lower port number
neq Match only packets not on a given port number
range Match only packets in the range of port numbersBesides selecting the source, we can also select the source port number. Keep in mind that when I connect from R1 to R2’s HTTP server my source port number will be random so I’m not going to specify a source port number here.
R2(config)#access-list 100 permit tcp 1.1.1.0 0.0.0.255 host 2.2.2.2 ?
ack Match on the ACK bit
dscp Match packets with given dscp value
eq Match only packets on a given port number
established Match established connections
fin Match on the FIN bit
fragments Check non-initial fragments
gt Match only packets with a greater port number
log Log matches against this entry
log-input Log matches against this entry, including input interface
lt Match only packets with a lower port number
neq Match only packets not on a given port number
precedence Match packets with given precedence value
psh Match on the PSH bit
range Match only packets in the range of port numbers
rst Match on the RST bit
syn Match on the SYN bit
time-range Specify a time-range
tos Match packets with given TOS value
urg Match on the URG bit
<cr>We will select the destination, which is the IP address 2.2.2.2. I could have typed “2.2.2.2 0.0.0.0,” but it’s easier to use the host keyword. Besides the destination IP address, we can select a destination port number with the eq keyword:
R2(config)#access-list 100 permit tcp 1.1.1.0 0.0.0.255 host 2.2.2.2 eq 80This will be the end result. Before we apply it to the interface, I will add one useful extra statement:



Hi Rene,
One quick question, why do you need to specify: Robocop(config)#access-list 100 deny ip any any log
when at the end of every access list there is the invisible deny command.
Any clarification would be greatly appreciated.
Thanks
P.S. Keep up the good work.
Hi Edmundo,
Adding the log keyword will show all denied packets in your console. This is useful for troubleshooting, debugging or labbing.
So if I understand correctly we would still achieve the same results if without entering this command? And the only reason we would use this command is mostly for logging events, troubleshooting or labbing…correct?
Thanks
Yes that’s right. There is always a default deny any at the bottom. Give it a try on a Cisco IOS router…
Hey.. that’s really helpful..thnx so much..keep up the good work!