PPP is one of the WAN protocols that you can configure on Cisco IOS routers. We will take a look at how PPP works and how to configure it. Do you still remember how the OSI model works?
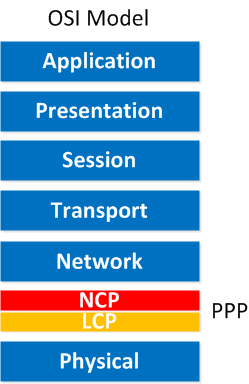
PPP operates on the data link layer (layer 2), but as you can see, the data link layer has been split into two pieces:
- NCP: Network Control Protocol
- LCP: Link Control Protocol
Let’s start with LCP:
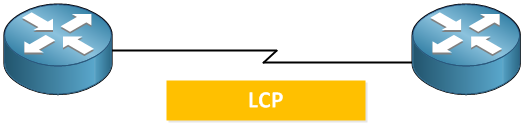
LCP takes care of setting up the link. If you enable authentication for PPP, it will take care of authentication. Once the link has been set up we use NCP.
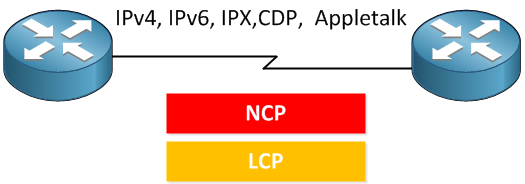
NCP will ensure you can run different protocols over our PPP link like IP, IPv6 but also CDP (Cisco Discovery Protocol) and older protocols like IPX or AppleTalk.
So, in short, if you enable PPP on both routers, this is what happens:
- LCP: Takes care of setting up the link.
- (Optional): Authentication.
- NCP: Makes sure we can send IP and other protocols across our PPP link.
Let’s see what authentication is about:

I have two routers; the router on the left side is called R1. If you want to use authentication for PPP, you have two options:
- PAP (Password Authentication Protocol): This is plaintext! It will send the username and password over the PPP link, and the router on the other side will check it.
- CHAP (Challenge Handshake Authentication Protocol): Instead of sending the password in plaintext, we will send a “challenge,” which is a hash of the password. This is far more secure.
In the example above, we are using PAP:
- On the left side, we have a router with the hostname R1.
- On the right side, we have a router without a hostname, but it has the username R1 and password VIDEO configured in a local database.
- PPP will start setting up the link by using LCP.
- Since authentication is enabled, our router on the right side will authenticate R1:
- R1 will send its hostname and password in plaintext.
- The router on the right side will accept or deny the credentials.
- If everything is ok, PPP will work, and we will be authenticated.
PAP is very simple but sending a username and password in plaintext is not a very secure method. Let’s see how CHAP works:



Have you ever encountered this scenario?
And because of this, interface is not bundling up in a multilink. As you can see that the inbound packet is telling the device that the protocol CDPCP is being rejected.
Hi Ali,
Do you have the complete debug for this? Normally I only see this when the PPP session is going down, for example when authentication fails or something.
Rene
This site is the best to learn network
Thank you Rene
Hi Rene,
Can we sub-interfaces in PPP to establishment more than one PPP connection on the same physical interface ?
thanks.
Hi Hussein,
PPP encapsulation on serial interfaces only works on the physical interface. If you want to get creative then you could run PPPoE on Ethernet sub-interfaces or PPP over frame-relay on sub-interfaces though.
Rene