NAT Port Forwarding is useful when you have a single public IP address and multiple devices behind it that you want to reach from the outside world. Take a look at the example below:
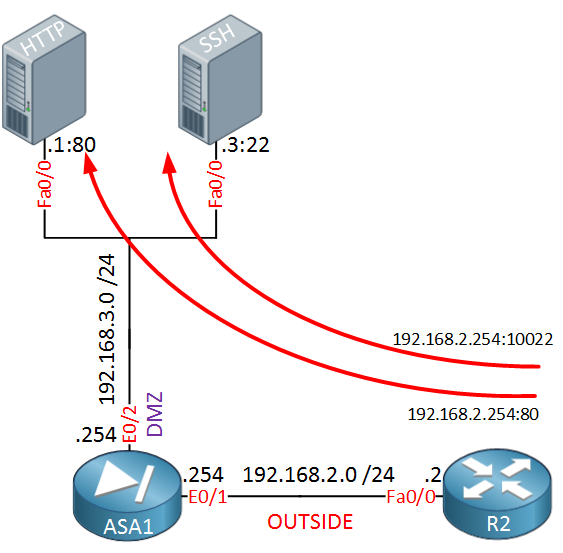 In the topology above we have an ASA firewall with a DMZ and two servers…a HTTP server and a SSH server. Let’s imagine that the IP address on the ASA’s E0/1 interface (192.168.2.254) is a public IP address. Our goal is to make sure that we can reach these servers from the outside world. R2 is only there so we have a device in the “outside” so we can try if NAT is working.
In the topology above we have an ASA firewall with a DMZ and two servers…a HTTP server and a SSH server. Let’s imagine that the IP address on the ASA’s E0/1 interface (192.168.2.254) is a public IP address. Our goal is to make sure that we can reach these servers from the outside world. R2 is only there so we have a device in the “outside” so we can try if NAT is working.
HTTP uses TCP port 80 and SSH uses TCP port 22 so what we’ll do is forward these ports. Whenever someone connects on IP address 192.168.2.254 TCP port 80 we will forward them to 192.168.3.1 TCP port 80.
We can use different port numbers if we want and to demonstrate this, we will configure the ASA so that whenever someone connects on 192.168.2.254 TCP port 10022, we will forward it to 192.168.3.3 TCP port 22.
Let me show you how to configure this. We start with the HTTP server:
ASA1(config)# object network WEB_SERVER
ASA1(config-network-object)# host 192.168.3.1
ASA1(config-network-object)# nat (DMZ,OUTSIDE) static interface service tcp 80 80We create a network object that specifies the real IP address of the web server and then we create our NAT rule. By using the keyword interface we tell the ASA to use the IP address on the (outside) interface. The first port number is the port that the server is listening on, the second port number is the outside port number. Let’s configure another PAT entry for the SSH server:
ASA1(config)# object network SSH_SERVER
ASA1(config-network-object)# host 192.168.3.3
ASA1(config-network-object)# nat (DMZ,OUTSIDE) static interface service tcp 22 10022This network object is similar to the first one but you can see I used a different port number for the outside. Whenever someone connects on TCP port 10022, it will be forwarded to TCP port 22. This takes care of the NAT rules but don’t forget to create an access-list or our traffic will be dropped:



Rene,
Your scenario explains forwarding traffic to port 22 for SSH, but further down in your configuration example you are using port 25 for SMTP. Any reason for the change between the scenario and the example configuration??
Hi Ralph,
That was a typo, I just changed port 25 to 22. Thanks for letting me know!
Rene
Hi Rene,
Thank you for the explanation.
I have a question.
In this tutorial, you are using PAT for sending traffic from Outside to DMZ. However, if I want to use PAT for sending traffic from DMZ to Outside, how should I do the configurations ?
Thank you
Taslim
Hi Taslim,
Hmm why would you want to do this? We use PAT in this example so that someone on the Internet is able to connect to a public IP address on the outside so that we can reach our DMZ servers with private IP addresses.
We use PAT in this example so that someone on the Internet is able to connect to a public IP address on the outside so that we can reach our DMZ servers with private IP addresses.
Our DMZ servers can reach the Internet by using “regular” NAT.
Rene
Hi Rene,
Diagram needs to be updated to 192.16.1.0/24 for lan subnet.