Lesson Contents
When you use pre-shared keys, you have to manually configure a pre-shared key for each peer that you want to use IPsec with.
With digital certificates, each peer gets a certificate from a CA (Certificate Authority). When two peers want to use IPsec, they exchange their certificates to authenticate each other.
What’s the big difference? One advantage of digital certificates is scalability.
For example, let’s say you have one firewall at your main office and 10 branch offices with a firewall each. All branch offices use IPsec to encrypt traffic between the branch and main office. For security reasons, we use a different pre-shared key between the main office and each branch office.
When you want to add an additional ASA firewall at your main office (perhaps for redundancy) then you will have to configure 10 additional pre-shared keys, one for each branch office. When two branch offices want to use IPsec between each other, you’ll need another pre-shared key.
With digital certificates, all firewalls will trust the certificates that are signed by the CA. When you want to use IPsec with a new firewall, the only thing you need to do is add a certificate to the new firewall. The other firewalls will automatically trust it since it was signed by the CA.
In this lesson, I’ll explain how to configure your Cisco ASA firewalls to use digital certificates for IPsec. We will use an OpenSSL server as the CA that signs the certificates for our firewalls.
Before you configure with this lesson, I would recommend finishing the following two lessons first:
In the first lesson you will learn how to build a CA with OpenSSL, the second lesson explains how to configure IPsec site-to-site VPNs with pre-shared keys.
Having said that, let’s get to work!
Configuration
We will use the following topology:
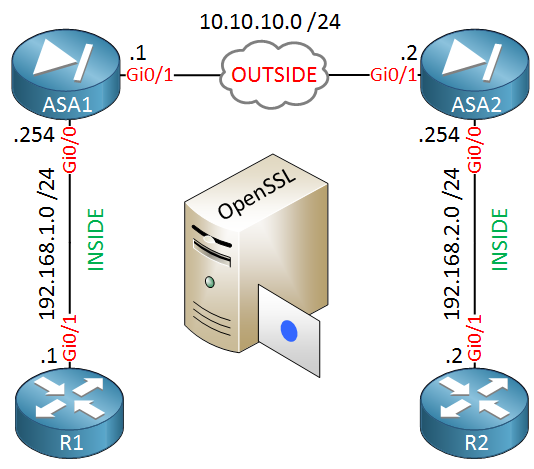
ASA1 and ASA2 are our two firewalls that we will configure to use IPsec to encrypt traffic between 192.168.1.0/24 and 192.168.2.0/24. Our routers, R1 and R2 are only used to test the VPN.
In the middle you will find the OpenSSL server. We don’t need network connectivity for this server to sign our certificates.
One thing you should check first is if your time, date and timezone is correct on all devices:
ASA1# show clock
10:04:12.169 CEST Fri Apr 8 2016ASA2# show clock
10:04:08.329 CEST Fri Apr 8 2016It’s a good idea to configure NTP on your Cisco ASA firewalls.
Install Root Certificate
Our firewalls have to trust our CA and we can do this by importing its root certificate. Let’s configure a trustpoint:
ASA1(config)# crypto ca trustpoint MY_CA
ASA1(config-ca-trustpoint)# enrollment terminal The trustpoint is called MY_CA and we will enroll the certificate from the terminal. We can do this with the following command:
ASA1(config)# crypto ca authenticate MY_CA
Enter the base 64 encoded CA certificate.
End with the word "quit" on a line by itself
-----BEGIN CERTIFICATE-----
MIIGBzCCA++gAwIBAgIBADANBgkqhkiG9w0BAQsFADCBnTELMAkGA1UEBhMCTkwx
FjAUBgNVBAgMDU5vcnRoLUJyYWJhbnQxEDAOBgNVBAcMB1RpbGJ1cmcxFzAVBgNV
BAoMDk5ldHdvcmtsZXNzb25zMSAwHgYDVQQDDBdDQS5uZXR3b3JrbGVzc29ucy5s
b2NhbDEpMCcGCSqGSIb3DQEJARYaYWRtaW5AbmV0d29ya2xlc3NvbnMubG9jYWww
HhcNMTYwNDAxMDg1ODMxWhcNMjYwMzMwMDg1ODMxWjCBnTELMAkGA1UEBhMCTkwx
FjAUBgNVBAgMDU5vcnRoLUJyYWJhbnQxEDAOBgNVBAcMB1RpbGJ1cmcxFzAVBgNV
BAoMDk5ldHdvcmtsZXNzb25zMSAwHgYDVQQDDBdDQS5uZXR3b3JrbGVzc29ucy5s
b2NhbDEpMCcGCSqGSIb3DQEJARYaYWRtaW5AbmV0d29ya2xlc3NvbnMubG9jYWww
ggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQCZUTCvJS+/ykH/+UtXI0yv
R9hqBZCKbB9KdhcuvvsM2QcLrsSS1u5hDW9K6K9rmK8Jj/M0E2pezEFZPdIVQIqV
JUKoBp0O6XwhNtWJLzAtP43xEqtmKMoAyr7lPOP1yaqgo+jdVY+xwZSD1diI/tFP
vUEL29/GoKTWsuz9k4sP82e766t47bn9butNLclpljLWilbZLJgN3hQk3NSo03GO
f/wO85aYo3VmACaPkkkGZhk1RhwE7kifV3HufmRGCtHHuTPmbORxvzNbq7k0Bfot
wXGMLVS2R08bqV4o91Z+1UfKXeBV5S7fHHCBFmJ8cQConkR5eSmq8nUXzs1Sb7tX
t53OP43APmPulkiOYuyZgkyqy6NOozbu4IWTCH1508+NHCSiKFwCnS+jt8RxxBFB
m9IGCy6MbL4Pjd1TsZECcYdERW2nZRf/hXlVg+SP8AUPKhpJcfN1fPTi0jF2K9DX
LeUgWbnIpy2vyyU/cYzJeCtCLoJECKOI/nQRYYJjh4AhK3+hXfqrm7HiU2lprpyN
8NL35E7bRUGF5voUeAtPS+xTcGr9giNPrayGj4inbbBWcD+GVDZOhZ1a7GZjyw1A
0OrLRviwVscoEKiLXic7GI5ChnIeZtHzflLWAt/gu2tYNnrnQv/zyICN+VPJD1Z/
aCdRwJTeDuBoviLy2ZKbmQIDAQABo1AwTjAdBgNVHQ4EFgQUGzi2n4JGcloEB3bC
2qVd65WDgTAwHwYDVR0jBBgwFoAUGzi2n4JGcloEB3bC2qVd65WDgTAwDAYDVR0T
BAUwAwEB/zANBgkqhkiG9w0BAQsFAAOCAgEARHaBLlb09q0/UPpM8TKgdkfwalb/
35zM2zjpvCR3q1dIMwZ4kYZHLmNBph3HE0rHzub44YLoiMOXQxklekcVTQo95ZFe
hGCaah9GUCNc6ck3WaQA9IcsWT6YLnWbUs4YKoV1Blp1O2nLAzm3YJNYiRnfvG0R
yTNLgA9cHdCHLtHv7vSrMHRYrZC+O2OE+nUO8NVcYpnAClx5ESzorKSpo5eLExgL
v0iY82YgsG67CaGKkHl1jzQDBnzBueSxqedqiZDoENsOc2uxl/h5Rkn14B7xc6I6
x+joKVmPWudbtjm1bG9ntXgnC6KifH8dALgHoAPqTOVUBdx8I1nDn6SrSPQIZTUL
zkxr7/VvfbTkfpiFEQMve718JOJ81MAksJ665Kv5A5wbmqbGCmPiE3aHcR/ErPFH
qpvYVXoiJJFKCSsFl3h7HpGrrzrghW2AjlqssOFRnT9mGKNbiqKOZ4Ow6CsR2qQU
I/SxxDPiPqOM3H3Knq5yV6O5jLTh1jhV1CGwxkZhlIssTGCqfF7r1aFqiGq53SfM
KtURG/XP9awc/VzJqHdV0tQmNJ0YKkTc90wgJepppw9Ud6v2/80TO5rgmGCvROXa
mYuubFQuc+hwBL6pKe3Rag6fB/5SeKS5CNV3zBXUj2t84kNs0AZGgQNd5sidr7xg
qqakkepONr6GoFU=
-----END CERTIFICATE-----
quitAbove I have pasted the contents of the cacert.pem file of my OpenSSL server. Don’t forget to add quit at the bottom. Once you have done this, you will see the following message:
ASA1#
INFO: Certificate has the following attributes:
Fingerprint: 4f35ae5b 496c0183 ddb8cadd 0d77e6f8
Do you accept this certificate? [yes/no]: yes
Trustpoint CA certificate accepted.
% Certificate successfully importedASA1 now trusts certificates that are signed by our CA.
Generate CSR (Certificate Signing Request) on ASA
The next step is to create a certificate for ASA1. We will do this by creating a CSR (Certificate Signing Request) which the CA will sign.
Let’s configure a hostname and domainname for our ASA:
ASA1(config)# hostname ASA1
ASA1(config)# domain-name networklessons.localThe CSR has to be signed with a private key so let’s generate one:
ASA1(config)# crypto key generate rsa label ASA1_KEY modulus 2048
INFO: The name for the keys will be: ASA1_KEY
Keypair generation process begin. Please wait...This will generate a key-pair called ASA1_KEY. Now we will configure the attributes for our CSR in the trustpoint:
ASA1(config)# crypto ca trustpoint MY_CALet’s configure the FQDN (Fully Qualified Domain Name) for our ASA:
ASA1(config-ca-trustpoint)# fqdn ASA1.networklessons.localAnd the attributes that identify our device:
ASA1(config-ca-trustpoint)# subject-name O=Networklessons, C=NL, EA=admin@networklessons.local, ST=North-Brabant, CN=ASA1.networklessons.localWe also need to specify the key that we want to use so sign the CSR. We will use the key-pair that we just created:
ASA1(config-ca-trustpoint)# keypair ASA1_KEYWe are now ready to create the CSR:
ASA1(config)# crypto ca enroll MY_CA
% Start certificate enrollment ..
% The subject name in the certificate will be: O=Networklessons, C=NL, EA=admin@networklessons.local, ST=North-Brabant, CN=ASA1.networklessons.local
% The fully-qualified domain name in the certificate will be: ASA1.networklessons.local
% Include the device serial number in the subject name? [yes/no]: no
Display Certificate Request to terminal? [yes/no]: yes
Certificate Request follows:
-----BEGIN CERTIFICATE REQUEST-----
MIIDRDCCAiwCAQAwgbcxIjAgBgNVBAMTGUFTQTEubmV0d29ya2xlc3NvbnMubG9j
YWwxFjAUBgNVBAgTDU5vcnRoLUJyYWJhbnQxKTAnBgkqhkiG9w0BCQEWGmFkbWlu
QG5ldHdvcmtsZXNzb25zLmxvY2FsMQswCQYDVQQGEwJOTDEXMBUGA1UEChMOTmV0
d29ya2xlc3NvbnMxKDAmBgkqhkiG9w0BCQIWGUFTQTEubmV0d29ya2xlc3NvbnMu
bG9jYWwwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDRXTZCwUQxpwF0
3P/qDGziiEF3gAXn+Tok+k5YLr/qyYBI3p2U7Yw7nyfVgtMqGjC42aIcWgRF+68d
XhP0Gj3FydRSYwL+3O1yP8ZbEo7Djfe6rLQg5M6IJqXUhy4Gk1zLCCF50Oul+kQ8
5JMJlE4sg4Fe6EEjykl1F0dwpx97mfuWqz27vY55o8NiFAbfqt9Ss2wizu1kwo/h
2mZNpPzQlbdNBpkOuJRDxcDs5eM9fZtzeLROM2t1keFLkbI6ZCrKQE26KjqEBY4Q
QUPDUYJQrdR77VQ6+LWl3OoYhrjhcGC8d9tw8We6JjjUljs4cA6smJuQA6jgorAF
Rr45unUNAgMBAAGgRzBFBgkqhkiG9w0BCQ4xODA2MA4GA1UdDwEB/wQEAwIFoDAk
BgNVHREEHTAbghlBU0ExLm5ldHdvcmtsZXNzb25zLmxvY2FsMA0GCSqGSIb3DQEB
BQUAA4IBAQCkIDeGBahWA3BiqSIckkkB+xJvPsRNSGMtlW8GX6FH3BELAltvvLnZ
D8f0ZzE1q58uiDzcht413C7xJ/8SmoYZi61g9G5snG+H5omWUWrjEffIDzjT6fo+
F5YeY4IU9nmeluLP89JjgIslJRLJfBuslnHVEl6I9t6Zkdtrs1TYDtmxJKGMZaD0
mloPcIG89py7/1UfbX96r01vfJNDLehsAY8GgxN+9btnlSaJ2uwH/Ytu+Lq7QO47
uc2j8+VmfRJqUkl0fEd7a7CR0owMGZ4kjK3mbP1kUHDdsFo/zpO7nAaKbRsOzaUs
W7sKv/Ty9XE1zxujHmMVXh1r/yuepOlB
-----END CERTIFICATE REQUEST-----
Redisplay enrollment request? [yes/no]: noAbove you can see that the firewall asks us to include the serial numbers, this is not required. Answer yes to display the CSR in the terminal.
We require this CSR on our CA so copy the contents (including the BEGIN and END lines) into a new file on your CA. I will call my file ASA1_CSR.txt.
We can use OpenSSL to sign the CSR:
# openssl ca -in ASA1_CSR.txt -out ASA1_SIGNED.pem
Using configuration from /usr/lib/ssl/openssl.cnf
Enter pass phrase for /root/ca/private/cakey.pem:
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 4661 (0x1235)
Validity
Not Before: Apr 8 08:25:15 2016 GMT
Not After : Apr 8 08:25:15 2017 GMT
Subject:
countryName = NL
stateOrProvinceName = North-Brabant
organizationName = Networklessons
commonName = ASA1.networklessons.local
emailAddress = admin@networklessons.local
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
36:D9:B1:A2:50:50:E9:92:07:D7:57:57:39:A2:13:93:9F:53:BE:AE
X509v3 Authority Key Identifier:
keyid:1B:38:B6:9F:82:46:72:5A:04:07:76:C2:DA:A5:5D:EB:95:83:81:30
Certificate is to be certified until Apr 8 08:25:15 2017 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base UpdatedAnswer yes to both questions and OpenSSL will sign the certificate for us, it will be stored in the ASA1_SIGNED.pem file.
Here’s what the file looks like:
-----BEGIN CERTIFICATE-----
MIIFIzCCAwugAwIBAgICEjUwDQYJKoZIhvcNAQELBQAwgZ0xCzAJBgNVBAYTAk5M
MRYwFAYDVQQIDA1Ob3J0aC1CcmFiYW50MRAwDgYDVQQHDAdUaWxidXJnMRcwFQYD
VQQKDA5OZXR3b3JrbGVzc29uczEgMB4GA1UEAwwXQ0EubmV0d29ya2xlc3NvbnMu
bG9jYWwxKTAnBgkqhkiG9w0BCQEWGmFkbWluQG5ldHdvcmtsZXNzb25zLmxvY2Fs
MB4XDTE2MDQwODA4MjUxNVoXDTE3MDQwODA4MjUxNVowgY0xCzAJBgNVBAYTAk5M
MRYwFAYDVQQIEw1Ob3J0aC1CcmFiYW50MRcwFQYDVQQKEw5OZXR3b3JrbGVzc29u
czEiMCAGA1UEAxMZQVNBMS5uZXR3b3JrbGVzc29ucy5sb2NhbDEpMCcGCSqGSIb3
DQEJARYaYWRtaW5AbmV0d29ya2xlc3NvbnMubG9jYWwwggEiMA0GCSqGSIb3DQEB
AQUAA4IBDwAwggEKAoIBAQDRXTZCwUQxpwF03P/qDGziiEF3gAXn+Tok+k5YLr/q
yYBI3p2U7Yw7nyfVgtMqGjC42aIcWgRF+68dXhP0Gj3FydRSYwL+3O1yP8ZbEo7D
jfe6rLQg5M6IJqXUhy4Gk1zLCCF50Oul+kQ85JMJlE4sg4Fe6EEjykl1F0dwpx97
mfuWqz27vY55o8NiFAbfqt9Ss2wizu1kwo/h2mZNpPzQlbdNBpkOuJRDxcDs5eM9
fZtzeLROM2t1keFLkbI6ZCrKQE26KjqEBY4QQUPDUYJQrdR77VQ6+LWl3OoYhrjh
cGC8d9tw8We6JjjUljs4cA6smJuQA6jgorAFRr45unUNAgMBAAGjezB5MAkGA1Ud
EwQCMAAwLAYJYIZIAYb4QgENBB8WHU9wZW5TU0wgR2VuZXJhdGVkIENlcnRpZmlj
YXRlMB0GA1UdDgQWBBQ22bGiUFDpkgfXV1c5ohOTn1O+rjAfBgNVHSMEGDAWgBQb
OLafgkZyWgQHdsLapV3rlYOBMDANBgkqhkiG9w0BAQsFAAOCAgEAj7lImxmS5QEc
5YTUk9IFKNsLIj1i5k2sqvbNZ1nVd/ACYlX4pfhteQb5MnKgoqgbMDN1i2fiJflZ
Zn0f7biaqYhgEAZKDJ8kHTJr3u6WRV1Y054vQ+uA7Zcjz/eVsmlfucef1x23Yxzi
Se64vhEbBNvvpurv15hWDts/c1LWHKmJx3nkvouaaqrjV4MlgKsFerKNFnkStq6F
WvS/eL1SwFVBKXnf4GjpsEiSOtsZISy1gSQ00aD2KUGiIyS5luMNyl7jG8MdTeMP
5jZHRvFIhi76DVTe6R6VtKI3Ed6E7LxTrw6hfYlfdFFekVeVBmYA9gTs2d1pIuGU
3MMBdsHq0MwpYcKOHrHzawz+r+Tas+DbZ2WF+krIpG18/BPHE3nNIQ4wrhm0hCUZ
i3kGA8PqRbaFU2J8CwwzkCCKYQovxjYmo1tjYU5T2f3G1BWnnOkmlKTisI5vnvmZ
D/Qf4gGAtTaPva8a1OdsBZI6TUJQCHFTgJTwreX+4R6OKDxFWkrLKEEmyqjTI1WP
ynO/VInIiStBUwWgyxRXz/KtlAZ1tAUTQfXXNcAvsXmAbQ7JmA9IlowzZnxY4j2E
/P+Ry/LVW2X3sNoLGdX64miEy9uGH/yq/5+5R7n5hSo8wy0mASkKuCMKL7GVqZLe
mUQ7YYAWPM6bPolr+dKlPRCUArpakns=
-----END CERTIFICATE-----Now we need to import this certificate to ASA1. Use the crypto ca import command for this:
ASA1(config)# crypto ca import MY_CA certificate
% The fully-qualified domain name in the certificate will be: ASA1.networklessons.local
Enter the base 64 encoded certificate.
End with the word "quit" on a line by itself
-----BEGIN CERTIFICATE-----
MIIFIzCCAwugAwIBAgICEjUwDQYJKoZIhvcNAQELBQAwgZ0xCzAJBgNVBAYTAk5M
MRYwFAYDVQQIDA1Ob3J0aC1CcmFiYW50MRAwDgYDVQQHDAdUaWxidXJnMRcwFQYD
VQQKDA5OZXR3b3JrbGVzc29uczEgMB4GA1UEAwwXQ0EubmV0d29ya2xlc3NvbnMu
bG9jYWwxKTAnBgkqhkiG9w0BCQEWGmFkbWluQG5ldHdvcmtsZXNzb25zLmxvY2Fs
MB4XDTE2MDQwODA4MjUxNVoXDTE3MDQwODA4MjUxNVowgY0xCzAJBgNVBAYTAk5M
MRYwFAYDVQQIEw1Ob3J0aC1CcmFiYW50MRcwFQYDVQQKEw5OZXR3b3JrbGVzc29u
czEiMCAGA1UEAxMZQVNBMS5uZXR3b3JrbGVzc29ucy5sb2NhbDEpMCcGCSqGSIb3
DQEJARYaYWRtaW5AbmV0d29ya2xlc3NvbnMubG9jYWwwggEiMA0GCSqGSIb3DQEB
AQUAA4IBDwAwggEKAoIBAQDRXTZCwUQxpwF03P/qDGziiEF3gAXn+Tok+k5YLr/q
yYBI3p2U7Yw7nyfVgtMqGjC42aIcWgRF+68dXhP0Gj3FydRSYwL+3O1yP8ZbEo7D
jfe6rLQg5M6IJqXUhy4Gk1zLCCF50Oul+kQ85JMJlE4sg4Fe6EEjykl1F0dwpx97
mfuWqz27vY55o8NiFAbfqt9Ss2wizu1kwo/h2mZNpPzQlbdNBpkOuJRDxcDs5eM9
fZtzeLROM2t1keFLkbI6ZCrKQE26KjqEBY4QQUPDUYJQrdR77VQ6+LWl3OoYhrjh
cGC8d9tw8We6JjjUljs4cA6smJuQA6jgorAFRr45unUNAgMBAAGjezB5MAkGA1Ud
EwQCMAAwLAYJYIZIAYb4QgENBB8WHU9wZW5TU0wgR2VuZXJhdGVkIENlcnRpZmlj
YXRlMB0GA1UdDgQWBBQ22bGiUFDpkgfXV1c5ohOTn1O+rjAfBgNVHSMEGDAWgBQb
OLafgkZyWgQHdsLapV3rlYOBMDANBgkqhkiG9w0BAQsFAAOCAgEAj7lImxmS5QEc
5YTUk9IFKNsLIj1i5k2sqvbNZ1nVd/ACYlX4pfhteQb5MnKgoqgbMDN1i2fiJflZ
Zn0f7biaqYhgEAZKDJ8kHTJr3u6WRV1Y054vQ+uA7Zcjz/eVsmlfucef1x23Yxzi
Se64vhEbBNvvpurv15hWDts/c1LWHKmJx3nkvouaaqrjV4MlgKsFerKNFnkStq6F
WvS/eL1SwFVBKXnf4GjpsEiSOtsZISy1gSQ00aD2KUGiIyS5luMNyl7jG8MdTeMP
5jZHRvFIhi76DVTe6R6VtKI3Ed6E7LxTrw6hfYlfdFFekVeVBmYA9gTs2d1pIuGU
3MMBdsHq0MwpYcKOHrHzawz+r+Tas+DbZ2WF+krIpG18/BPHE3nNIQ4wrhm0hCUZ
i3kGA8PqRbaFU2J8CwwzkCCKYQovxjYmo1tjYU5T2f3G1BWnnOkmlKTisI5vnvmZ
D/Qf4gGAtTaPva8a1OdsBZI6TUJQCHFTgJTwreX+4R6OKDxFWkrLKEEmyqjTI1WP
ynO/VInIiStBUwWgyxRXz/KtlAZ1tAUTQfXXNcAvsXmAbQ7JmA9IlowzZnxY4j2E
/P+Ry/LVW2X3sNoLGdX64miEy9uGH/yq/5+5R7n5hSo8wy0mASkKuCMKL7GVqZLe
mUQ7YYAWPM6bPolr+dKlPRCUArpakns=
-----END CERTIFICATE-----
quit
INFO: Certificate successfully importedPaste the contents of the ASA1_SIGNED.pem file on the ASA and it will be import the certificate. Don’t forget to add “quit” at the end of the certificate.
ASA1 now has a certificate that it can use to authenticate itself.
We can repeat this process on ASA2. Let’s import the root certificate of the CA:
ASA2(config)# crypto ca trustpoint MY_CA
ASA2(config-ca-trustpoint)# enrollment terminalASA2(config)# crypto ca authenticate MY_CA
Enter the base 64 encoded CA certificate.
End with the word "quit" on a line by itself
-----BEGIN CERTIFICATE-----
MIIGBzCCA++gAwIBAgIBADANBgkqhkiG9w0BAQsFADCBnTELMAkGA1UEBhMCTkwx
FjAUBgNVBAgMDU5vcnRoLUJyYWJhbnQxEDAOBgNVBAcMB1RpbGJ1cmcxFzAVBgNV
BAoMDk5ldHdvcmtsZXNzb25zMSAwHgYDVQQDDBdDQS5uZXR3b3JrbGVzc29ucy5s
b2NhbDEpMCcGCSqGSIb3DQEJARYaYWRtaW5AbmV0d29ya2xlc3NvbnMubG9jYWww
HhcNMTYwNDAxMDg1ODMxWhcNMjYwMzMwMDg1ODMxWjCBnTELMAkGA1UEBhMCTkwx
FjAUBgNVBAgMDU5vcnRoLUJyYWJhbnQxEDAOBgNVBAcMB1RpbGJ1cmcxFzAVBgNV
BAoMDk5ldHdvcmtsZXNzb25zMSAwHgYDVQQDDBdDQS5uZXR3b3JrbGVzc29ucy5s
b2NhbDEpMCcGCSqGSIb3DQEJARYaYWRtaW5AbmV0d29ya2xlc3NvbnMubG9jYWww
ggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQCZUTCvJS+/ykH/+UtXI0yv
R9hqBZCKbB9KdhcuvvsM2QcLrsSS1u5hDW9K6K9rmK8Jj/M0E2pezEFZPdIVQIqV
JUKoBp0O6XwhNtWJLzAtP43xEqtmKMoAyr7lPOP1yaqgo+jdVY+xwZSD1diI/tFP
vUEL29/GoKTWsuz9k4sP82e766t47bn9butNLclpljLWilbZLJgN3hQk3NSo03GO
f/wO85aYo3VmACaPkkkGZhk1RhwE7kifV3HufmRGCtHHuTPmbORxvzNbq7k0Bfot
wXGMLVS2R08bqV4o91Z+1UfKXeBV5S7fHHCBFmJ8cQConkR5eSmq8nUXzs1Sb7tX
t53OP43APmPulkiOYuyZgkyqy6NOozbu4IWTCH1508+NHCSiKFwCnS+jt8RxxBFB
m9IGCy6MbL4Pjd1TsZECcYdERW2nZRf/hXlVg+SP8AUPKhpJcfN1fPTi0jF2K9DX
LeUgWbnIpy2vyyU/cYzJeCtCLoJECKOI/nQRYYJjh4AhK3+hXfqrm7HiU2lprpyN
8NL35E7bRUGF5voUeAtPS+xTcGr9giNPrayGj4inbbBWcD+GVDZOhZ1a7GZjyw1A
0OrLRviwVscoEKiLXic7GI5ChnIeZtHzflLWAt/gu2tYNnrnQv/zyICN+VPJD1Z/
aCdRwJTeDuBoviLy2ZKbmQIDAQABo1AwTjAdBgNVHQ4EFgQUGzi2n4JGcloEB3bC
2qVd65WDgTAwHwYDVR0jBBgwFoAUGzi2n4JGcloEB3bC2qVd65WDgTAwDAYDVR0T
BAUwAwEB/zANBgkqhkiG9w0BAQsFAAOCAgEARHaBLlb09q0/UPpM8TKgdkfwalb/
35zM2zjpvCR3q1dIMwZ4kYZHLmNBph3HE0rHzub44YLoiMOXQxklekcVTQo95ZFe
hGCaah9GUCNc6ck3WaQA9IcsWT6YLnWbUs4YKoV1Blp1O2nLAzm3YJNYiRnfvG0R
yTNLgA9cHdCHLtHv7vSrMHRYrZC+O2OE+nUO8NVcYpnAClx5ESzorKSpo5eLExgL
v0iY82YgsG67CaGKkHl1jzQDBnzBueSxqedqiZDoENsOc2uxl/h5Rkn14B7xc6I6
x+joKVmPWudbtjm1bG9ntXgnC6KifH8dALgHoAPqTOVUBdx8I1nDn6SrSPQIZTUL
zkxr7/VvfbTkfpiFEQMve718JOJ81MAksJ665Kv5A5wbmqbGCmPiE3aHcR/ErPFH
qpvYVXoiJJFKCSsFl3h7HpGrrzrghW2AjlqssOFRnT9mGKNbiqKOZ4Ow6CsR2qQU
I/SxxDPiPqOM3H3Knq5yV6O5jLTh1jhV1CGwxkZhlIssTGCqfF7r1aFqiGq53SfM
KtURG/XP9awc/VzJqHdV0tQmNJ0YKkTc90wgJepppw9Ud6v2/80TO5rgmGCvROXa
mYuubFQuc+hwBL6pKe3Rag6fB/5SeKS5CNV3zBXUj2t84kNs0AZGgQNd5sidr7xg
qqakkepONr6GoFU=
-----END CERTIFICATE-----
quit
INFO: Certificate has the following attributes:
Fingerprint: 4f35ae5b 496c0183 ddb8cadd 0d77e6f8
Do you accept this certificate? [yes/no]: yes
Trustpoint CA certificate accepted.
% Certificate successfully importedNow we can generate a key-pair and configure the attributes for the CSR:
ASA2(config)# crypto key generate rsa label ASA2_KEY modulus 2048
INFO: The name for the keys will be: ASA2_KEY
Keypair generation process begin. Please wait...ASA2(config)# crypto ca trustpoint MY_CA
ASA2(config-ca-trustpoint)# fqdn ASA2.networklessons.local
ASA2(config-ca-trustpoint)# subject-name O=Networklessons, C=NL, EA=admin@networklessons.local, ST=North-Brabant, CN=ASA2.networklessons.local
ASA2(config-ca-trustpoint)# keypair ASA2_KEY
ASA2(config-ca-trustpoint)# exitLet’s create the CSR:
ASA2(config)# crypto ca enroll MY_CA
% Start certificate enrollment ..
% The subject name in the certificate will be: O=Networklessons, C=NL, EA=admin@networklessons.local, ST=North-Brabant, CN=ASA2.networklessons.local
% The fully-qualified domain name in the certificate will be: ASA2.networklessons.local
% Include the device serial number in the subject name? [yes/no]: no
Display Certificate Request to terminal? [yes/no]: yes
Certificate Request follows:
-----BEGIN CERTIFICATE REQUEST-----
MIIDRDCCAiwCAQAwgbcxIjAgBgNVBAMTGUFTQTIubmV0d29ya2xlc3NvbnMubG9j
YWwxFjAUBgNVBAgTDU5vcnRoLUJyYWJhbnQxKTAnBgkqhkiG9w0BCQEWGmFkbWlu
QG5ldHdvcmtsZXNzb25zLmxvY2FsMQswCQYDVQQGEwJOTDEXMBUGA1UEChMOTmV0
d29ya2xlc3NvbnMxKDAmBgkqhkiG9w0BCQIWGUFTQTIubmV0d29ya2xlc3NvbnMu
bG9jYWwwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDLOlT+lcnSH9qK
HGgqFLfpJVTbRw2J62aG4kjoO/mRVTECi2i+R2T8hreGao2NVALvgiip6mOr9h7d
jlkL5ztGLju2gLOvcYnSBuZwjBVUTCKpUySGUOzYTxQ9mY+Htw9Gqz81NnZ+tbso
WNAZhsLa0n7gfHmKBaIgleWhqOStnxIUywtUROCzzC6XLChS9/Qx77zqgsQfSE40
tWyDSEA7legjhizFBKrI3Ugwh0XV1imsTtuW+wxBAky7IkZ+O/5B5Mq9JEnPbp39
pEPgrw6nE6MQAbNqTfkgH92IecGXKAXU49CHPemaTpsj8PzOlfShVTtzIva9Mw5P
xjSaA+ZtAgMBAAGgRzBFBgkqhkiG9w0BCQ4xODA2MA4GA1UdDwEB/wQEAwIFoDAk
BgNVHREEHTAbghlBU0EyLm5ldHdvcmtsZXNzb25zLmxvY2FsMA0GCSqGSIb3DQEB
BQUAA4IBAQCcGlrBKWLmuAanUSU+lCvfRYstsDHn8EYzIp88sIgl8rz54PEo1vbi
stX1cl9Y48Tqg3wE7OSfvMAoYGcnyl5cdA3FZyLzUHhdWVjCzoJPwym+PWLEFgqV
8sLFnlQDBe1n4em4+O7tmOjLtQFndY1VrHk5oOhFNOk2D13WFZINZ8ExzjyYSsO2
Wxxn10lZdoBG2Kh47NVdpzdRrVgvLFqQtpZFs/gteztE6tBXbsuQdCr9Cw5zmIn7
sbfLW7muPZotyuvnQ3x0EXKrX/i6ki8SvbTNb/5bVzDhdk/j/RZC2l+WZdbCxYAw
20K/nrCRA8TqK6WYjSjPHyyZ3S+3R8hn
-----END CERTIFICATE REQUEST-----
Redisplay enrollment request? [yes/no]: noAnd sign the CSR with OpenSSL to create a certificate, saved as ASA2_SIGNED.pem.
# openssl ca -in ASA2_CSR.txt -out ASA2_SIGNED.pem
Using configuration from /usr/lib/ssl/openssl.cnf
Enter pass phrase for /root/ca/private/cakey.pem:
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 4662 (0x1236)
Validity
Not Before: Apr 8 08:36:48 2016 GMT
Not After : Apr 8 08:36:48 2017 GMT
Subject:
countryName = NL
stateOrProvinceName = North-Brabant
organizationName = Networklessons
commonName = ASA2.networklessons.local
emailAddress = admin@networklessons.local
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
13:C5:8F:D4:CA:C1:3D:43:35:84:28:EC:03:D5:DE:94:B5:3E:CB:38
X509v3 Authority Key Identifier:
keyid:1B:38:B6:9F:82:46:72:5A:04:07:76:C2:DA:A5:5D:EB:95:83:81:30
Certificate is to be certified until Apr 8 08:36:48 2017 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base UpdatedNow we need to import this certificate on ASA2. Open the new ASA2_SIGNED.pem file, we are going to paste it on ASA2:
ASA2(config)# crypto ca import MY_CA certificate
% The fully-qualified domain name in the certificate will be: ASA2.networklessons.local
Enter the base 64 encoded certificate.
End with the word "quit" on a line by itself
-----BEGIN CERTIFICATE-----
MIIFIzCCAwugAwIBAgICEjYwDQYJKoZIhvcNAQELBQAwgZ0xCzAJBgNVBAYTAk5M
MRYwFAYDVQQIDA1Ob3J0aC1CcmFiYW50MRAwDgYDVQQHDAdUaWxidXJnMRcwFQYD
VQQKDA5OZXR3b3JrbGVzc29uczEgMB4GA1UEAwwXQ0EubmV0d29ya2xlc3NvbnMu
bG9jYWwxKTAnBgkqhkiG9w0BCQEWGmFkbWluQG5ldHdvcmtsZXNzb25zLmxvY2Fs
MB4XDTE2MDQwODA4MzY0OFoXDTE3MDQwODA4MzY0OFowgY0xCzAJBgNVBAYTAk5M
MRYwFAYDVQQIEw1Ob3J0aC1CcmFiYW50MRcwFQYDVQQKEw5OZXR3b3JrbGVzc29u
czEiMCAGA1UEAxMZQVNBMi5uZXR3b3JrbGVzc29ucy5sb2NhbDEpMCcGCSqGSIb3
DQEJARYaYWRtaW5AbmV0d29ya2xlc3NvbnMubG9jYWwwggEiMA0GCSqGSIb3DQEB
AQUAA4IBDwAwggEKAoIBAQDLOlT+lcnSH9qKHGgqFLfpJVTbRw2J62aG4kjoO/mR
VTECi2i+R2T8hreGao2NVALvgiip6mOr9h7djlkL5ztGLju2gLOvcYnSBuZwjBVU
TCKpUySGUOzYTxQ9mY+Htw9Gqz81NnZ+tbsoWNAZhsLa0n7gfHmKBaIgleWhqOSt
nxIUywtUROCzzC6XLChS9/Qx77zqgsQfSE40tWyDSEA7legjhizFBKrI3Ugwh0XV
1imsTtuW+wxBAky7IkZ+O/5B5Mq9JEnPbp39pEPgrw6nE6MQAbNqTfkgH92IecGX
KAXU49CHPemaTpsj8PzOlfShVTtzIva9Mw5PxjSaA+ZtAgMBAAGjezB5MAkGA1Ud
EwQCMAAwLAYJYIZIAYb4QgENBB8WHU9wZW5TU0wgR2VuZXJhdGVkIENlcnRpZmlj
YXRlMB0GA1UdDgQWBBQTxY/UysE9QzWEKOwD1d6UtT7LODAfBgNVHSMEGDAWgBQb
OLafgkZyWgQHdsLapV3rlYOBMDANBgkqhkiG9w0BAQsFAAOCAgEAgv2SErS0AAw7
Fpv+PChIW1ibog3TSQ7RGFn2PQuOQX+F+PP/0G/r+ERoQsZureqCrs1i2hAJW7Lq
qMyK9pvQHmbB0uH5kCUJq15OcnBAmGBk7QyvPYDOPzsq/mOtq8Z94nJbf3dqhYtz
kwI6OAmoOnIUGlS4Q/CSjuaxDQqL7nnEU7lg7Uk9piIS6Zv17bz3E5kHVvMyBmwA
cWHRn4N9KQ/0w0Mymrz24U8d0UrEsRAb8Et6Kdr/dXaBM/pO8hv+f3hvcfPZO17l
0JPVTgJZwvJ5h8EDw6HyaRk156f5lcPAck3q3PFESivcSSmt/4cL3PyXnThXQFzX
zN6ztujCY+aTdGId1KeMWSacgoK+M0uw5OGUg/YcZ4rKG1G+qHHsrnTZtWp0TlV1
Zwofblxxe0nLvtMthzlg8W8FWZLa1hVjc8PbpDScA8f6jRIEn2qBhXtATvMcRrbc
pYRj559yEk3c3RI/jjz0lNZvkXW1qXir36A9v9lNOxatC2k984bvjHx9SJJSvVYk
uUa6MuV4t/NB3g70XReMSgZmwvqCR3YHzVw3lVCReTvWB5YUU8nSK/kmASewpym9
geWfvxn4F67Yuw7eWIpLkxqg4HSuFZPrxuxdo2Y6jR+745NXiMnC3P8RPH8KfsrL
yhP2hvTt5FZeP+yAX0XjsKq1XOwVClA=
-----END CERTIFICATE-----
quit
INFO: Certificate successfully importedThat’s it. ASA2 now has a certificate.
Both ASA firewalls trust our CA and each has a certificate that it can use for authentication. Time to configure IPsec.
Phase 1 Configuration
The VPN configuration for digital certificates is 99% the same as for pre-shared keys. First we will configure phase 1:


Rene,
Well done with this post, please post more article with this kind.
Thank you
Rene,
Thanks for the presentation, great info as always…
What would be the advantages of changing my current ASA VPN Pre-Shared Keys to Certificates?
I am kind of new to certificates, so what would be the process for my customers who connect with PSK VPNs? Would they need to provide me certificate from a trusted CA for my ASA, and I would provide them a certificate as well?
If i have a couple hundred VPNs, can i provide the same certificate to every customer, or is that not a best practice?
Thanks again for all the great tutorials.
Hi Brian,
Security-wise, the public/private key of a certificate are typically longer than a pre-shared key.
If you want to use certificates then both devices will have to trust the same root CA. You could use your own CA like I did with this example and sign two certificates. One for your firewall and one for the customer. Since both devices trust the CA, they will trust each other’s certificate.
This is the main advantage of using certificates. For example, let’s say you have 100 customers that build a VPN to your main office’s firewall. If you want to add an
... Continue reading in our forumHI my friend.
I am not sure if CA must be always available to the peers even when they authenticate each other. At the moment CA is not available the vpn will failed? what happen if reload one of the peers? it was only available at the moment of enrolling and authenticating certificates, could you explain me please?
Hello Brian
The use of a hostname is essentially there to make your life easier. According to Cisco: “Assigning a hostname identifies the host for subsequent enrollment commands, additional configuration, and provides flexibility in case the IP address of the CA server changes.”
... Continue reading in our forum